目录导航
数字取证和事件响应 (DFIR) 解释
Digital Forensics and Incident Response (DFIR)
数字取证和事件响应 (DFIR)
数字取证和事件响应 (DFIR) 是网络安全领域的其中一个领域,专注于网络攻击的识别、调查和补救。
DFIR 有两个主要组成部分:
- 数字取证:取证科学的一个子集,用于检查系统数据、用户活动和其他数字证据,以确定攻击是否正在进行以及活动的幕后黑手。
- 事件响应:组织将遵循的总体流程,以准备、检测、遏制数据泄露并从中恢复。
由于端点的激增和总体网络安全攻击的升级,DFIR 已成为组织安全策略和威胁搜寻能力中的核心能力。向云的转变以及基于远程的工作的加速,进一步提高了组织确保保护连接到网络的所有设备免受各种威胁的需求。
尽管 DFIR 传统上是一种反应性安全功能,但复杂的工具和先进技术(例如人工智能 (AI) 和机器学习 (ML))使一些组织能够利用 DFIR 活动来影响和通知预防措施。在这种情况下,DFIR 也可以被视为主动安全策略中的一个组件。
如何在事件响应计划中使用数字取证
数字取证提供计算机应急响应小组 (CERT) 或计算机安全事件响应小组 (CSIRT) 响应安全事件所需的必要信息和证据。
数字取证可能包括:
- 文件系统取证:分析端点内的文件系统以寻找受损迹象。
- 内存取证:分析内存中可能不会出现在文件系统中的攻击指标。
- 网络取证:审查网络活动,包括电子邮件、消息传递和网页浏览,以识别攻击、了解网络犯罪分子的攻击技术并评估事件的范围。
- 日志分析:审查和解释活动记录或日志以识别可疑活动或异常事件。
除了帮助团队应对攻击之外,数字取证还在整个补救过程中发挥着重要作用。数字取证还可能包括提供支持诉讼的证据或向审计员展示的文件。
此外,数字取证团队的分析可以帮助制定和加强预防性安全措施。这可以使组织降低整体风险,并加快未来的响应时间。
中文翻译
用于安全事件响应的精选工具和资源列表,旨在帮助安全分析师和DFIR团队。
数字取证和事件响应 (DFIR) 团队是组织中负责管理安全事件响应的一组人员,包括收集事件证据、补救其影响以及实施控制措施以防止事件在未来再次发生。
内容
- 对手模拟
- 多合一工具
- 图书
- 社区
- 磁盘映像创建工具
- 证据收集
- 事件管理
- 知识库
- Linux 发行版
- Linux证据收集
- 日志分析工具
- 内存分析工具
- 内存成像工具
- OSX 证据收集
- 其他列表
- 其他工具
- 剧本
- 进程转储工具
- 沙箱/逆向工具
- 扫描仪工具
- 时间线工具
- 视频
- Windows 证据收集
IR 工具集
对手模拟
- APTSimulator – Windows 批处理脚本,它使用一组工具和输出文件使系统看起来好像受到了威胁。
- Atomic Red Team (ART) – 映射到 MITRE ATT&CK 框架的小型且高度便携的检测测试。
- AutoTTP – 自动化战术技术和程序。手动重新运行复杂序列以进行回归测试、产品评估,为研究人员生成数据。
- Blue Team Training Toolkit (BT3) – 用于防御性安全培训的软件,它将把您的网络分析培训课程、事件响应演练和红队参与提升到一个新的水平。
- Caldera – 在 Windows 企业网络中执行侵害后对抗行为的自动化对抗模拟系统。它使用计划系统和基于对抗战术、技术和常识 (ATT&CK™) 项目的预配置对抗模型在操作期间生成计划。
- DumpsterFire – 模块化、菜单驱动的跨平台工具,用于构建可重复的、延时的、分布式的安全事件。轻松为蓝队演习和传感器/警报映射创建自定义事件链。红队可以制造诱饵事件、干扰和诱惑来支持和扩大他们的行动。
- Metta – 用于进行对抗性模拟的信息安全准备工具。
- Network Flight Simulator – 用于生成恶意网络流量并帮助安全团队评估安全控制和网络可见性的轻量级实用程序。
- Red Team Automation (RTA) – RTA 提供了一个脚本框架,旨在让蓝队测试他们针对恶意交易的检测能力,以 MITRE ATT&CK 为模型。
- RedHunt-OS – 用于对手模拟和威胁搜寻的虚拟机。
多合一工具
- Belkasoft Evidence Center – 该工具包将通过分析硬盘驱动器、驱动器映像、内存转储、iOS、黑莓和安卓备份、UFED、JTAG 和芯片转储,从多个来源快速提取数字证据。
- CimSweep – 基于 CIM/WMI 的工具套件,能够跨所有版本的 Windows 远程执行事件响应和搜索操作。
- CIRTkit – CIRTKit 不仅是工具的集合,而且还是一个框架,可帮助持续统一事件响应和取证调查流程。
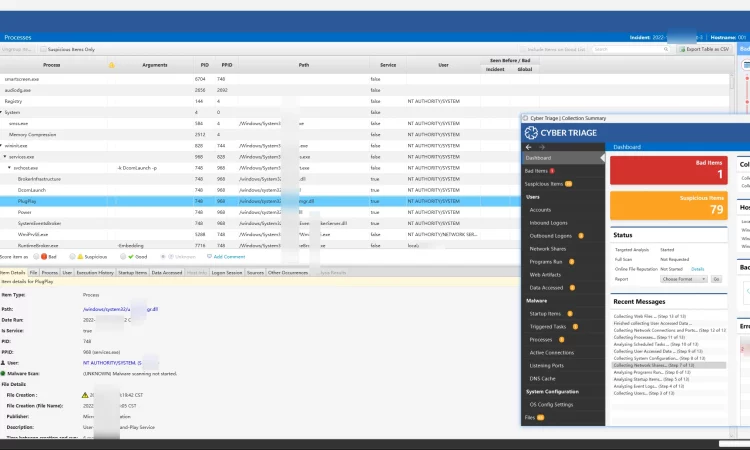
- Cyber Triage – Cyber Triage 远程收集和分析端点数据以帮助确定它是否受到损害。它的无代理方法和对易用性和自动化的关注使公司能够在没有重大基础设施变化和没有取证专家团队的情况下做出响应。其结果用于决定系统是否应该被删除或进一步调查。
- Doorman – osquery 车队管理器,允许远程管理节点检索的 osquery 配置。它利用 osquery 的 TLS 配置、记录器和分布式读/写端点,以最小的开销和侵入性为管理员提供跨设备队列的可见性。
- Falcon Orchestrator – 基于 Windows 的可扩展应用程序,提供工作流自动化、案例管理和安全响应功能。
- Flare – 一个完全可定制的、基于 Windows 的安全发行版,用于恶意软件分析、事件响应、渗透测试。
- Fleetdm – 为安全专家量身定制的最先进的主机监控平台。利用 Facebook 久经考验的 osquery 项目,Fleetdm 提供持续更新、功能和对重大问题的快速解答。
