目录导航
关于Awvs扫描器请参考往期文章
http://www.ddosi.org/?s=awvs
acunetix_13.0.200807156更新日志
更新日期:2020年8月10日
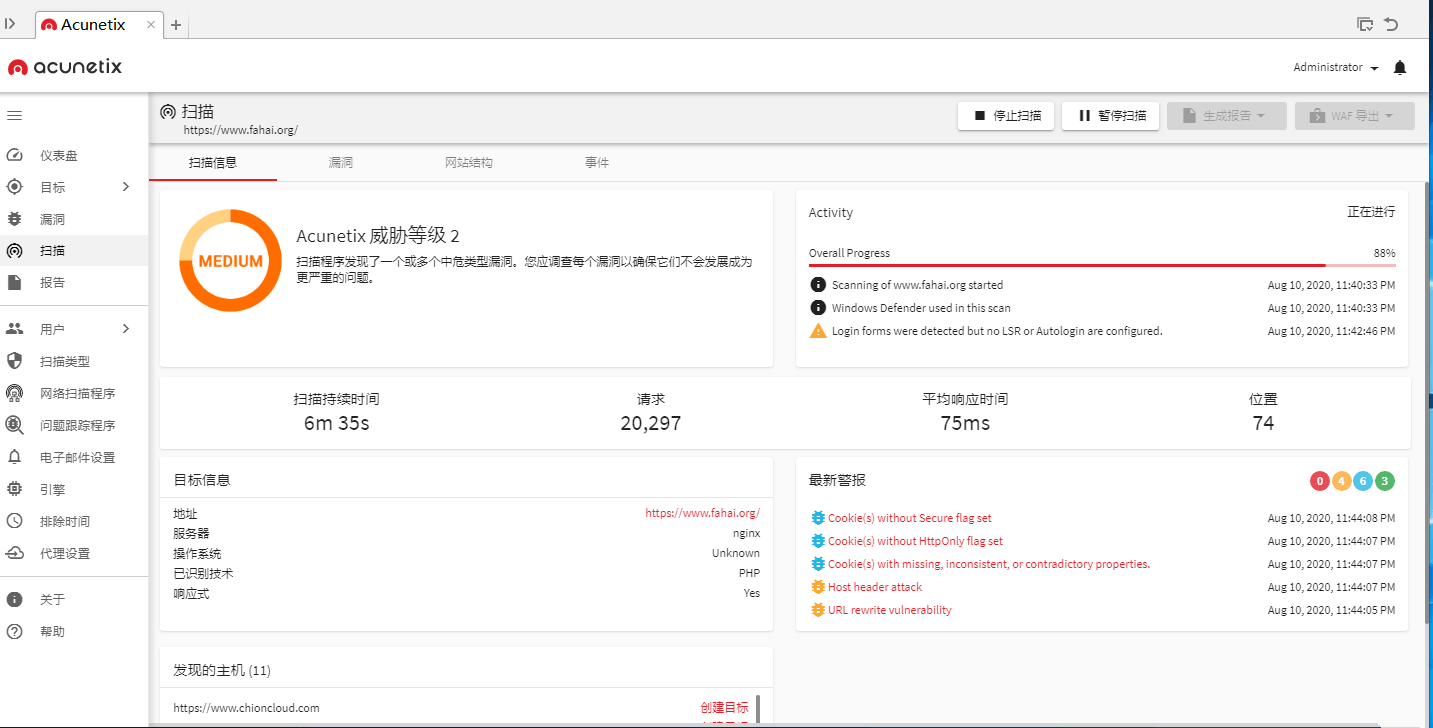
已针对Windows和Linux发布了新的Acunetix更新:13.0.200807155和macOS:13.0.200807156。
此Acunetix更新在UI中引入了中文支持,从而使Acunetix的中国用户可以浏览Acunetix UI并以其语言读取漏洞数据。新版本显示了扫描站点结构中的路径片段,并引入了针对Rails,SAP NetWeaver,Atlassian Jira等的新漏洞检查。此外,还有大量更新和修补程序,所有版本和更新都可用于Acunetix的所有版本。
新功能
- Acunetix现在提供简体中文版本
- 路径片段现在显示在站点结构中
新的漏洞检查
- 不安全的嵌入式框架的新检查
- 新检查在Rails中远程执行用户提供的本地名称的代码
- SAP NetWeaver RECON身份验证绕过漏洞的新检查
- H2控制台的新检查可公开访问
- PHP版本公开的新检查
- Atlassian Jira Service Desk错误配置的新检查
- 针对Jolokia XML外部实体(XXE)漏洞的新测试
- WordPress核心,WordPress主题,WordPress插件,Joomla和Drupal的新检查
更新
- 创建日期和上次更新日期适用于漏洞
- 比较报告中各节的顺序已更新,更加直观
- 目标地址在UI中完整显示
- 在/用户/端点现在是API中
bug修复
- 修复了包含CVSS3.1的漏洞导出到WAF时的问题
- 修复了导致自定义用户代理在扫描期间未在所有请求中使用的问题
- 修复了导致某些漏洞在发送到Jira问题跟踪器时无法正确格式化的问题
- 修复了在Acunetix Online中添加Jira问题跟踪器时的问题
- 修复了将目标添加到现有目标组时导致的问题
- 综合报告文本中的次要修复
- 修复了使用浏览器后退按钮时显示空白列表(扫描,目标等)的UI问题
- 修复了由扫描具有复杂GraphQL模式的目标引起的问题
更新日志详情查看官网:
https://www.acunetix.com/blog/releases
acunetix_13.0.200807156目前能扫描的漏洞列表
漏洞英文列表
All checks
│───Scanning tests
│ │───File tests
│ │ │───Hidden, obsolete and backup copies of files
│ │ │───Bash remote code execution (ShellShock)
│ │ │───HTML form in redirect page
│ │ │───AJAX hashbang search
│ │ │───JavaScript Abstract Syntax Tree parser
│ │ │───JavaScript libraries audit
│ │ │───PHP SuperGlobals Overwrite
│ │ │───RESTful web service discovery and audit (per file)
│ │ │───Relative Path Overwrite
│ │ │───File Information Disclosure text search
│ │ │───XSS in file URI
│ │ │───XXE in file URI
│ │ │───Apache Tomcat Information Disclosure
│ │ │───Spring Data REST Remote Code Execution
│───│───Directory tests
│ │ │───PHP APC audit
│ │ │───ASP.NET application trace
│ │ │───ASP.NET debugging enabled
│ │ │───ASP.NET diagnostic page
│ │ │───Access Database Search
│ │ │───Apache Solr audit
│ │ │───Apache Tomcat Windows directory traversal
│ │ │───Hidden, obsolete and backup copies of directories
│ │ │───HTTP Basic Authentication over HTTP
│ │ │───Bazaar repository
│ │ │───CVS repository
│ │ │───Core dump (memory dump) search
│ │ │───Development files
│ │ │───Directory listing
│ │ │───Dreamweaver scripts
│ │ │───Git repository
│ │ │───Grails database console
│ │ │───HTML form in redirect directory
│ │ │───HTTP verb tampering
│ │ │───Microsoft IIS Directory Authentication bypass
│ │ │───Invalid page text search
│ │ │───JetBrains .idea project directory
│ │ │───Mercurial repository
│ │ │───Exposed phpinfo()
│ │ │───Possible sensitive directories
│ │ │───Possible sensitive files
│ │ │───RESTful web service discovery and audit (per directory)
│ │ │───README Files
│ │ │───SFTP credentials exposure
│ │ │───SQL Injection in HTTP Basic Authentication
│ │ │───SQL Injection in URI
│ │ │───SQLite database search
│ │ │───SVN repository
│ │ │───Sensitive files
│ │ │───Directory Information Disclosure text search
│ │ │───Web-shell search
│ │ │───WS_FTP.LOG Information Disclosure
│ │ │───Weak HTTP Basic authentication password
│ │ │───Webadmin search
│ │ │───XSS in directory URI
│ │ │───XXE in directory URI
│ │ │───.htaccess file readable
│ │ │───DEADJOE file
│ │ │───Symfony databases.yml
│ │ │───Dotenv file
│ │ │───Spring Boot Actuator version 2
│ │ │───Spring Boot WhiteLabel Error Page SpEL
│ │ │───Nginx Path Traversal via misconfigured alias
│ │ │───Spring Security Authentication Bypass
│ │ │
│───│───Input scheme tests
│ │ │───ASP code injection
│ │ │───Analyze HTTP request parameter values
│ │ │───Arbitrary file creation
│ │ │───Arbitrary file deletion
│ │ │───Blind SQL Injection
│ │ │───Blind XSS
│ │ │───CRLF injection (HTTP response splitting)
│ │ │───Remote Code Execution
│ │ │───Directory Traversal On Inputs
│ │ │───Email Header Injection
│ │ │───Email (SMTP) Injection
│ │ │───Unexpected and malformed input error messages
│ │ │───Expression Language (EL) injection
│ │ │───File inclusion
│ │ │───File Tampering
│ │ │───File Upload
│ │ │───Padding Oracle
│ │ │───HTTP Parameter Pollution
│ │ │───Password Reset Poisoning
│ │ │───HTML authentication audit
│ │ │───LDAP Injection
│ │ │───Long password DoS
│ │ │───MongoDB injection
│ │ │───Server Side JavaScript Injection
│ │ │───PHP Code Injection
│ │ │───Ruby on Rails Code Injection
│ │ │───Perl Code Injection
│ │ │───User Controlled PHP vulnerabilities
│ │ │───Ruby on Rails (RoR) insecure Mass-Assignment
