目录导航
项目介绍
HaE是基于 BurpSuite Java插件API 开发的请求高亮标记与信息提取的辅助型框架式插件,该插件可以通过自定义正则的方式匹配响应报文或请求报文,并对满足正则匹配的报文进行信息高亮与提取。
现代化Web应用走上前后端分离开发模式,这就导致在日常测试时候会有许多的流量,如果你想要尽可能全面的对一个Web应用进行测试评估,将花费大量精力浪费在无用的报文上;HaE的出现正是为了解决这一类似场景,借助HaE你可以有效的减少测试的时间,将更多的精力放在有价值、有意义的报文上,提高漏洞挖掘效率。
注: 要想灵活的使用HaE,你需要掌握正则表达式阅读、编写、修改能力;由于Java正则表达式的库并没有Python的优雅或方便,所以HaE要求使用者必须用()将所需提取的表达式内容包含;例如你要匹配一个Shiro应用的响应报文,正常匹配规则为rememberMe=delete,如果你要提取这段内容的话就需要变成(rememberMe=delete)。
使用方法
插件装载: Extender - Extensions - Add - Select File - Next
初次装载HaE会初始化配置文件,默认配置文件内置一个正则: Email,初始化的配置文件会放在的/用户根目录/.config/HaE/目录下。
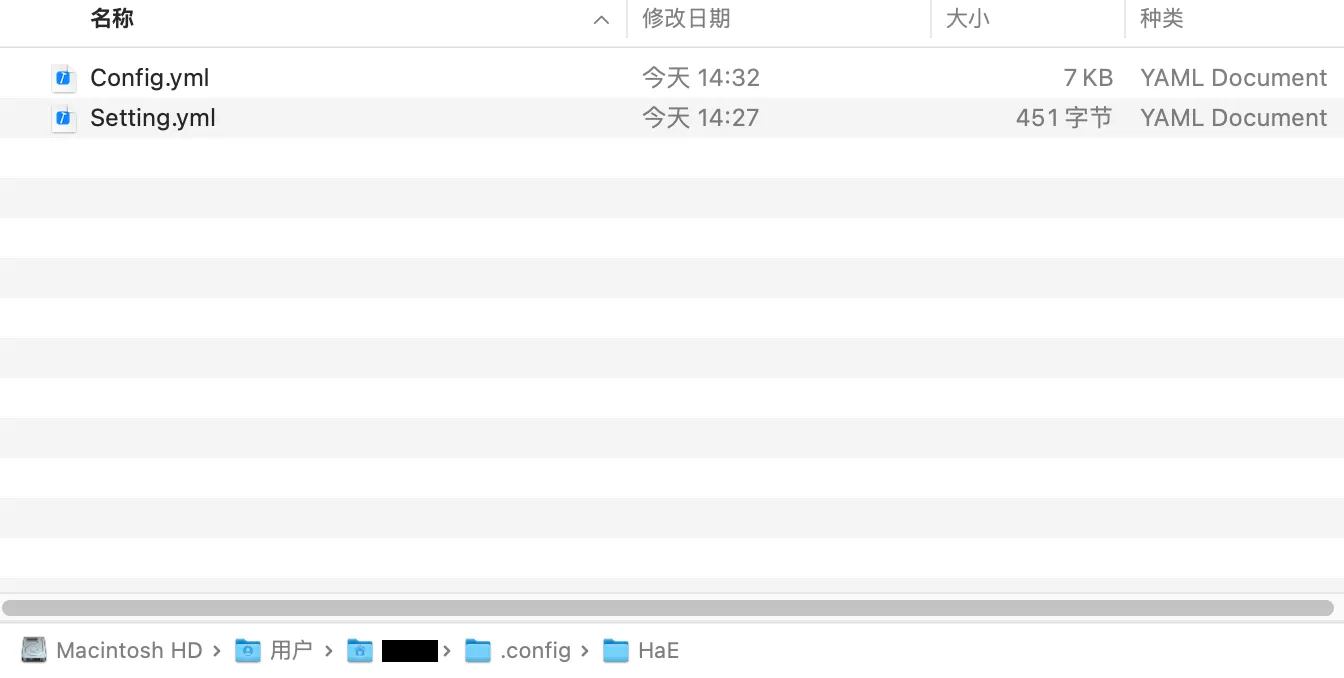
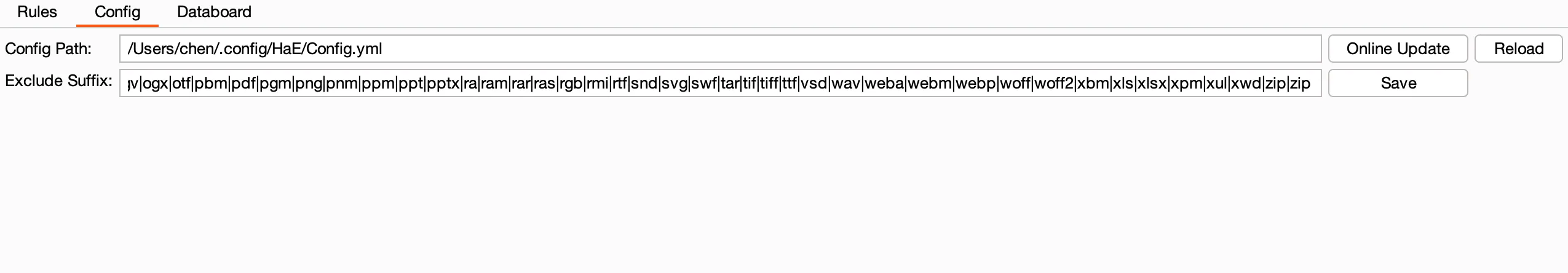
除了初始化的配置文件外,还有Setting.yml,该文件用于存储配置文件路径与排除后缀名;HaE支持在线更新配置文件,你可以通过点击Online Update按钮进行更新(部分网络需要挂代理)。
优势特点
