目录导航
①2021年3月18日:未写完,待续…….
基础技能&工具
常用方法
三要素:
时间
地点
事件(系统,安全设备,相关应用,操作历史日志)
回溯攻击手法:
模拟攻击
经验法
常用目录:(/tmp /var/tmp /dev/shm RECYCLER)
惯用手法:常见一句话木马,常见后门.
常见恶意程序特征
日志
主机
应用程序
安全性
系统
其他
IIS
Apache
Tomcat
日志id
登录
4625登陆失败
4624登陆成功
事件
5 拒绝访问
6 句柄无效
7 存储控制块被破坏
8 存储空间不足
9 存储控制块地址无效
常用工具
Sysinternals Suite工具合集
https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
Sysinternals故障排除实用程序已汇总到单个工具套件中。该文件包含各个故障排除工具和帮助文件。它不包含非故障排除工具,例如BSOD Screen Saver
下载地址:
下载Sysinternals Suite(38 MB)
下载Sysinternals Suite for Nano Server(7.9 MB)
下载Sysinternals Suite for ARM64(9.7 MB)
Autoruns
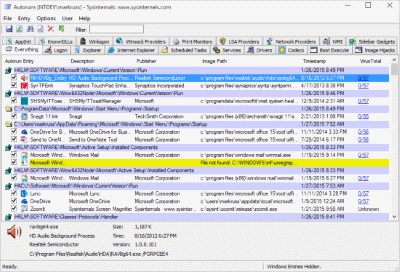
该实用程序具有所有启动监视器的自动启动位置的最全面的知识,它向您显示在系统启动或登录期间配置了哪些程序以运行,以及在启动各种内置Windows应用程序(例如Internet Explorer,Explorer和媒体)时玩家。这些程序和驱动程序包括在启动文件夹,Run,RunOnce和其他注册表项中。 自动运行会 报告资源管理器外壳程序扩展,工具栏,浏览器帮助对象,Winlogon通知,自动启动服务等。 自动运行超出其他自动启动的实用程序的方式。
自动运行‘ 签名的Microsoft项隐藏 选项,可帮助您在已添加到您的系统的第三方自动启动图像放大,并有在看配置的系统上配置其他帐户的自动启动图像的支持。下载软件包中还包含等效的命令行,可以以CSV格式自动运行输出。
https://docs.microsoft.com/zh-cn/sysinternals/downloads/autoruns
下载地址:
Download Autoruns and Autorunsc(2.5 MB)
Run now from Sysinternals Live.
procdump
ProcDump是一个命令行实用程序,其主要目的是监视应用程序中的CPU尖峰并在尖峰期间生成崩溃转储,管理员或开发人员可以使用它来确定尖峰原因。ProcDump还包括挂起的窗口监视(使用Windows和Task Manager使用的相同的窗口挂起定义),未处理的异常监视,并且可以基于系统性能计数器的值生成转储。它也可以用作常规流程转储实用程序,您可以将其嵌入其他脚本中。
https://docs.microsoft.com/zh-cn/sysinternals/downloads/procdump
下载地址:
下载ProcDump (659 KB)
PChunter
PC Hunter可以查看内核文件、驱动模块、隐藏进程、注册表等等信息,方便系统工程师在运维工作中获取相关数据。(火绒剑/Power Tool)
process monitor
Process Monitor是Windows的高级监视工具,可显示实时文件系统,注册表和进程/线程活动。它结合了两个旧的Sysinternals实用程序Filemon和 Regmon的功能,并添加了广泛的增强功能列表,包括丰富的和非破坏性的过滤,全面的事件属性(例如会话ID和用户名),可靠的过程信息,带有集成符号的完整线程堆栈支持每个操作,同时记录到文件等。它独特的强大功能将使Process Monitor成为您的系统故障排除和恶意软件搜索工具包中的核心实用程序。
Process Monitor具有强大的监视和过滤功能,其中包括:
- 为操作输入和输出参数捕获更多数据
- 无损过滤器使您可以设置过滤器而不会丢失数据
- 捕获每个操作的线程堆栈在许多情况下都可以确定操作的根本原因
- 可靠地捕获过程详细信息,包括图像路径,命令行,用户和会话ID
- 任何事件属性的可配置和可移动列
- 可以为任何数据字段设置过滤器,包括未配置为列的字段
- 先进的日志记录体系结构可扩展到数千万个捕获的事件和数千兆字节的日志数据
- 进程树工具显示跟踪中引用的所有进程的关系
- 本机日志格式保留所有数据以供加载到不同的Process Monitor实例中
- 过程工具提示,可轻松查看过程图像信息
- 详细信息工具提示可方便地访问列中不适合的格式化数据
- 可取消的搜索
- 所有操作的启动时间记录
https://docs.microsoft.com/zh-cn/sysinternals/downloads/procmon
下载地址
下载Process Monitor(2 MB)
现在可以从Sysinternals Live运行。
event log explorer
Event Log Explorer是一款检测系统安全的软件。查看,监视和分析跟事件记录,包括安全,系统,应用程序和其他微软Windows 的记录被记载的事件.
