目录导航
文件大小
文件目录列表
APT_REPORT
│ 0day _In the Wild_.xlsx
│ APT Groups and Operations.xlsx
│ APT_2021_global_research_qianxin.pdf
│ A_Threat_Actor_Encyclopedia.pdf
│ microsoft-threat-actor-list.xlsx
│ National Cyber Power Index 2020.pdf
│ README.md
│ Threat Group Cards.pdf
│ Threat_Group_Cards_v2.0.pdf
│
├─Agrius
│ evol-agrius.pdf
│ README.MD
│
├─AISecurity
│ Engaging with Artificial Intelligence (AI).pdf
│ readme.md
│ US-23-Huang-IRonMAN.pdf
│ US23-Heiding-Devicing-and-Detecting-Phishing-wp.pdf
│ US23-Heiding-Devicing-and-Detecting-Phishing.pdf
│
├─Anonymous
│ │ Alert_OpIsrael_Final_3-29-23.pdf
│ │ Anonymous-Sudan-Report.pdf
│ │ README.MD
│ │
│ └─IsraelPalestinewar
│ readme.md
│
├─APT-hunting
│ │ ActiveDirectory DACL Abuse.jpeg
│ │ hunting-cobaltstrike-beacons-in-the-dark.pdf
│ │ README.MD
│ │ THREAT HUNTING PLAYBOOK .pdf
│ │ Threat Hunting with VirusTotal.pdf
│ │ VTI_Cheatsheet.pdf
│ │
│ └─fn_fuzzy
│ │ cli_export.py
│ │ dump_types.py
│ │ fn_fuzzy.py
│ │ fuzzy64.dll
│ │ README.org
│ │ yara_fn.py
│ │
│ └─img
│ fn_fuzzy.png
│ res_funcs.png
│ res_summary.png
│
├─APT28
│ │ 2021-05_FancyBear.pdf
│ │ APT28_CERTFR_2023_EN.pdf
│ │ BlueDelta Exploits Ukrainian Government Roundcube Mail Servers to Support Espionage Activities.pdf
│ │ README.MD
│ │
│ ├─decode
│ │ zebrocy_decrypt_artifact.py
│ │
│ ├─history-report-pdf
│ │ 20180713_CSE_APT28_X-Agent_Op-Roman Holiday-Report_v6_1.pdf
│ │ APT28-Center-of-Storm-2017.pdf
│ │ apt28-targets-hospitality-sector.html.pdf
│ │ apt28.pdf
│ │ Bitdefender-Whitepaper-APT-Mac-A4-en-EN-web.pdf
│ │ Bitdefender_In-depth_analysis_of_APT28__The_Political_Cyber-Espionage.pdf
│ │ eset-sednit-part-2.pdf
│ │ eset-sednit-part1.pdf
│ │ eset-sednit-part3.pdf
│ │ New Xagent Mac Malware Linked with the APT28 _ Bitdefender Labs.pdf
│ │ Sednit APT Group Meets Hacking Team.pdf
│ │ sednit-update-analysis-zebrocy_.pdf
│ │ Threat_Group_APT28_Slips_Office_Malware.pdf
│ │
│ ├─IOC
│ │ 2019-04-05-ioc-mark.txt
│ │ 2019-04-09-ioc-mark.txt
│ │
│ └─yara
│ APT28.yar
│ apt28_backdoor_cls.yar
│ tau_fancybear_downloader_public.yara
│
├─APT29
│ │ AA21-116A_Russian_Foreign_Intelligence_Service_Cyber_Operations_508C.pdf
│ │ aa23-347a-russian-foreign-intelligence-service-svr-exploiting-jetbrains-teamcity-cve-globally.pdf
│ │ Advisory Further TTPs associated with SVR cyber actors.pdf
│ │ APT29 Adapts to Target Diplomatic Entities with GraphicalProton Malware.pdf
│ │ APT29 attacks Embassies using CVE-2023-38831 - report en.pdf
│ │ BlueBravo Uses Ambassador Lure to Deploy GraphicalNeutrino Malware.pdf
│ │ F-Secure_Dukes_Whitepaper.pdf
│ │ NCSC_APT29_ADVISORY-QUAD-OFFICIAL-20200709-1810.PDF
│ │ README.MD
│ │
│ └─CERT.PL
│ HALFRIG_.pdf
│ IoC_Reference_.pdf
│ QUARTERRIG_.pdf
│ README.MD
│ SNOWYAMBER_.pdf
│
├─APT3
│ apt3-nsa-tool.zip
│ README.MD
│
├─APT34
│ │ APT34-LeakCode.zip
│ │ apt34leak-part2.zip
│ │ Jason.zip
│ │ README.MD
│ │ update picture.zip
│ │
│ └─APT34 's hacker-picture