- 精细化配置项:高自由度配置更适配精细化场景需求;
- 简洁可视界面:简洁的可视化界面让你更加清晰了解HaE的各项配置,操作更轻松,使用更简单;
- 颜色升级算法:内置颜色升级算法,避免“屠龙者终成恶龙”场景,突出最具价值的请求;
- 标签化规则项:标签化你的正则规则,让规则可分类,让管理更轻松;
- 数据集合面板:将所有匹配数据集合到Databoard中,使得测试、梳理更高效;
- 高亮标记一体:在Proxy – History页面你可以通过颜色高亮与Comment判断请求价值;
- 实战化官方库:基于实战化场景、案例进行输出的官方规则库,提升测试实战性;
- 配置文件易读:配置文件使用YAML格式存储,更加便于阅读与修改。
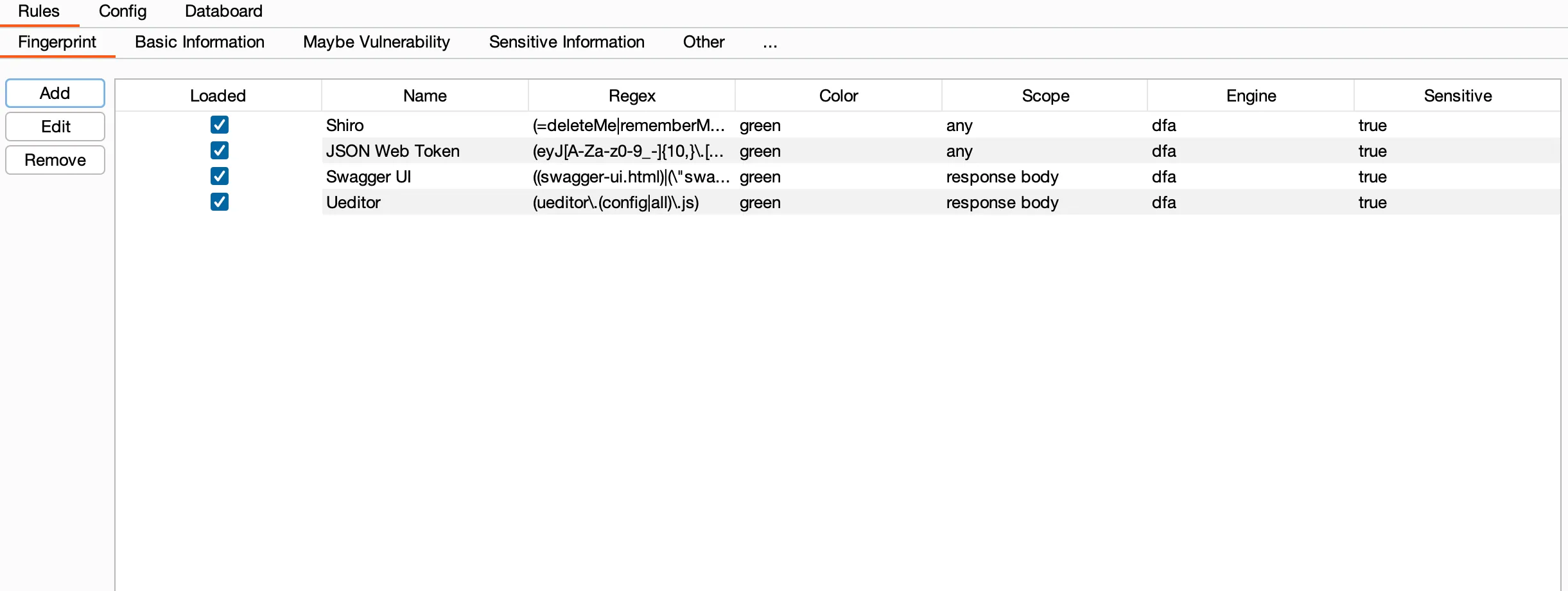
Rules(规则信息管理)
Config(配置信息管理)
Databoard(数据集合面板)
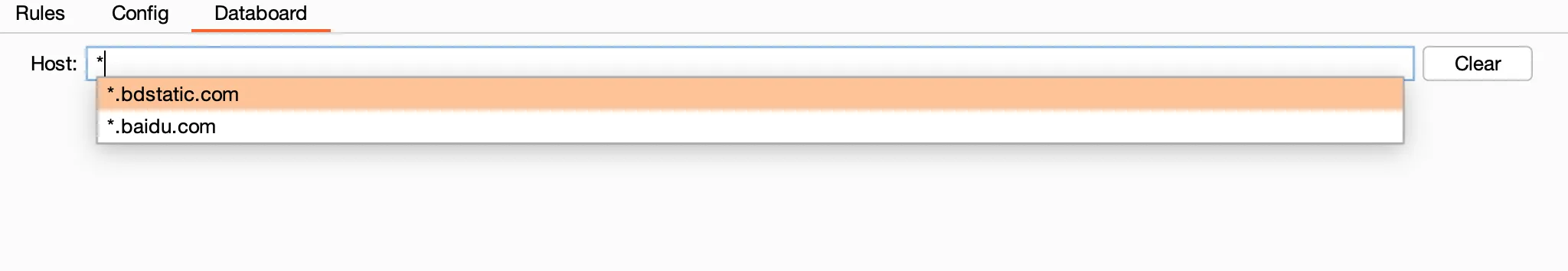
实际使用
使用 RGPerson 生成测试数据,放入网站根目录文件中:
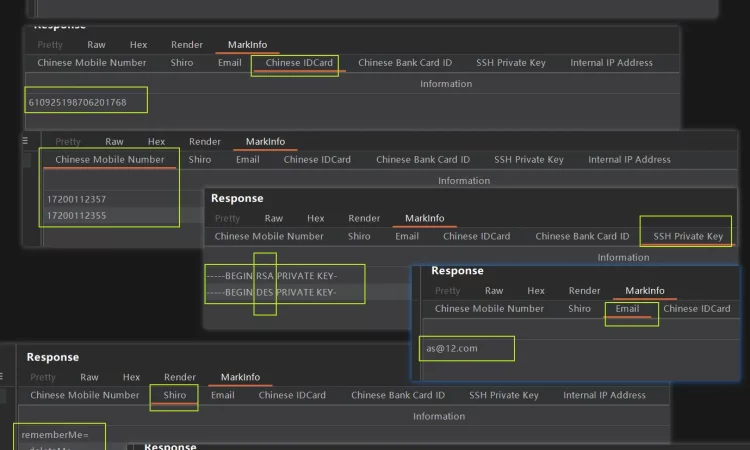
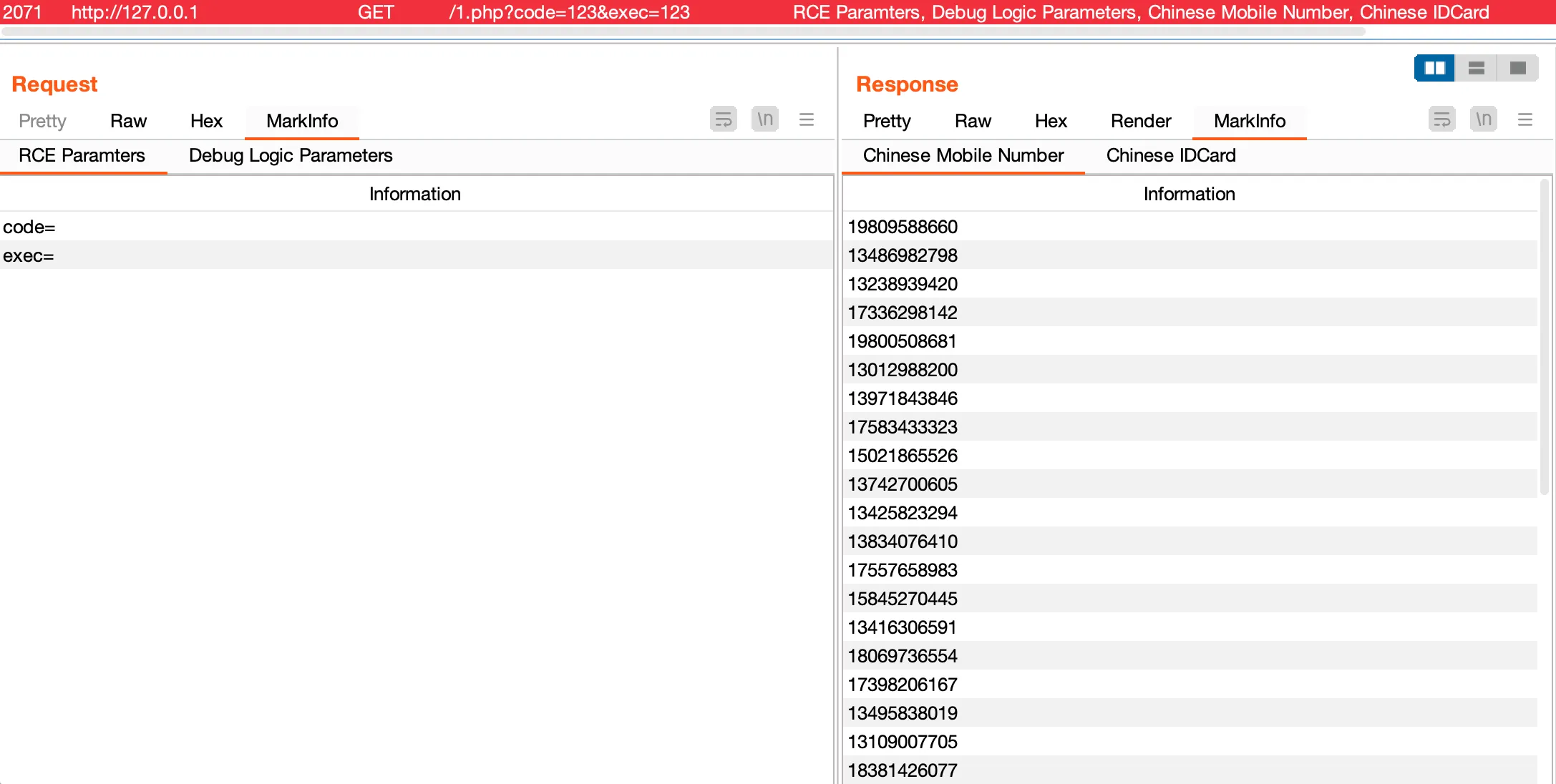
访问该地址,在Proxy - HTTP History中可以看见高亮请求,响应标签页中含有MarkINFO标签,其中将匹配到的信息提取了出来。
下载地址
①GitHub
- HaE-2.4.5-J8.jar 1.04 MB
- HaE-2.4.5-J9.jar 1.04 MB
②云中转网盘
③burp应用商店安装
注意:应用商店的版本比github低一个数量级.(2.4.4),建议直接在GitHub下载安装.