- GRR Rapid Response – 专注于远程实时取证的事件响应框架。它由安装在目标系统上的 python 代理(客户端)和可以管理代理并与之通信的 python 服务器基础结构组成。除了包含的 Python API 客户端外,PowerGRR在 PowerShell 中提供了一个 API 客户端库,可在 Windows、Linux 和 macOS 上运行,用于 GRR 自动化和脚本编写。
- IRIS – IRIS 是一个供事件响应分析师使用的网络协作平台,允许在技术层面共享调查结果。
- Kuiper – 数字取证调查平台
- Limacharlie – 端点安全平台由一系列小项目组成,所有这些项目协同工作,为您提供跨平台(Windows、OSX、Linux、Android 和 iOS)低级环境,用于管理附加模块并将其推送到内存中以扩展其功能。
- Matano:AWS 上的开源无服务器安全湖平台,可让您将 PB 级安全数据提取、存储和分析到 Apache Iceberg 数据中,并以代码形式运行实时 Python 检测。
- MozDef – 自动化安全事件处理过程并促进事件处理程序的实时活动。
- MutableSecurity – 用于自动设置、配置和使用网络安全解决方案的 CLI 程序。
- nightHawk – 使用 ElasticSearch 作为后端为异步取证数据呈现构建的应用程序。它旨在摄取 Redline 集合。
- Open Computer Forensics Architecture – 另一种流行的分布式开源计算机取证框架。该框架建立在Linux平台上,使用postgreSQL数据库存储数据。
- osquery – 使用类似 SQL 的查询语言轻松询问有关 Linux 和 macOS 基础设施的问题;提供的事件响应包可帮助您检测和响应违规行为。
- Redline – 为用户提供主机调查功能,以通过内存和文件分析以及威胁评估配置文件的开发来查找恶意活动的迹象。
- Sleuth Kit & Autopsy – 基于 Unix 和 Windows 的工具,有助于对计算机进行取证分析。它带有各种有助于数字取证的工具。这些工具有助于分析磁盘映像、对文件系统进行深入分析以及其他各种事情。
- TheHive – 可扩展的三合一开源和免费解决方案,旨在让 SOC、CSIRT、CERT 和任何信息安全从业者处理需要迅速调查和采取行动的安全事件时更轻松。
- Velociraptor – 端点可见性和收集工具
- X-Ways Forensics – 用于磁盘克隆和成像的取证工具。它可用于查找已删除的文件和磁盘分析。
- Zentral – 将 osquery 强大的端点清单功能与灵活的通知和操作框架相结合。这使人们能够识别并响应 OS X 和 Linux 客户端上的更改。
书籍
- Applied Incident Response – Steve Anson 关于事件响应的书。
- 内存取证艺术– 检测 Windows、Linux 和 Mac 内存中的恶意软件和威胁。
- 制作 InfoSec 剧本:安全监控和事件响应总体规划– 作者:Jeff Bollinger、Brandon Enright 和 Matthew Valites。
- 数字取证和事件响应:响应现代网络威胁的事件响应技术和程序– 杰拉德·约翰森 (Gerard Johansen)。
- DFIR 简介– 作者:Scott J. Roberts。
- 事件响应与计算机取证,第三版– 事件响应权威指南。
- Incident Response Techniques for Ransomware Attacks – 为勒索软件攻击构建事件响应策略的绝佳指南。奥列格·斯库尔金。
- Incident Response with Threat Intelligence – 建立基于威胁情报的事件响应计划的重要参考。罗伯托·马丁内斯。
- Intelligence-Driven Incident Response – 作者:Scott J. Roberts,Rebekah Brown。
- 操作员手册:红队 + OSINT + 蓝队参考– 事件响应者的重要参考。
- Practical Memory Forensics – 实践内存取证的权威指南。作者:Svetlana Ostrovskaya 和 Oleg Skulkin。
- The Practice of Network Security Monitoring: Understanding Incident Detection and Response – Richard Bejtlich 关于 IR 的书。
社区
- 数字取证 Discord 服务器– 由来自执法部门、私营部门和取证供应商的 8,000 多名工作专业人员组成的社区。此外,还有很多学生和爱好者!指南在这里。
- SANS DFIR mailing list – SANS 的 DFIR 邮件列表.
- Slack DFIR 频道– Slack DFIR Communitiy 频道 –在此处注册。
磁盘映像创建工具
- AccessData FTK Imager – 取证工具,其主要目的是从任何类型的磁盘预览可恢复的数据。FTK Imager 还可以获取 32 位和 64 位系统上的实时内存和分页文件。
- Bitscout – Vitaly Kamluk 的 Bitscout 可帮助您构建完全可信的可自定义 LiveCD/LiveUSB 映像,以用于远程数字取证(或您选择的任何其他任务). 它应该是透明的,并且可以由系统的所有者监控,具有法证上的合理性、可定制性和紧凑性。
- GetData Forensic Imager – 基于 Windows 的程序,它将获取、转换或验证以下常见取证文件格式之一的取证图像。
- Guymager – 用于在 Linux 上获取媒体的免费取证成像器。
- Magnet ACQUIRE – Magnet Forensics 的 ACQUIRE 允许在 Windows、Linux 和 OS X 以及移动操作系统上执行各种类型的磁盘采集.