│ 107de0b2-9cb0-4184-b621-aed90033dc65.jpg
│ 1fb983fc-5ad8-423e-95c8-ce7a15d8a7f4.jpg
│ 3b91b18d-d06c-428c-a82b-9f9a000a83ea.jpg
│ 91d58763-da11-4125-abe2-7b8e6bac2148.jpg
│ 91fc0002-1631-46d1-8f53-254c5a499f1c.jpg
│ a436839b-dd74-4bdb-848a-12a80dd5f290.jpg
│ Ahmad Ghazi.jpg
│ fc45ac24-1d55-4eb0-9c09-7de7bcb1307c.jpg
│ Mehdi farhadi.png
│ phone.txt
│
├─APT36
│ README.MD
│
├─APT41
│ README.MD
│ With KEYPLUG,China’sRedGolf Spies On, Steals From Wide Field of Targets.pdf
│
├─APT43
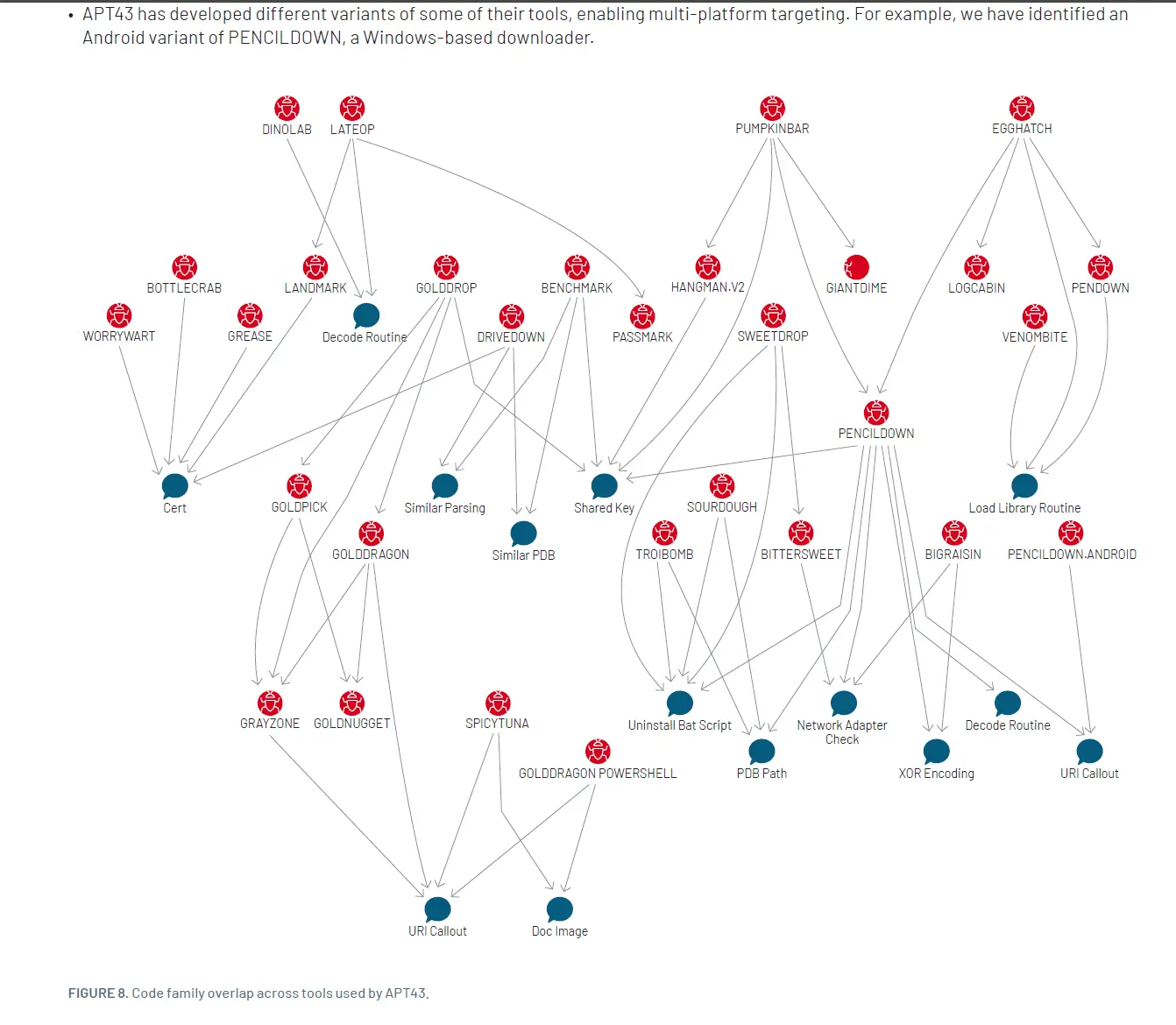
│ APT43 Report.pdf
│ README.MD
│
├─Arid Viper
│ README.MD
│ Technical-threat-report-Arid-Viper-April-2021.pdf
│
├─baby-kimsuky
│ BabyShark Rule - Mal Cert and others.xlsx
│ babyshark-CVE20188174.php
│ Decode-Cowboy.py
│ README.MD
│
├─BadMagic
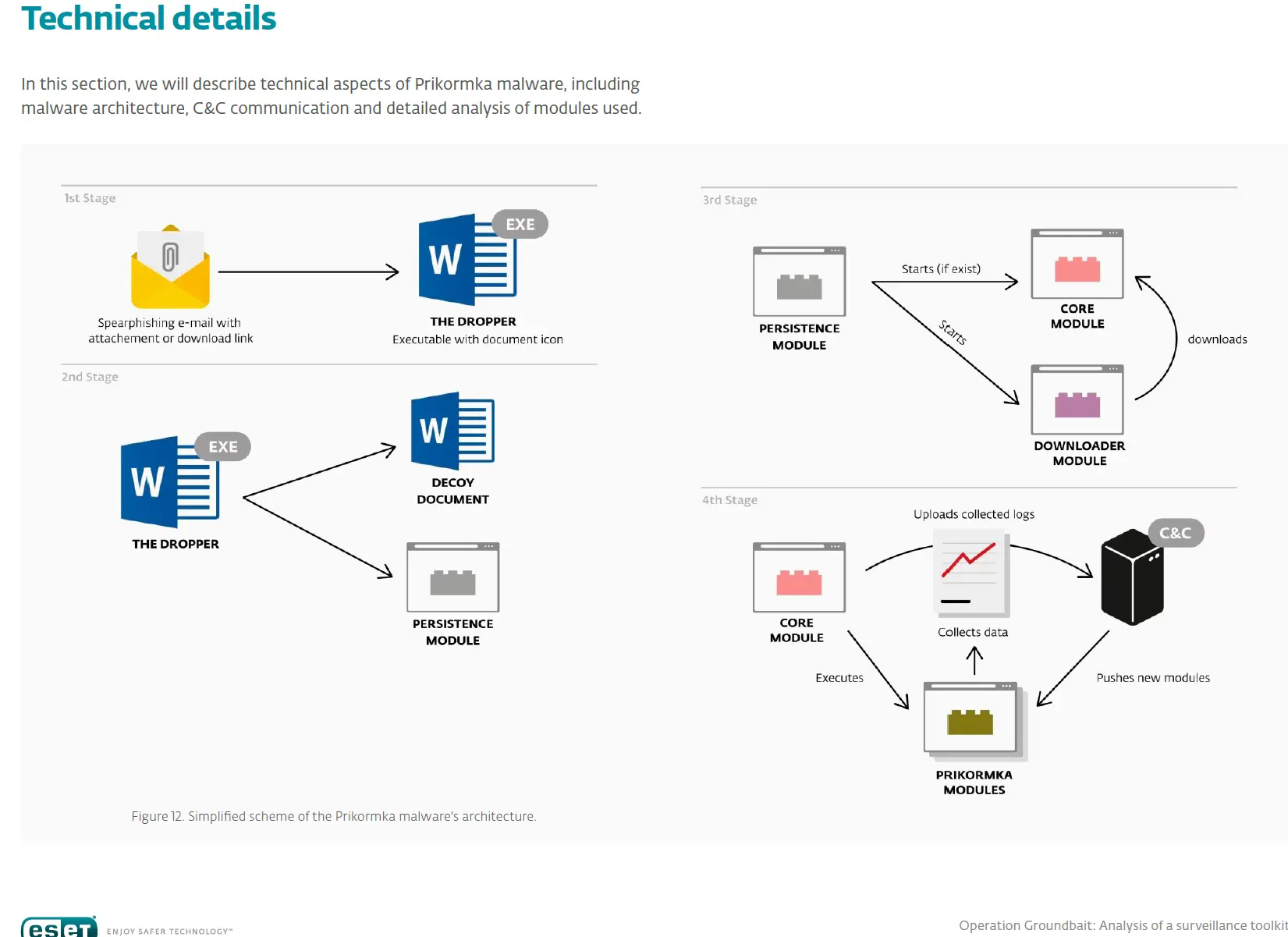
│ Operation-Groundbait.pdf
│ readme.md
│
├─bitter
│ │ Inf.MD
│ │
│ ├─2020
│ │ Android-Bitter-ioc.txt
│ │ Bitdefender-PR-Whitepaper-BitterAPT-creat4571-en-EN-GenericUse.pdf
│ │
│ └─2022
│ Quarterly-Adversarial-Threat-Report-Q2-2022.pdf
│ README.MD
│
├─Blacktech
│ blacktech-TSCookie.zip
│ CSA_BLACKTECH_HIDE_IN_ROUTERS_TLP-CLEAR.PDF
│ README.MD
│ tscookie_data_decode.py
│
├─BlindEagle
│ APT_Blind_Eagles.pdf
│ APT_Blind_Eagles_Malware_Arsenal_Technical_Analysis_of_the_New.pdf
│ README.MD
│
├─Buhtrap
│ README.MD
│
├─Calisto
│ BlueCharlie_Continues_to_Deploy_New_Infrastructure_in_2023.pdf
│ Nisos-Research-Coldriver-Group.pdf
│ readme.md
│
├─Candiru
│ Candiru_product.pdf
│ README.MD
│
├─carbanak
│ carbanak-sourcecode(password is 123).zip
│ README.MD
│
├─Chafer-APT39
│ README.MD
│ TREKX.YAR
│
├─Charming Kitten
│ 2023-08-10-cyber-brief-no-01-2023.pdf
│ README.MD
│ The-Kittens-are-Back-in-Town-3.pdf
│ The-Kittens-Are-Back-in-Town-Charming-Kitten-2019.pdf
│
├─Confucius
│ OperationTibbar-A-retaliatory-targeted-attack-from-SouthAsian-APT-Group-Confucius.pdf
│ README.MD
│
├─COVID
│ 200407-MWB-COVID-White-Paper_Final.pdf
│ README.MD
│
├─cybercrime
│ │ Analysis-of-THE-MANUAL.pdf
│ │ KELA_Telegram_CEBIN.pdf
│ │ README.MD
│ │ [RIG] RIG Exploit Kit_ In-Depth Analysis.pdf
│ │
│ ├─2023
│ │ 2022 INTERNET CRIME REPORT.pdf
│ │ README.MD
│ │
│ ├─BEC
│ │ 202305ioc.txt
│ │ Exploring-the-Rise-of-Israel-Based-BEC-Attacks.pdf
│ │ readme.md
│ │
│ ├─botnet
│ │ └─BADBOX
│ │ HUMAN_Report_BADBOX-and-PEACHPIT.pdf
│ │ readme.md
│ │
│ ├─emotet
│ │ Emotet_Exposed_A_Look_Inside_the_Cybercriminal_Supply_Chain.pdf
│ │ README.MD
│ │
│ └─OPERA1ER
│ Group-IB_RPRT_OPERA1ER_EN_full.pdf
│ README.MD
│
├─CyberMerceNary
│ IOCs-void-balaur-tracking-a-cybermercenary-activities.txt
│ README.MD
│ wp-void-balaur-tracking-a-cybermercenarys-activities.pdf
│
├─Cytrox
│ Predator_ioc.csv
│ README.MD
│ Threat-Report-on-the-Surveillance-for-Hire-Industry.pdf
│
├─Darkhotel
│ │ README.MD
│ │
│ ├─exploit-attack
│ │ cve-2020-0674.poc
│ │
│ └─higaisa
│ higaisa_apt_report.pdf
│ README.MD
│
├─data
│ │ readme.md
│ │
│ ├─facebookdb
