目录导航
GitDorker是一个利用GitHub Search API和我从各种来源汇编的GitHub dork的广泛列表来提供给定搜索查询github上存储的敏感信息的工具。
GitDorker的主要目的是为用户提供一个干净且量身定制的攻击工具在GitHub上收集敏感信息。GitDorker可以与其他工具(例如GitRob或Trufflehog)一起使用,或从GitDorker发现的用户使用以产生最佳效果。
速率限制
GitDorker利用GitHub搜索API,每分钟最多只能请求30个请求。为了防止速率限制,每30个请求后,GitDorker就会内置一个睡眠功能以防止搜索失败。因此,如果要运行带有GitDorker的alldorks.txt文件,该过程大约需要5分钟才能完成。
安装条件
** Python3
** GitHub个人访问令牌
**在此存储库的requirements.txt文件中安装需求(pip3 install -r requirements.txt)
如果不确定如何创建个人访问令牌,请遵循以下指南:creating-a-personal-access-token
建议
建议为GitDorker提供至少两个GitHub个人访问令牌,以便它可以在dorking过程中在两个GitHub个人访问令牌之间交替出现,并降低速率受限的可能性。使用来自单独的GitHub帐户的多个令牌将提供最佳结果。
dorks文件夹
在dorks文件夹中是dork的列表。映射github秘密攻击面时,建议使用“ alldorks.txt”文件。“ alldorks.txt”是我从各种资源中提取的傻瓜集合,总共有239个敏感github信息的列表。
GitHub敏感信息关键词列表
".mlab.com password"
"AWSSecretKey"
"JEKYLL_GITHUB_TOKEN"
"SF_USERNAME salesforce"
"access_key"
"access_token"
"amazonaws"
"apiSecret"
"api_key"
"api_secret"
"apidocs"
"apikey"
"app_key"
"app_secret"
"appkey"
"appkeysecret"
"application_key"
"appsecret"
"appspot"
"auth"
"auth_token"
"authorizationToken"
"aws_access"
"aws_access_key_id"
"aws_key"
"aws_secret"
"aws_token"
"bashrc password"
"bucket_password"
"client_secret"
"cloudfront"
"codecov_token"
"config"
"conn.login"
"connectionstring"
"consumer_key"
"credentials"
"database_password"
"db_password"
"db_username"
"dbpasswd"
"dbpassword"
"dbuser"
"dot-files"
"dotfiles"
"encryption_key"
"fabricApiSecret"
"fb_secret"
"firebase"
"ftp"
"gh_token"
"github_key"
"github_token"
"gitlab"
"gmail_password"