证据收集
- artifactcollector – artifactcollector 项目提供了一个在系统上收集取证工件的软件。
- bulk_extractor – 扫描磁盘映像、文件或文件目录并在不解析文件系统或文件系统结构的情况下提取有用信息的计算机取证工具。由于忽略了文件系统结构,该程序在速度和彻底性方面脱颖而出。
- Cold Disk Quick Response – 简化的解析器列表,可快速分析取证图像文件(
dd、E01.vmdk等)并输出九份报告。 - CyLR – CyLR 工具可快速、安全地从具有 NTFS 文件系统的主机收集取证工件,并将对主机的影响降至最低。
- 取证工件– 数字取证工件存储库
- ir-rescue – Windows 批处理脚本和 Unix Bash 脚本,用于在事件响应期间全面收集主机取证数据。
- Live Response Collection – 从基于 Windows、OSX 和 *nix 的操作系统收集易失数据的自动化工具。
- Margarita Shotgun – 用于并行化远程内存获取的命令行实用程序(适用于或不适用 Amazon EC2 实例)。
- UAC – UAC(类 Unix 工件收集器)是用于事件响应的实时响应收集脚本,它利用本机二进制文件和工具来自动收集 AIX、Android、ESXi、FreeBSD、Linux、macOS、NetBSD、NetScaler、OpenBSD 和Solaris 系统工件。
事件管理
- Catalyst – 一个免费的 SOAR 系统,有助于自动化警报处理和事件响应过程。
- CyberCPR – 社区和商业事件管理工具,内置 Need-to-Know 以在处理敏感事件时支持 GDPR 合规性。
- Cyphon – Cyphon 通过单一平台简化大量相关任务,消除了令人头疼的事件管理。它接收、处理和分类事件,为您的分析工作流提供包罗万象的解决方案——聚合数据、捆绑和优先排序警报,并使分析师能够调查和记录事件。
- CORTEX XSOAR – Paloalto 安全编排、自动化和响应平台,具有完整的事件生命周期管理和许多集成以增强自动化。
- DFTimewolf – 用于编排取证收集、处理和数据导出的框架。
- DFIRTrack – 事件响应跟踪应用程序通过具有大量受影响系统和工件的案例和任务处理一个或多个事件。
- 快速事件响应 (FIR) – 网络安全事件管理平台在设计时考虑了敏捷性和速度。它允许轻松创建、跟踪和报告网络安全事件,对 CSIRT、CERT 和 SOC 等非常有用。
- RTIR – Request Tracker for Incident Response (RTIR) 是针对计算机安全团队的主要开源事件处理系统。我们与全球十几个 CERT 和 CSIRT 团队合作,帮助您处理不断增加的事件报告量。RTIR 建立在 Request Tracker 的所有功能之上。
- Sandia Cyber Omni Tracker (SCOT) – 专注于灵活性和易用性的事件响应协作和知识捕获工具。我们的目标是在不增加用户负担的情况下为事件响应流程增加价值。
- Shuffle – 一个专注于可访问性的通用安全自动化平台。
- threat_note – 轻量级调查笔记本,允许安全研究人员注册和检索与其研究相关的指标。
- Zenduty – Zenduty 是一个新颖的事件管理平台,提供端到端的事件警报、随叫随到的管理和响应编排,使团队能够更好地控制和自动化事件管理生命周期。
知识库
- 数字取证神器知识库– 数字取证神器知识库
- Windows 事件攻击样本– Windows 事件攻击样本
- Windows 注册表知识库– Windows 注册表知识库
Linux 发行版
- 数字调查和分析设备 (ADIA) – 基于 VMware 的设备,用于数字调查和采集,完全由公共领域软件构建。ADIA 中包含的工具包括 Autopsy、Sleuth Kit、数字取证框架、log2timeline、Xplico 和 Wireshark。大多数系统维护使用 Webmin。它专为中小型数字调查和采集而设计。该设备在 Linux、Windows 和 Mac OS 下运行。i386(32 位)和 x86_64(64 位)版本均可用。
- Computer Aided Investigative Environment (CAINE) – 包含许多工具,可帮助调查人员进行分析,包括取证证据收集。
- CCF-VM – CyLR CDQR 取证虚拟机 (CCF-VM):一种用于解析收集到的数据的一体式解决方案,使其可以通过内置的常见搜索轻松搜索,同时搜索单个和多个主机。
- Digital Evidence & Forensics Toolkit (DEFT) – 用于计算机取证证据收集的 Linux 发行版。它与适用于 Windows 的数字高级响应工具包 (DART) 捆绑在一起。DEFT 的轻型版本(称为 DEFT Zero)也可用,它主要侧重于取证可靠的证据收集。
- NST – 网络安全工具包– Linux 发行版,包括大量对网络安全专业人员有用的同类最佳开源网络安全应用程序。
- PALADIN – 修改后的 Linux 发行版以合理的方式执行各种取证任务。它附带了许多开源取证工具。
- Security Onion – 专门的 Linux 发行版,旨在使用高级分析工具进行网络安全监控。
- SANS Investigative Forensic Toolkit (SIFT) Workstation – 展示了先进的事件响应能力和针对入侵的深入数字取证技术可以使用免费提供且经常更新的尖端开源工具来实现。
Linux证据收集
- FastIR Collector Linux – 适用于 Linux 的 FastIR 在实时 Linux 上收集不同的工件,并将结果记录在 CSV 文件中。
日志分析工具
- AppCompatProcessor – AppCompatProcessor 旨在从企业范围的 AppCompat / AmCache 数据中提取额外的价值,超越经典的堆栈和 grepping 技术。
- APT Hunter – APT-Hunter 是 Windows 事件日志的威胁搜寻工具.