│ │ mongodb-2.json
│ │ mongodb.json
│ │
│ └─wordpress
│ │ a316d81976b82d3d6cee974ba4dd5333506d2c93a7f0b2e5cd8e1a75bb325a1b
│ │ backdoorGood.txt
│ │ one.txt
│ │ README.MD
│ │ two.txt
│ │
│ └─PHP
│ 3uHxyFAZ.txt
│ 6hCDtMRr.txt
│ 6yK2y2Qm.txt
│ cugKiQ7h.txt
│ fbHtDWxe.txt
│ fgwNrs5e.txt
│ JFtCDEJE.txt
│ PuT9UvUS.txt
│ test
│ zRj9ETT9.txt
│
├─DeadlyKiss
│ DeadlyKiss_TAAR.pdf
│ README.MD
│
├─Donot
│ │ Donot Group & Innefu Labs.pdf
│ │ README.MD
│ │
│ └─android-sample
│ kashmirVoice.zip
│ README.MD
│
├─DustSquad
│ Nomadic Octopus’ Paperbug Campaign.pdf
│ README.MD
│
├─EquationGroup
│ 7989032a5a2baece889100c4cfeca81f1da1241ab47365dad89107e417ce7bac
│ README.MD
│ The_Bvp47_a_top-tier_backdoor_of_us_nsa_equation_group.en.pdf
│
├─Exploit
│ EXP-LIST.md
│
├─exploit_report
│ #bluekeep RDP from patch to remote code execution.pdf
│ DETECT AND PREVENT WEB SHELL MALWARE.PDF
│ README.MD
│
├─Gamaredon
│ Beyond_Bullets_and_Bombs_An_Examination_of_Armageddon_Groups_Cyber.pdf
│ Cybergun_Technical_Analysis_of_the_Armageddons_Infostealer.pdf
│ Gamaredon.yar
│ Gamaredon202102_ioc1000+.csv
│ Platinum feature article - Targeted attacks in South and Southeast Asia April 2016.pdf
│ README.MD
│ Technical report Armagedon.pdf
│
├─Ghostwriter
│ Ghostwriter-Report-Final.pdf
│ README.MD
│ unc1151-ghostwriter-update-report.pdf
│
├─group123
│ │ 20230620_threat_inteligence_report_apt37_macos.pdf
│ │ 20231229_threat_inteligence_report_market.pdf
│ │ 2023_Group123_threat_inteligence_report_BitB.pdf
│ │ apt37newyear.pdf
│ │ Chinotto_Backdoor_Technical_Analysis_of_the_APT_Reapers_Powerful.pdf
│ │ Dragon Messenger_APT_Group123.pdf
│ │ ESRC-1808-TLP-White-IR002_RocketMan_English.pdf
│ │ README.MD
│ │ ScarCruft (APT37) active in South Korea.pdf
│ │ special-ioc.txt
│ │ Stairwell-threat-report-The-ink-stained-trail-of-GOLDBACKDOOR.pdf
│ │
│ └─IEexploit202212sample
│ infected.zip
│ README.MD
│ RTF-infected.zip
│
├─iLOBleed
│ Implant.ARM_.iLOBleed.a-en.pdf
│ README.MD
│
├─information_operations
│ │ readme.md
│ │
│ └─Empire_Dragon
│ Empire Dragon.pdf
│ readme.md
│
├─Intellexa
│ └─Predator Files
│ ACT1072452023ENGLISH.pdf
│ readme.md
│
├─International Strategic
│ ├─Australia
│ │ critical-infrastructure-resilience-strategy-2023.pdf
│ │ README.MD
│ │
│ ├─China
│ │ 2023-02-bfv-cyber-brief-en.pdf
│ │ Charting China’s Climb as a Leading Global Cyber Power.pdf
│ │ china-cyber-report.pdf
│ │ chinese_darkweb_analysis.pdf
│ │ README.MD
│ │ RedFoxtrot_group.pdf
│ │ TAG-74.pdf
│ │
│ ├─European
│ │ README.MD
│ │
│ ├─India
│ │ Linking_South_Asian_cyber_espionnage_groups-to-publish.pdf
│ │ modified-elephant-apt.pdf
│ │ README.MD
│ │
│ ├─Iran
│ │ APT42_Crooked_Charms_Cons_and_Compromises.pdf
│ │ Bitdefender-PR-Whitepaper-EyeSpyVPN-creat625-en-EN.pdf
│ │ ClearSky-Fox-Kitten-Campaign-v1.pdf
│ │ Iran internal Politics and USPolicy.pdf
│ │ Iranian-Nation-State-APT-Leak-Analysis-and-Overview.pdf
│ │ README.MD
│ │ Saudi-Arabia-CNA-report.pdf
