目录导航
这是与特定攻击和利用技术相关联的Windows事件样本的容器。
可用于:
- 基于EVTX解析测试您的检测脚本
- 使用事件日志进行DFIR培训和威胁搜寻
- 使用Windows和Sysmon事件日志设计检测用例
- 如果您是红队成员,请不要吐槽
Winlogbeat批量读取
其中包含一个PowerShell脚本,可以使用winlogbeat循环遍历,解析和重放evtx文件。这对于将日志重放到ELK堆栈或本地文件中很有用。默认情况下,此脚本将按照winlogbeat_example.yml文件中的配置将日志输出到。\winlogbeat\events.json,您可以在winlogbeat.yml中配置任何自己的目标(从git中排除),如果以下示例配置文件将被忽略:找到winlogbeat.yml。
日志列表
├─AutomatedTestingTools
│ PanacheSysmon_vs_AtomicRedTeam01.evtx
│ panache_sysmon_vs_EDRTestingScript.evtx
│ readme.md
│ WinDefender_Events_1117_1116_AtomicRedTeam.evtx
│
├─Command and Control
│ cmds over dns txt queries and reponses.pcap
│ DE_RDP_Tunneling_4624.evtx
│ DE_RDP_Tunneling_TerminalServices-RemoteConnectionManagerOperational_1149.evtx
│ DE_RDP_Tunnel_5156.evtx
│ DE_sysmon-3-rdp-tun.evtx
│ readme.md
│ tunna_iis_rdp_smb_tunneling_sysmon_3.evtx
│ Tunna_rdp_tunnel_IIS.log
│ web_attack_and_isp_webshell_localhost_access_log.txt
│
├─Credential Access
│ 4794_DSRM_password_change_t1098.evtx
│ ACL_ForcePwd_SPNAdd_User_Computer_Accounts.evtx
│ babyshark_mimikatz_powershell.evtx
│ CA_4624_4625_LogonType2_LogonProc_chrome.evtx
│ CA_chrome_firefox_opera_4663.evtx
│ CA_DCSync_4662.evtx
│ CA_hashdump_4663_4656_lsass_access.evtx
│ CA_keefarce_keepass_credump.evtx
│ CA_keepass_KeeThief_Get-KeePassDatabaseKey.evtx
│ CA_Mimikatz_Memssp_Default_Logs_Sysmon_11.evtx
│ CA_protectedstorage_5145_rpc_masterkey.evtx
│ CA_sysmon_hashdump_cmd_meterpreter.evtx
│ CA_teamviewer-dumper_sysmon_10.evtx
│ dc_applog_ntdsutil_dfir_325_326_327.evtx
│ discovery_sysmon_1_iis_pwd_and_config_discovery_appcmd.evtx
│ etw_ad_netlogon_provider_zerologon_mimikatz.etl
│ etw_rpc_zerologon.evtx
│ kerberos_pwd_spray_4771.evtx
│ MSSQL_multiple_failed_logon_EventID_18456.evtx
│ phish_windows_credentials_powershell_scriptblockLog_4104.evtx
│ Powershell_4104_MiniDumpWriteDump_Lsass.evtx
│ remote_pwd_reset_rpc_mimikatz_postzerologon_target_DC.evtx
│ Sysmon13_MachineAccount_Password_Hash_Changed_via_LsarSetSecret.evtx
│ sysmon17_18_kekeo_tsssp_default_np.evtx