- Chainsaw – Chainsaw 提供强大的“第一响应”功能,可以快速识别 Windows 事件日志中的威胁。
- Event Log Explorer – 开发用于快速分析日志文件和其他数据的工具。
- Event Log Observer – 使用此 GUI 工具查看、分析和监控记录在 Microsoft Windows 事件日志中的事件。
- Hayabusa – Hayabusa 是由日本大和安全集团创建的 Windows 事件日志快速取证时间线生成器和威胁搜寻工具。
- Kaspersky CyberTrace – 威胁情报融合和分析工具,将威胁数据源与 SIEM 解决方案集成在一起。用户可以在其现有安全操作的工作流程中立即利用威胁情报进行安全监控和事件报告 (IR) 活动。
- Log Parser Lizard – 针对结构化日志数据执行 SQL 查询:服务器日志、Windows 事件、文件系统、Active Directory、log4net 日志、逗号/制表符分隔的文本、XML 或 JSON 文件。还为 Microsoft LogParser 2.2 提供了一个 GUI,具有强大的 UI 元素:语法编辑器、数据网格、图表、数据透视表、仪表板、查询管理器等。
- Lorg – 用于高级 HTTPD 日志文件安全分析和取证的工具。
- Logdissect – 用于分析日志文件和其他数据的 CLI 实用程序和 Python API。
- LogonTracer – 通过可视化和分析 Windows 事件日志来调查恶意 Windows 登录的工具。
- Sigma – 已包含大量规则集的 SIEM 系统的通用签名格式。
- StreamAlert – 无服务器实时日志数据分析框架,能够使用用户定义的逻辑获取自定义数据源和触发警报。
- SysmonSearch – SysmonSearch 通过事件日志的聚合使 Windows 事件日志分析更有效且耗时更少.
- WELA – Windows 事件日志分析器旨在成为 Windows 事件日志的瑞士军刀。
- Zircolite – 一种独立且快速的基于 SIGMA 的 EVTX 或 JSON 检测工具。
内存分析工具
- AVML – 用于 Linux 的便携式易失性内存获取工具。
- Evolve – 波动性内存取证框架的 Web 界面。
- inVtero.net – 具有嵌套管理程序支持的 Windows x64 高级内存分析。
- LiME – 可加载内核模块 (LKM),它允许从 Linux 和基于 Linux 的设备(以前称为 DMD)获取易失性内存。
- MalConfScan – MalConfScan 是一个 Volatility 插件,用于提取已知恶意软件的配置数据。Volatility 是一种用于事件响应和恶意软件分析的开源内存取证框架。该工具在内存映像中搜索恶意软件并转储配置数据。此外,该工具还具有列出恶意代码引用的字符串的功能。
- Memoryze – 免费的内存取证软件,可帮助事件响应者发现实时内存中的错误。Memoryze 可以获取和/或分析内存图像,并且在实时系统上,可以在其分析中包括页面文件。
- Memoryze for Mac – Memoryze for Mac 是 Memoryze,但适用于 Mac。但是,功能数量较少。
- Orochi -Orochi 是一个用于协作取证内存转储分析的开源框架。
- Rekall – 用于从易失性存储器 (RAM) 样本中提取数字伪像的开源工具(和库)。
- Responder PRO – Responder PRO 是行业标准的物理内存和自动化恶意软件分析解决方案。
- Volatility – 高级内存取证框架。
- Volatility 3 – 易失性内存提取框架(Volatility 的后继者)
- VolatilityBot – 供研究人员使用的自动化工具将所有猜测工作和手动任务从二进制提取阶段移除,或者帮助调查人员执行内存分析调查的第一步。
- VolDiff – 基于波动性的恶意软件内存足迹分析。
- WindowsSCOPE – 用于分析易失性内存的内存取证和逆向工程工具,提供分析 Windows 内核、驱动程序、DLL 以及虚拟和物理内存的能力。
内存成像工具
- Belkasoft Live RAM Capturer – 小巧的免费取证工具,可以可靠地提取计算机易失性内存的全部内容——即使受到主动反调试或反倾销系统的保护。
- Linux Memory Grabber – 用于转储 Linux 内存和创建波动率配置文件的脚本。
- Magnet RAM Capture – 免费的映像工具,旨在捕获嫌疑人计算机的物理内存。支持最新版本的 Windows。
- OSForensics – 在 32 位和 64 位系统上获取实时内存的工具。可以完成单个进程的内存空间转储或物理内存转储。
OSX 证据收集
- Knockknock – 显示设置为在 OSX 上自动执行的持久性项目(脚本、命令、二进制文件等)。
- macOS Artifact Parsing Tool (mac_apt) – 基于插件的取证框架,用于快速 mac 分类,适用于实时机器、磁盘映像或单个工件文件。
- OSX Auditor – 免费的 Mac OS X 计算机取证工具。
- OSX Collector – 用于实时响应的 OSX Auditor 分支.
- ESF Playground – 一种实时查看 Apple Endpoint Security Framework (ESF) 中事件的工具。
其他列表
- Awesome Event IDs – 对数字取证和事件响应有用的事件 ID 资源集合。
- Awesome Forensics – 精选的取证分析工具和资源列表。
- Didier Stevens Suite – 工具集
- Eric Zimmerman Tools – 由 SANS 研究所讲师 Eric Zimmerman 创建的取证工具的更新列表.
- List of various Security APIs – 用于安全的公共 JSON APIs 的集合列表。
其他工具
- Cortex – Cortex 允许您使用 Web 界面逐一或以批量模式分析可观察对象,例如 IP 和电子邮件地址、URL、域名、文件或哈希值. 分析师还可以使用其 REST API 自动执行这些操作。
- Crits – 基于 Web 的工具,它将分析引擎与网络威胁数据库相结合。
- Diffy – 由 Netflix 的 SIRT 开发的 DFIR 工具,允许调查人员在事件期间快速跨云实例(目前是 AWS 上的 Linux 实例)确定侵害范围,并通过显示与基线的差异来有效地对这些实例进行分类以进行后续操作。
- domfind – 用于在不同 TLD 下查找相同域名的 Python DNS 爬虫。
- Fileintel – 根据文件哈希提取情报。
- HELK – 威胁搜寻平台。
- Hindsight – Google Chrome / Chromium 的互联网历史取证.
- Hostintel – 按主机提取情报。
- imagemounter – 命令行实用程序和 Python 包,用于简化(卸载)取证磁盘映像的安装。
- Kansa – PowerShell 中的模块化事件响应框架。
- MFT 浏览器– MFT 目录树重建和记录信息。
- Munin – VirusTotal 和其他服务的在线哈希检查器。
- PowerSponse – PowerSponse 是一个 PowerShell 模块,专注于在安全事件响应期间进行有针对性的遏制和补救.
- PyaraScanner – 非常简单的多线程多规则到多文件 YARA 扫描恶意软件动物园和 IR 的 Python 脚本。
- rastrea2r – 允许在 Windows、Linux 和 OS X 上使用 YARA 扫描磁盘和内存以查找 IOC.