│ │ │───Ruby on Rails (RoR) Active Record WHERE-clause SQL Injection
│ │ │───Ruby on Rails (RoR) render inline RCE
│ │ │───Remote File Inclusion XSS
│ │ │───Source code disclosure
│ │ │───Server-side Request Forgery
│ │ │───SQL Injection
│ │ │───Apache Struts2 Remote Command Execution (S2-053)
│ │ │───Apache Struts 2.0.29 RCE
│ │ │───Unsafe preg_replace()
│ │ │───XFS and Redir
│ │ │───XML External Entity Injection (XXE)
│ │ │───XPath Injection
│ │ │───Cross-site Scripting (XSS)
│ │ │───Edge Side Include Injection (ESI Injection)
│ │ │───Java Object Deserialization
│ │ │───Python pickle serialization
│ │ │───Python code injection
│ │ │───Argument Injection
│ │ │
│───│───Server tests
│ │ │───Apache Tomcat AJP protocol audit
│ │ │───ASP.NET error message
│ │ │───ASP.NET Forms Authentication bypass
│ │ │───Apache Axis2 audit
│ │ │───Apache Geronimo default credentials audit
│ │ │───Apache HTTP Server CONNECT method enabled
│ │ │───Apache Roller audit
│ │ │───Apache HTTP Server running as a proxy
│ │ │───Apache HTTP Server mod_info audit
│ │ │───Apache Solr administration accessible
│ │ │───Apache HTTP Server unfiltered expect header injection
│ │ │───Apache HTTP Server XSS via malformed HTTP requests
│ │ │───Apache HTTP Server HttpOnly cookie disclosure
│ │ │───Apache mod_negotiation filename bruteforcing
│ │ │───Ruby on Rails Action Pack arbitrary file disclosure
│ │ │───Barracuda multiple product 'locale' directory traversal
│ │ │───Bash remote code execution (ShellShock) server audit
│ │ │───CRLF injection (HTTP response splitting) server audit
│ │ │───Clickjacking
│ │ │───clientaccesspolicy.xml audit
│ │ │───Adobe ColdFusion audit
│ │ │───ColdFusion user agent XSS
│ │ │───Adobe ColdFusion FCKEditor file upload
│ │ │───Adobe ColdFusion Solr Information Disclosure
│ │ │───Core dump (memory dump) search server audit
│ │ │───crossdomain.xml audit
│ │ │───Database backup
│ │ │───Django admin weak password audit
│ │ │───Error page path disclosure
│ │ │───Flask debug mode enabled
│ │ │───Microsoft FrontPage Server Extensions enabled
│ │ │───Microsoft FrontPage information
│ │ │───Microsoft FrontPage authors.pwd
│ │ │───Oracle GlassFish Server Directory Traversal
│ │ │───Oracle GlassFish Server audit
│ │ │───Hadoop cluster web interface
│ │ │───OpenSSL TLS heartbeat (Heartbleed) vulnerability
│ │ │───Horde IMP Webmail audit
│ │ │───IBM WebSphere audit
│ │ │───ASP Global.asa
│ │ │───IIS internal IP address
│ │ │───Microsoft IIS Unicode Directory Traversal
│ │ │───Microsoft IIS service configuration exposed
│ │ │───Microsoft IIS NTLM and HTTP Basic Authentication bypass
│ │ │───Ioncube Loader Wizard
│ │ │───Red Hat JBoss audit
│ │ │───JBoss Status Servlet information leak
│ │ │───JBoss Web Service Console
│ │ │───JMX and RMI service audit
│ │ │───Java application server fuzzing
│ │ │───Java Debug Wire Protocol (JDWP) audit
│ │ │───Jenkins audit
│ │ │───Jetty audit
│ │ │───IBM Domino audit
│ │ │───Misfortune Cookie
│ │ │───MongoDB audit
│ │ │───Movable Type RCE
│ │ │───Nginx PHP FastCGI RCE via file upload
│ │ │───Open Redirect
│ │ │───Oracle application logs
│ │ │───Oracle reports audit
│ │ │───PHP CGI RCE force redirect
│ │ │───PHP Hash Collision Denial of Service
│ │ │───Plesk audit
│ │ │───Plesk Agent SQL Injection
│ │ │───Plesk Single-Sign-On SO XXE
│ │ │───Plone Remote Code Execution
│ │ │───Pyramid debug mode enabled
│ │ │───Railo audit
│ │ │───Ruby on Rails (RoR) XML and YAML deserialization
│ │ │───Registration page
│ │ │───Reverse Proxy Bypass
│ │ │───Ruby on Rails (RoR) database file
│ │ │───TLS/SSL audit
│ │ │───Same-site Scripting
│ │ │───Snoop servlet
│ │ │───Spring Boot Actuator audit
│ │ │───Hostile subdomain takeover
│ │ │───Apache Tomcat audit
│ │ │───Apache Tomcat default credentials
│ │ │───Apache Tomcat examples
│ │ │───Apache Tomcat Hello.jsp XSS
│ │ │───Apache Tomcat status page
│ │ │───Tornado debug mode enabled
│ │ │───TRACK and TRACE methods enabled
│ │ │───Exposed phpMyAdmin interface
│ │ │───VMWare (multiple products) Directory Traversal Privilege Escalation
│ │ │───Known web server vulnerabilities
│ │ │───VirtualHost audit
│ │ │───WAF detection
│ │ │───WEBrick Directory Traversal
│ │ │───Apache Tomcat /WEB-INF/web.xml audit
│ │ │───Oracle WebLogic Server audit
│ │ │───Web Server Default Welcome Page
│ │ │───Web statistics search
│ │ │───Adobe (multiple products) XXE
│ │ │───Zend Framework configuration file exposed
│ │ │───ElasticSearch audit
