目录导航
CTF简介
CTF(Capture The Flag,夺旗赛)是一种网络安全竞赛,参与者通过解决各种挑战来获取“旗标”(flag),这些旗标通常是一些字符串,证明参赛者成功完成了某个任务。CTF比赛通常包含以下几类题目:
- Web安全:寻找Web应用程序中的漏洞,例如SQL注入、XSS、CSRF等。
- 逆向工程:分析二进制程序或软件,了解其内部工作原理,找到其中的漏洞或隐藏信息。
- 密码学:解决与加密和解密相关的难题,破解密码或加密算法。
- 取证:从受损的系统或文件中恢复数据,寻找隐藏的线索。
- Pwn:通过漏洞利用获得对系统的控制权限,常见的有缓冲区溢出、格式化字符串漏洞等。
- 隐写术:在图片、音频或其他文件中隐藏信息,解码并提取出来。
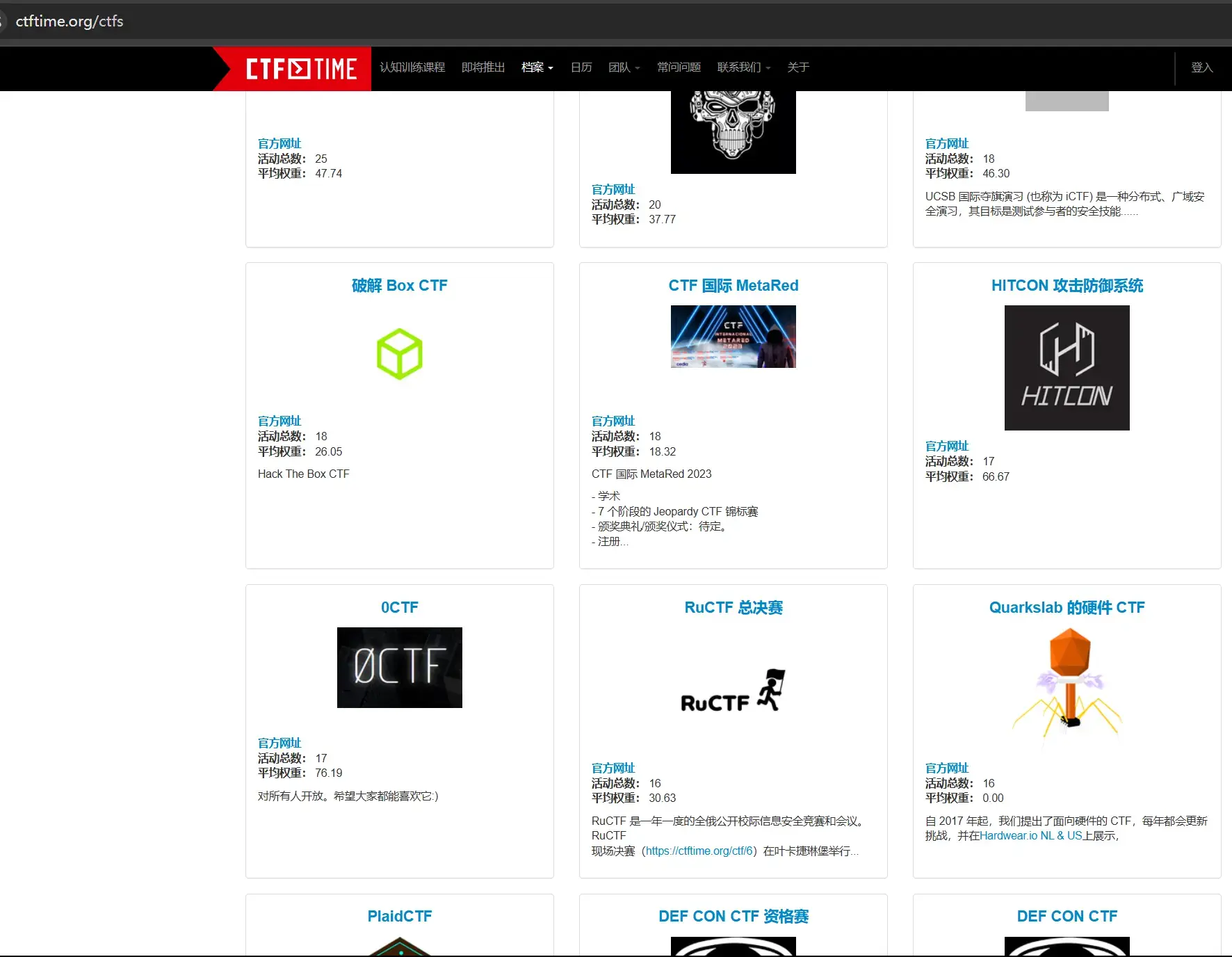
黑客靶场
黑客靶场(Hack The Box,简称HTB)是一个提供合法的、模拟的网络安全环境的平台,旨在帮助网络安全爱好者、渗透测试人员、以及CTF竞赛者练习和提升自己的技术。它通过设置各种具有挑战性的靶机(虚拟机)供用户攻破,并且每台靶机的目的是让参与者找到漏洞、利用漏洞、并最终获得特定的“旗标”(flag)
列表
- HackTheBox App – link
- HackTheBox Academy – link
- TryHackMe – link
- VulnLab – link
- VulnHub – link
- CryptoHack – link
- Portswigger Web Security Academy – link
- CTFTime – link
- PicoCTF – link
- PWNable – link
- RE Challenges – link
- XSS Game – link
- Game Of Active Directory – link
- Vulnerable Active Directory – link
- Vulnerable Active Directory Plus – link
- All Damn Vulnerable Resources – link
- Lets Defend – link
- CyberDefenders – link
- Ethernaut – wargames – link
- API Security University – link
- Expose Lab – link
- Damn Vulnerable GraphQL Application – link
- CloudLabsAD – link
- Offensive Security Labs – link
- ICS Security Labs – link
- SANS Holiday Hack Challenge – link
- Damn Vulnerable DeFi – link
- Vulnerable app with examples showing how to not use secrets – link
- Learn to Code Blockchain DApps by Building Simple Games – link
- CodeWars: Achieve mastery through challenge – link
- Sad Servers – link
- RHme Challanges 2015 – link
- RHme Challanges 2016 – link
- RHme Challanges 2017 – link
- Crackmes – link
- Cryptopals – link
- ROP Emporium – link
- CloudGoat – link
- IAM Vulnerable – link
- SadCloud – link
- Damn Vulnerable GraphQL Application – link
- MemLabs: Educational, CTF-styled labs for individuals interested in Memory Forensics. – link
- PWNED Labs – link
- Hands-on Security Labs focused on Azure IaaS Security – link