FullEventLogView
FullEventLogView是一个Windows事件日志查看工具,能够显示并查看所有的Windows事件日志的详细信息,包括事件描述,支持查看本地计算机的事件、也可以查看远程计算机的事件,并可以将事件导出为text、csv、tab-delimited、html、xml等类型的文件。
log paresr
- 日志解析器是一种功能强大的多功能工具,可提供对基于文本的数据(例如日志文件,XML文件和CSV文件)以及Windows®操作系统上的关键数据源(例如事件日志,注册表,文件系统和ActiveDirectory®。您可以告诉Log Parser所需的信息以及如何对其进行处理。查询结果可以在基于文本的输出中自定义格式,也可以持久保存到SQL,SYSLOG或图表等更特殊的目标中。
大多数软件旨在完成有限的特定任务。Log Parser是不同的…它的使用方式数量仅受用户的需求和想象力的限制。
下载地址
https://www.microsoft.com/en-us/download/details.aspx?id=24659
勒索病毒解密工具及网站
https://id-ransomware.malwarehunterteam.com/
$$$ Ransomware, 010001, 0kilobypt, 16x, 24H Ransomware, 32aa, 4rw5w, 5ss5c, 777, 7ev3n, 7h9r, 7zipper, 8lock8, AAC, ABCLocker, ACCDFISA v2.0, AdamLocker, Adhubllka, AES_KEY_GEN_ASSIST, AES-Matrix, AES-NI, AES256-06, AESMew, Afrodita, AgeLocker, Ako / MedusaReborn, Al-Namrood, Al-Namrood 2.0, Alcatraz, Alfa, Allcry, Alma Locker, Alpha, AMBA, Amnesia, Amnesia2, Anatova, AnDROid, AngryDuck, Annabelle 2.1, AnteFrigus, Anubi, Anubis, AnubisCrypt, Apocalypse, Apocalypse (New Variant), ApocalypseVM, ApolloLocker, AresCrypt, Argus, Aris Locker, Armage, ArmaLocky, Arsium, ASN1 Encoder, Ataware, Atchbo, Aurora, AutoLocky, AutoWannaCryV2, Avaddon, AVCrypt, Avest, AWT, AxCrypter, aZaZeL, B2DR, Babaxed, Babuk, BadBlock, BadEncript, BadRabbit, Bam!, BananaCrypt, BandarChor, Banks1, BarakaTeam, Bart, Bart v2.0, Basilisque Locker, BB Ransomware, BeijingCrypt, BetaSup, BigBobRoss, BigLock, Bisquilla, BitCrypt, BitCrypt 2.0, BitCryptor, BitKangoroo, Bitpaymer / DoppelPaymer, BitPyLock, Bitshifter, BitStak, BKRansomware, Black Claw, Black Feather, Black Shades, BlackHeart, BlackKingdom, Blackout, BlackRuby, Blind, Blind 2, Blocatto, BlockFile12, Blooper, Blue Blackmail, Bonsoir, BoooamCrypt, Booyah, BrainCrypt, Brazilian Ransomware, Brick, BrickR, BTCamant, BTCWare, BTCWare Aleta, BTCWare Gryphon, BTCWare Master, BTCWare PayDay, Bubble, Bucbi, Bud, Bug, BugWare, BuyUnlockCode, c0hen Locker, Cancer, Cassetto, Cerber, Cerber 2.0, Cerber 3.0, Cerber 4.0 / 5.0, CerberTear, CheckMail7, Chekyshka, ChernoLocker, Chimera, ChinaJm, ChinaYunLong, ChineseRarypt, CHIP, ClicoCrypter, Clop, Clouded, CmdRansomware, CNHelp, CobraLocker, CockBlocker, Coin Locker, CoinVault, Comrade Circle, Conficker, Consciousness, Conti, CoronaVirus, CorruptCrypt, Cossy, Coverton, Cr1ptT0r Ransomware, CradleCore, CreamPie, Creeper, Cripton, Cripton7zp, Cry128, Cry36, Cry9, Cryakl, CryCryptor, CryFile, CryLocker, CrypMic, Crypren, Crypt0, Crypt0L0cker, Crypt0r, Crypt12, Crypt32, Crypt38, Crypt3r, CryptConsole, CryptConsole3, CryptFuck, CryptGh0st, CryptInfinite, CryptoDarkRubix, CryptoDefense, CryptoDevil, CryptoFinancial, CryptoFortress, CryptoGod, CryptoHasYou, CryptoHitman, CryptoJacky, CryptoJoker, CryptoLocker3, CryptoLockerEU, CryptoLocky, CryptoLuck, CryptoMix, CryptoMix Revenge, CryptoMix