│ │ │───ASP.NET ELMAH library Information Disclosure
│ │ │───Lighttpd SQL Injection
│ │ │───Microsoft SharePoint XSS
│ │ │───phpMoAdmin RCE
│ │ │───Laravel log file
│ │ │───Oracle Weblogic WLS-WSAT Component Deserialization RCE
│ │ │───PHPUnit RCE (CVE-2017-9841)
│ │ │───Atlassian OAuth Plugin IconUriServlet SSRF
│ │ │───Django Debug Mode via DisallowedHost
│ │ │───PHP-FPM Status Page
│ │ │───Test CGI scripts
│ │ │───Tests for Cisco ASA Path Traversal
│ │ │───Insecure Odoo Web Database Manager
│ │ │───JBoss Remote Code Execution (CVE-2015-7501)
│ │ │───JBoss Remote Code Execution (CVE-2017-7504)
│ │ │───WebSphere Remote Code Execution (CVE-2015-7450)
│ │ │───Liferay TunnelServlet Deserialization RCE
│ │ │───Liferay XMLRPC Blind SSRF
│ │ │───Spring Security OAuth RCE
│ │ │
│───│───Structure tests
│ │ │───Apache Flex audit
│ │ │───ASP.NET AJAX Control Toolkit audit
│ │ │───amCharts audit
│ │ │───Amazon S3 Buckets audit
│ │ │───Apache HTTP Server Content Negotiation file discovery
│ │ │───Microsoft Azure Blobs audit
│ │ │───CKEditor Audit
│ │ │───CakePHP audit
│ │ │───clipboard.swf audit
│ │ │───Configuration file disclosure
│ │ │───Ext JS audit
│ │ │───Ext JS examples arbitrary file read
│ │ │───FCKEditor audit
│ │ │───Google Web Toolkit (GWT) audit
│ │ │───Genericons audit
│ │ │───Host Header Attack
│ │ │───IBM Web Content Manager XPath Injection
│ │ │───Microsoft IIS Tilde Directory Enumeration
│ │ │───Java EE audit
│ │ │───JAAS authentication bypass
│ │ │───JBoss Seam Framework Remoting
│ │ │───JBoss Seam Framework
│ │ │───JPlayer audit
│ │ │───JSP authentication bypass
│ │ │───JW Player audit
│ │ │───Microsoft Windows HTTP.sys RCE (MS15-034)
│ │ │───Minify audit
│ │ │───Open Flash Charts unrestricted file upload
│ │ │───Open Flash Chart audit
│ │ │───Oracle Java Server Faces 2 Directory Traversal
│ │ │───PHP CGI RCE
│ │ │───Plupload audit
│ │ │───PrimeFaces EL Injection
│ │ │───Ruby on Rails (RoR) audit
│ │ │───Ruby on Rails (RoR) routes audit
│ │ │───Ruby on Rails (RoR) Devise authentication password reset
│ │ │───Ruby on Rails (RoR) Rails weak secret token
│ │ │───SWFUpload audit
│ │ │───Server directory listing
│ │ │───Directory Traversal
│ │ │───Server source code disclosure
│ │ │───Session Fixation
│ │ │───SharePoint audit
│ │ │───SimpleViewer audit
│ │ │───Apache Struts2 ClassLoader manipulation DoS (S2-020)
│ │ │───Apache Struts2 ClassLoader manipulation DoS (S2-021)
│ │ │───Apache Struts2 development mode
│ │ │───Apache Struts2 OGNL Injection RCE
│ │ │───Apache Struts 2.0.14 RCE
│ │ │───Apache Struts2 remote command execution (S2-045)
│ │ │───Apache Struts2 Remote Code Execution (S2-048)
│ │ │───Apache Struts2 Remote Command Execution (S2-052)
│ │ │───Timthumb audit
│ │ │───Tiny MCE audit
│ │ │───Uploadify jQuery plugin audit
│ │ │───Uploadify Flash audit
│ │ │───WADL files
│ │ │───WebDAV audit
│ │ │───XML Quadratic Blowup DoS
│ │ │───X-Forwarded-For header authentication bypass
│ │ │───YUI Uploader SWF audit
│ │ │───Zend Framework LFI via XXE
│ │ │───ZeroClipboard SWF audit
│ │ │───Flowplayer SWF audit
│ │ │───Nginx Redirect Header Injection
│ │ │───phpLiteAdmin audit
│ │ │───phpThumb() audit
│ │ │───TCPDF audit
│ │ │
│───│───Post-scan tests
│ │ │───Stored vulnerabilities
│ │ │───Webmail password audit
│ │ │───Stored XSS
│ │ │───Stored SQL Injection
│ │ │───Stored File Inclusion
│ │ │───Stored Directory Traversal
│ │ │───Stored code execution
│ │ │───Stored File Tampering
│ │ │───Stored PHP Code Execution
│ │ │───Multiple web servers
│ │ │
│───│───Known web application tests
│ │ │───CMS Made Simple audit
│ │ │───CodeIgniter Web Framework audit
│ │ │───Atlassian Confluence audit
│ │ │───DNN (DotNetNuke) audit
│ │ │───Drupal audit
│ │ │───Drupal RCE
│ │ │───Drupal Views module Information Disclosure
│ │ │───Drupal SQL Injection
│ │ │───Drupal RCE SA-CORE-2018-002
│ │ │───Ektron CMS audit
│ │ │───Gallery audit
│ │ │───Horde audit
│ │ │───Invision Power Board audit
│ │ │───Atlassian JIRA audit
│ │ │───Joomla! audit
│ │ │───Joomla! weak credentials
│ │ │───Joomla! SQL Injection
│ │ │───Joomla! RCE
│ │ │───Joomla! JCE Arbitrary File Upload
│ │ │───Joomla! JomSocial RCE
│ │ │───Joomla! SQL Injection 3.2.1
│ │ │───Joomla! SQL Injection 3.2.2
│ │ │───Joomla! Kunena Forum SQL Injection
│ │ │───Joomla! Akeeba Backup Access Control Bypass
│ │ │───Joomla! RFI
│ │ │───Joomla! VirtueMart Access Control Bypass
│ │ │───Kayako Fusion audit