公开规则库
自带规则库仅有一个,可以自行下载如下规则库替换原始的Config.yml,然后reload即可.
配置文件位置
%UserProfile%/.config/HaE/Config.yml地址:
gh0stkey/HaE/gh-pages/Config.yml
规则:
rules:
- rule:
- color: green
engine: dfa
loaded: true
name: Shiro
regex: (=deleteMe|rememberMe=)
scope: any
sensitive: true
- color: green
engine: dfa
loaded: true
name: JSON Web Token
regex: (eyJ[A-Za-z0-9_-]{10,}\.[A-Za-z0-9._-]{10,}|eyJ[A-Za-z0-9_\/+-]{10,}\.[A-Za-z0-9._\/+-]{10,})
scope: any
sensitive: true
- color: green
engine: dfa
loaded: true
name: Swagger UI
regex: ((swagger-ui.html)|(\"swagger\":)|(Swagger UI)|(swaggerUi))
scope: response body
sensitive: true
- color: green
engine: dfa
loaded: true
name: Ueditor
regex: (ueditor\.(config|all)\.js)
scope: response body
sensitive: true
type: Fingerprint
- rule:
- color: yellow
engine: nfa
loaded: true
name: Email
regex: (([a-z0-9][_|\.])*[a-z0-9]+@([a-z0-9][-|_|\.])*[a-z0-9]+\.((?!js|css|jpg|jpeg|png|ico)[a-z]{2,}))
scope: response
sensitive: false
- color: orange
engine: nfa
loaded: true
name: Chinese IDCard
regex: '[^0-9]((\d{8}(0\d|10|11|12)([0-2]\d|30|31)\d{3}$)|(\d{6}(18|19|20)\d{2}(0[1-9]|10|11|12)([0-2]\d|30|31)\d{3}(\d|X|x)))[^0-9]'
scope: response body
sensitive: true
- color: orange
engine: nfa
loaded: true
name: Chinese Mobile Number
regex: '[^\w]((?:(?:\+|00)86)?1(?:(?:3[\d])|(?:4[5-79])|(?:5[0-35-9])|(?:6[5-7])|(?:7[0-8])|(?:8[\d])|(?:9[189]))\d{8})[^\w]'
scope: response body
sensitive: true
- color: cyan
engine: nfa
loaded: true
name: Internal IP Address
regex: '[^0-9]((127\.0\.0\.1)|(10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(172\.((1[6-9])|(2\d)|(3[01]))\.\d{1,3}\.\d{1,3})|(192\.168\.\d{1,3}\.\d{1,3}))'
scope: response
sensitive: true
- color: green
engine: nfa
loaded: true
name: MAC Address
regex: (^([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5})|[^a-zA-Z0-9]([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5}))
scope: response
sensitive: true
- color: orange
engine: nfa
loaded: false
name: Chinese Bank Card ID
regex: '[^0-9]([1-9]\d{12,18})[^0-9]'
scope: response
sensitive: true
type: Basic Information
- rule:
- color: cyan
engine: dfa
loaded: true
name: RCE Paramters
regex: ((cmd=)|(exec=)|(command=)|(execute=)|(ping=)|(query=)|(jump=)|(code=)|(reg=)|(do=)|(func=)|(arg=)|(option=)|(load=)|(process=)|(step=)|(read=)|(function=)|(feature=)|(exe=)|(module=)|(payload=)|(run=)|(daemon=)|(upload=)|(dir=)|(download=)|(log=)|(ip=)|(cli=))
scope: request
sensitive: true
- color: yellow
engine: dfa
loaded: true
name: Java Deserialization
regex: (javax\.faces\.ViewState)
scope: response
sensitive: true
- color: cyan
engine: dfa
loaded: true
name: Debug Logic Parameters
regex: ((access=)|(adm=)|(admin=)|(alter=)|(cfg=)|(clone=)|(config=)|(create=)|(dbg=)|(debug=)|(delete=)|(disable=)|(edit=)|(enable=)|(exec=)|(execute=)|(grant=)|(load=)|(make=)|(modify=)|(rename=)|(reset=)|(root=)|(shell=)|(test=)|(toggl=))
scope: request
sensitive: true
- color: cyan
engine: nfa
loaded: true
name: URL As A Value
regex: (=(https?://.*|https?%3(a|A)%2(f|F)%2(f|F).*))
scope: request
sensitive: true
- color: yellow
engine: dfa
loaded: true
name: Upload Form
regex: (type=\"file\")
scope: response body
sensitive: true
- color: cyan
engine: nfa
loaded: true
name: DoS Paramters
regex: ((size=)|(page=)|(num=))
scope: request
sensitive: false
- color: yellow
engine: nfa
loaded: true
name: JSONP Response
regex: (^(\w.*?)\()
scope: response body
sensitive: false
type: Maybe Vulnerability
- rule:
- color: yellow
engine: dfa
loaded: true
name: OSS
regex: ([A|a]ccess[K|k]ey[I|i][d|D]|[A|a]ccess[K|k]ey[S|s]ecret)
scope: any
sensitive: true
- color: green
engine: nfa
loaded: true
name: Amazon AWS URL
regex: (((([a-zA-Z0-9._-]+\.s3|s3)(\.|\-)+[a-zA-Z0-9._-]+|[a-zA-Z0-9._-]+\.s3|s3)\.amazonaws\.com)|(s3:\/\/[a-zA-Z0-9-\.\_]+)|(s3.console.aws.amazon.com\/s3\/buckets\/[a-zA-Z0-9-\.\_]+)|(amzn\.mws\.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12})|(ec2-[0-9-]+.cd-[a-z0-9-]+.compute.amazonaws.com)|(us[_-]?east[_-]?1[_-]?elb[_-]?amazonaws[_-]?com))
scope: response body
sensitive: true
- color: green
engine: nfa
loaded: true
name: Amazon AWS AccessKey ID
regex: '[^0-9]((aws(.{0,20})?(?-i)[''\"][0-9a-zA-Z\/+]{40}[''\"])|((A3T[A-Z0-9]|AKIA|AGPA|AIDA|AROA|AIPA|ANPA|ANVA|ASIA)[a-zA-Z0-9]{16}))[^0-9]'
scope: response body
sensitive: true
- color: green
engine: nfa
loaded: true
name: Amazon AWS Region
regex: ((us(-gov)?|ap|ca|cn|eu|sa)-(central|(north|south)?(east|west)?)-\d)
scope: response body
sensitive: true
- color: blue
engine: nfa
loaded: true
name: SSH Private Key
regex: ([-]+BEGIN [^\s]+ PRIVATE KEY[-])
scope: response body
sensitive: true
- color: green
engine: nfa
loaded: true
name: Windows File/Dir Path
regex: '[^\w](([a-zA-Z]:\\(?:\w+\\?)*)|([a-zA-Z]:\\(?:\w+\\)*\w+\.\w+))'
scope: response
sensitive: true
- color: yellow
engine: nfa
loaded: true
name: Password Field
regex: ((|'|")([p](ass|wd|asswd|assword))(|'|")(:|=)( |)('|")(.*?)('|")(|,))
scope: response body
sensitive: false
- color: green
engine: nfa
loaded: true
name: Username Field
regex: ((|'|")([u](ser|name|ame|sername))(|'|")(:|=)( |)('|")(.*?)('|")(|,))
scope: response body
sensitive: false
- color: green
engine: dfa
loaded: true
name: WeCom Key
regex: ([c|C]or[p|P]id|[c|C]orp[s|S]ecret)
scope: response body
sensitive: true
- color: yellow
engine: nfa
loaded: true
name: JDBC Connection
regex: (jdbc:[a-z:]+://[a-z0-9\.\-_:;=/@?,&]+)
scope: any
sensitive: false
- color: yellow
engine: nfa
loaded: true
name: Authorization Header
regex: ((basic [a-z0-9=:_\+\/-]{5,100})|(bearer [a-z0-9_.=:_\+\/-]{5,100}))
scope: response body
sensitive: false
- color: green
engine: nfa
loaded: true
name: Github Access Token
regex: ([a-z0-9_-]*:[a-z0-9_\-]+@github\.com*)
scope: response body
sensitive: false
- color: cyan
engine: nfa
loaded: true
name: Microsoft Teams Webhook
regex: (https://outlook\.office\.com/webhook/[a-z0-9@-]+/IncomingWebhook/[a-z0-9-]+/[a-z0-9-]+)
scope: response body
sensitive: false
- color: cyan
engine: nfa
loaded: true
name: Zoho Webhook
regex: (https://creator\.zoho\.com/api/[a-z0-9/_.-]+\?authtoken=[a-z0-9]+)
scope: response body
sensitive: false
- color: cyan
engine: nfa
loaded: true
name: Sonarqube Token
regex: (sonar.{0,50}(?:"|\'|`)?[0-9a-f]{40}(?:"|\'|`)?)