│ sysmon_10_11_lsass_memdump.evtx
│ sysmon_10_11_outlfank_dumpert_and_andrewspecial_memdump.evtx
│ sysmon_10_1_memdump_comsvcs_minidump.evtx
│ sysmon_10_lsass_mimikatz_sekurlsa_logonpasswords.evtx
│ sysmon_13_keylogger_directx.evtx
│ Sysmon_13_Local_Admin_Password_Changed.evtx
│ sysmon_2x10_lsass_with_different_pid_RtlCreateProcessReflection.evtx
│ sysmon_3_10_Invoke-Mimikatz_hosted_Github.evtx
│ Zerologon_CVE-2020-1472_DFIR_System_NetLogon_Error_EventID_5805.evtx
│ Zerologon_VoidSec_CVE-2020-1472_4626_LT3_Anonym_follwedby_4742_DC_Anony_DC.evtx
│
├─Defense Evasion
│ apt10_jjs_sideloading_prochollowing_persist_as_service_sysmon_1_7_8_13.evtx
│ DE_104_system_log_cleared.evtx
│ DE_1102_security_log_cleared.evtx
│ DE_BYOV_Zam64_CA_Memdump_sysmon_7_10.evtx
│ DE_EventLog_Service_Crashed.evtx
│ DE_Fake_ComputerAccount_4720.evtx
│ de_hiding_files_via_attrib_cmdlet.evtx
│ DE_KernelDebug_and_TestSigning_ON_Security_4826.evtx
│ de_portforward_netsh_rdp_sysmon_13_1.evtx
│ DE_Powershell_CLM_Disabled_Sysmon_12.evtx
│ de_powershell_execpolicy_changed_sysmon_13.evtx
│ de_PsScriptBlockLogging_disabled_sysmon12_13.evtx
│ DE_remote_eventlog_svc_crash_byt3bl33d3r_sysmon_17_1_3.evtx
│ DE_renamed_psexec_service_sysmon_17_18.evtx
│ DE_suspicious_remote_eventlog_svc_access_5145.evtx
│ de_sysmon_13_VBA_Security_AccessVBOM.evtx
│ DE_timestomp_and_dll_sideloading_and_RunPersist.evtx
│ DE_UAC_Disabled_Sysmon_12_13.evtx
│ de_unmanagedpowershell_psinject_sysmon_7_8_10.evtx
│ DE_WinEventLogSvc_Crash_System_7036.evtx
│ DE_xp_cmdshell_enabled_MSSQL_EID_15457.evtx
│ DSE_bypass_BYOV_TDL_dummydriver_sysmon_6_7_13.evtx
│ evasion_codeinj_odzhan_conhost_sysmon_10_1.evtx
│ evasion_codeinj_odzhan_spoolsv_sysmon_10_1.evtx
│ faxhell_sysmon_7_1_18_3_bindshell_dllhijack.evtx
│ meterpreter_migrate_to_explorer_sysmon_8.evtx
│ process_suspend_sysmon_10_ga_800.evtx
│ Sysmon 7 Update Session Orchestrator Dll Hijack.evtx
│ Sysmon 7 dllhijack_cdpsshims_CDPSvc.evtx
│ sysmon_10_1_ppid_spoofing.evtx