Wallet, CryptON, Crypton, CryptoPatronum, CryptoPokemon, CryptorBit, CryptoRoger, CryptoShield, CryptoShocker, CryptoTorLocker, CryptoViki, CryptoWall 2.0, CryptoWall 3.0, CryptoWall 4.0, CryptoWire, CryptXXX, CryptXXX 2.0, CryptXXX 3.0, CryptXXX 4.0, CryPy, CrySiS, Crystal, CSP Ransomware, CTB-Faker, CTB-Locker, Cuba, CXK-NMSL, Cyborg, Cyrat, D00mEd, Dablio, Damage, DarkoderCryptor, DarkSide, DataKeeper, DavesSmith / Balaclava, Dcrtr, DCry, DCry 2.0, Deadly, DearCry, DeathHiddenTear, DeathHiddenTear v2, DeathNote, DeathOfShadow, DeathRansom, DEcovid19, Decr1pt, DecryptIomega, DecYourData, DEDCryptor, Defender, Defray, Defray777 / RansomEXX, DeriaLock, DeroHE, Desync, Dharma (.cezar Family), Dharma (.dharma Family), Dharma (.onion Family), Dharma (.wallet Family), Digisom, DilmaLocker, DirtyDecrypt, Dishwasher, District, DMA Locker, DMA Locker 3.0, DMA Locker 4.0, DMALocker Imposter, DoggeWiper, Domino, Done, DoNotChange, Donut, DoubleLocker, DriedSister, DryCry, DualShot, Dviide, DVPN, DXXD, DynA-Crypt, eBayWall, eCh0raix / QNAPCrypt, ECLR Ransomware, EdgeLocker, EduCrypt, EggLocker, Egregor, El Polocker, Enc1, Encrp, EnCrypt, EncryptedBatch, EncrypTile, EncryptoJJS, Encryptor RaaS, Enigma, Enjey Crypter, EnkripsiPC, EOEO, Epsilon, Erebus, Erica Ransomware, Eris, Estemani, Eternal, Everbe, Everbe 2.0, Everbe 3.0, Evil, Executioner, ExecutionerPlus, Exerwa CTF, Exocrypt XTC, Exorcist Ransomware, Exotic, Extortion Scam, Extractor, EyeCry, Fabiansomware, Fadesoft, Fantom, FartPlz, FCPRansomware, FCrypt, FCT, FenixLocker, FenixLocker 2.0, Fenrir, FilesLocker, FindZip, FireCrypt, Flamingo, Flatcher3, FLKR, FlowEncrypt, Flyper, FonixCrypter, FreeMe, FrozrLock, FRSRansomware, FS0ciety, FTCode, FuckSociety, FunFact, FuxSocy Encryptor, Galacti-Crypter, GandCrab, GandCrab v4.0 / v5.0, GandCrab2, GarrantyDecrypt, GC47, Geneve, Gerber, GermanWiper, GetCrypt, GhostCrypt, GhostHammer, Gibberish, Gibon, Gladius, Globe, Globe (Broken), Globe3, GlobeImposter, GlobeImposter 2.0, GoCryptoLocker, Godra, GOG, GoGoogle, GoGoogle 2.0, Golden Axe, GoldenEye, Gomasom, Good, Gopher, GoRansom, Gorgon, Gotcha, GPAA, GPCode, GPGQwerty, GusCrypter, GX40, Hades, HadesLocker, Hakbit, Halloware, Hansom, HappyDayzz, hc6, hc7, HDDCryptor, HDMR, HE-HELP, Heimdall, Hello (WickrMe), HelloKitty, HellsRansomware, Help50, HelpDCFile, Herbst, Hermes, Hermes 2.0, Hermes 2.1, Hermes837, Heropoint, Hi Buddy!, HiddenTear, HildaCrypt, HKCrypt, HollyCrypt, HolyCrypt, HowAreYou, HPE iLO Ransomware, HR, Hucky, Hydra, HydraCrypt, IEncrypt, IFN643, ILElection2020, Ims00ry, ImSorry, Incanto, InducVirus, InfiniteTear, InfinityLock, InfoDot, InsaneCrypt, IQ, iRansom, Iron, Ironcat, Ishtar, Israbye, iTunesDecrypt, JabaCrypter, Jack.Pot, Jaff, Jager, JapanLocker, JavaLocker, JCrypt, JeepersCrypt, Jemd, Jigsaw, JNEC.a, JobCrypter, JoeGo