│ │ │───Liferay audit
│ │ │───Magento audit
│ │ │───MantisBT audit
│ │ │───MediaWiki audit
│ │ │───MoinMoinWiki audit
│ │ │───Movable Type audit
│ │ │───Nagios audit
│ │ │───OpenX audit
│ │ │───phpMyAdmin audit
│ │ │───PmWiki audit
│ │ │───Roundcube audit
│ │ │───Microsoft SharePoint audit
│ │ │───Symfony audit
│ │ │───Symphony audit
│ │ │───Tiki Wiki CMS audit
│ │ │───Typo3
│ │ │───Umbraco audit
│ │ │───Umbraco LFI
│ │ │───vBulletin audit
│ │ │───vBulletin SQL Injection
│ │ │───vBulletin RCE
│ │ │───TimThumb WordPress plugin audit
│ │ │───WordPress plugins and themes audit
│ │ │───WordPress caching plugins audit
│ │ │───OptimizePress WordPress plugin audit
│ │ │───Jetpack WordPress plugin audit
│ │ │───All in One SEO Pack WordPress plugin audit
│ │ │───MailPoet Newsletters WordPress plugin audit
│ │ │───WPtouch WordPress plugin audit
│ │ │───Revolution Slider WordPress plugin audit
│ │ │───WordPress debug mode enabled
│ │ │───WordPress /wp-admin accessible without HTTP authentication
│ │ │───WordPress Path Disclosure
│ │ │───WordPress wp-config.php backup file search
│ │ │───WordPress open registration
│ │ │───WooFramework WordPress plugin audit
│ │ │───WordPress ToolsPack malware
│ │ │───WordPress XML-RPC authentication brute force
│ │ │───WordPress W3 Total Cache plugin audit
│ │ │───WordPress plugins audit
│ │ │───WordPress weak credentials audit
│ │ │───WordPress plugin enumeration
│ │ │───X-Cart audit
│ │ │───Zabbix audit
│ │ │───Drupal Backup Migrate
│ │ │───Atlassian Jira ManageFilters Information Disclosure
│ │ │───Atlassian Jira OAuth Plugin IconUriServlet SSRF
│ │ │───WordPress REST API User Enumeration
│ │ │───Atlassian Jira Insecure REST Permissions
│ │ │───Liferay older versions
│ │ │───Drupal Core Open Redirect
│ │ │───WPEngine _wpeprivate/config.json information disclosure
│ │ │───Remote Code Execution vulnerability in WordPress Duplicator
│ │ │───Ektron CMS authentication bypass (CVE-2018-12596)
│ │ │───Unauthenticated Stored XSS in WordPress Plugin WPML
│ │ │───vBulletin 5 routestring LFI
│ │ │───SAP common files and folders
│ │ │───SAP Netweaver version information leaks
│ │ │───SAP Netweaver bcbadmSystemInfo.jsp information leak
│ │ │───SAP Netweaver ipcpricing SSRF
│ │ │───SAP ICF /sap/public/info information disclosure
│ │ │───SAP weak/predictable user credentials
│ │ │───SAP weak/predictable user credentials (variant)
│ │ │───SAP NetWeaver ConfigServlet remote command execution
│ │ │───SAP Management Console list logfiles
│ │ │───SAP Management Console get user list
│ │ │───SAP KMC incorrect permissions
│ │ │───SAP Portal directory traversal vulnerability
│ │ │───SAP NetWeaver Java AS WD_CHAT information disclosure
│ │ │───Drupal REST Remote Code Execution
│ │ │───Magento Unauthenticated SQL Injection
│ │ │───Jira Unauthorized SSRF via REST API
│ │ │───vBulletin 5.x 0day pre-auth RCE
│ │ │
│───│───Runtime passive analysis
│ │ │───Insecure transition from HTTP (HTTPS) to HTTPS (HTTP)
│ │ │───SQL statement in comment
│ │ │───Content-type not specified
│ │ │───Session token in URL
│ │ │───Password sent via GET method
│ │ │───Cookie scoped to parent domain
│ │ │───Session cookie without HttpOnly flag set
│ │ │───Session Cookie without Secure flag set
│ │ │───Cacheable sensitive page
│ │ │───Unencrypted ASP.NET View State parameter
│ │ │───Subresource Integrity (SRI) not implemented
│ │ │───Secured connection
│ │ │───Mojolicious weak secret key
│ │ │───Yii2 weak secret key
│ │ │───Oracle PeopleSoft SSO weak secret key
│ │ │───Web2py weak secret key
│ │ │───Express cookie-session weak secret key
│ │ │───Express express-session weak secret key
│ │ │───Flask weak secret key
│ │ │───Cookie signed with weak secret key (universal)
│ │ │
│───│───Crawler tests
│ │ │
│───│───Location tests
│ │ │───Tomcat path traversal via reverse proxy mapping
│ │ │───CORS origin validation failure
│ │ │───Enabled Yii2 Framework Gii module
│ │ │───Node.js web application source code disclosure
│ │ │───npm log file publicly accessible (npm-debug.log)
│ │ │───PHP-CS-Fixer cache file publicly accessible (.php_cs.cache)
│ │ │───Laravel log viewer LFD (Local File Download)
│ │ │───SAP B2B/B2C CRM LFI (Local File Inclusion)
│ │ │───Node.js path validation vulnerability (CVE-2017-14849)
│ │ │───jQuery File Upload unauthenticated arbitrary file upload
│ │ │───GoAhead web server remote code execution
│ │ │───File creation via HTTP method PUT