- RaQet – 非常规的远程采集和分类工具,允许对使用专门构建的取证操作系统重新启动的远程计算机(客户端)的磁盘进行分类。
- Raccine – 一种简单的勒索软件保护
- Stalk – 在出现问题时收集有关 MySQL 的取证数据。
- Scout2 – 允许 Amazon Web Services 管理员评估其环境安全状况的安全工具。
- Stenographer – 数据包捕获解决方案,旨在快速将所有数据包假脱机到磁盘,然后提供对这些数据包子集的简单、快速的访问。它存储尽可能多的历史记录,管理磁盘使用情况,并在达到磁盘限制时删除。它非常适合在事件发生之前和期间捕获流量,而无需明确存储所有网络流量。
- sqhunter – 基于 osquery 和 Salt Open (SaltStack) 的威胁猎手,无需 osquery 的 tls 插件即可发出临时或分布式查询。sqhunter 允许您查询开放的网络套接字并根据威胁情报来源检查它们。
- sysmon-config – 具有默认高质量事件跟踪的 Sysmon 配置文件模板
- sysmon-modular – sysmon 配置模块的存储库
- traceroute-circl – 扩展的 traceroute 以支持 CSIRT(或 CERT)操作员的活动。通常 CSIRT 团队必须根据收到的 IP 地址来处理事件。由卢森堡计算机应急响应中心创建。
- X-Ray 2.0 – Windows 实用程序(维护不善或不再维护),用于将病毒样本提交给 AV 供应商。
剧本
- AWS 事件响应 Runbook 示例– AWS IR Runbook 示例旨在根据每个使用它们的实体进行定制。这三个样本是:“DoS 或 DDoS 攻击”、“凭据泄漏”和“对 Amazon S3 存储桶的意外访问”。
- Counteractive Playbooks – Counteractive PLaybooks 系列。
- GuardSIght Playbook Battle Cards – 网络事件响应 Playbook Battle Cards 的集合
- IRM – CERT Societe Generale 的事件响应方法。
- IR Workflow Gallery – 不同的通用事件响应工作流程,例如恶意软件爆发、数据盗窃、未经授权的访问……每个工作流程都包含七个步骤:准备、检测、分析、遏制、根除、恢复、事件后处理。工作流程可在线获取或下载。
- PagerDuty 事件响应文档– 描述 PagerDuty 事件响应流程的各个部分的文档。它不仅提供有关为事件做准备的信息,还提供事件发生期间和事件之后应该做什么的信息。源代码在GitHub上可用。
- Phantom Community Playbooks – 适用于 Splunk 的 Phantom Community Playbooks,但也可定制用于其他用途.
- ThreatHunter-Playbook – 帮助开发狩猎活动技术和假设的手册。
进程转储工具
- Microsoft ProcDump – 动态转储任何正在运行的 Win32 进程内存映像。
- PMDump – 允许您在不停止进程的情况下将进程的内存内容转储到文件的工具。
沙箱/逆向工具
- AMAaaS – Android 恶意软件分析即服务,在原生 Android 环境中执行。
- Any Run – 交互式在线恶意软件分析服务,用于使用任何环境对大多数类型的威胁进行动态和静态研究。
- CAPEv2 – 恶意软件配置和有效载荷提取。
- Cuckoo – 开源高度可配置的沙盒工具。
- Cuckoo-modified – 由社区开发的经过大量修改的 Cuckoo 叉子。
- Cuckoo-modified-api – 用于控制 cuckoo 修改沙箱的 Python 库。
- Cutter – 由 Radare2 提供支持的逆向工程平台.
- Ghidra – 软件逆向工程框架。
- Hybrid-Analysis – CrowdStrike 提供的免费的强大在线沙箱.
- Intezer – Intezer Analyze 深入研究 Windows 二进制文件以检测微代码与已知威胁的相似性,以提供准确但易于理解的结果。
- Joe Sandbox(社区) – Joe Sandbox 检测并分析 Windows、Android、Mac OS、Linux 和 iOS 上的潜在恶意文件和 URL 以进行可疑活动;提供全面详细的分析报告。
- Mastiff – 静态分析框架,可自动执行从多种不同文件格式中提取关键特征的过程。
- Metadefender Cloud – 免费的威胁情报平台,提供文件的多重扫描、数据清理和漏洞评估。
- Radare2 – 逆向工程框架和命令行工具集。
- Reverse.IT – CrowdStrike 提供的混合分析工具的替代域。
- Rizin – 类 UNIX 逆向工程框架和命令行工具集
- StringSifter – 一种机器学习工具,可根据字符串与恶意软件分析的相关性对字符串进行排名。
- Threat.Zone – 基于云的威胁分析平台,包括供研究人员使用的沙箱、CDR 和交互式分析。
- Valkyrie Comodo – Valkyrie 使用文件中的运行时行为和数百个功能来执行分析.
- Viper – 基于 Python 的二进制分析和管理框架,与 Cuckoo 和 YARA 配合良好。
- Virustotal – 分析文件和 URL 的免费在线服务,可以识别病毒、蠕虫、特洛伊木马和防病毒引擎和网站扫描程序检测到的其他类型的恶意内容。
- Visualize_Logs – 用于日志的开源可视化库和命令行工具(Cuckoo、Procmon,还有更多)。
- Yomi – 由 Yoroi 管理和托管的免费 MultiSandbox.
扫描仪工具
- Fenrir – 简单的 IOC 扫描仪。它允许在纯 bash 中扫描任何 Linux/Unix/OSX 系统以查找 IOC。由 THOR 和 LOKI 的创造者创建。
- LOKI – 免费的 IR 扫描仪,用于使用 yara 规则和其他指标 (IOC) 扫描端点。
- Spyre – 用 Go 编写的基于 YARA 的简单 IOC 扫描器
时间线工具
- Aurora 事件响应– 为轻松构建事件的详细时间表而开发的平台。
- Highlighter – Fire/Mandiant 提供的免费工具,可描绘日志/文本文件,突出显示图形上与关键字或短语相对应的区域。有助于确定感染的时间以及侵害后所做的事情。
- Morgue – Etsy 的 PHP Web 应用程序,用于管理事后分析.