│ Sysmon_10_Evasion_Suspicious_NtOpenProcess_CallTrace.evtx
│ Sysmon_12_DE_AntiForensics_MRU_DeleteKey.evtx
│ sysmon_13_rdp_settings_tampering.evtx
│ sysmon_2_11_evasion_timestomp_MACE.evtx
│ Win_4985_T1186_Process_Doppelganging.evtx
│
├─Discovery
│ dicovery_4661_net_group_domain_admins_target.evtx
│ discovery_bloodhound.evtx
│ discovery_enum_shares_target_sysmon_3_18.evtx
│ discovery_local_user_or_group_windows_security_4799_4798.evtx
│ discovery_meterpreter_ps_cmd_process_listing_sysmon_10.evtx
│ discovery_psloggedon.evtx
│ Discovery_Remote_System_NamedPipes_Sysmon_18.evtx
│ discovery_sysmon_18_Invoke_UserHunter_NetSessionEnum_DC-srvsvc.evtx
│ discovery_sysmon_3_Invoke_UserHunter_SourceMachine.evtx
│ discovery_UEFI_Settings_rweverything_sysmon_6.evtx
│
├─Execution
│ exec_driveby_cve-2018-15982_sysmon_1_10.evtx
│ exec_msxsl_xsl_sysmon_1_7.evtx
│ exec_persist_rundll32_mshta_scheduledtask_sysmon_1_3_11.evtx
│ exec_sysmon_1_11_lolbin_rundll32_openurl_FileProtocolHandler.evtx
│ exec_sysmon_1_11_lolbin_rundll32_shdocvw_openurl.evtx
│ exec_sysmon_1_11_lolbin_rundll32_zipfldr_RouteTheCall.evtx
│ exec_sysmon_1_7_jscript9_defense_evasion.evtx
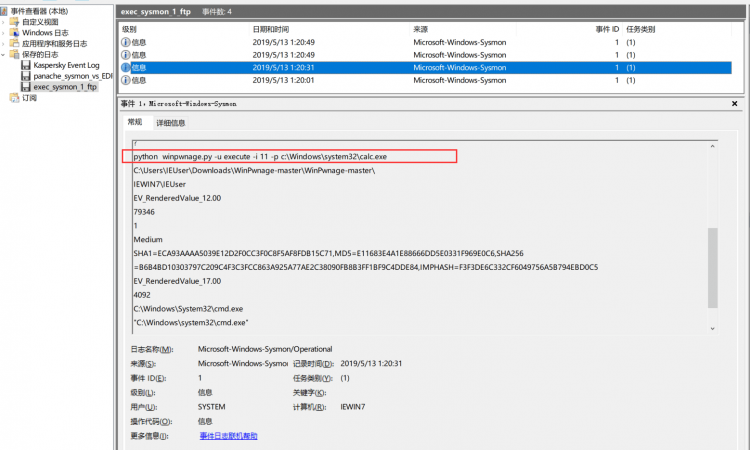
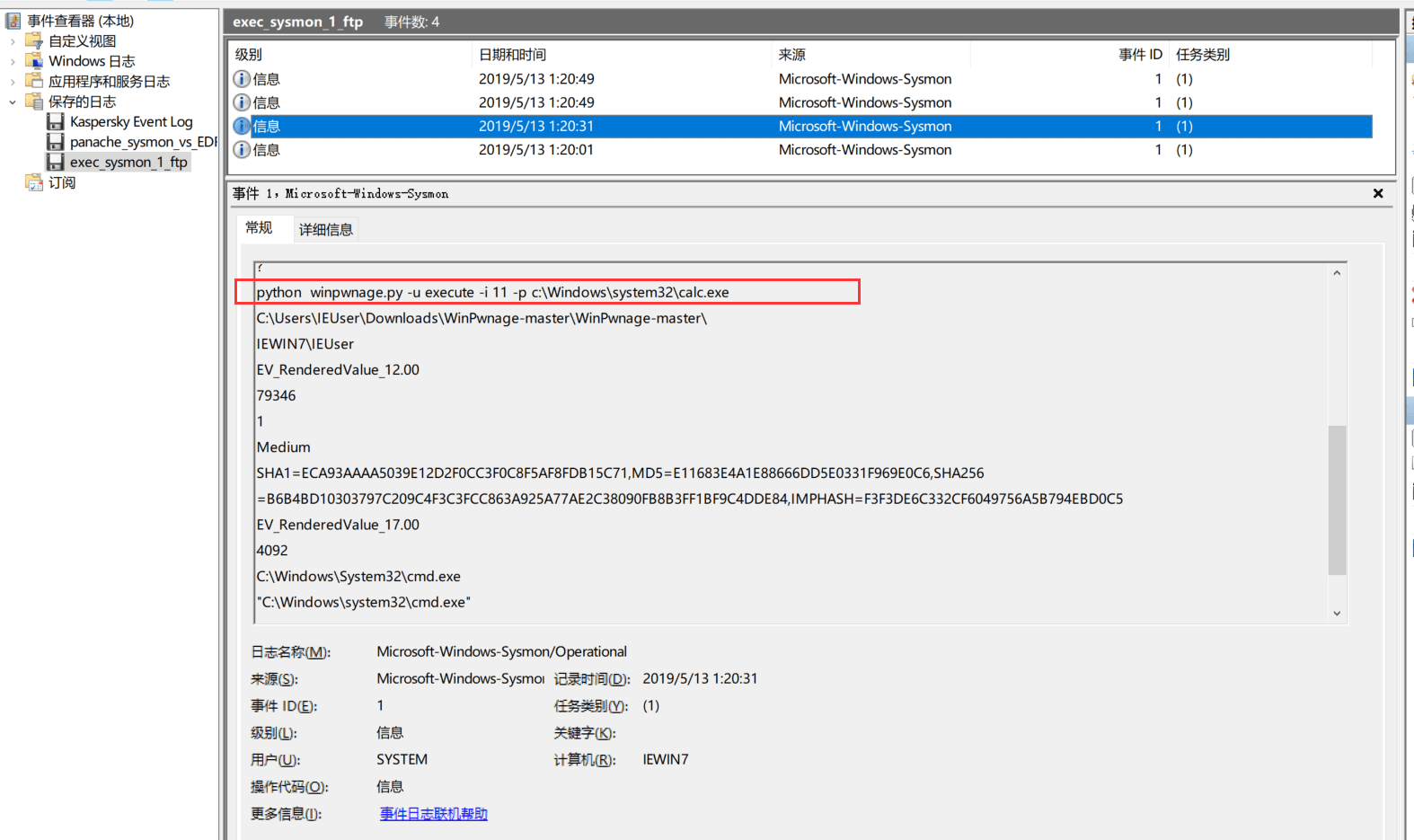
│ exec_sysmon_1_ftp.evtx
│ exec_sysmon_1_lolbin_pcalua.evtx
│ exec_sysmon_1_lolbin_renamed_regsvr32_scrobj.evtx
│ exec_sysmon_1_lolbin_rundll32_advpack_RegisterOCX.evtx
│ exec_sysmon_1_rundll32_pcwutl_LaunchApplication.evtx
│ exec_sysmon_lobin_regsvr32_sct.evtx
│ Exec_sysmon_meterpreter_reversetcp_msipackage.evtx
│ Exec_via_cpl_Application_Experience_EventID_17_ControlPanelApplet.evtx
│ exec_wmic_xsl_internet_sysmon_3_1_11.evtx
│ revshell_cmd_svchost_sysmon_1.evtx
│ rogue_msi_url_1040_1042.evtx
│ susp_explorer_exec.evtx
│ susp_explorer_exec_root_cmdline_@[email protected]
│ sysmon_11_1_lolbas_downldr_desktopimgdownldr.evtx
│ sysmon_1_11_rundll32_cpl_ostap.evtx
│ Sysmon_Exec_CompiledHTML.evtx
│ sysmon_exec_from_vss_persistence.evtx