│ │ │───ColdFusion RDS enabled
│ │ │───ColdFusion Request Debugging information disclosure
│ │ │───ColdFusion Robust Exception information disclosure
│ │ │───ColdFusion-specific paths
│ │ │───ColdFusion AMF Deserialization RCE
│ │ │───ColdFusion JNDI injection RCE (CVE-2018-15957)
│ │ │───ColdFusion Arbitrary File Upload RCE (CVE-2018-15961)
│ │ │───Python web application source code disclosure
│ │ │───Ruby web application source code disclosure
│ │ │───Confluence Widget Connector RCE
│ │ │───Apache Shiro Deserialization RCE
│ │ │───ColdFusion FlashGateway Deserialization RCE (CVE-2019-7091)
│ │ │───Oracle Business Intelligence Convert XXE (CVE-2019-2767)
│ │ │───Oracle Business Intelligence Adfresource Path traversal (CVE-2019-2588)
│ │ │───Oracle Business Intelligence AuthBypass CVE-2019-2768
│ │ │───Oracle Business Intelligence ReportTemplateService XXE (CVE-2019-2616)
│ │ │───Oracle Business Intelligence default administrative credentials
│ │ │
│───│───HTTP Data tests
│ │ │───Known malicious links
│ │ │───Publicly writable Amazon S3 Buckets
│ │ │───Header-Based Authentication Bypass
│ │ │───Detect Apache Shiro
│ │ │───RichFaces EL Injection RCE
│ │ │───Spring JSONP enabled by default in MappingJackson2JsonView
│ │ │───Spring Webflow SPEL RCE
│ │ │───Telerik Web UI Cryptographic Weakness
│ │ │───Java JSON deserialization
│ │ │───Apache Struts Remote Code Execution (S2-057)
│ │ │───URL rewrite vulnerability
│ │ │───Enabled Yii2 Framework debug toolkit
│ │ │───Content Security Policy (CSP) is not implemented
│ │ │───Adobe Experience Manager security issues
│ │ │───Httpoxy vulnerability
│ │ │───Firebase database accessible without authentication
│ │ │───Flex BlazeDS AMF Deserialization RCE (CVE-2017-5641)
│ │ │───Information Disclosure text search
│ │ │───Rails File Content Disclosure
│ │ │───Atlassian Crowd Remote Code Execution
│ │ │───Apache Tapestry weak secret key
│ │ │
│───│───Target tests
│ │ │───Rails Sprockets Path Traversal Vulnerability
│ │ │───Web Cache Poisoning
│ │ │───Auxiliary systems SSRF
│ │ │───Reverse proxy misrouting SSRF
│ │ │───Cross site scripting in HTTP-01 ACME challenge implementation
│ │ │───JavaMelody detection and security issues
│ │ │───uWSGI Path Traversal vulnerability
│ │ │───WebLogic RCE (CVE-2018-3245)
│ │ │───XDebug RCE
│ │ │───NGINX range filter integer overflow
│ │ │───Jupyter Notebook publicly accessible
│ │ │───Hadoop YARN ResourceManager publicly accessible
│ │ │───CouchDB REST API publicly accessible
│ │ │───Apache Log4j socket receiver deserialization vulnerability
│ │ │───Apache ActiveMQ default administrative credentials
│ │ │───Apache mod_jk access control bypass
│ │ │───ACME mini_httpd (web server) arbitrary file read
│ │ │───OSGi Management Console Default Credentials
│ │ │───Docker Engine API publicly exposed
│ │ │───Docker Registry API publicly exposed
│ │ │───Jenkins security audit
│ │ │───ThinkPHP v5.0.22/5.1.29 RCE
│ │ │───Typo3 Restler 1.7.0 LFD
│ │ │───uWSGI Unauthorized Access Vulnerability
│ │ │───FastGI Unauthorized Access Vulnerability
│ │ │───Apache balancer-manager application
│ │ │───Cisco ISE Unauthenticated XSS to Privileged RCE
│ │ │───Horde Imp Unauthenticated Remote Command Execution
│ │ │───Nagios XI Magpie_debug.php Unauthenticated RCE
│ │ │───Arbitrary File Read in Next.js < 2.4.1
│ │ │───PHP opcache-status page publicly accessible
│ │ │───OpenCms Solr XXE
│ │ │───Redis Unauthorized Access Vulnerability
│ │ │───Memcached Unauthorized Access Vulnerability
│ │ │───Oracle Weblogic Async Component Deserialization RCE (CVE-2019-2725)
│ │ │───Oracle Weblogic T3 XXE (CVE-2019-2647)
│ │ │───Reverse proxy detection
│ │ │───Apache Cassandra Unauthorized Access Vulnerability
│ │ │───Nagios XI Unauthenticated SQLi CVE-2018-8734
│ │ │───Remote code execution in bootstrap-sass
│ │ │───Apache Spark Audit
│ │ │───Fortigate SSL VPN Arbitrary File reading (CVE-2018-13379)
│ │ │───Pulse Secure SSL VPN Arbitrary File reading (CVE-2019-11510)
│ │ │───SAP Hybris Deserialization RCE (CVE-2019-0344)
│ │ │───Webmin v1.920 RCE
│ │
│───│───DOM-based XSS tests
│ │
│───│───CSRF (Cross-site Request Forgery)
│ │
│───│───TLS1-SSLv3 renegotiation vulnerability
│ │
│───│───Slow HTTP Denial of Service (DoS)漏洞中文翻译列表[Google智障翻译]
所有检查
│───扫描测试
││────文件测试
│││───文件的隐藏,作废和备份副本
│││────Bash远程代码执行(
ShellShock )│││────HTML格式在重定向页面
│││────AJAXhashbang搜索
│││────JavaScript抽象语法树解析器
│││────JavaScript库审计
│││────PHPSuperGlobals覆盖