│ │
│ ├─Korea
│ │ │ author-name-jeff.png
│ │ │ Crypto Country North Korea’s Targeting of Cryptocurrency.pdf
│ │ │ dprk.png
│ │ │ DrillMalware-ioc.MD
│ │ │ HighSpeed-shellcode.png
│ │ │ North Korea’s Cyber Strategy.pdf
│ │ │ README.MD
│ │ │ US-Army-report-on-North-Korean-military.pdf
│ │ │
│ │ └─usa-catch
│ │ 6583f0cfa4f9191595d0543243d949420051418b80955956da5b9906ccae8b6f
│ │ korean0512(infected).zip
│ │ North Korean(infected).zip
│ │ README.MD
│ │
│ ├─LATAM
│ │ Looking-into-TUTs-tomb-the-universe-of-threats-in-LATAM.pdf
│ │ readme.md
│ │
│ ├─Russia
│ │ │ 230802_Disinformation_FrancophoneAfrica.pdf
│ │ │ Advisory-APT29-targets-COVID-19-vaccine-development.pdf
│ │ │ APT-Ecosystem-master.zip
│ │ │ A_year_of_Russian_hybrid_warfare_in_Ukraine_MS_Threat_Intelligence.pdf
│ │ │ CSA_DROVORUB_RUSSIAN_GRU_MALWARE_AUG_2020.pdf
│ │ │ fronton-report.pdf
│ │ │ google_fog_of_war_research_report.pdf
│ │ │ graphika_report_summit_old_summit_new.pdf
│ │ │ README.MD
│ │ │ remediation-hardening-strategies-for-m365-defend-against-apt29-white-paper.pdf
│ │ │ RussianAPTDetector.7z
│ │ │ Russia’s Cyber Tactics Lessons Learned 2022.pdf
│ │ │ Sahel-Gabon-Coup-Playbook-PDF.pdf
│ │ │
│ │ ├─gamaredon
│ │ │ detect.yar
│ │ │
│ │ ├─GoldenChickens
│ │ │ README.MD
│ │ │ Unmasking_VenomSpider_Report-Final.pdf
│ │ │
│ │ └─Vulkan
│ │ amezit.pdf
│ │ krystal2v.pdf
│ │ README.MD
│ │ sandworm.pdf
│ │ scanv_1.pdf
│ │ scanv_2.pdf
│ │ scanv_3.pdf
│ │ scanv_4.pdf
│ │
│ ├─SouthAsia
│ │ README.MD
│ │ 南亚地区APT组织2019年度攻击活动总结.pdf
│ │
│ ├─Ukraine
│ │ IT_Army_of_Ukraine_In_Depth_Analysis_on_The_Roles_of_Threat_Actors.pdf
│ │ README.MD
│ │ Ukraine-Report-Q1_2023.pdf
│ │
│ ├─USA
│ │ │ README.MD
│ │ │
│ │ ├─2023
│ │ │ FINAL FINAL Safeguarding the US Space Industry - Digital.pdf
│ │ │ National-Cybersecurity-Strategy-2023.pdf
│ │ │ README.MD
│ │ │
│ │ └─Triangulation
│ │ 64f36b0b8ef62634a3ec15b4a21700d32b3d950a846daef5661b8bbca01789dc
│ │ 7e779a019f250d8cec9761d1230296236a8b714743df42c49ce8daf818d542e7
│ │ c2393fceab76776e19848c2ca3c84bea0ed224ac53206c48f1c5fd525ef66306
│ │ fd9e97cfb55f9cfb5d3e1388f712edd952d902f23a583826ebe55e9e322f730f
│ │ ff2f223542bbc243c1e7c6807e4c80ddad45005bcd78a77f8ec91de29deb2f6e
│ │ readme.md
│ │
│ └─Vietnam
│ Docless Vietnam APT.pdf
│ README.MD
│ WithSecure-Meet-the-ducks.pdf
│ WithSecure_Research_DUCKTAIL.pdf
│
├─kimsuky
│ │ 2022-Threat-Trend-Report-on-Kimsuky.pdf
│ │ 20231016_threat_inteligence_report_DarkHorse.pdf
│ │ 20231101_Kimsuky_OP.-Covert-Stalker-EN.pdf
│ │ ATIP_2023_Feb_Threat-Trend-Report-on-Kimsuky-Group.pdf
│ │ Joint_CSA_NK_Using_Social_Engineering_20230531.pdf
│ │ Kimsuky APT Group targeted on South Korean defense and security departments.pdf
│ │ kimsuky-2023-03-20-joint-cyber-security-advisory.pdf
│ │ kimsuky-doc
│ │ Kimsuky-KGH.pdf
│ │ kimsuky-note.txt
│ │ Operation_Newton_Kimsuky-APPLE(SEED).pdf
│ │ README.MD
│ │ Smoke Screen.pdf