scope: response body
sensitive: false
type: Sensitive Information
- rule:
- color: gray
engine: nfa
loaded: true
name: Linkfinder
regex: (?:"|')(((?:[a-zA-Z]{1,10}://|//)[^"'/]{1,}\.[a-zA-Z]{2,}[^"']{0,})|((?:/|\.\./|\./)[^"'><,;|*()(%%$^/\\\[\]][^"'><,;|()]{1,})|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{1,}\.(?:[a-zA-Z]{1,4}|action)(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{3,}(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-]{1,}\.(?:php|asp|aspx|jsp|json|action|html|js|txt|xml)(?:[\?|#][^"|']{0,}|)))(?:"|')
scope: response body
sensitive: true
- color: pink
engine: dfa
loaded: true
name: Source Map
regex: (\.js\.map)
scope: response body
sensitive: true
- color: magenta
engine: nfa
loaded: true
name: HTML Notes
regex: (<!--[\s\S]*?-->)
scope: response body
sensitive: true
- color: green
engine: dfa
loaded: true
name: Create Script
regex: (createElement\(\"script\"\))
scope: response body
sensitive: true
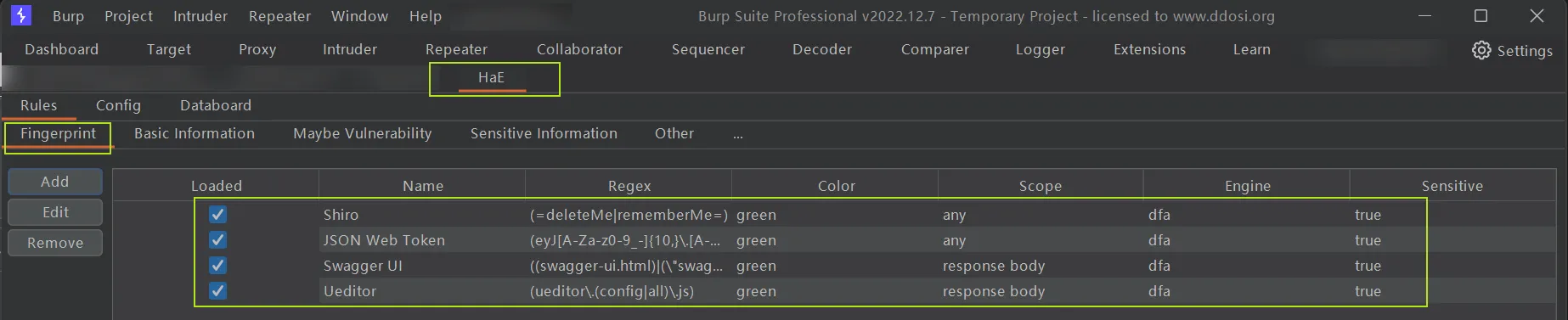
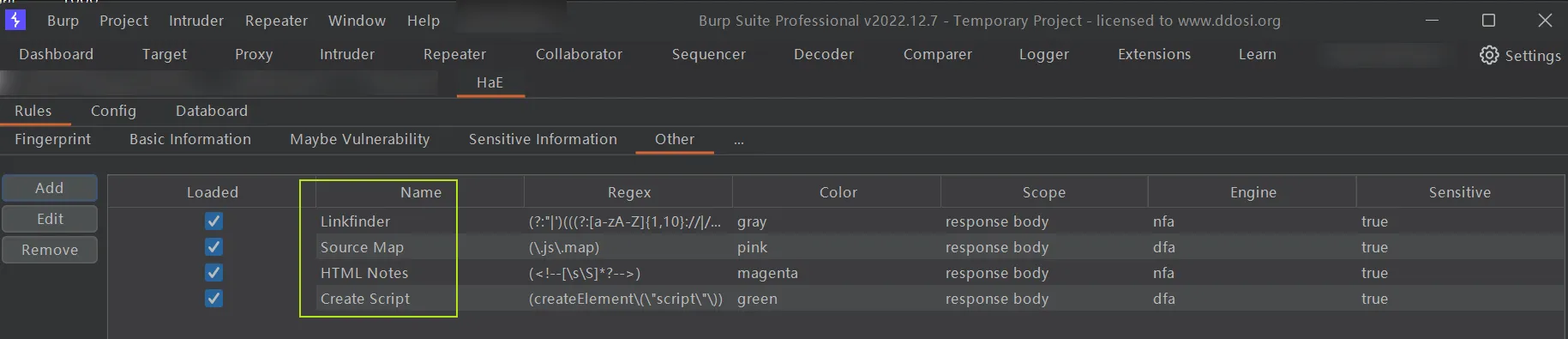
type: Other配置好以后该插件目前就可以检测到如下这些东西了
Shiro
JSON Web Token
Swagger UI
Ueditor