││││────RESTfulWeb服务发现和审计(每个文件)
│││───Relative路径覆盖
│││───File信息披露的文本搜索
│││───XSS文件URI
│││───XXE文件URI
│││ ───ApacheTomcat信息披露
│││──────SpringData REST远程代码执行
│────────目录测试
│││────PHPAPC审核
│││────ASP.NET应用程序跟踪
│││────ASP。启用NET调试
│││────ASP.NET诊断页
│││────访问数据库搜索
│││────ApacheSolr审核
│││────ApacheTomcat Windows目录遍历
│││────隐藏的目录的过时,过时和备份副本
│││────基于HTTP的HTTP基本认证
│││───Bazaar信息库
││││────CVS信息库
│││────核心转储(内存转储)搜索
│││ ────开发文件
│││────目录清单
│││───Dreamweaver脚本
│││────Git存储库
│││────Grails数据库控制台
│││────HTML重定向目录中的表单
│││───HTTP动词篡改
│││─────Microsoft IIS目录身份验证绕过
││ │───无效的页面文本搜索
│││────JetBrains.idea项目目录
│││────Mercurial存储库
│││────暴露的phpinfo()
│││─────可能的敏感目录
│││─ ──可能的敏感文件
││────RESTfulWeb服务发现和审核(每个目录)
│││────自述文件
│││────SFTP凭证暴露
│││────HTTP基本身份验证中的SQL注入
│││────URI中的SQL注入
│││────SQLite数据库搜索
│││────SVN存储库
│││────敏感文件
│││───目录信息公开文本搜索
│││────Web外壳搜索
│││─ ──WS_FTP.LOG信息泄露
│││───弱的HTTP基本认证密码
│││────Webadmin搜索
│││────目录URI中的
XSS│││─────目录URI中的
XSE││││─ ──.htaccess文件可读
│││───DEADJOE文件
│││───Symfonydatabases.yml里
│││───Dotenv文件
│││───Spring引导执行器版本2
│││───Spring引导WhiteLabel错误页面SpEL│││────
通过错误配置的别名进行Nginx路径遍历
│││───Spring安全验证绕过
│││
│───│───Input方案测试
│││───ASP代码注入
│││───AnalyzeHTTP请求的参数值
│││───任意文件的创建
│││─── 任意文件的删除
│││────盲SQL注入
│││────
盲XSS│││────CRLF注入(HTTP响应拆分)
│││────远程代码执行
│││────对输入的目录遍历
│││────电子邮件标题注入
│││─────电子邮件(SMTP)注入
│││────输入错误消息异常且格式错误
│││───语言(EL)注入
│││───文件包含
│││────文件篡改
│││───文件上传
│││────
填充Oracle│││────HTTP参数污染
│││────密码重置中毒
│││────HTML身份验证审核
│││────LDAP注入
│││────长密码
DoS│││────MongoDB注入
│││────服务器端JavaScript注入
│││────PHP代码注入
│││── ──Rubyon Rails代码注入
│││────Perl代码注入
│││────用户控制的PHP漏洞
│││────Rubyon Rails(RoR)不安全的批量分配
││││────Rubyon Rails (RoR)Active Record WHERE子句SQL注入
│││────Rubyon Rails(RoR)渲染内联
RCE│││────远程文件包含
XSS│││────源代码公开
│││────服务器端请求伪造
│││── ─SQL注入
│││────ApacheStruts2远程命令执行(S2-053)
│││────ApacheStruts 2.0.29
RCE│││────不安全的preg_replace()
│││────XFS和Redir
│││────XML外部实体注入(XXE)
│││────XPath注入
│││────跨站脚本(XSS)
│││────边包含边注入(ESI注入)
││ │───Java对象反
序列化│││────Pythonpickle序列化
│││───Python代码注入
│││───Argument注射
│││
│───│───Server测试
│││───ApacheTomcat的AJP协议审计
│││───ASP.NET错误消息
│││───ASP .NET表单身份验证绕过
│││────ApacheAxis2审核
│││────启用了Apache Geronimo默认凭据审核
│││────启用了Apache HTTP Server CONNECT方法
│││────ApacheRoller审核
│││─ ──以代理身份运行的
Apache HTTP Server│││────Apache HTTP Server mod_info审核
│││────可访问Apache Solr管理
│││────未经过滤的Apache HTTP Server期望头注入
││││────Apache通过格式错误的HTTP请求的HTTP Server XSS
│││────ApacheHTTP Server HttpOnly cookie公开
│││────Apachemod_negotiation文件名bruteforcing│││────Rubyon
Rails Action Pack任意文件公开
│││────梭子鱼多产品'locale'目录遍历
│││───Bash远程执行代码(弹震)服务器审计
│││───CRLF注射(HTTP响应分裂)服务器审计
│││───Clickjacking
│││───clientaccesspolicy.xml审计
│││ ────AdobeColdFusion审核
│││──ColdFusion用户代理
XSS│││────AdobeColdFusion FCKEditor文件上传
│││────AdobeColdFusion Solr信息披露
│││────核心转储(内存转储)搜索服务器审核
│││────crossdomain.xml审核
│││────数据库备份
│││────Djangoadmin弱密码审核
│││────错误页面路径泄露
│││─────启用了瓶装调试模式
│ ││────启用Microsoft FrontPage Server Extensions│││────MicrosoftFrontPage
信息
│││────Microsoft FrontPage authors.pwd│││────OracleGlassFish
Server目录遍历
│││────OracleGlassFish Server审核
│││────Hadoop集群Web界面
│││────OpenSSLTLS心跳(Heartbleed)漏洞
│││────HordeIMP Webmail审核
│││────IBMWebSphere审核
│││────ASP Global.asa
│││────IIS内部IP地址
│││────Microsoft IIS Unicode目录遍历
│││────暴露出Microsoft IIS服务配置
│││────Microsoft IIS NTLM和HTTP基本身份验证绕过
│││─ ──IoncubeLoader向导
││────Red Hat JBoss审核
│││────JBossStatus Servlet信息泄漏
│││────JBossWeb服务控制台
│││────JMX和RMI服务审核
│││ ───Java应用服务器模糊
测试│││────Java调试线协议(JDWP)审核
│││────詹金斯审核
│││────码头审核
│││────IBMDomino审核
│││─ ──
不幸的Cookie│││───MongoDB审核
│││────可移动类型
RCE││││────NginxPHP FastCGI RCE通过文件上传
│││────打开重定向
│││────Oracle应用程序日志
││││───Oracle报告审核
││力重定向│───PHPCGI RCE
││服务│───PHP哈希冲突拒绝
│││───Plesk审计
│││───Plesk代理SQL注入
│││───Plesk单点登录在SO XXE上
│││───克隆远程代码执行
│││──启用金字塔调试模式
│││────Railo审核
│││────Rubyon Rails(RoR)XML和YAML反序列化
│││ ────注册页面
│││────反向代理绕过
│││────Rubyon Rails(RoR)数据库文件
│││────TLS/ SSL审核
│││────同一站点脚本
│││────
侦听servlet│││────Spring Boot Actuator审核
│││────敌对子域接管
│││ ───ApacheTomcat的审计
│││───Apache的Tomcat默认凭据
│││───Apache的Tomcat实例
│││───Apache的Tomcat的hello.jsp XSS
│││───ApacheTomcat的状态页
│││ ────启用了Tornado调试模式│││────启用了
TRACK和TRACE方法
│││────暴露的phpMyAdmin接口
│││────VMWare(多种产品)目录遍历权限提升
│││────已知网络服务器漏洞
│││───VirtualHost审核
│││────WAF检测
│││────WEBrick目录遍历
│││────Apache Tomcat /WEB-INF/web.xml审核
│││────Oracle WebLogic Server审核
│││──── Web服务器默认欢迎页面
│││───Web统计信息搜索