- Plaso – 用于工具 log2timeline 的基于 Python 的后端引擎。
- Timesketch – 用于协作取证时间线分析的开源工具。
PPT
- The Future of Incident Response – 由 Bruce Schneier 在 OWASP AppSecUSA 2015 上发表。
Windows 证据收集
- AChoir – 框架/脚本工具,用于标准化和简化为 Windows 编写实时采集实用程序脚本的过程。
- Crowd Response – 轻量级 Windows 控制台应用程序,旨在帮助收集事件响应和安全参与的系统信息。它具有众多模块和输出格式。
- DFIR ORC – DFIR ORC 是专门用于可靠地解析和收集关键工件(如 MFT、注册表配置单元或事件日志)的专用工具的集合。DFIR ORC 收集数据,但不对其进行分析:它并不意味着对机器进行分类。它提供了运行 Microsoft Windows 的计算机的取证相关快照。代码可以在GitHub上找到。
- FastIR Collector – 在实时 Windows 系统上收集不同工件并将结果记录在 csv 文件中的工具。通过对这些工件的分析,可以检测到早期的危害。
- Fibratus – 用于探索和跟踪 Windows 内核的工具。
- Hoarder – 为取证或事件响应调查收集最有价值的工件。
- IREC – 多合一 IR 证据收集器,可捕获 RAM 映像、$MFT、事件日志、WMI 脚本、注册表配置单元、系统还原点等。它是免费的,闪电般快速且易于使用。
- Invoke-LiveResponse – Invoke-LiveResponse 是用于目标收集的实时响应工具。
- IOC Finder – 来自 Mandiant 的免费工具,用于收集主机系统数据和报告侵害指标 (IOC) 的存在。仅支持 Windows。不再维护。仅完全支持 Windows 7 / Windows Server 2008 R2。
- IRTriage – 事件响应分类 – 用于取证分析的 Windows 证据收集。
- KAPE -Eric Zimmerman 的 Kroll 工件解析器和提取器(KAPE). 一种分类工具,可以找到最流行的数字工件,然后快速解析它们。当时间紧迫时,伟大而彻底。
- LOKI – 免费的 IR 扫描仪,用于使用 yara 规则和其他指标 (IOC) 扫描端点。
- MEERKAT – 适用于 Windows 的基于 PowerShell 的分类和威胁搜寻。
- Panorama – 实时 Windows 系统上的快速事件概述。
- PowerForensics – 使用 PowerShell 的实时磁盘取证平台。
- PSRecon – PSRecon 使用 PowerShell(v2 或更高版本)从远程 Windows 主机收集数据,将数据组织到文件夹中,对所有提取的数据进行哈希处理,对 PowerShell 和各种系统属性进行哈希处理,并将数据发送给安全团队。可以将数据推送到共享、通过电子邮件发送或保留在本地。
- RegRipper – 用 Perl 编写的开源工具,用于从注册表中提取/解析信息(键、值、数据)并将其呈现以供分析。
英文 English
Awesome Incident Response
A curated list of tools and resources for security incident response, aimed to help security analysts and DFIR teams.
Digital Forensics and Incident Response (DFIR) teams are groups of people in an organization responsible for managing the response to a security incident, including gathering evidence of the incident, remediating its effects, and implementing controls to prevent the incident from recurring in the future.
Contents
- Adversary Emulation
- All-In-One Tools
- Books
- Communities
- Disk Image Creation Tools
- Evidence Collection
- Incident Management
- Knowledge Bases
- Linux Distributions
- Linux Evidence Collection
- Log Analysis Tools
- Memory Analysis Tools
- Memory Imaging Tools
- OSX Evidence Collection
- Other Lists
- Other Tools
- Playbooks
- Process Dump Tools
- Sandboxing/Reversing Tools
- Scanner Tools
- Timeline Tools
- Videos
- Windows Evidence Collection
IR Tools Collection
Adversary Emulation
- APTSimulator – Windows Batch script that uses a set of tools and output files to make a system look as if it was compromised.
- Atomic Red Team (ART) – Small and highly portable detection tests mapped to the MITRE ATT&CK Framework.
- AutoTTP – Automated Tactics Techniques & Procedures. Re-running complex sequences manually for regression tests, product evaluations, generate data for researchers.
- Blue Team Training Toolkit (BT3) – Software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level.
- Caldera – Automated adversary emulation system that performs post-compromise adversarial behavior within Windows Enterprise networks. It generates plans during operation using a planning system and a pre-configured adversary model based on the Adversarial Tactics, Techniques & Common Knowledge (ATT&CK™) project.
- DumpsterFire – Modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events. Easily create custom event chains for Blue Team drills and sensor / alert mapping. Red Teams can create decoy incidents, distractions, and lures to support and scale their operations.
- Metta – Information security preparedness tool to do adversarial simulation.
- Network Flight Simulator – Lightweight utility used to generate malicious network traffic and help security teams to evaluate security controls and network visibility.
- Red Team Automation (RTA) – RTA provides a framework of scripts designed to allow blue teams to test their detection capabilities against malicious tradecraft, modeled after MITRE ATT&CK.
- RedHunt-OS – Virtual machine for adversary emulation and threat hunting.
All-In-One Tools
- Belkasoft Evidence Center – The toolkit will quickly extract digital evidence from multiple sources by analyzing hard drives, drive images, memory dumps, iOS, Blackberry and Android backups, UFED, JTAG and chip-off dumps.
- CimSweep – Suite of CIM/WMI-based tools that enable the ability to perform incident response and hunting operations remotely across all versions of Windows.
- CIRTkit – CIRTKit is not just a collection of tools, but also a framework to aid in the ongoing unification of Incident Response and Forensics investigation processes.
- Cyber Triage – Cyber Triage remotely collects and analyzes endpoint data to help determine if it is compromised. It’s agentless approach and focus on ease of use and automation allows companies to respond without major infrastructure changes and without a team of forensics experts. Its results are used to decide if the system should be erased or investigated further.
- Doorman – osquery fleet manager that allows remote management of osquery configurations retrieved by nodes. It takes advantage of osquery’s TLS configuration, logger, and distributed read/write endpoints, to give administrators visibility across a fleet of devices with minimal overhead and intrusiveness.
- Falcon Orchestrator – Extendable Windows-based application that provides workflow automation, case management and security response functionality.
- Flare – A fully customizable, Windows-based security distribution for malware analysis, incident response, penetration testing.
- Fleetdm – State of the art host monitoring platform tailored for security experts. Leveraging Facebook’s battle-tested osquery project, Fleetdm delivers continuous updates, features and fast answers to big questions.