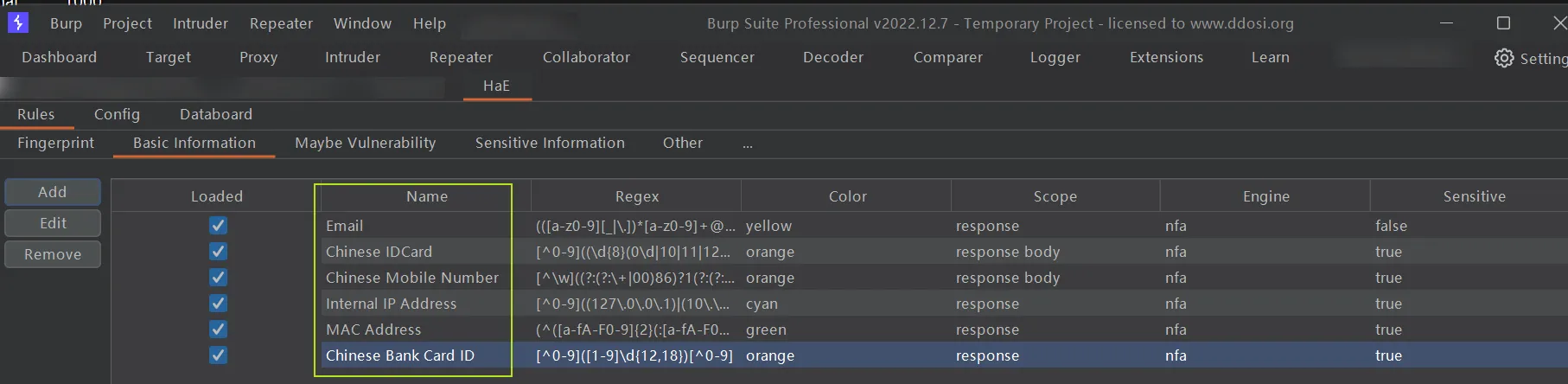
Email
Chinese IDCard
Chinese Mobile Number
Internal IP Address
MAC Address
Chinese Bank Card ID
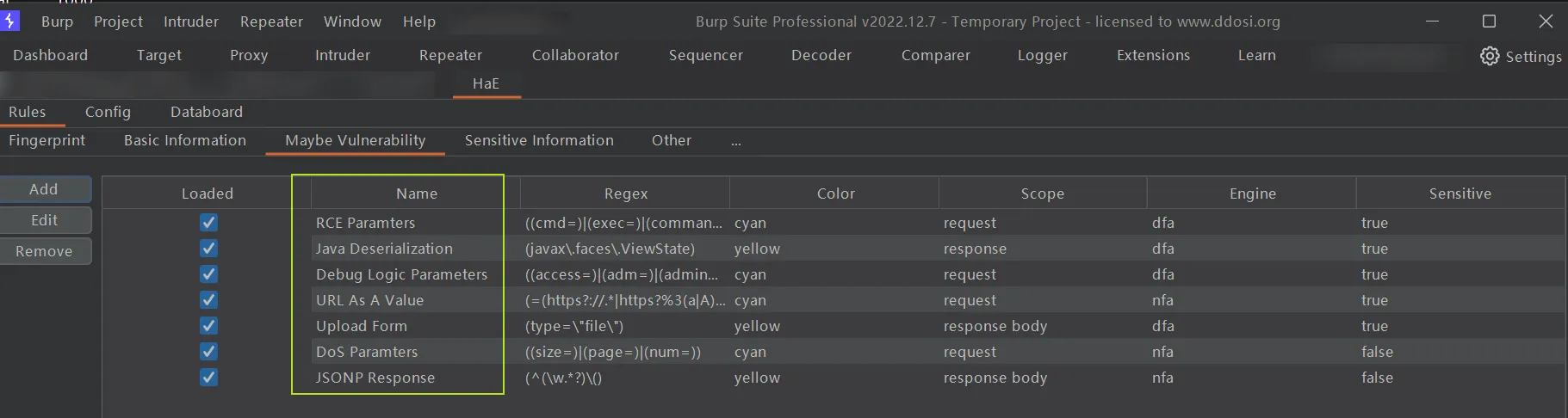
RCE Paramters
Java Deserialization
Debug Logic Parameters
URL As A Value
Upload Form
DoS Paramters
JSONP Response
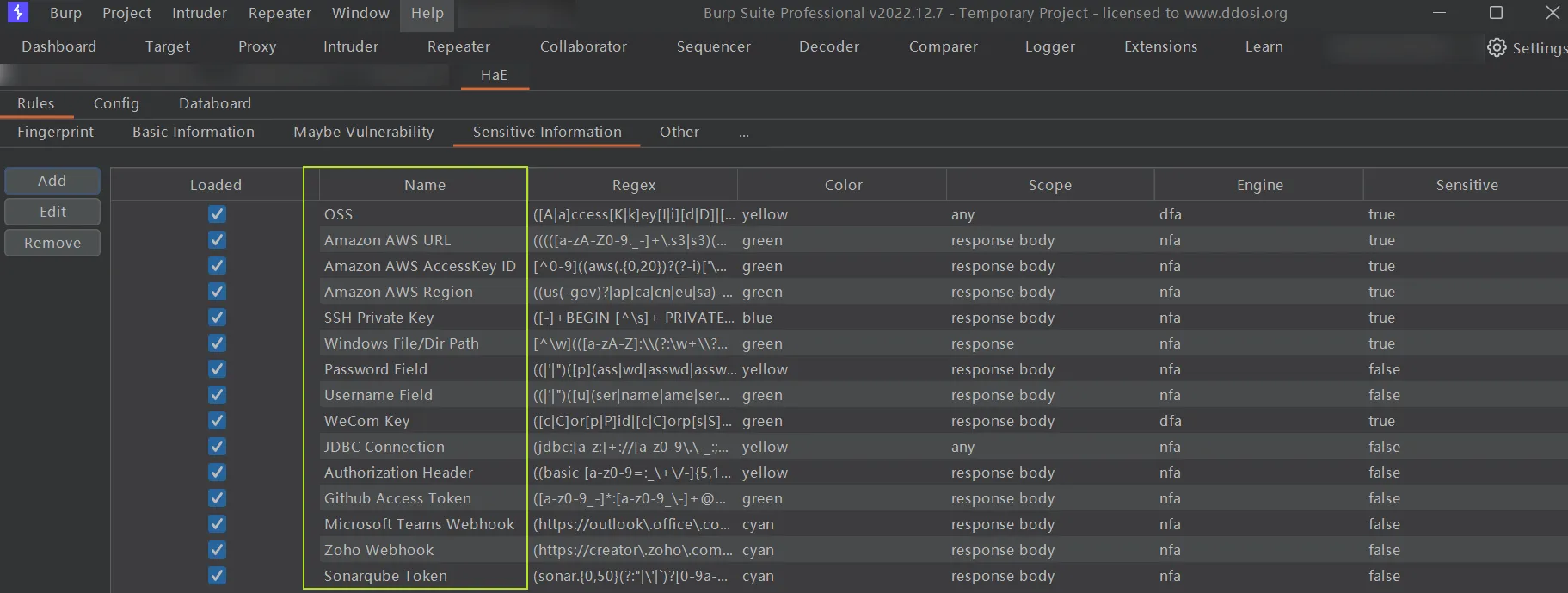
OSS
Amazon AWS URL
Amazon AWS AccessKey ID
Amazon AWS Region
SSH Private Key
Windows File/Dir Path
Password Field
Username Field
WeCom Key
JDBC Connection
Authorization Header
Github Access Token
Microsoft Teams Webhook
Zoho Webhook
Sonarqube Token
Linkfinder
Source Map
HTML Notes
Create Script中文翻译
Shiro
JSON Web 令牌
Swagger UI
Ueditor
电子邮件
中国身份证
中国手机号码
内部 IP 地址
MAC 地址
中国银行卡 ID
远程代码执行参数
Java 反序列化
调试逻辑参数
URL 作为值
上传表单
DoS 参数
JSONP 响应
OSS(对象存储)
亚马逊AWS网址
亚马逊AWS AccessKey ID
亚马逊AWS 区域
SSH 私钥
Windows 文件/目录路径
密码字段
用户名字段
WeCom 密钥
JDBC 连接
授权标头
Github访问令牌
Microsoft Teams Webhook
Zoho Webhook
Sonarqube令牌
Linkfinder
源映射
HTML 笔记
创建脚本配置完成是这样的
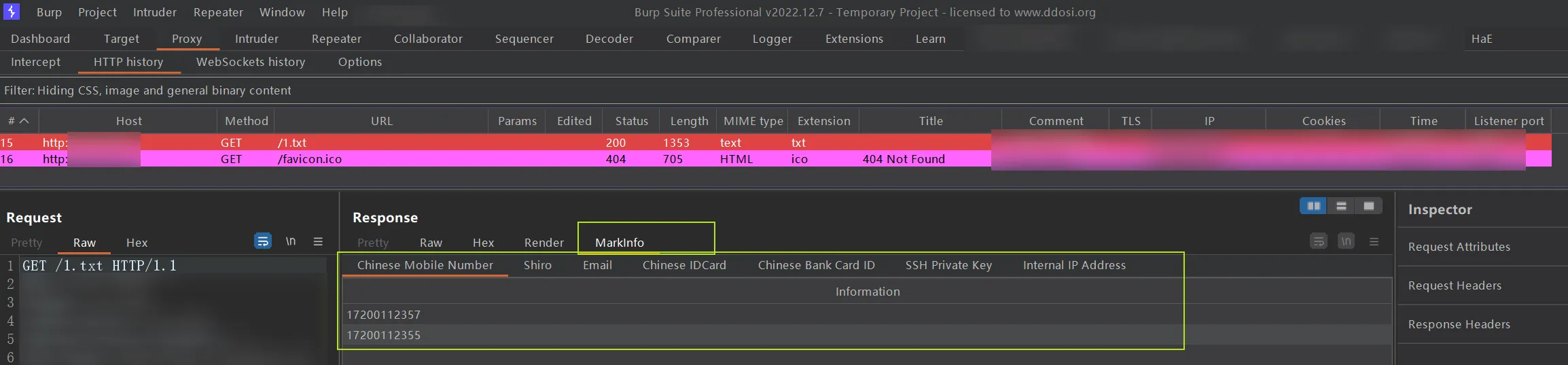
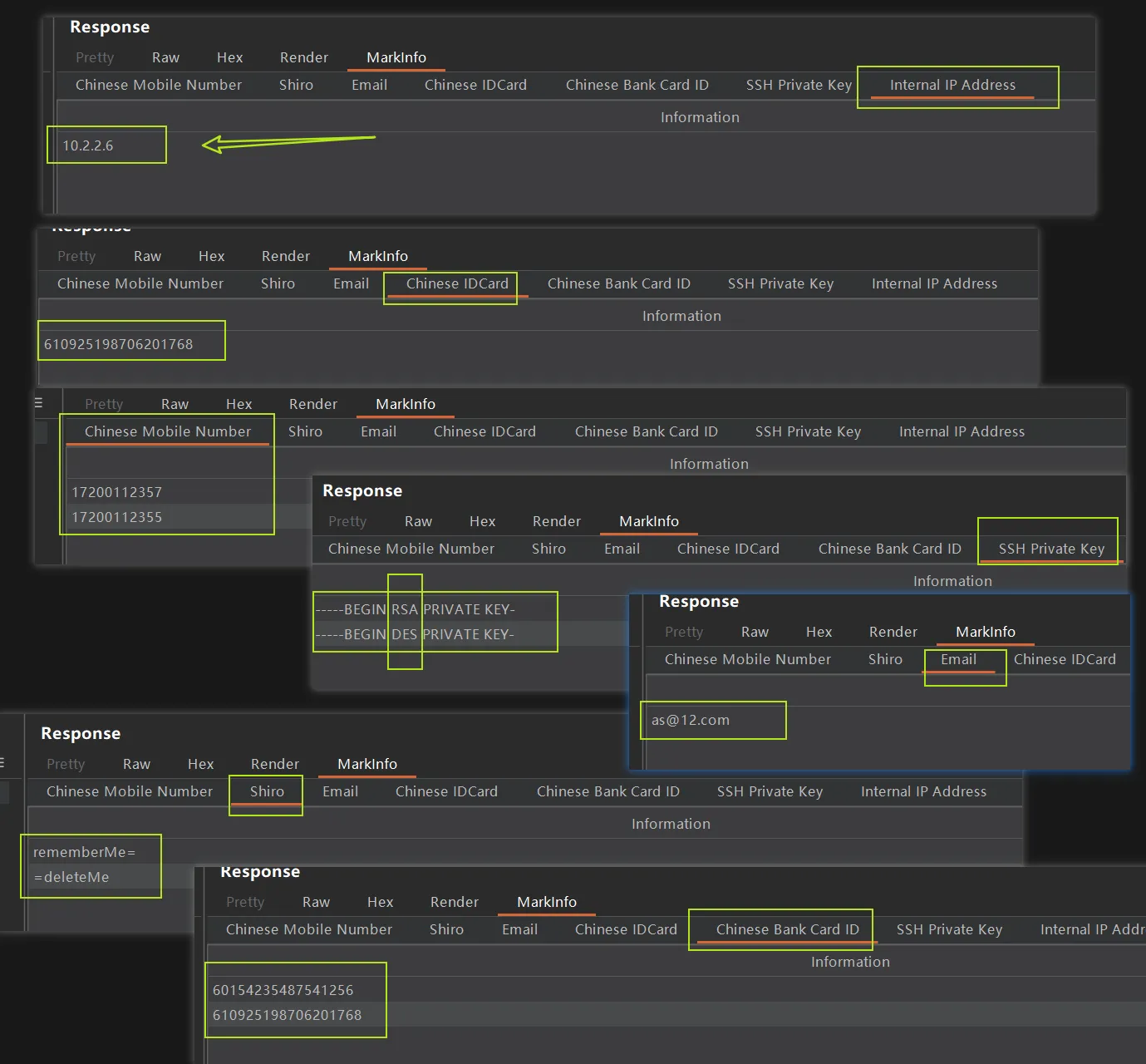
效果测试
测试数据
17200112355
sdsdvfbn
sdvflmwkerbsd
rememberMe=
=deleteMe
xcvldf
17200112357/\sdc'=-