│││─────Adobe(多种产品)
XXE││││────暴露Zend Framework配置文件
│││────ElasticSearch审核
│││── ─ASP.NETELMAH库信息披露
│││───LighttpdSQL注入
│││───Microsoft的SharePoint XSS
│││───phpMoAdminRCE
│││───Laravel日志文件
│││───Oracle Weblogic WLS-WSAT组件反序列化RCE
│││────PHPUnitRCE(CVE-2017-9841)
│││──AtlassianOAuth插件IconUriServlet
SSRF│││──通过DisallowedHost进行的Django调试模式
│││────PHP-FPM状态页
││ │────测试CGI脚本
│││────针对Cisco ASA路径遍历的
测试│││────不安全的Odoo Web数据库管理器
│││────JBoss远程代码执行(CVE-2015-7501)
│││ ────JBoss远程执行代码(CVE-2017-7504)
│││──WebSphere远程执行代码(CVE-2015-7450)
││────LiferayTunnelServlet反序列化
RCE│││────LiferayXMLRPC Blind SSRF
│││───Spring安全的OAuth RCE
│││
│───│───Structure测试
│││────ApacheFlex审核
│││────ASP.NETAJAX Control Toolkit审核
│││────amCharts审核
│││────AmazonS3 Buckets审核
│││────ApacheHTTP Server Content协商文件发现
│││────MicrosoftAzure Blobs审核
│││────CKEditor审核
│││────CakePHP审核
│││────clipboard.swf审核
│││────配置文件公开
││ │───ExtJS审核
││││──ExtJS示例任意文件读取
│││────FCKEditor审核
│││────Google Web Toolkit(GWT)审核
│││────Genericons审核
││ │───主机头攻击
│││───IBMWeb Content Manager XPath注入
│││───MicrosoftIIS波浪号目录列表
│││───JavaEE审计
│││───JAAS绕过认证
│││───JBossSeam框架远程处理
│││───JBossSeam框架
││ │───JPlayer审核
│││────JSP身份验证绕过
│││────JWPlayer审核
│││───MicrosoftWindows HTTP.sys RCE(MS15-034)
│││────最小化审核
│ ││───OpenFlash Charts不受限制地上传文件
│││───OpenFlash Chart审核
│││───OracleJava Server Faces 2目录遍历
│││────PHPCGI
RCE│││────Plupload审核
│││────PrimeFacesEL注塑
│││───Rubyon Rails(RoR)审核
│││────Rubyon Rails(RoR)路线审核
│││────Rubyon Rails(RoR)设计认证密码重置
│││────Rubyon Rails(RoR)Rails弱秘密令牌
│││─ ──SWFUpload审核
│││────服务器目录清单│││────目录
遍历
│││─────服务器源代码公开
│││────会话固定
││││───SharePoint审核
│││ ────SimpleViewer审核
│││──ApacheStruts2 ClassLoader操作DoS(S2-020)
│││────ApacheStruts2 ClassLoader操作DoS(S2-021)
│││────ApacheStruts2开发模式
│││ ────ApacheStruts2 OGNL注入
RCE│││────ApacheStruts 2.0.14 RCE
│││────ApacheStruts2远程命令执行(S2-045)
││││──ApacheStruts2远程代码执行(S2-048)
│││────ApacheStruts2远程命令执行(S2-052)
││ │───Timthumb审核
│││────微小的MCE审核
│││────UploadifyjQuery插件审核
│││────UploadifyFlash审核
││││───WADL文件
│││────WebDAV审核
│││────XML二次爆破
DoS│││────X转发头的身份验证旁路
│││────YUIUploader SWF审核
│││────通过XXE的Zend Framework
LFI│││── ─零剪贴板SWF审核
│││────FlowplayerSWF审核
│││────Nginx重定向头注入
│││───phpLiteAdmin审计
│││───phpThumb()审计
│││───TCPDF审计
│││
│───│───Post扫描测试
│││───Stored漏洞
│ ││────Webmail密码审核
│││────存储的XSS│││────
存储的SQL注入
│││────存储的文件包含
│││────存储的目录遍历
│││────代码执行
│││───Stored文件篡改
│││───StoredPHP代码执行
│││───MultipleWeb服务器
│││
│───│───KnownWeb应用程序测试
│││── ─CMS简化审核
│││───CodeIgniterWeb框架审核
│││───Atlassian总汇审计
│││───DNN(DotNetNuke的)审核
│││───Drupal审计
│││───DrupalRCE
│││───Drupal视图模块信息披露
│││ ────DrupalSQL注入
│││────DrupalRCE SA-CORE-2018-002│││────EktronCMS
审核
│││────画廊审核
│││─────部落审核
│││─ ──Invision电源板审核
│││────Atlassian JIRA审核
│││───Joomla!审核
│││─── 凭据薄弱
│││───Joomla!SQL注入
│││─── RCE
│││───Joomla!JCE任意文件上传
│││───Joomla!JomSocial RCE
│││─── SQL注入
3.2.1│││───Joomla!SQL注入
3.2.2│││───Joomla!Kunena论坛SQL注入
│││───Joomla!Akeeba备份访问控制旁路
│││───Joomla!RFI
│││───Joomla!VirtueMart访问控制旁路
│││──KayakoFusion审核
│││──Liferay审核
│││────Magento审核
│││────MantisBT审核
│││─────MediaWiki审核
│││── ─MoinMoinWiki审核
│││──可移动类型审核
│││──Nagios审核
│││────OpenX审核
│││────phpMyAdmin审核
│││────PmWiki审核
│││──── Roundcube审核
│││───Microsoft的SharePoint审计
│││───Symfony审计
│││───Symphony审计
│││───Tiki维基CMS审计
│││───Typo3
│││───Umbraco审计
│││───UmbracoLFI
│││───vBulletin审计
│││───vBulletinSQL注入
│││───vBulletinRCE
│││───TimThumbWordPress插件审计
│││───WordPress插件和主题审核
│││────WordPress缓存插件审核
│││────OptimizePressWordPress插件审核
│││────JetpackWordPress插件审核
│││────一站式SEO Pack WordPress插件审核
││ │───MailPoet通讯WordPress插件审核
│││────WPtouchWordPress插件审核
│││────RevolutionSlider WordPress插件审核
│││────启用WordPress 调试模式
│││────WordPress/ wp-admin无需HTTP身份验证即可访问
│││─ ──WordPress路径披露
││││──WordPresswp-config.php备份文件搜索
│││────WordPress开放注册
│││────WooFrameworkWordPress插件审核
││││────WordPressToolsPack恶意软件
││ │───WordPressXML-RPC认证蛮力
│││────WordPressW3 Total Cache插件审核
│││────WordPress插件审核
│││────WordPress弱凭据审核
│││────WordPress插件枚举
│││────X-Cart审核
│││────Zabbix审核
│││────DrupalBackup
Migrate│││────Atlassian Jira ManageFilters信息披露
│││────AtlassianJira OAuth插件IconUriServlet SSRF
│││────WordPressREST API用户枚举
│││────Atlassian Jira不安全的REST权限
│││────Liferay的旧版本
│││────DrupalCore Open Redirect│││────WPEngine_wpeprivate
/ config.json信息泄露
│││───WordPress Duplicator中的远程执行代码漏洞
│││────EktronCMS身份验证绕过(CVE-2018-12596)
│││───WordPress插件WPML中未经身份验证的存储XSS
│││────vBulletin5路由字符串