│ │ Unveil the evolution of Kimsuky targeting Android device with newly discovered mobile malware.xlsx
│ │
│ └─monthreport
│ ATIP_2023_May_Threat-Trend-Report-on-Kimsuky-Group.pdf
│ readme.md
│
├─konni
│ 20230727_threat_inteligence_report_Konni.pdf
│ 20230926_threat_inteligence_report_konniapt.pdf
│ bluesky.txt
│ konni related kimsuky.png
│ konni-threat-insight-paper-triple-threat-N-Korea-aligned-TA406-steals-scams-spies.pdf
│ konni_ioclist_202111.csv
│ ReadME.md
│ the-konni-apt-chronicle-tracing-their-intelligence-driven-attack-chain.pdf
│
├─Lamberts
│ │ README.MD
│ │
│ └─DePriMon
│ README.MD
│
├─lazarus
│ │ 20231013_Lazarus_OP.Dream_Magic.pdf
│ │ C2_Communication_of_ThreatNeedle.pdf
│ │ CryptoCore-Lazarus-Clearsky.pdf
│ │ Dream-Job-Campaign.pdf
│ │ Dtrack RAT.zip
│ │ kaspersky-ics-cert-lazarus-targets-defense-industry-with-threatneedle-en-20210225.pdf
│ │ Lazarus Group Recruitment_ Threat Hunters vs Head Hunters.pdf
│ │ lazarus-powershell.zip
│ │ lazarus-threat-intel-report2.pdf
│ │ multiple campaigns of the Lazarus group and their connections.pdf
│ │ Operation-Blockbuster-Report.pdf
│ │ README.MD
│ │ The Nightmare of Global Cryptocurrency Companies DangerousPassword of the APT Organization.pdf
│ │ The_Lazarus_Constellation.pdf
│ │ uscert.txt
│ │ WithSecure-Lazarus-No-Pineapple-Threat-Intelligence-Report-2023.pdf
│ │
│ ├─3CXSupplyChain
│ │ NCSC_MAR-Smooth-Operator.pdf
│ │ README.MD
│ │
│ ├─MATA
│ │ readme.md
│ │ Updated-MATA-attacks-Eastern-Europe_full-report_ENG.pdf
│ │
│ └─sample
│ 9454715b9081323f525970dae9c37e9d
│ README.MD
│
├─londonblue
│ london-blue-april-2019.pdf
│
├─Machete
│ ESET_Machete.pdf
│ README.MD
│
├─Magecart
│ README.MD
│
├─Metador
│ metador_An_Unattributed_Threat_Hiding_in_Telcos_SPs_and_Universities.pdf
│ README.MD
│
├─mobile-APT
│ mobile-APT-threat-report.pdf
│ Readme.md
│
├─Molerats
│ README.MD
│ Welcome-Chat.txt
│
├─muddywater
│ │ Clearsky-Iranian-APT-group-‘MuddyWater’-Adds-Exploits-to-Their-Arsenal.pdf
│ │ Iranian intel cyber suite of malware uses open source tools.pdf
│ │ muddyc3.zip
│ │ README.MD
│ │ wp_new_muddywater_findings_uncovered.pdf
│ │
│ └─greenleaker
│ GreenLeaker(blackorbird).zip
│ README.MD
│
├─nazar
│ apt_ZZ_Sig37_NAZAR.yara.txt
│ nazar-sample(infected).zip
│ python-server.txt
│ README.MD
│
├─NSOGroup
│ │ Memo-Citizen-Lab-Raymundo-Ramos-230304.pdf
│ │ README.MD
│ │ Six Palestinian human rights defenders hacked with.pdf
│ │ VB2022-Exploit-archaeology-a-forensic-history-of-in-the-wild-NSO-Group-exploits.pdf
│ │
│ └─Morocco
│ article_3.pdf
│ ExoneratingMorocco-DisprovingTheSpyware.pdf
│ README.MD
│
├─Oceanlotus
│ │ APT32-Graph-Deobfuscator.py
│ │ apt32_report_2019.pdf
│ │ aptnote0402
│ │ aptnote20190409
│ │ ESET_OceanLotus.pdf
│ │ hunting-rule.txt
│ │ OceanLotus' Attacks to Indochinese Peninsula Evolution of Targets, Techniques and Procedure.pdf
│ │ Oceanlotus-APK-sample.TXT
│ │ OceanLotus-Steganography-Malware-Analysis-White-Paper.pdf