-----BEGIN RSA PRIVATE KEY-----
MIICWwIBAAKBgQCiUmxRn5dAbFhZNlGoweecUYE+QNWp54nVwSWSYc/15SHFXV/N
YKWgGmk1RunNmTqeCaiEKRdrhELSuom3aOwyo7pGQs776WH++owAC+BNGK4T/3kI
NSttkl+qE2JoXyZ31tR31BphdhqWnC67ngdYKdr9JRuIrXDFEwhUJ6BjwIDAQAB
AoGAQe0a/E3Glw5KFbW3lcRnZrg9t0SK4w5cj3n6Ygki9vpgbHH/moDx0+RWLaLH
C897nLtMe5za27qkj0Te8SSGpWbciWD3ixEVomPXriAMujKMmsd0fGQ/m0a1KBl
2N/SGOalDuYirOKNIUa1AqpE4nrn/vvL8qgM8Fcw/G3iMH0CQQDUOD5qMfsnOoAw
yV88nzEwJgx86P74SpXwodfpdE/UfLAKjL0ECRQno2IRYb4aDtKity3cw2Um3Mtm
P8fq15y1AkEAw876U+/n8EVtcsYI8mOAvaFk4+9hgqy+PXM6eICcGxaRvnW8Wq6C
65LBB3e4nP+NXbGrry0gFekhks7EBWCTswJAIDkWCQvjxbYVRtMcudi2IEh2tvSt
2keA8tOwNAtsH6h7Fm7+OEGkpMwjFN6RfeVSDqmJRIqJrd5zuG6Wkc4zQJAddlY
6LP3kLD4kp+GOvyQO5Gru1QUCCYXybxUcLpXOiZ3SX5rAtkNiuMksm3n+vYEC2Qn
xKMQMJ/DySwQ5nud6QJAWh2YjD2WELcHGbltlRGCFDMvIgDBcWYaI48ahX8rzmlX
qyVgflSl5eowsh7WC4pUAU9taFKwVNe8E9Qiv6sUdg==
-----END RSA PRIVATE KEY-----
[email protected]
610925198706201768
10.2.2.6
60154235487541256
-----BEGIN DES PRIVATE KEY-----
-----BEGIN rsa PUBLIC KEY-----效果:
项目地址
GitHub:
https://github.com/gh0stkey/HaE
你可能需要用到的信息
DFA 和 NFA 的区别
geeksforgeeks.org/difference-between-dfa-and-nfa/