LFI│││───SAP通用文件和文件夹
│││───SAPNetweaver版本信息泄漏
│││───SAPNetweaver bcbadmSystemInfo.jsp信息泄漏
│││── ─SAP Netweaver ipcpricing
SSRF│││───SAPICF / sap / public / info信息公开
│││───SAP弱/可预测的用户凭证
│││───SAP弱/可预测的用户凭证(变量)
││ │───SAPNetWeaver ConfigServlet远程命令执行
│││────SAP管理控制台列表日志文件
│││───SAP管理控制台获取用户列表
│││──SAPKMC错误权限
││││───SAP门户目录遍历漏洞
│││────SAPNetWeaver Java AS WD_CHAT信息公开
│││──DrupalREST远程执行代码
│││────Magento未经身份验证的SQL注入
│││────吉拉通过REST API的未经授权的
SSRF││││─ ──vBulletin5.x的0DAY预AUTH RCE
│││
│───│───Runtime被动分析
从HTTP│││───Insecure过渡(HTTPS)到HTTPS(HTTP)
│││───SQL注释中的声明
│││────未指定内容类型
│││────URL中的会话令牌
│││────通过GET方法发送的
密码│││────Cookie范围为父域
│││── ──未设置HttpOnly标志的
会话Cookie│││───未设置安全标志的会话Cookie
│││────可缓存的敏感页面
│││────未加密的ASP.NET视图状态参数
│││────未实现子资源完整性(SRI)
│││────安全连接
│││────Mojolicious弱密钥
│││────Yii2弱密钥
│││────Oracle PeopleSoft SSO弱密钥
│││────Web2py弱密钥
│││───Express cookie-session弱密钥
││ │───Express表达会话弱密钥
│││───Flask弱密钥
│││───Cookie弱密钥(通用)签署
│││
│───│───Crawler测试
│ ││
│───│───Location测试
│││────通过反向代理映射遍历Tomcat路径
│││────CORS原始验证失败
│││────启用Yii2 Framework Gii模块
│││────Node.jsWeb应用程序源代码公开
││ │────可公开访问的npm日志文件(npm-debug.log)
│││──── 可公开访问的PHP-CS-Fixer缓存文件(.php_cs.cache)
│││────Laravel日志查看器LFD(本地文件)下载)
│││───SAPB2B / B2C CRM LFI(包含本地文件)
│││───Node.js路径验证漏洞(CVE-2017-14849)
│││────jQuery文件上传未经身份验证的任意文件上传
│││────GoAheadWeb服务器远程执行代码
│││───通过HTTP方法PUT创建文件
│││────启用
ColdFusion RDS│││────ColdFusion请求调试信息公开
│││────ColdFusion健壮异常信息公开
│││────ColdFusion专用路径
││││────ColdFusionAMF反序列化RCE
│││───ColdFusionJNDI注射RCE(CVE-2018-15957)
│││───ColdFusion任意文件上传RCE(CVE-2018-15961)
│││───Pythonweb应用程序的源代码公开
││ │───RubyWeb应用程序源代码公开
│││────ConfluenceWidget Connector
RCE│││────ApacheShiro Deserialization
RCE││────ColdFusionFlashGateway Deserialization RCE(CVE-2019-7091)
│││────Oracle商业智能转换XXE(CVE-2019-2767)
│││────Oracle商业智能Adfresource路径遍历(CVE-2019-2588)
│││───Oracle商业智能AuthBypass CVE-2019 -2768
│││───Oracle商业智能ReportTemplateService XXE(CVE-2019至2616年)
│││───Oracle商业智能默认管理凭据
│││
│───│───HTTP数据进行测试
│││─ ──已知的恶意链接
│││────可公开写入的Amazon S3存储桶
│││────基于标题的身份验证绕行
│││────检测Apache
Shiro│││────RichFacesEL Injection
RCE││││─ ──在MappingJackson2JsonView中默认启用Spring JSONP
│││────SpringWebflow SPEL
RCE│││────TelerikWeb UI加密弱点
│││────Java JSON反序列化
│││────ApacheStruts远程执行代码(S2-057)
│││── ──URL重写漏洞
│││────已启用的Yii2 Framework调试工具包
│││────未实施内容安全策略(CSP)
│││────AdobeExperience Manager安全问题
││││────Httpoxy漏洞
│││────无需身份验证即可访问Firebase数据库
│││────FlexBlazeDS AMF反序列化RCE(CVE-2017-5641)
│││────信息披露文本搜索
│││────轨文件内容披露
│││───Atlassian人群远程执行代码
│││───Apache挂毯弱密钥
│││
│───│───Target测试
│││───Rails链轮路径遍历漏洞
│││─ ──Web缓存中毒
│││──辅助系统
SSRF│││──反向代理错误
路由SSRF│││────HTTP-01 ACME挑战实现中的跨站点脚本
│││────JavaMelody检测和安全性问题
│││────uWSGI路径遍历漏洞
│││────WebLogicRCE(CVE-2018-3245)
│││──XDebug
RCE│││──────NGINX范围过滤器整数溢出
│││── ─JupyterNotebook可公开访问
│││────HadoopYARN ResourceManager可公开访问
│││────CouchDBREST API可公开访问
│││────ApacheLog4j套接字接收器反序列化漏洞
│││────ApacheActiveMQ默认管理凭据
│││── ─Apache mod_jk访问控制旁路
│││────ACMEmini_httpd(Web服务器)任意文件读取
│││───OSGi管理控制台默认凭证
│││───公开暴露的Docker引擎
API│││───Docker公开暴露了Registry
API│││────Jenkins安全审核
│││────ThinkPHPv5.0.22 / 5.1.29
RCE│││──Typo3Restler 1.7.0
LFD│││────uWSGI未经授权的访问漏洞
│││────FastGI未经授权的访问漏洞
│││────Apache平衡器-管理器应用程序
│││────思科ISE未经身份验证的XSS到特权
RCE││││────HordeImp未经身份验证的远程命令执行
│││─ ──Nagios十一Magpie_debug.php未经验证的RCE
│││───Arbitrary文件的读取Next.js <2.4.1
│││───PHPopcache状态页公开访问
│││───OpenCmsSolr的XXE
││ │───Redis未经授权的访问漏洞
│││────Memcached未经授权的访问漏洞
│││────OracleWeblogic异步组件反序列化RCE(CVE-2019-2725)
│││───Oracle Weblogic T3 XXE(CVE- 2019-2647)
│││────逆向代理检测
│││────ApacheCassandra未经授权的访问漏洞
│││────NagiosXI未经身份验证的SQLi CVE-2018-8734│││────
在bootstrap-sass中执行远程代码
││ │───ApacheSpark审核
│││────FortigateSSL VPN任意文件读取(CVE-2018-13379)
│││───脉冲安全SSL VPN任意文件读取(CVE-2019-11510)
│││─ ──SAP反序列化款Hybris RCE(CVE-2019-0344)
│││───Webminv1.920 RCE
││
基于│───│───DOMXSS测试
││
│───│───CSRF (跨站请求伪造)
││
│───│───TLS1,重新谈判的SSLv3漏洞
││
│───│────慢速HTTP拒绝服务(DoS)破解过程{正确打开方式–安装–复制–替换}
① wvsc.exe覆盖到“C:\Program Files (x86)\Acunetix\13.0.200807155\
② license_info.json覆盖到“C:\ProgramData\Acunetix\shared\license”
acunetix_13.0.200807156破解版下载地址
①天翼网盘: https://cloud.189.cn/t/bieuy2AjuYNf (访问码:ds99)
②雨苁网盘: https://w.ddosi.workers.dev/
解压密码: www.ddosi.org
共四个文件:windows+linux+mac+破解补丁
acunetix_13.0.200807155.exe
acunetix_13.0.200807155_x64.sh
acunetix_13.0.200807156_mac_x64.pkg
AWVS_13_Win&Linux破解版.rar注意事项
该工具仅可用于研究使用,切勿用于非法活动.
工具安全性自测,For your safety请放虚拟机运行