│ sysmon_lolbas_rundll32_zipfldr_routethecall_shell.evtx
│ sysmon_lolbin_bohops_vshadow_exec.evtx
│ Sysmon_meterpreter_ReflectivePEInjection_to_notepad_.evtx
│ sysmon_mshta_sharpshooter_stageless_meterpreter.evtx
│ sysmon_vbs_sharpshooter_stageless_meterpreter.evtx
│ temp_scheduled_task_4698_4699.evtx
│ windows_bits_4_59_60_lolbas desktopimgdownldr.evtx
│
├─Lateral Movement
│ DFIR_RDP_Client_TimeZone_RdpCoreTs_104_example.evtx
│ LM_4624_mimikatz_sekurlsa_pth_source_machine.evtx
│ LM_5145_Remote_FileCopy.evtx
│ LM_add_new_namedpipe_tp_nullsession_registry_turla_like_ttp.evtx
│ LM_DCOM_MSHTA_LethalHTA_Sysmon_3_1.evtx
│ LM_dcom_shwnd_shbrwnd_mmc20_failed_traces_system_10016.evtx
│ LM_impacket_docmexec_mmc_sysmon_01.evtx
│ LM_PowershellRemoting_sysmon_1_wsmprovhost.evtx
│ LM_REMCOM_5145_TargetHost.evtx
│ LM_Remote_Service01_5145_svcctl.evtx
│ LM_Remote_Service02_7045.evtx
│ LM_renamed_psexecsvc_5145.evtx
│ LM_ScheduledTask_ATSVC_target_host.evtx
│ lm_sysmon_18_remshell_over_namedpipe.evtx
│ LM_sysmon_1_12_13_3_tsclient_SharpRdp.evtx
│ LM_sysmon_3_12_13_1_SharpRDP.evtx
│ LM_sysmon_3_DCOM_ShellBrowserWindow_ShellWindows.evtx
│ LM_sysmon_psexec_smb_meterpreter.evtx
│ LM_tsclient_startup_folder.evtx
│ LM_typical_IIS_webshell_sysmon_1_10_traces.evtx
│ LM_winrm_exec_sysmon_1_winrshost.evtx
│ LM_winrm_target_wrmlogs_91_wsmanShellStarted_poorLog.evtx
│ LM_WMIC_4648_rpcss.evtx
│ LM_wmiexec_impacket_sysmon_whoami.evtx
│ LM_WMI_4624_4688_TargetHost.evtx
│ LM_wmi_PoisonHandler_Mr-Un1k0d3r_sysmon_1_13.evtx
│ LM_xp_cmdshell_MSSQL_Events.evtx
│ MSSQL_15281_xp_cmdshell_exec_failed_attempt.evtx
│ net_share_drive_5142.evtx
│ powercat_revShell_sysmon_1_3.evtx
│ remote task update 4624 4702 same logonid.evtx
│ RemotePowerShell_MS_Windows-Remote_Management_EventID_169.evtx
│ remote_file_copy_system_proc_file_write_sysmon_11.evtx
│ sharprdp_sysmon_7_mstscax.dll.evtx
│ smb_bi_auth_conn_spoolsample.evtx
│ spoolsample_5145.evtx
│ sysmon_1_exec_via_sql_xpcmdshell.evtx
│
├─Other