Ransomware, JoJoCrypter, JosepCrypt, JSWorm, JSWorm 2.0, JSWorm 4.0, JuicyLemon, JungleSec, Kaenlupuf, Kali, Karma, Karmen, Karo, Kasiski, Katyusha, KawaiiLocker, KCW, Kee Ransomware, KeRanger, Kerkoporta, KesLan, KeyBTC, KEYHolder, KillerLocker, KillRabbit, KimcilWare, Kirk, Knot, KokoKrypt, Kolobo, Kostya, Kozy.Jozy, Kraken, Kraken Cryptor, KratosCrypt, Krider, Kriptovor, KryptoLocker, Kupidon, L33TAF Locker, Ladon, Lalabitch, LambdaLocker, LeakThemAll, LeChiffre, LightningCrypt, Lilocked, Lime, Litra, LittleFinger, LLTP, LMAOxUS, Lock2017, Lock2Bits, Lock93, LockBit, LockBox, LockCrypt, LockCrypt 2.0, LockDown, Locked-In, LockedByte, LockeR, LockerGoga, LockLock, LockMe, Lockout, LockTaiwan, Locky, Loki, Lola, LolKek, LongTermMemoryLoss, LonleyCrypt, LooCipher, Lortok, Lost_Files, LoveServer, LowLevel04, LuciferCrypt, Lucky, MadBit, MAFIA, MafiaWare, Magic, Magniber, Major, Makop, Maktub Locker, MalwareTech's CTF, MaMoCrypter, Maoloa, Mapo, Marduk, Marlboro, MarraCrypt, Mars, MarsJoke, Matrix, MauriGo, MaxiCrypt, Maykolin, Maysomware, Maze Ransomware, MCrypt2018, MedusaLocker, MegaCortex, MegaLocker, Mespinoza, Meteoritan, Mew767, Mikoyan, MindSystem, Minotaur, MirCop, MireWare, Mischa, MMM, MNS CryptoLocker, Mobef, MongoLock, Montserrat, MoonCrypter, MorrisBatchCrypt, MOTD, MountLocker, MoWare, MRCR1, MrDec, Muhstik, Mystic, n1n1n1, NanoLocker, NAS Data Compromiser, NCrypt, Nefilim, NegozI, Nemty, Nemty 2.x, Nemty Special Edition, Nemucod, Nemucod-7z, Nemucod-AES, NETCrypton, Netix, Netwalker (Mailto), NewHT, NextCry, Nhtnwcuf, NM4, NMoreira, NMoreira 2.0, Noblis, Nomikon, NonRansomware, NotAHero, Nozelesn, NSB Ransomware, Nuke, NullByte, NxRansomware, Nyton, ODCODC, OhNo!, OmniSphere, OnyxLocker, OoPS, OopsLocker, OpenToYou, OpJerusalem, Ordinypt, Osno, Ouroboros v6, OutCrypt, OzozaLocker, PadCrypt, Panther, Paradise, Paradise .NET, Paradise B29, Parasite, Pay2Key, Paymen45, PayPalGenerator2019, PaySafeGen, PClock, PClock (Updated), PEC 2017, Pendor, Petna, PewCrypt, PewPew, PGPSnippet, PhantomChina, Philadelphia, Phobos, PhoneNumber, Pickles, PL Ransomware, Plague17, Planetary Ransomware, PoisonFang, Pojie, PonyFinal, PopCornTime, Potato, Povlsomware, PowerLocky, PowerShell Locker, PowerWare, PPDDDP, Pr0tector, Predator, PrincessLocker, PrincessLocker 2.0, PrincessLocker Evolution, Project23, Project34, Project57, ProLock, Protected Ransomware, PshCrypt, PUBG Ransomware, PureLocker, PwndLocker, PyCL, PyCL, PyL33T, PyLocky, qkG, QP Ransomware, QuakeWay, Quimera Crypter, QwertyCrypt, Qweuirtksd, R980, RAA-SEP, RabbitFox, RabbitWare, RackCrypt, Radamant, Radamant v2.1, Radiation, RagnarLocker, RagnarLocker 2.0+, Ragnarok, Random6, RandomLocker, RandomRansom, Ranion, RanRan, RanRans, Rans0mLocked, RansomCuck, Ransomnix, RansomPlus, Ransomwared, RansomWarrior, Rapid, Rapid 2.0 / 3.0, RaRansomware, RarVault, Razy, RedBoot, RedEye, RedRum / Tycoon 1.0, RegretLocker, REKTLocker, Rektware, Relock, RemindMe, RenLocker, RensenWare, RetMyData, REvil / Sodinokibi, Reyptson, Rhino, RNS, RobbinHood, Roga, Rokku, Rontok, RoshaLock, RotorCrypt, Roza, RSA-NI, RSA2048Pro, RSAUtil, Ruby, Russenger, Russian EDA2, Ryuk, SAD, SadComputer, Sadogo, SADStory, Sage 2.0, Salsa, SamSam, Sanction, Sanctions, SantaCrypt, Satan, Satana, SatanCryptor, Saturn, SaveTheQueen, Scarab, ScareCrow, SD 1.1, Sekhmet, Seon, Sepsis, SerbRansom, Serpent, SFile, ShellLocker, Shifr, Shigo, ShinigamiLocker, ShinoLocker, ShivaGood, ShkolotaCrypt, Shrug, Shrug2, Shujin, Shutdown57, SifreCozucu, Sifreli, Sigma, Sigrun, SilentDeath, SilentSpring, Silvertor, Simple_Encoder, SintaLocker, Skull Ransomware, SkyFile, SkyStars, Smaug, Smrss32, Snake (Ekans), SnakeLocker, SnapDragon, Snatch, SNSLocker, SoFucked, Solider, Solo Ransomware, Solve, Somik1, Spartacus, SpartCrypt, Spectre, Spider, Spora, Sport, SQ_, Stampado, Stinger, STOP (Djvu), STOP / KEYPASS, StorageCrypter, Storm, Striked, Stroman, Stupid Ransomware, Styx, Such_Crypt, SunCrypt, SuperB, SuperCrypt, Surprise, SynAck, SyncCrypt, Syrk, SYSDOWN, SystemCrypter, SZFLocker, Szymekk, T1Happy, TapPiF, Team XRat, Telecrypt, TellYouThePass, Termite, TeslaCrypt 0.x, TeslaCrypt 2.x, TeslaCrypt 3.0, TeslaCrypt 4.0, Teslarvng, TeslaWare, TFlower, Thanatos, Thanos, The DMR, TheDarkEncryptor, THIEFQuest, THT Ransomware, ThunderCrypt, ThunderX, tk, Tongda, Torchwood, TotalWipeOut, TowerWeb, ToxCrypt, Tripoli, Trojan.Encoder.6491, Troldesh / Shade, Tron, TrueCrypter, TrumpLocker, TurkStatik, Tycoon 2.0 / 3.0, UCCU, UIWIX, Ukash, UmbreCrypt, UnblockUPC, Ungluk, Unit09, Unknown Crypted, Unknown Lock, Unknown XTBL, Unlock26, Unlock92, Unlock92 2.0, Unlock92 Zipper, UnluckyWare, Useless Disk, UselessFiles, UserFilesLocker, USR0, Uyari, V8Locker, Vaggen, Vapor v1, Vash-Sorena, VaultCrypt, vCrypt, VCrypt, Vega / Jamper / Buran, Velso, Vendetta, VenisRansomware, VenusLocker, VHD Ransomware, ViACrypt, VindowsLocker, VisionCrypt, VMola, VoidCrypt, Vortex, Vovalex, Vurten, VxLock, Waffle, Waiting, Waldo, WannaCash, WannaCash 2.0, WannaCry, WannaCry.NET, WannaCryFake, WannaCryOnClick, WannaDie, WannaPeace, WannaRen, WannaScream, WannaSmile, WannaSpam, WastedBit, WastedLocker, Wesker, WhatAFuck, WhiteRose, WildFire Locker, WininiCrypt, Winnix Cryptor, WinRarer, WonderCrypter, WoodRat, Wooly, Wulfric, X Locker 5.0, XCry, XCrypt, XData, XerXes, XiaoBa, XiaoBa 2.0, XMRLocker, Xorist, Xort, XRTN, XTP Locker 5.0, XYZWare, Yatron, Yogynicof, YouAreFucked, YourRansom, Yyto, Z3, ZariqaCrypt, zCrypt, Zekwacrypt, Zenis, Zeoticus, Zeoticus 2.0, Zeppelin, ZeroCrypt, ZeroFucks, Zeronine, Zeropadypt, Zeropadypt NextGen / Ouroboros, ZeroRansom, Zhen, Ziggy, Zilla, ZimbraCryptor, ZinoCrypt, ZipLocker, Zipper, Zoldon, Zorab, ZQ, Zyklon