│ │ oceanlotus_png_loader.yar
│ │ OL_OSX_decryptor.py
│ │ png_decode.py
│ │ README.MD
│ │ Stairwell-threat-report-The-origin-of-APT32-macros.pdf
│ │
│ └─sample
│ 233.zip
│ Documents to be signed on One Belt One Road Forum.zip
│ Oceanlotus-apk(infected).zip
│ README.MD
│ thaydoinoidegiaydep.zip
│ wwlib.dll_000176573_c__programdata_Intel.dll
│ wwlib.dll_000176573_c__programdata_Offices.dll
│
├─Osint
│ Arastirma-KitiPriviaSecurity.pdf
│ README.MD
│
├─Patchwork
│ README.MD
│
├─phpstudyGhost
│ README.MD
│
├─Sandworm
│ Appendix_Cyclops Blink Sets Sights on ASUS Routers.pdf
│ Clearing the Fog of War A Critical Analysis of Recent Energy Sector Attacks in Denmark and Ukraine.pdf
│ Cyclops-Blink-Malware-Analysis-Report.pdf
│ NCSC-MAR-Infamous-Chisel.pdf
│ README.MD
│ russia-nexus-uac-0113-emulating-telecommunication-providers-in-ukraine.pdf
│ SBU exposes russian intelligence attempts to penetrate Armed Forces' planning operations system.pdf
│ sektorcert-angrebet-mod-dansk-kritisk-infrastruktur-tlp-clear-en.pdf
│ Validation-script_Cyclops-Blink-Sets-Sights-on-Asus-Routers-n2HqxTq.txt
│ Активність угруповання.pdf
│
├─Seaturtle
│ readme.md
│
├─SideCopy
│ Hashes_IOCs_for_coverage.txt
│ Network_IOCs_list_for_coverage.txt
│ README.MD
│ SideCopy.pdf
│
├─sidewinder
│ 0daefb3d05e4455b590da122255121079e83d48763509b0688e0079ab5d48886
│ 135cb239966835fefbb346165b140f584848c00c4b6a724ce122de7d999a3251
│ global-perspective-of-the-sidewinder-apt.pdf
│ readme.md
│ sidewinder-apk.rar
│
├─simjacker
│ AdaptiveMobile_Security_Simjacker_Technical_Paper.pdf
│ README.MD
│
├─StrongPity
│ README.MD
│
├─summary
│ ├─2020
│ │ APT-blackberry-mobile-malware-report.pdf
│ │ ESET_Threat_Report_Q22020.pdf
│ │ Estonian-Foreign-Intelligence-raport-2020-en.pdf
│ │ PWC-cyber-threats-2019-retrospect.pdf
│ │ README.MD
│ │ tencent-apt_report_2019.pdf
│ │
│ ├─2021
│ │ 2020-2021-cyber-espionage-report.pdf
│ │ 2021 Threat Predictions Report _ McAfee Blogs.pdf
│ │ 2021(APT) Microsoft Digital Defense Report.pdf
│ │ 2021-Threat-Detection-Report.pdf
│ │ Adversary Infrastructure Report 2020.pdf
│ │ APT group activities under the shadow of the epidemic(2020).pdf
│ │ apt28-northkorean-blackmatter.pdf
│ │ Cloud_Native_Threat_Report_2021.pdf
│ │ eset_threat_report_t12021.pdf
│ │ Global APT Research Report for the first half of 2021-360.pdf
│ │ Google_Cybersecurity_Action_Team_Threat_Horizons_Report#1.pdf
│ │ Looking back on the incidents in 2020_JPCERT_en.pdf
│ │ mpressioncss_ta_report_2020_5_en.pdf
│ │ Offensive-Cyber-Capabilities-Proliferation-Report.pdf
│ │ README.MD
│ │ rpt-mtrends-2021-fireeye.pdf
│ │ rpt-security-predictions-2021-fireeye.pdf
│ │ rpt-turn-the-tide-trend-micro-security-predictions-for-2021.pdf
│ │ sophos-2021-threat-report.pdf
│ │ The CrowdStrike 2021 Global Threat Report.pdf
│ │ wp-cyber-threat-predictions-for-2021-fortinet.pdf
│ │ Yoroi_Cybersecurity_Annual_-Security_Report_2020-ENGLISH_rMT-FINAL-1s.pdf