"gmail_username"
"api.googlemaps AIza"
"herokuapp"
"internal"
"irc_pass"
"key"
"keyPassword"
"ldap_password"
"ldap_username"
"login"
"mailchimp"
"mailgun"
"master_key"
"mydotfiles"
"mysql"
"node_env"
"npmrc _auth"
"oauth_token"
"pass"
"passwd"
"password"
"passwords"
"pem private"
"preprod"
"private_key"
"prod"
"pwd"
"pwds"
"rds.amazonaws.com password"
"redis_password"
"root_password"
"secret"
"secret.password"
"secret_access_key"
"secret_key"
"secret_token"
"secrets"
"secure"
"security_credentials"
"send.keys"
"send_keys"
"sendkeys"
"sf_username"
"slack_api"
"slack_token"
"sql_password"
"ssh"
"ssh2_auth_password"
"sshpass"
"staging"
"stg"
"storePassword"
"stripe"
"swagger"
"testuser"
"token"
"x-api-key"
"xoxp"
"xoxb "
HEROKU_API_KEY language:json
HEROKU_API_KEY language:shell
HOMEBREW_GITHUB_API_TOKEN language:shell
PT_TOKEN language:bash
[WFClient] Password= extension:ica
extension:avastlic "support.avast.com"
extension:bat
extension:cfg
extension:env
extension:exs
extension:ini
extension:json api.forecast.io
extension:json googleusercontent client_secret
extension:json mongolab.com
extension:pem
extension:pem private
extension:ppk
extension:ppk private
extension:properties
extension:sh
extension:sls
extension:sql
extension:sql mysql dump
extension:sql mysql dump password
extension:yaml mongolab.com
extension:zsh
filename:.bash_history
filename:.bash_profile aws
filename:.bashrc mailchimp
filename:.bashrc password
filename:.cshrc
filename:.dockercfg auth
filename:.env DB_USERNAME NOT homestead