正则在线调式工具regexr
添加规则
您可以通过工具Regexr利用该功能。它可以帮助您在将模式添加到 HaE 中的规则之前调试和测试模式。
图形用户界面 (GUI) 易于使用。只需添加一个规则,命名它并添加一个正则表达式。一旦在所选源中检测到模式,添加规则的名称将成为注释。
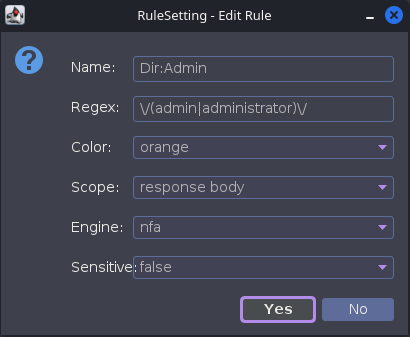
收集和分类
这些工具在创建您自己的规则模式时很有用:
我喜欢让我的模式与类别相关,以便在分析我截获的请求和响应时获得更清晰的反馈。HaE 扩展默认提供许多模式,但最好的解决方案是创建您自己的独特模式。为了在不产生大量垃圾和误报的情况下获得良好的结果,请使用更有可能有效的更严格的模式。
下面是一个如何将坏模式变成好模式的示例:下面的正则表达式模式试图收集所有具有.log扩展名的文件。
此正则表达式[a-zA-Z0-9-_]+.log( bad ) 收集所有具有.log扩展名的文件,但它也收集误报,例如console.log()JavaScript 函数。
为避免这种情况,您可以改为创建一个正则表达式模式,如下所示:([a-zA-Z0-9-_]+.log)([^([{]). 正则表达式不是防弹的,但它避免了大多数误报。
下面您会发现一些我自己创建的模式,我觉得它们非常有用。这些模式为我提供了有关目标的快速信息,还让我能够被动地检测可能存在漏洞的代码模式。
更多规则
车牌号(新能源+非新能源)
([京津沪渝冀豫云辽黑湘皖鲁新苏浙赣鄂桂甘晋蒙陕吉闽贵粤青藏川宁琼使领][A-HJ-NP-Z][A-HJ-NP-Z0-9]{4,5}[A-HJ-NP-Z0-9挂学警港澳])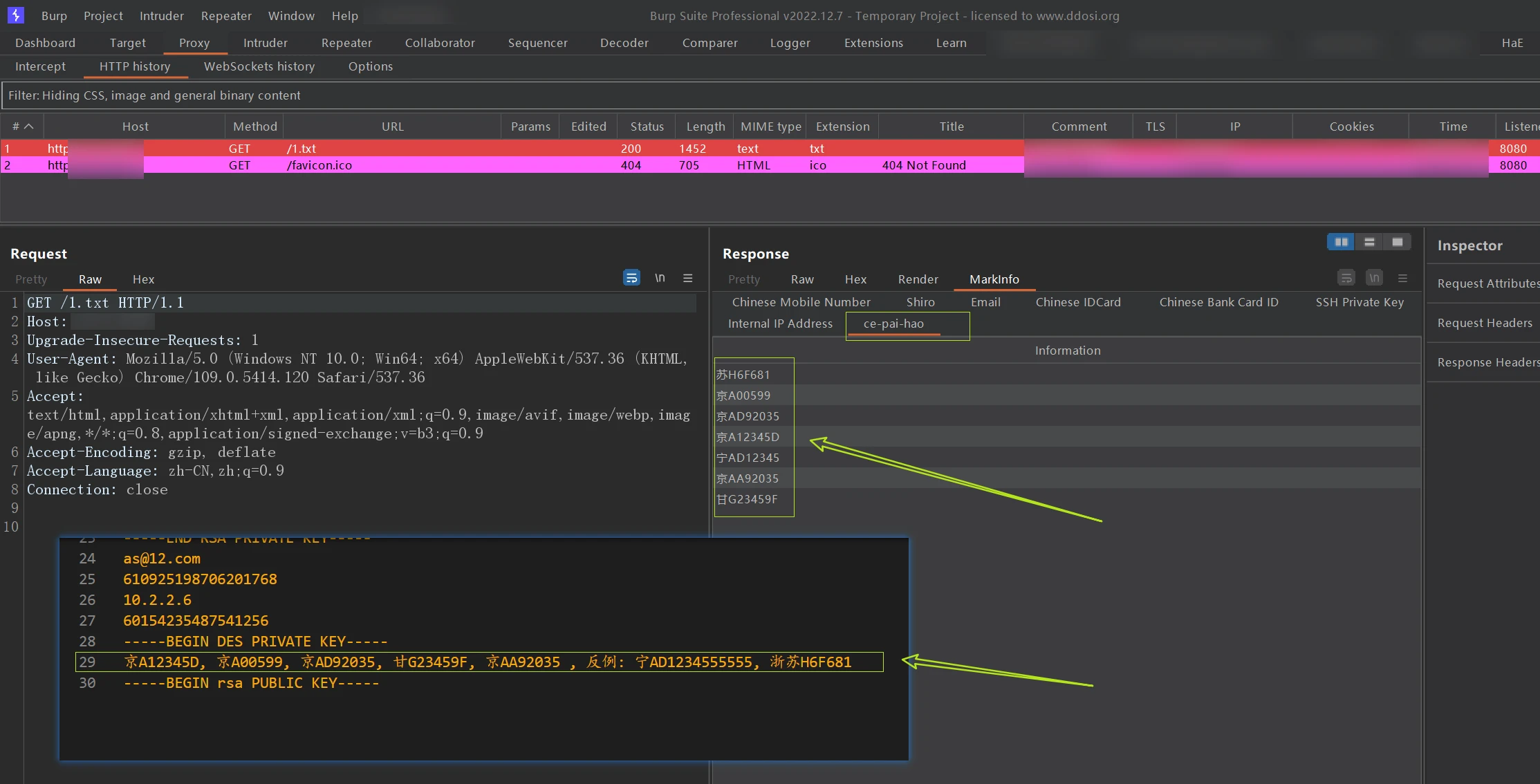
统一社会信用代码
([0-9A-HJ-NPQRTUWXY]{2}\d{6}[0-9A-HJ-NPQRTUWXY]{10})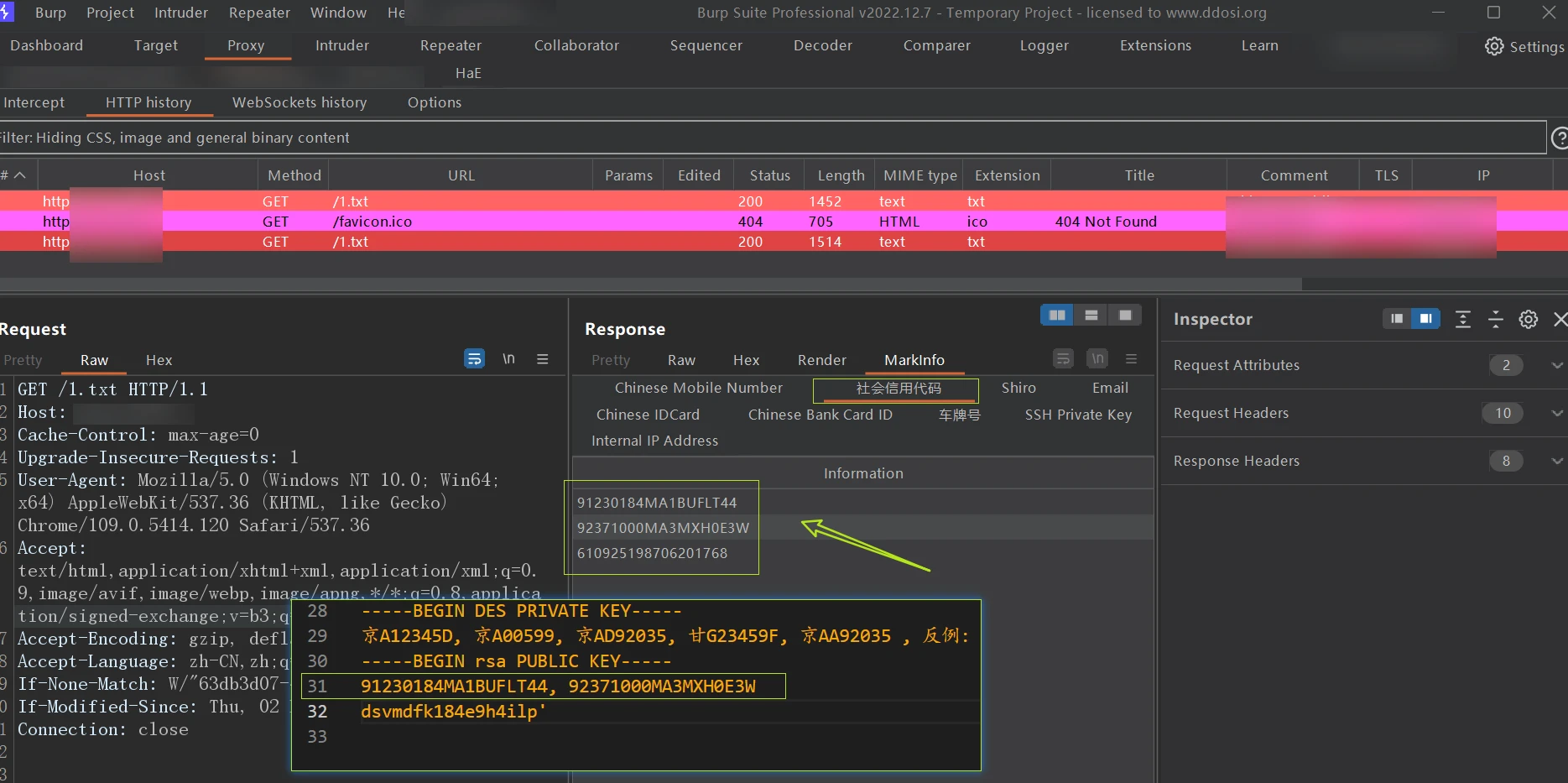
护照(包含港澳台)
([EK]\d{8}|(SE|DE|PE|MA)\d{7})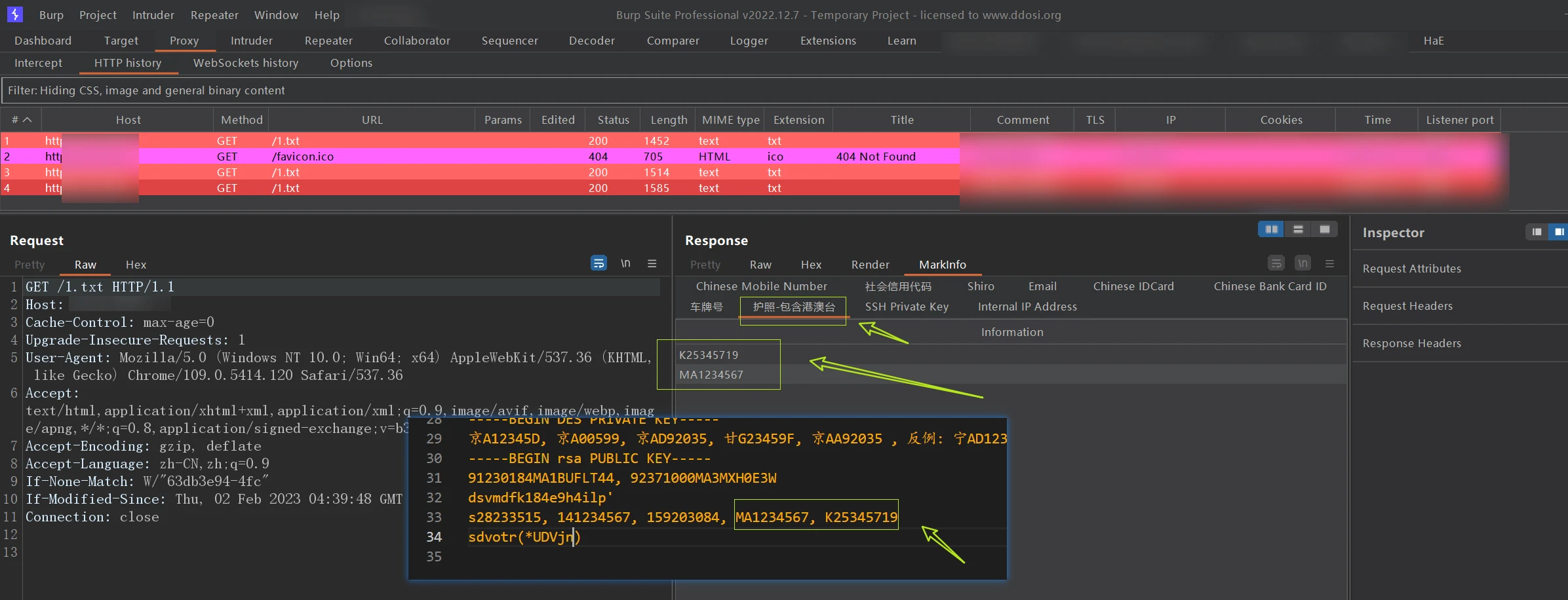
香港身份证
([a-zA-Z]\d{6}\([\dA]\))澳门身份证
([1|5|7]\d{6}[(\d)]{3})台湾身份证
([a-zA-Z][0-9]{9})侦察
(wordpress|wp-([a-zA-Z]+))
(cdn.shopify.com|_shopify|shopify_)
(nginx|apache|akamai|cloudflare|iis|varnish|fastly)