- GRR Rapid Response – Incident response framework focused on remote live forensics. It consists of a python agent (client) that is installed on target systems, and a python server infrastructure that can manage and talk to the agent. Besides the included Python API client, PowerGRR provides an API client library in PowerShell working on Windows, Linux and macOS for GRR automation and scripting.
- IRIS – IRIS is a web collaborative platform for incident response analysts allowing to share investigations at a technical level.
- Kuiper – Digital Forensics Investigation Platform
- Limacharlie – Endpoint security platform composed of a collection of small projects all working together that gives you a cross-platform (Windows, OSX, Linux, Android and iOS) low-level environment for managing and pushing additional modules into memory to extend its functionality.
- Matano: Open source serverless security lake platform on AWS that lets you ingest, store, and analyze petabytes of security data into an Apache Iceberg data lake and run realtime Python detections as code.
- MozDef – Automates the security incident handling process and facilitate the real-time activities of incident handlers.
- MutableSecurity – CLI program for automating the setup, configuration, and use of cybersecurity solutions.
- nightHawk – Application built for asynchronous forensic data presentation using ElasticSearch as the backend. It’s designed to ingest Redline collections.
- Open Computer Forensics Architecture – Another popular distributed open-source computer forensics framework. This framework was built on Linux platform and uses postgreSQL database for storing data.
- osquery – Easily ask questions about your Linux and macOS infrastructure using a SQL-like query language; the provided incident-response pack helps you detect and respond to breaches.
- Redline – Provides host investigative capabilities to users to find signs of malicious activity through memory and file analysis, and the development of a threat assessment profile.
- The Sleuth Kit & Autopsy – Unix and Windows based tool which helps in forensic analysis of computers. It comes with various tools which helps in digital forensics. These tools help in analyzing disk images, performing in-depth analysis of file systems, and various other things.
- TheHive – Scalable 3-in-1 open source and free solution designed to make life easier for SOCs, CSIRTs, CERTs and any information security practitioner dealing with security incidents that need to be investigated and acted upon swiftly.
- Velociraptor – Endpoint visibility and collection tool
- X-Ways Forensics – Forensics tool for Disk cloning and imaging. It can be used to find deleted files and disk analysis.
- Zentral – Combines osquery’s powerful endpoint inventory features with a flexible notification and action framework. This enables one to identify and react to changes on OS X and Linux clients.
Books
- Applied Incident Response – Steve Anson’s book on Incident Response.
- Art of Memory Forensics – Detecting Malware and Threats in Windows, Linux, and Mac Memory.
- Crafting the InfoSec Playbook: Security Monitoring and Incident Response Master Plan – by Jeff Bollinger, Brandon Enright and Matthew Valites.
- Digital Forensics and Incident Response: Incident response techniques and procedures to respond to modern cyber threats – by Gerard Johansen.
- Introduction to DFIR – By Scott J. Roberts.
- Incident Response & Computer Forensics, Third Edition – The definitive guide to incident response.
- Incident Response Techniques for Ransomware Attacks – A great guide to build an incident response strategy for ransomware attacks. By Oleg Skulkin.
- Incident Response with Threat Intelligence – Great reference to build an incident response plan based also on Threat Intelligence. By Roberto Martinez.
- Intelligence-Driven Incident Response – By Scott J. Roberts, Rebekah Brown.
- Operator Handbook: Red Team + OSINT + Blue Team Reference – Great reference for incident responders.
- Practical Memory Forensics – The definitive guide to practice memory forensics. By Svetlana Ostrovskaya and Oleg Skulkin.
- The Practice of Network Security Monitoring: Understanding Incident Detection and Response – Richard Bejtlich’s book on IR.
Communities
- Digital Forensics Discord Server – Community of 8,000+ working professionals from Law Enforcement, Private Sector, and Forensic Vendors. Additionally, plenty of students and hobbyists! Guide here.
- SANS DFIR mailing list – Mailing list by SANS for DFIR.
- Slack DFIR channel – Slack DFIR Communitiy channel – Signup here.
Disk Image Creation Tools
- AccessData FTK Imager – Forensics tool whose main purpose is to preview recoverable data from a disk of any kind. FTK Imager can also acquire live memory and paging file on 32bit and 64bit systems.
- Bitscout – Bitscout by Vitaly Kamluk helps you build your fully-trusted customizable LiveCD/LiveUSB image to be used for remote digital forensics (or perhaps any other task of your choice). It is meant to be transparent and monitorable by the owner of the system, forensically sound, customizable and compact.
- GetData Forensic Imager – Windows based program that will acquire, convert, or verify a forensic image in one of the following common forensic file formats.
- Guymager – Free forensic imager for media acquisition on Linux.
- Magnet ACQUIRE – ACQUIRE by Magnet Forensics allows various types of disk acquisitions to be performed on Windows, Linux, and OS X as well as mobile operating systems.
Evidence Collection
- artifactcollector – The artifactcollector project provides a software that collects forensic artifacts on systems.
- bulk_extractor – Computer forensics tool that scans a disk image, a file, or a directory of files and extracts useful information without parsing the file system or file system structures. Because of ignoring the file system structure, the program distinguishes itself in terms of speed and thoroughness.
- Cold Disk Quick Response – Streamlined list of parsers to quickly analyze a forensic image file (
dd, E01,.vmdk, etc) and output nine reports. - CyLR – The CyLR tool collects forensic artifacts from hosts with NTFS file systems quickly, securely and minimizes impact to the host.
- Forensic Artifacts – Digital Forensics Artifact Repository
- ir-rescue – Windows Batch script and a Unix Bash script to comprehensively collect host forensic data during incident response.
- Live Response Collection – Automated tool that collects volatile data from Windows, OSX, and *nix based operating systems.
- Margarita Shotgun – Command line utility (that works with or without Amazon EC2 instances) to parallelize remote memory acquisition.
- UAC – UAC (Unix-like Artifacts Collector) is a Live Response collection script for Incident Response that makes use of native binaries and tools to automate the collection of AIX, Android, ESXi, FreeBSD, Linux, macOS, NetBSD, NetScaler, OpenBSD and Solaris systems artifacts.
Incident Management
- Catalyst – A free SOAR system that helps to automate alert handling and incident response processes.