filename:.env MAIL_HOST=smtp.gmail.com
filename:.esmtprc password
filename:.ftpconfig
filename:.git-credentials
filename:.history
filename:.htpasswd
filename:.netrc password
filename:.npmrc _auth
filename:.pgpass
filename:.remote-sync.json
filename:.s3cfg
filename:.sh_history
filename:.tugboat NOT _tugboat
filename:CCCam.cfg
filename:WebServers.xml
filename:_netrc password
filename:bash
filename:bash_history
filename:bash_profile
filename:bashrc
filename:beanstalkd.yml
filename:composer.json
filename:config
filename:config irc_pass
filename:config.json auths
filename:config.php dbpasswd
filename:configuration.php JConfig password
filename:connections
filename:connections.xml
filename:constants
filename:credentials
filename:credentials aws_access_key_id
filename:cshrc
filename:database
filename:dbeaver-data-sources.xml
filename:deploy.rake
filename:deployment-config.json
filename:dhcpd.conf
filename:dockercfg
filename:environment
filename:express.conf
filename:express.conf path:.openshift
filename:filezilla.xml
filename:filezilla.xml Pass
filename:git-credentials
filename:gitconfig
filename:global
filename:history
filename:htpasswd
filename:hub oauth_token
filename:id_dsa
filename:id_rsa
filename:id_rsa or filename:id_dsa
filename:idea14.key
filename:known_hosts
filename:logins.json
filename:makefile
filename:master.key path:config
filename:netrc
filename:npmrc
filename:pass
filename:passwd path:etc
filename:pgpass
filename:prod.exs
filename:prod.exs NOT prod.secret.exs