│ │
│ └─2022
│ 2021 Advanced Threat Trends Research Report-dbappsecurity.pdf
│ 2021 Adversary Infrastructure Report.pdf
│ 2021 Vulnerability Landscape.pdf
│ 2021-Malware-Report-Resecurity.pdf
│ 2021-NCC-Group-Annual-Research-Report.pdf
│ 2021_Year_in_Cybersecurity_Lessons_and_Plans_for_2022.pdf
│ 2022 Adversary Infrastructure Report.pdf
│ 2022 Global Crime Trend Summary Report.pdf
│ 2022 Global Threat Report.pdf
│ 2022-Apr-Ransomware-Report-v3.pdf
│ 2022-unit42-incident-response-report-final.pdf
│ 2022-Yoroi_Cybersecurity_Annual_Report.pdf
│
├─SunBurst
│ Nobelium2021.pdf
│ README.MD
│ SilverFish_Solarwinds.pdf
│
├─Tools
│ └─Builder
│ blackhats2019.zip
│ README.MD
│
├─Tortoiseshell
│ README.MD
│ tortoiseshell.zip
│
├─TransparentTribe
│ README.MD
│ transparent-tribe-threat-insight-en2020.pdf
│
├─Turla
│ │ aa23-129a_snake_malware_2.pdf
│ │ APT_MAL_LNX_Turla_Apr202004_1.yara
│ │ APT_MAL_LNX_Turla_Apr202004_1_opcode.yara
│ │ IOC.TXT
│ │ Malware Technical Insight _Turla “Penquin_x64”.pdf
│ │ README.MD。
│ │ turla2020(infected).zip
│ │
│ ├─2014
│ │ cd00r.c
│ │ README.MD
│ │
│ └─2017
│ Penquins_Moonlit_Maze_AppendixB.pdf
│ Penquins_Moonlit_Maze_PDF_eng.pdf
│ PENQUIN_MOONLIT_MAZE.yara
│ README.MD
│
├─UNC****
│ │ readme.md
│ │
│ ├─UNC3347
│ │ GroundPeony_Crawling_with_Malice.pdf
│ │ readme.md
│ │
│ └─UNC4841
│ readme.md
│
├─WhiteCompany
│ README.MD
│ WhiteCompanyOperationShaheenReport.pdf
│
├─Winnti
│ README.MD
│ winnti-apt-group-docks-in-sri-lanka-for-new-campaign-final.pdf
│
├─Wizard Spider
│ README.MD
│ WizardSpider_TLPWHITE_v.1.4.pdf
│
└─ZooPark
README.MD
ZooPark_for_public_final_edited.pdf
部分APT组织名称
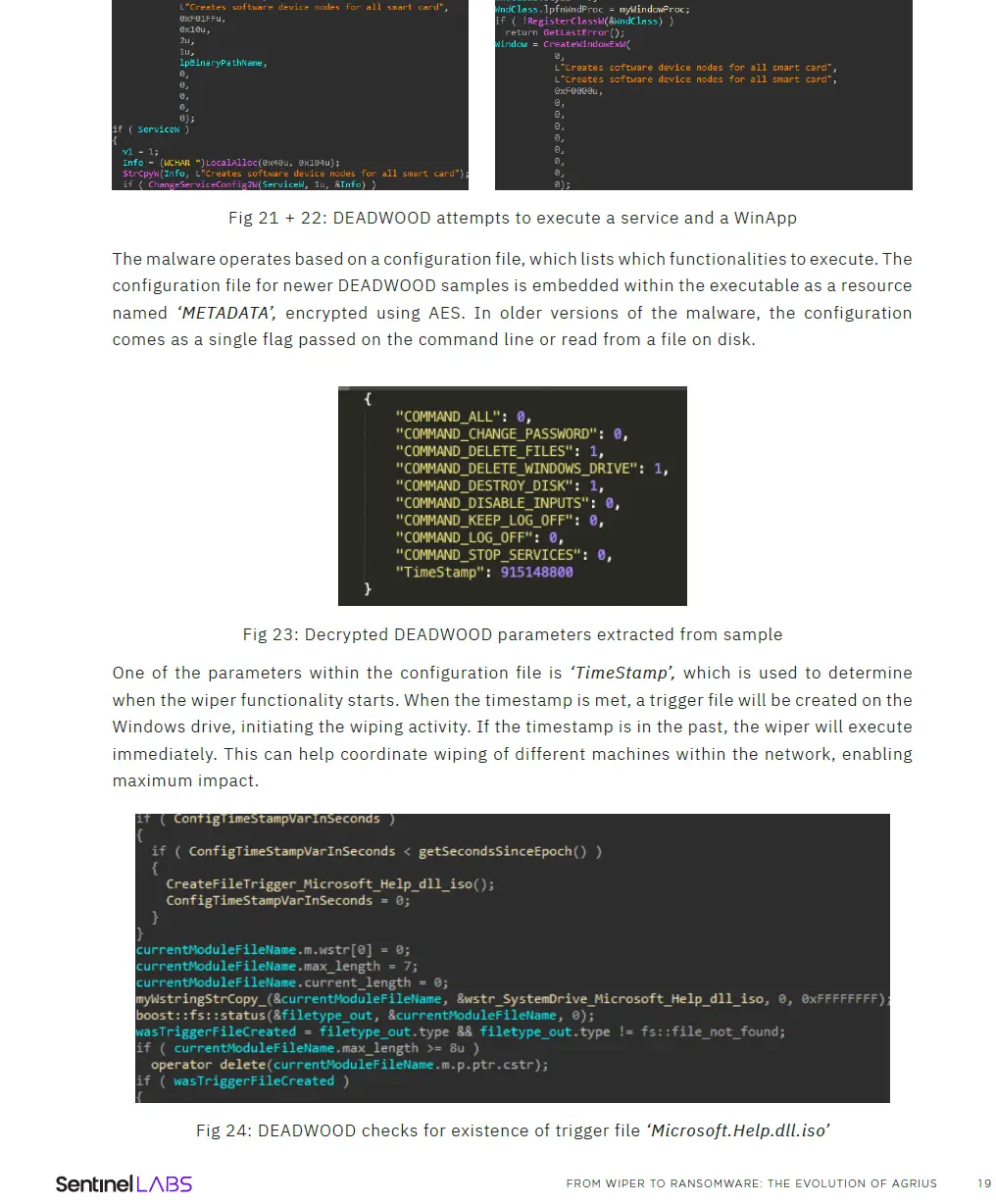
Comment Crew,APT2,UPS,IXESHE,APT16,Hidden Lynx,Wekby,Axiom,Winnti Group,Shell Crew,Naikon,Lotus Blossom,APT6,APT26,Mirage,NetTraveler,Ice Fog,Beijing Group,APT22,Suckfly,APT4,Pitty Tiger,Scarlet Mimic,C0d0so,SVCMONDR,Wisp Team,Mana Team,TEMP.Zhenbao,SPIVY,Mofang,DragonOK,Group 27,Tonto Team,TA459,Tick,Lucky Cat,APT40,PassCV,BARIUM,LEAD,Iron Group,Anchor Panda,Aquatic Panda,Big Panda,Electric Panda,Eloquent Panda,Emissary Panda,Foxy Panda,Gibberish Panda,Goblin Panda,Hammer Panda,Hurricane Panda,Impersonating Panda,Judgement Panda,Karma Panda,Keyhole Panda,Kryptonite Panda,Mustang Panda,Night Dragon,Nightshade Panda,Nomad Panda,Pale Panda,Pirate Panda,Poisonous Panda,Predator Panda,Radio Panda,Sabre Panda,Spicy Panda,Stone Panda,Temper Panda,Test Panda,Toxic Panda,Twisted Panda,Union Panda,Vicious Panda,Violin Panda,Wet Panda,?,?,?,?,?,Calypso,Tropic Trooper,APT41,Poison Carp,AVIVORE,APT-C-01,DarkUniverse,Taskmasters,GALLIUM,RANCOR,ChinaZ,APT-C-37,APT-C-27,Storm Cloud,TA410,SixLittleMonkeys,HAFNIUM,Luminous Moth,Spiral,Sparkling Goblin,APT5,RedFoxtrot ,IronHusky,Antlion,DEV-0322,Curious Gorge,Scarab,BackdoorDiplomacy,Earth Berberoka,RedAlpha,Bluebottle,DragonSpark,Yanluowang,LuoYu,Aoqin Dragon,Earth Yako,Dark,Sofacy,APT29,Turla