│ │ netlogon_log_CVE-2020-1472_ZeroLogon.txt
│ │ rdpcorets_148_mst120_bluekeep_rpdscan_full.evtx
│ │
│ └─emotet
│ exec_emotet_ps_4104.evtx
│ exec_emotet_ps_800_get-item.evtx
│ exec_emotet_ps_800_invoke-item.evtx
│ exec_emotet_ps_800_new-item.evtx
│ exec_emotet_ps_800_new-object.evtx
│ exec_emotet_sysmon_1.evtx
│ README.md
│
├─Persistence
│ DACL_DCSync_Right_Powerview_ Add-DomainObjectAcl.evtx
│ evasion_persis_hidden_run_keyvalue_sysmon_13.evtx
│ Network_Service_Guest_added_to_admins_4732.evtx
│ persistence_accessibility_features_osk_sysmon1.evtx
│ persistence_pendingGPO_sysmon_13.evtx
│ persistence_security_dcshadow_4742.evtx
│ Persistence_Shime_Microsoft-Windows-Application-Experience_Program-Telemetry_500.evtx
│ persistence_SilentProcessExit_ImageHijack_sysmon_13_1.evtx
│ persistence_startup_UserShellStartup_Folder_Changed_sysmon_13.evtx
│ persistence_sysmon_11_13_1_shime_appfix.evtx
│ Persistence_Winsock_Catalog Change EventId_1.evtx
│ persist_bitsadmin_Microsoft-Windows-Bits-Client-Operational.evtx
│ persist_firefox_comhijack_sysmon_11_13_7_1.evtx
│ persist_turla_outlook_backdoor_comhijack.evtx
│ persist_valid_account_guest_rid_hijack.evtx
│ sysmon_13_1_persistence_via_winlogon_shell.evtx
│ sysmon_1_persist_bitsjob_SetNotifyCmdLine.evtx
│ sysmon_1_smss_child_proc_bootexecute_setupexecute.evtx
│ sysmon_20_21_1_CommandLineEventConsumer.evtx
│ sysmon_local_account_creation_and_added_admingroup_12_13.evtx
│ wmighost_sysmon_20_21_1.evtx
│
└─Privilege Escalation
4624 LT3 AnonymousLogon Localhost - JuicyPotato.evtx
4765_sidhistory_add_t1178.evtx
CVE-2020-0796_SMBV3Ghost_LocalPrivEsc_Sysmon_3_1_10.evtx
Invoke_TokenDuplication_UAC_Bypass4624.evtx
PrivEsc_CVE-2020-1313_Sysmon_13_UScheduler_Cmdline.evtx
PrivEsc_Imperson_NetSvc_to_Sys_Decoder_Sysmon_1_17_18.evtx
PrivEsc_NetSvc_SessionToken_Retrival_via_localSMB_Auth_5145.evtx
privesc_registry_symlink_CVE-2020-1377.evtx
privesc_roguepotato_sysmon_17_18.evtx
privesc_rotten_potato_from_webshell_metasploit_sysmon_1_8_3.evtx