(admin|administrator).
(mysql|mssql|sqlite|postgresql|)JavaScript DOM
(createElement("script"))
(URLSearchParams|location.search|(.split(("|'|`)(?|&)))
.(write|innerHTML)(.*((+|,)( ?)(element|location|window|document).[a-zA-Z])跟踪错误
(([A-Z]):\|(t|T)he server could not|database connection|syntax error, |error, unexpected |PHP (Syntax|Parse) error:|(php|PHP):|in ([a-zA-Z0-9-/_.]+) on line (d+))文件和端点
/(admin|administrator)/
(admin|administrator).?
(api|rest|soap|v(1|2|3)|wp-json|swagger|)(.?)(jsp|json|/|)
([a-zA-Z0-9+].(php|asp|aspx|py|rb|go|pl|sql|xml|jsp|java))(]|}|)|"|'|`|/|d|s)
([a-zA-Z0-9+].(bak|log|csv))(]|}|)|"|'|`|/|d|s)
(((user|database|sql|db|dashboard|backup|restore|old|saved|storage|internal|access|secret|password)(s?)).(php|asp|aspx|py|rb|go|pl|sql|xml|jsp|java|doc|docs|xls|xlsx|csv|db|sql|bak|log|csv))(]|}|)|"|'|`|/|d|s)跨站脚本
[^s+-([{\=.?.)](""|''|``|(\\|\\\\)([^\]|"|'|`))备份包含所有模式的Yaml 配置文件很重要。可以在以下位置找到来自 HaE 的模式:/$HOME/.config/HaE/Config.yml。您可以使用以下命令将 Yaml 文件复制到另一个目录:cp /$HOME/.config/HaE/Config.yml /$HOME/Desktop/HaE_bak.yml
题外话
配合CYS4-SensitiveDiscoverer插件效果更佳.
转载请注明出处及链接