- Multi-use Hybrid + Identity Cyber Range implementing a small Active Directory Domain in Azure – link
- AWSGoat : A Damn Vulnerable AWS Infrastructure – link
- AzureGoat : A Damn Vulnerable Azure Infrastructure – link
- Damn Vulnerable Web Application (DVWA) – link
- Damn Vulnerable Web Services – link
- Damn Vulnerable Hybrid Mobile App – link
- A deliberately vulnerable CI/CD environment – link
- Vulnerable REST API with OWASP top 10 vulnerabilities for security testing – link
- Damn Vulnerable Serverless Application – link
- Damn Vulnerable Thick Client App developed in C# .NET – link
- Damn Vulnerable Java (EE) Application – link
- Damn Vulnerable IoT Device – link
- Damn Vulnerable Python Web App – link
- Damn Vulnerable Bank – link
- Damn Vulnerable WordPress Site – link
- Damn Vulnerable NodeJS Application – link
- Damn Vulnerable Rails app – link
- Damn Vulnerable Grade Management System – link
- Damn Vulnerable C# Application (API) – link
- Damn Vulnerable iOS App – link
- Damn Vulnerable iOS App #2 – link
- The Damn Vulnerable Router Firmware Project – link
- Damn Vulnerable Functions as a Service – link
- Damn Vulnerable Cloud Application – link
- Create a vulnerable active directory that’s allowing you to test most of the active directory attacks in a local lab – link
- An active directory laboratory for penetration testing – link
- The Ethernaut is a Web3/Solidity based wargame – link
- APIsec University – link
- OverTheWire – link
- CrypTool – link
- Root Me – link
- Webhacking.kr – link
- Damn Vulnerable Restaurant – link
- Reverse Engineering challenges – link
- HackMyVM – link
- UnderTheWire – link
- Google CTF – link
- Proving Grounds Play (Offsec) – link
- OWASP crAPI – link
- OWASP NodeGoat – link
- OWASP Juice Shop – link
- OWASP Mutillidae II – link
- vAPI (vulnerable API) – link
- AI Security Challenge – link
- Gandalf: Test Your Prompt Injection Skills – link
- DockerLabs – link
- The Hackers Labs – link