filename:prod.secret.exs
filename:proftpdpasswd
filename:recentservers.xml
filename:recentservers.xml Pass
filename:robomongo.json
filename:s3cfg
filename:secrets.yml password
filename:server.cfg
filename:server.cfg rcon password
filename:settings
filename:settings.py SECRET_KEY
filename:sftp-config.json
filename:sftp.json path:.vscode
filename:shadow
filename:shadow path:etc
filename:spec
filename:sshd_config
filename:tugboat
filename:ventrilo_srv.ini
filename:wp-config
filename:wp-config.php
filename:zhrc
jsforce extension:js conn.login
language:yaml -filename:travis
msg nickserv identify filename:config
path:sites databases password
private -language:java
shodan_api_key language:python用法
我已经在这里创建了一个博客文章,其中详细介绍了如何使用GitDorker和潜在用例:-Wins-92a0a0a6b8d5
git clone https://github.com/obheda12/GitDorker
pip3 install -r requirements.txtpython3 GitDorker.py -h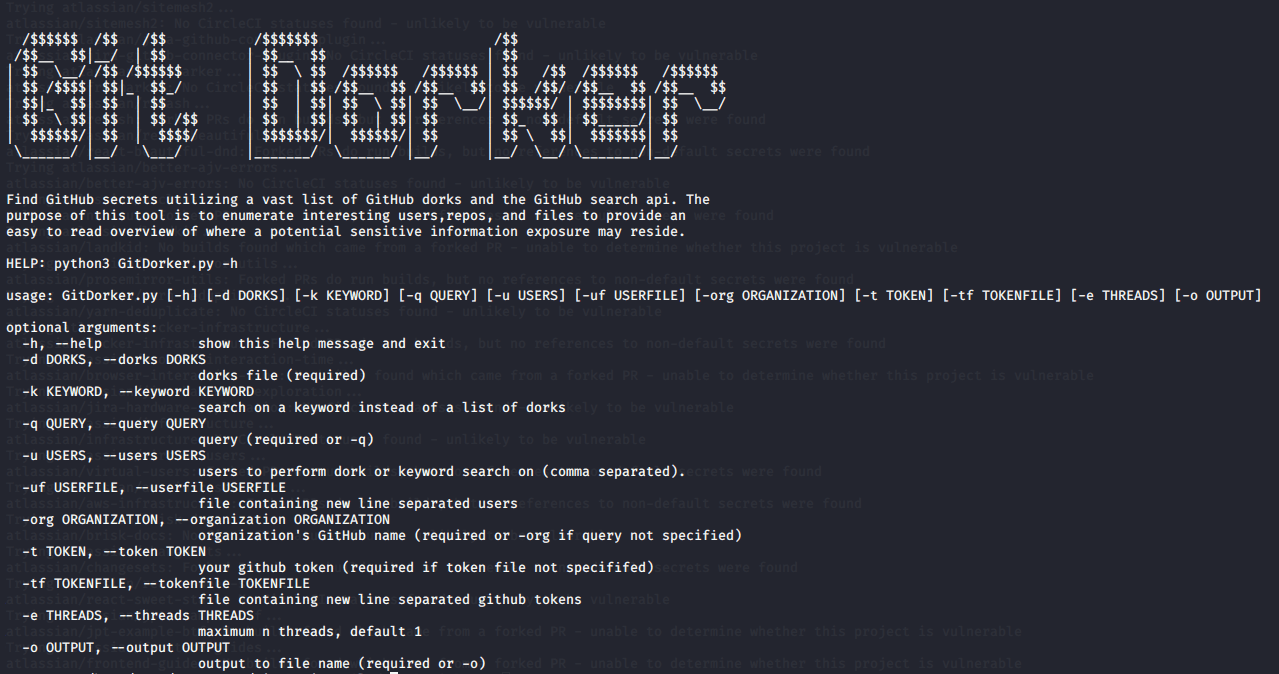
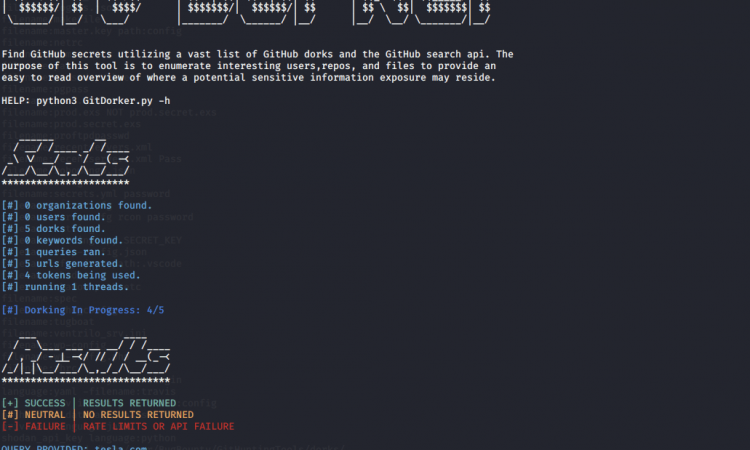
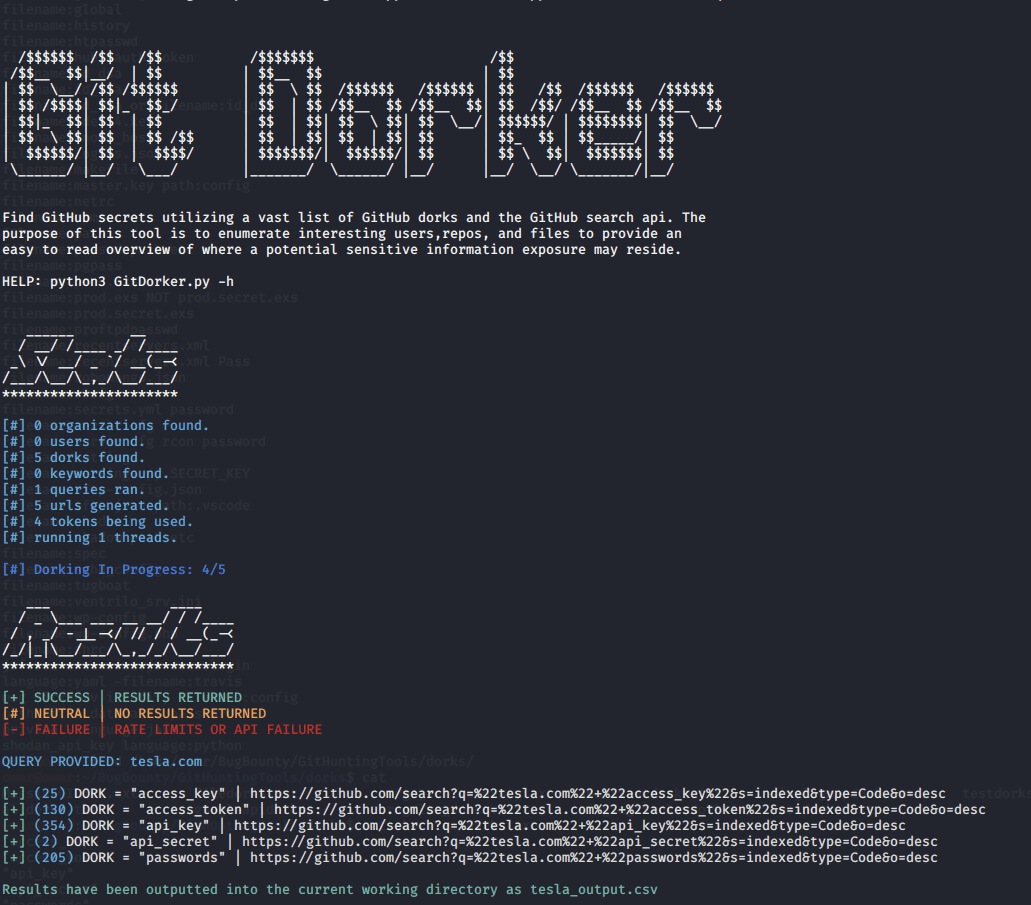
python3 GitDorker.py -tf *tokensfile* -org teslamotors -d *dorksfile* -o *outputfile*下面是使用dorks文件的终端中标准输出的示例。
在此示例中,我们将使用“ -q ”开关和“ tesla.com ”作为我们的目标域。
python3 GitDorker.py -tf tokensfile.txt -q tesla.com -d dorks / demo_dorks.txt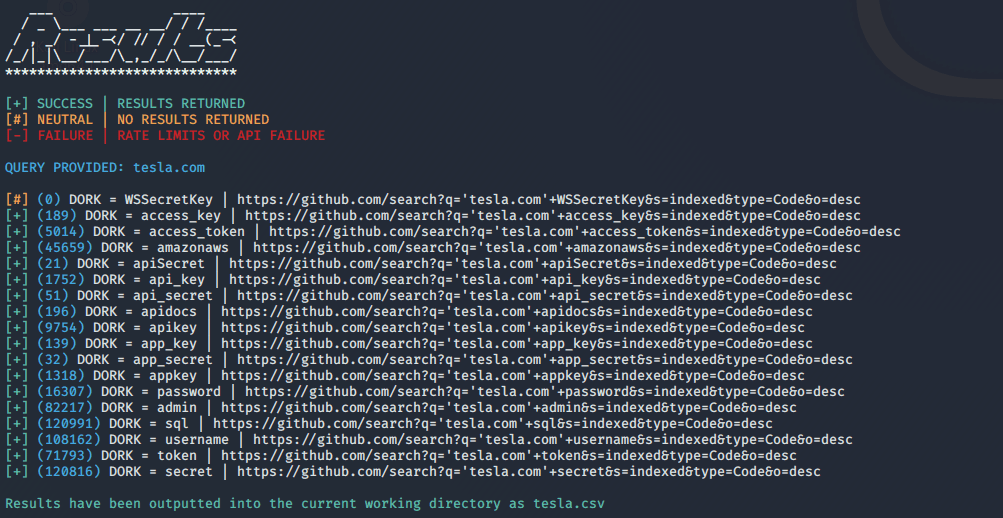
以下是在excel中打开并根据结果数量进行过滤以方便分析的相应CSV输出。

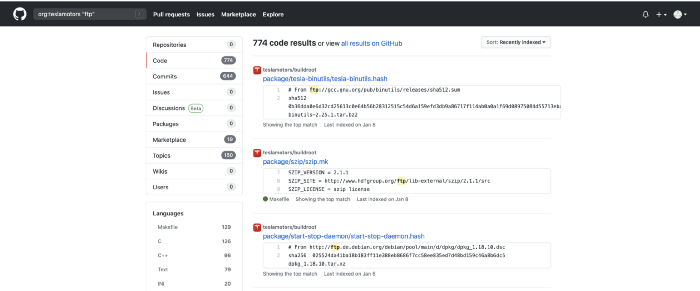
如您所见,将为每个dork生成自定义搜索查询的URL以及供参考的结果数。我们将访问为“ ftp ”文件生成的链接,并分析我们的结果。
下载地址
①GitHub: GitDorker-master.zip
②雨苁网盘:w.ddosi.workers.dev
③迅雷网盘:pan.xunlei.com 提取码:T4CE
④蓝奏云: waf.lanzoui.com