PrivEsc_SeImpersonatePriv_enabled_back_for_upnp_localsvc_4698.evtx
privesc_seimpersonate_tosys_spoolsv_sysmon_17_18.evtx
privesc_unquoted_svc_sysmon_1_11.evtx
privexchange_dirkjan.evtx
RogueWinRM.evtx
Runas_4624_4648_Webshell_CreateProcessAsUserA.evtx
security_4624_4673_token_manip.evtx
sysmon_11_1_15_WScriptBypassUAC.evtx
sysmon_11_1_7_uacbypass_cliconfg.evtx
sysmon_11_7_1_uacbypass_windirectory_mocking.evtx
sysmon_13_1_12_11_perfmonUACBypass.evtx
sysmon_13_1_compmgmtlauncherUACBypass.evtx
sysmon_13_1_meterpreter_getsystem_NamedPipeImpersonation.evtx
Sysmon_13_1_UACBypass_SDCLTBypass.evtx
Sysmon_13_1_UAC_Bypass_EventVwrBypass.evtx
sysmon_1_11_exec_as_system_via_schedtask.evtx
sysmon_1_13_11_cmstp_ini_uacbypass.evtx
sysmon_1_13_UACBypass_AppPath_Control.evtx
sysmon_1_7_11_mcx2prov_uacbypass.evtx
sysmon_1_7_11_migwiz.evtx
sysmon_1_7_11_sysprep_uacbypass.evtx
sysmon_1_7_elevate_uacbypass_sysprep.evtx
sysmon_privesc_from_admin_to_system_handle_inheritance.evtx
Sysmon_UACME_22.evtx
Sysmon_UACME_23.evtx
Sysmon_UACME_30.evtx
Sysmon_UACME_32.evtx
Sysmon_UACME_33.evtx
Sysmon_UACME_34.evtx
Sysmon_UACME_36_FileCreate.evtx
Sysmon_UACME_37_FileCreate.evtx
Sysmon_UACME_38.evtx
Sysmon_UACME_39.evtx
Sysmon_UACME_41.evtx
Sysmon_UACME_43.evtx
Sysmon_UACME_45.evtx
Sysmon_UACME_53.evtx
Sysmon_UACME_54.evtx
Sysmon_UACME_56.evtx
Sysmon_uacme_58.evtx
System_7045_namedpipe_privesc.evtx
UACME_61_Changepk.evtx
win10_4703_SeDebugPrivilege_enabled.evtxWinlogbeat批量读取用法:
## 显示帮助信息的命令:
.\Winlogbeat-Bulk-Read.ps1 -Help
##使用默认值运行(读取 ./递归并在你的路径中查找winlogbeat.exe):
.\Winlogbeat-Bulk-Read.ps1
##如果你想把这个脚本指向另一个目录的evtx文件,并指定一个路径到winlogbeat.exe文件:
.\Winlogbeat-Bulk-Read.ps1 -Exe ~\Downloads\winlogbeat\winlogbeat.exe -Source "..\EVTX-ATTACK-SAMPLES\"PS C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master> .\Winlogbeat-Bulk-Read.ps1 -help
名称
C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master\Winlogbeat-Bulk-Read.ps1
摘要
PowerShell loop to read local .evtx files into Elastic's winlogbeat agent.