Group ,Energetic Bear,Sandworm,FIN7,FIN8,Inception Framework,TeamSpy Crew,BuhTrap,Carberb,???,FSB 16th & 18th Centers,Cyber Berkut,WhiteBear,???,GRU GTsST (Main Center for Special Technology),TEMP.Veles,Zebrocy,SectorJ04,FullofDeep,RedCurl,TA551,UNC2452,Ember Bear,COLDRIVER,Vice Society,Karakurt,Cyber Spetsnazs,Royal,Revil,Lazarus Group,APT37,Andariel,Kimsuki,NoName,OnionDog,TEMP.Hermit,?,Stardust Chollima,APT43,Cutting Kitten,Shamoon,Clever Kitten,Madi,Cyber fighters of Izz Ad-Din Al Qassam,Chafer,Prince of Persia,Sima,Oilrig,CopyKittens,Charming Kitten,Greenbug ,Magic Hound,Rocket Kitten,?,ITSecTeam,MuddyWater,Mabna Institute,DarkHydrus ,Domestic Kitten,Flash Kitten,Gold lowell,Iridium,DNSpionage,Tortoiseshell,?,Fox Kitten,Tracer KItten,Agrius,MalKamak,Nemesis Kitten,UNC3313,DEV-0343,APT42 ,HomeLand Justice,Emennet Pasargad,Predatory Sparrow,Bohrium,Unit 8200,Unit 8200,SunFlower,GOSSIPGIRL,Equation Group,Lamberts,Snowglobe,Slingshot,?,Sea Turtle,Molerats,AridViper,Volatile Cedar,Syrian Electronic Army (SEA),Cyber Caliphate Army (CCA),Ghost Jackal,Corsair Jackal,Extreme Jackal,Electric Powder,APT-C-23,APT-C-27,Dark Caracal,Tempting Cedar,?,Sandcat,Group WITRE,ZooPark,APT-C-37,POLONIUM,BackdoorDiplomacy,Corsair Jackal,The Mask,El Machete,Patchwork,Hellsing APT,Wild Neutron,Sykipot ,Platinum,Danti,SVCMONDR,Transparent Tribe,APT32,BlackOasis,NEODYMIUM,PROMETHIUM,Andromeda Spider,Bamboo Spider,Boson Spider,Cobalt Spider,Dextorous Spider,Dungeon Spider,Grim Spider,Hound Spider,Indrik Spider,Lunar Spider,Magnetic Spider,Mimic Spider,Monty Spider,Mummy Spider,Overlord Spider,Pinchy Spider,Pizzo Spider,Shark Spider,Singing Spider,Skeleton Spider,Static Spider,Union Spider,Wicked Spider,Wizard Spider,Wold Spider,Zombie Spider,Curious Jackal,Extreme Jackal,Gekko Jackal,Shifty Jackal,Mythic Leopard,GravityRAT,SilverTerrier,InvisiMole,SideWinder ,Blackgear,Gorgon Group,Donot Team,Nomadic Octopus,Anunak,TA505(merged w/Indrik Spider),TA544,TA551,TA555,Blind Eagle,Bitter,Bahamut,WindShift,EmpireMonkey,Pacha Group,DNSpionage,PLATINUM,GreyEnergy Group,TA516,TA564,TA543,TA545,TA2101,Evilnum,Golden Chickens,IamtheKing,UNC1945,APT-C-44,DarkHotel,UNC1151,ModifiedElephant,STIBNITE,Scattered Spider,Crouching Yeti,NewRomanic Cyber Army Team ,The Whois Hacking Team,ItaDuke,Roaming Tiger,Blue Termite,Suckfly,?,SPIVY,EvilPost,Danti,?,Evanescent Bat,NewsBeef,Poseidon,Ghoul,FruityArmor,Snake Wine,APT5,Sowbug,Triton,?,Orangeworm,FIN10,BlackTech,White Company,Silence Group,Whitefly,Roaming Mantis,LYCEUM,APT-C-37,APT-C-38,Storm Cloud,Chimera,AcidBox,FIN12,White Tur,Keksec,BlueHornet,Worok,GhostSec,NB65,Winter Vivern部分文件截图

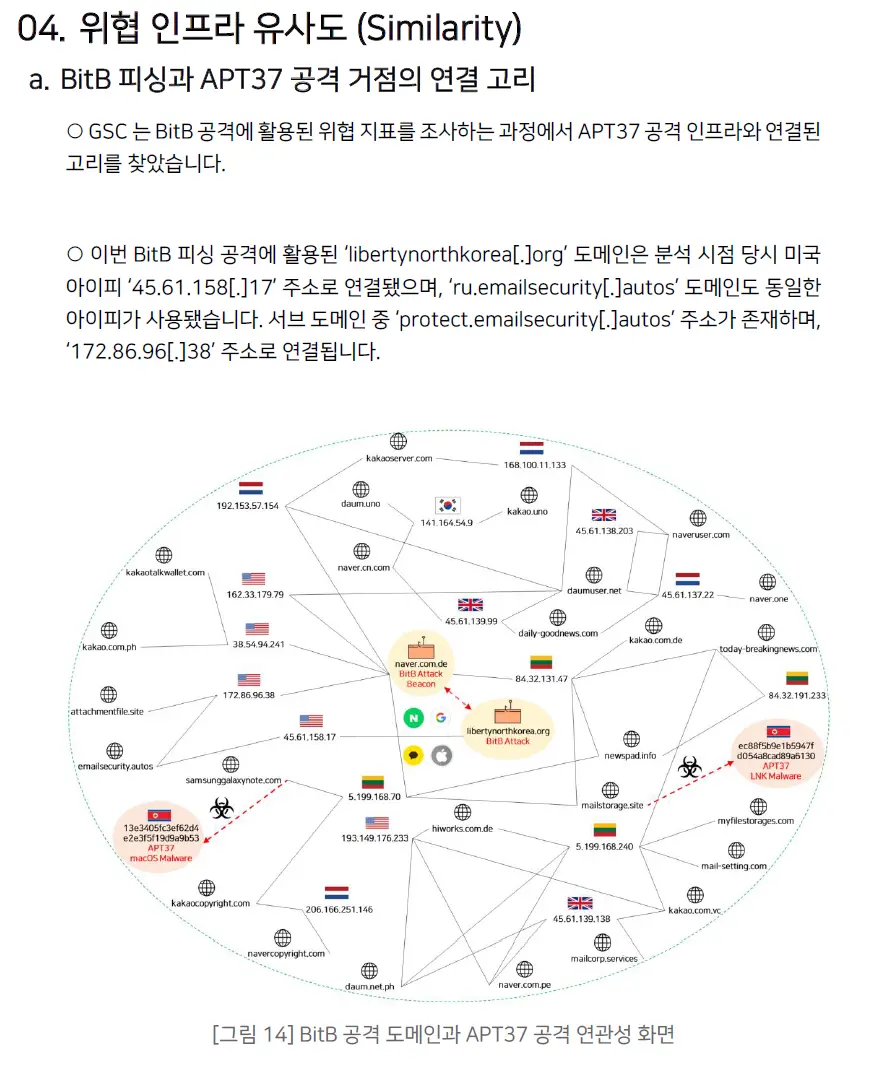
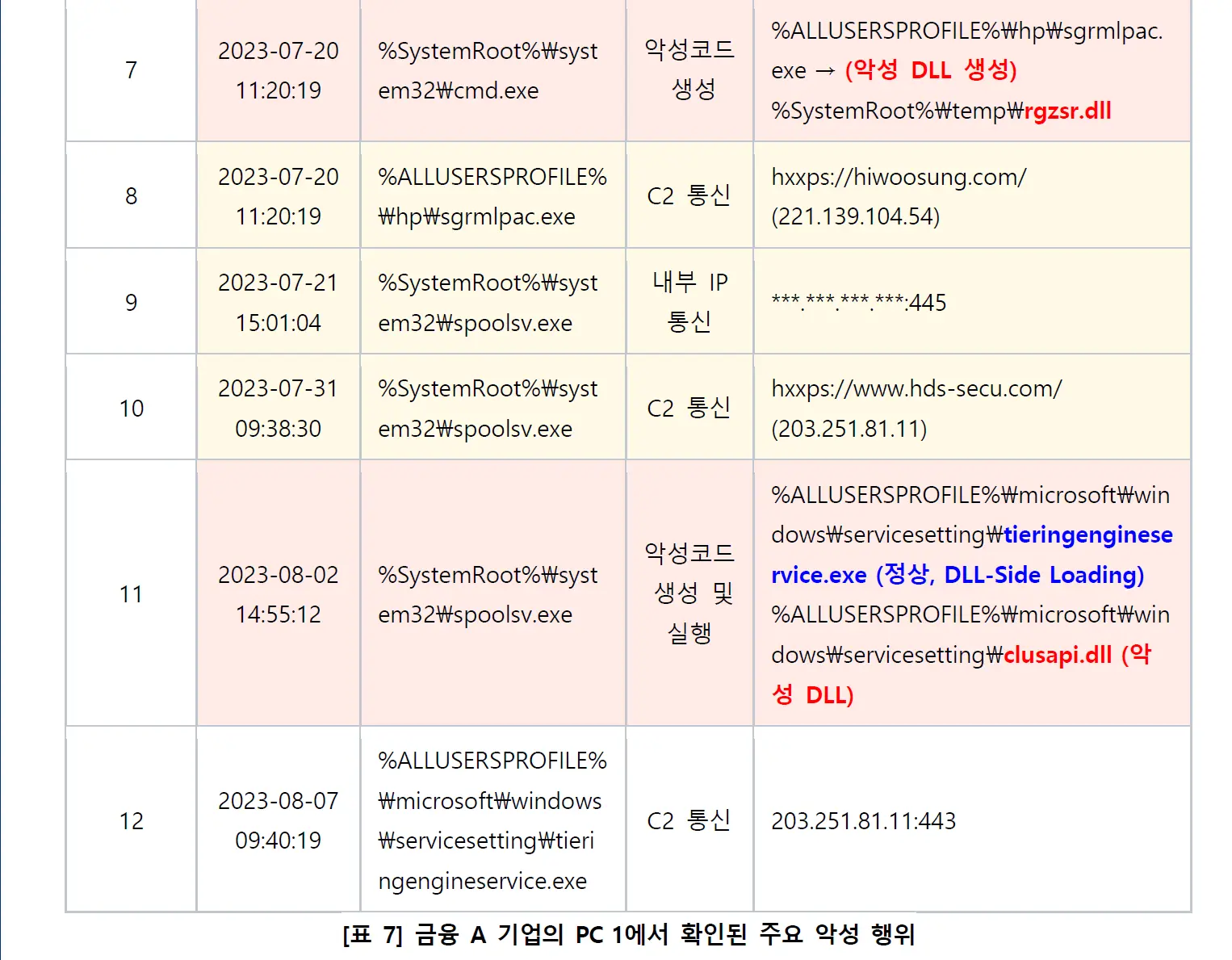
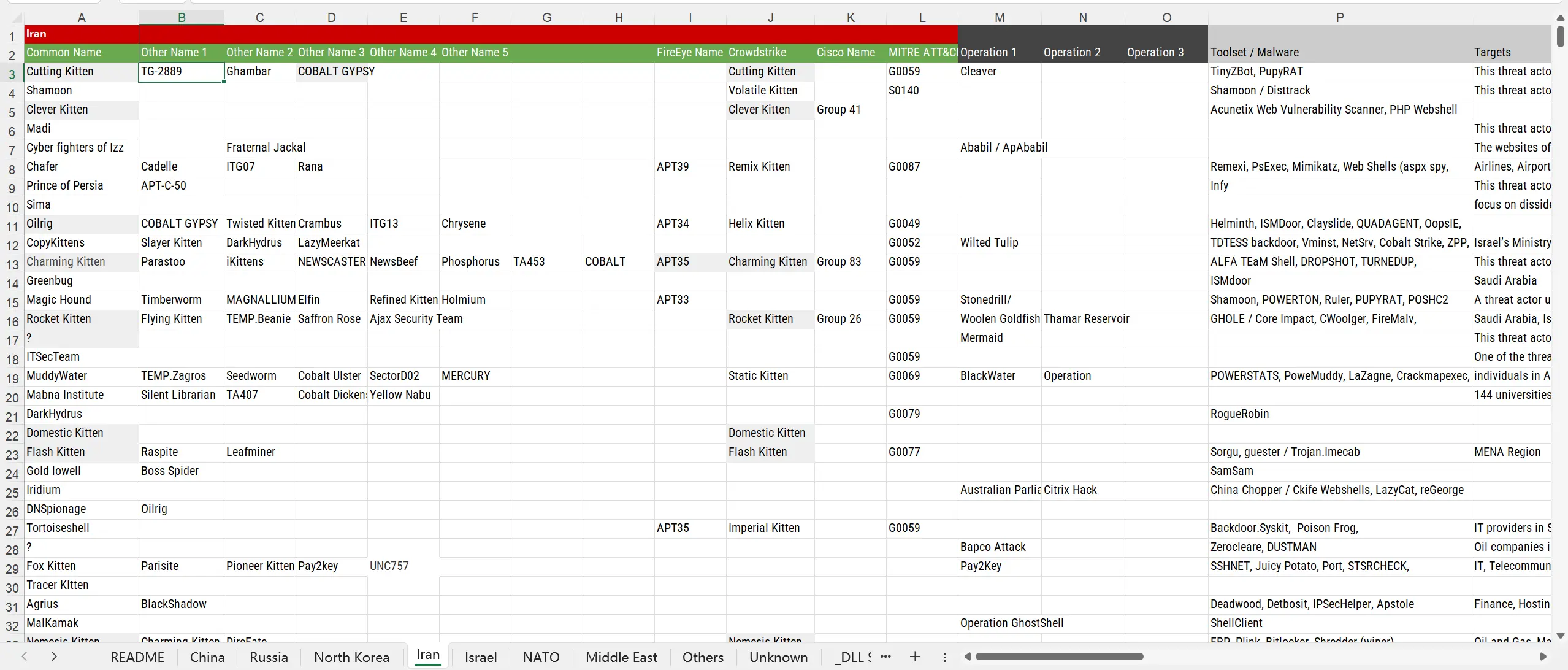
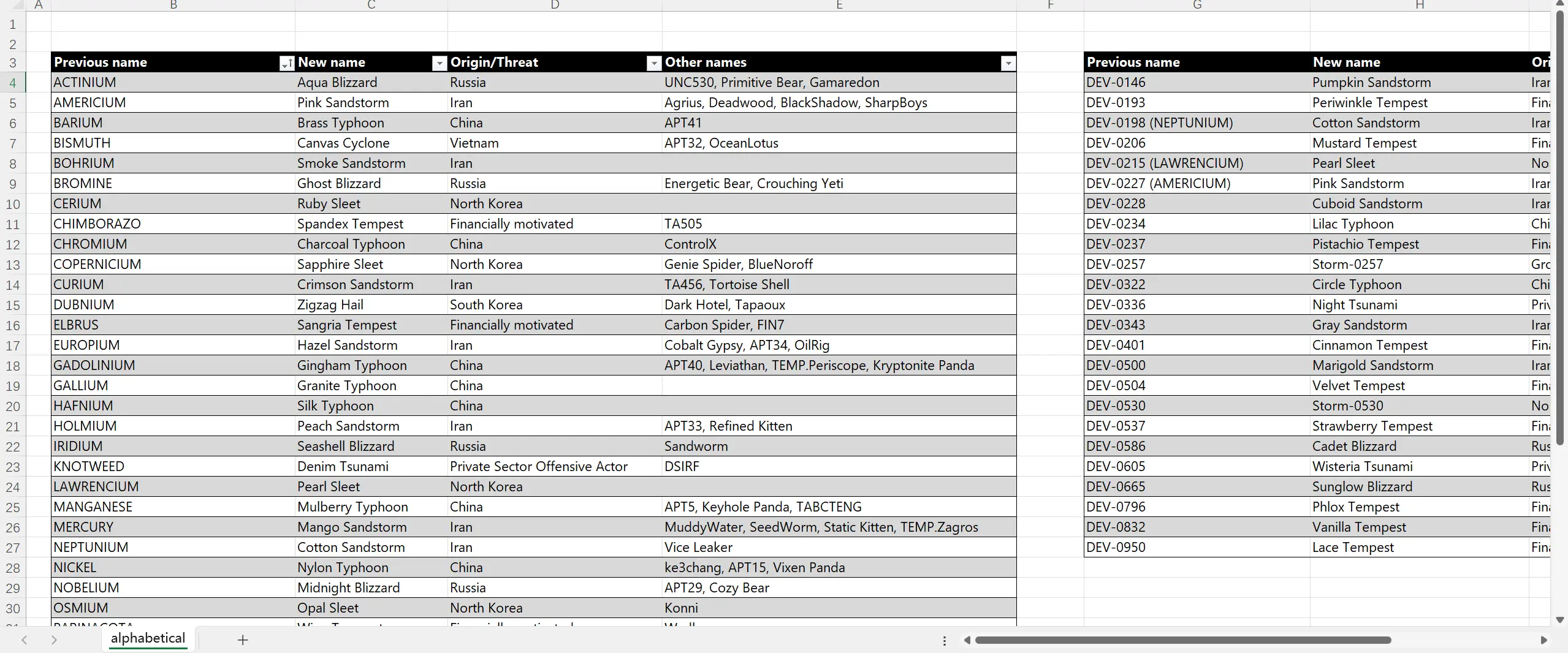
项目地址
GitHub:
https://github.com/blackorbird
下载地址
https://github.com/blackorbird/APT_REPORT
转载请注明出处及链接