语法
C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master\Winlogbeat-Bulk-Read.ps1 [[-Source] <S
tring>] [[-Exe] <String>] [[-Config] <String>] [-Append] [-Test] [-Reset] [-Verbose] [-Help] [<CommonParameters>]
说明
PowerShell loop to read local .evtx files into Elastic's winlogbeat agent.
Use winlogbeat.yml to customize your configuration of winlogbeat including output.
This script will attempt to use winlogbeat.yml which is ignored in .gitignore but
if this file is not found, it will fall back to using the example that will output
logs to .\winlogbeat\events.json. Once an EVTX file has been read winlogbeat will
store the file path in winlogbeat.registry_file to prevent reading the same logs.
Remove this file to replay already read files.
Author: Grant Sales
Date: 2020.08.20
参数
-Source <String>
Path to recurse read through to find EVTX files.
-Exe <String>
Path to the winlogbeat.exe binary, when not provided, will look in $path.
-Config <String>
Path to custom winlogbeat configuration. Useful if you have multiple configuration files
used in testing.
-Append [<SwitchParameter>]
When using the example config, will also output events to bulk_events.json.
-Test [<SwitchParameter>]
Test winlogbeat config and exit, will only run a max of 10 times within the loop.
-Reset [<SwitchParameter>]
Reset flag will delete the registry file allowing replay of evtx files that have
already been read once. By default, winlogbeat will read all the files but will not
generate output from an already read file due to bookmarks set in the registry file.
-Verbose [<SwitchParameter>]
Verbose output, this will output file names as they are read and could help in
finding any possible errors.
-Help [<SwitchParameter>]
<CommonParameters>
此 Cmdlet 支持常见参数: Verbose、Debug、
ErrorAction、ErrorVariable、WarningAction、WarningVariable、
OutBuffer、PipelineVariable 和 OutVariable。有关详细信息,请参阅
about_CommonParameters (https:/go.microsoft.com/fwlink/?LinkID=113216)。
-------------------------- 示例 1 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1
-------------------------- 示例 2 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Exe $env:USERPROFILE\Downloads\winlogbeat\winlogbeat-7.8.1-windows-x86_64\winlog
beat.exe -Source "..\EVTX-ATTACK-SAMPLES\"
-------------------------- 示例 3 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Exe$env:USERPROFILE\Downloads\winlogbeat\winlogbeat-7.8.1-windows-x86_64\winlog
beat.exe
-------------------------- 示例 4 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Exe $env:USERPROFILE\Downloads\winlogbeat\winlogbeat-7.8.1-windows-x86_64\winlog
beat.exe -Source "..\EVTX-ATTACK-SAMPLES\" -Config "C:\Dev\winlogbeat-customconfig.yml"
-------------------------- 示例 5 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Exe $env:USERPROFILE\Downloads\winlogbeat\winlogbeat-7.8.1-windows-x86_64\winlog
beat.exe -Append
-------------------------- 示例 6 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Exe "C:\Program Files\winlogbeat\winlogbeat.exe" -Reset -Verbose
-------------------------- 示例 7 --------------------------
PS C:\>.\Winlogbeat-Bulk-Read.ps1 -Help
备注
若要查看示例,请键入: "get-help C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master\Winlog
beat-Bulk-Read.ps1 -examples".
有关详细信息,请键入: "get-help C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master\Winlog
beat-Bulk-Read.ps1 -detailed".
若要获取技术信息,请键入: "get-help C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master\Wi
nlogbeat-Bulk-Read.ps1 -full".
PS C:\Users\ddos1\Desktop\EVTX-ATTACK-SAMPLES-master\EVTX-ATTACK-SAMPLES-master>如果powershell无法运行,请输入该命令 set-ExecutionPolicy RemoteSigned
EVTX和winlogbeat下载地址
雨苁网盘: w.ddosi.workers.dev