- CyberCPR – Community and commercial incident management tool with Need-to-Know built in to support GDPR compliance while handling sensitive incidents.
- Cyphon – Cyphon eliminates the headaches of incident management by streamlining a multitude of related tasks through a single platform. It receives, processes and triages events to provide an all-encompassing solution for your analytic workflow — aggregating data, bundling and prioritizing alerts, and empowering analysts to investigate and document incidents.
- CORTEX XSOAR – Paloalto security orchestration, automation and response platform with full Incident lifecycle management and many integrations to enhance automations.
- DFTimewolf – A framework for orchestrating forensic collection, processing and data export.
- DFIRTrack – Incident Response tracking application handling one or more incidents via cases and tasks with a lot of affected systems and artifacts.
- Fast Incident Response (FIR) – Cybersecurity incident management platform designed with agility and speed in mind. It allows for easy creation, tracking, and reporting of cybersecurity incidents and is useful for CSIRTs, CERTs and SOCs alike.
- RTIR – Request Tracker for Incident Response (RTIR) is the premier open source incident handling system targeted for computer security teams. We worked with over a dozen CERT and CSIRT teams around the world to help you handle the ever-increasing volume of incident reports. RTIR builds on all the features of Request Tracker.
- Sandia Cyber Omni Tracker (SCOT) – Incident Response collaboration and knowledge capture tool focused on flexibility and ease of use. Our goal is to add value to the incident response process without burdening the user.
- Shuffle – A general purpose security automation platform focused on accessibility.
- threat_note – Lightweight investigation notebook that allows security researchers the ability to register and retrieve indicators related to their research.
- Zenduty – Zenduty is a novel incident management platform providing end-to-end incident alerting, on-call management and response orchestration, giving teams greater control and automation over the incident management lifecycle.
Knowledge Bases
- Digital Forensics Artifact Knowledge Base – Digital Forensics Artifact Knowledge Base
- Windows Events Attack Samples – Windows Events Attack Samples
- Windows Registry Knowledge Base – Windows Registry Knowledge Base
Linux Distributions
- The Appliance for Digital Investigation and Analysis (ADIA) – VMware-based appliance used for digital investigation and acquisition and is built entirely from public domain software. Among the tools contained in ADIA are Autopsy, the Sleuth Kit, the Digital Forensics Framework, log2timeline, Xplico, and Wireshark. Most of the system maintenance uses Webmin. It is designed for small-to-medium sized digital investigations and acquisitions. The appliance runs under Linux, Windows, and Mac OS. Both i386 (32-bit) and x86_64 (64-bit) versions are available.
- Computer Aided Investigative Environment (CAINE) – Contains numerous tools that help investigators during their analysis, including forensic evidence collection.
- CCF-VM – CyLR CDQR Forensics Virtual Machine (CCF-VM): An all-in-one solution to parsing collected data, making it easily searchable with built-in common searches, enable searching of single and multiple hosts simultaneously.
- Digital Evidence & Forensics Toolkit (DEFT) – Linux distribution made for computer forensic evidence collection. It comes bundled with the Digital Advanced Response Toolkit (DART) for Windows. A light version of DEFT, called DEFT Zero, is also available, which is focused primarily on forensically sound evidence collection.
- NST – Network Security Toolkit – Linux distribution that includes a vast collection of best-of-breed open source network security applications useful to the network security professional.
- PALADIN – Modified Linux distribution to perform various forensics task in a forensically sound manner. It comes with many open source forensics tools included.
- Security Onion – Special Linux distro aimed at network security monitoring featuring advanced analysis tools.
- SANS Investigative Forensic Toolkit (SIFT) Workstation – Demonstrates that advanced incident response capabilities and deep dive digital forensic techniques to intrusions can be accomplished using cutting-edge open-source tools that are freely available and frequently updated.
Linux Evidence Collection
- FastIR Collector Linux – FastIR for Linux collects different artifacts on live Linux and records the results in CSV files.
Log Analysis Tools
- AppCompatProcessor – AppCompatProcessor has been designed to extract additional value from enterprise-wide AppCompat / AmCache data beyond the classic stacking and grepping techniques.
- APT Hunter – APT-Hunter is Threat Hunting tool for windows event logs.
- Chainsaw – Chainsaw provides a powerful ‘first-response’ capability to quickly identify threats within Windows event logs.
- Event Log Explorer – Tool developed to quickly analyze log files and other data.
- Event Log Observer – View, analyze and monitor events recorded in Microsoft Windows event logs with this GUI tool.
- Hayabusa – Hayabusa is a Windows event log fast forensics timeline generator and threat hunting tool created by the Yamato Security group in Japan.
- Kaspersky CyberTrace – Threat intelligence fusion and analysis tool that integrates threat data feeds with SIEM solutions. Users can immediately leverage threat intelligence for security monitoring and incident report (IR) activities in the workflow of their existing security operations.
- Log Parser Lizard – Execute SQL queries against structured log data: server logs, Windows Events, file system, Active Directory, log4net logs, comma/tab separated text, XML or JSON files. Also provides a GUI to Microsoft LogParser 2.2 with powerful UI elements: syntax editor, data grid, chart, pivot table, dashboard, query manager and more.
- Lorg – Tool for advanced HTTPD logfile security analysis and forensics.
- Logdissect – CLI utility and Python API for analyzing log files and other data.
- LogonTracer – Tool to investigate malicious Windows logon by visualizing and analyzing Windows event log.
- Sigma – Generic signature format for SIEM systems already containing an extensive ruleset.
- StreamAlert – Serverless, real-time log data analysis framework, capable of ingesting custom data sources and triggering alerts using user-defined logic.
- SysmonSearch – SysmonSearch makes Windows event log analysis more effective and less time consuming by aggregation of event logs.
- WELA – Windows Event Log Analyzer aims to be the Swiss Army knife for Windows event logs.
- Zircolite – A standalone and fast SIGMA-based detection tool for EVTX or JSON.
Memory Analysis Tools
- AVML – A portable volatile memory acquisition tool for Linux.
- Evolve – Web interface for the Volatility Memory Forensics Framework.
- inVtero.net – Advanced memory analysis for Windows x64 with nested hypervisor support.
- LiME – Loadable Kernel Module (LKM), which allows the acquisition of volatile memory from Linux and Linux-based devices, formerly called DMD.
- MalConfScan – MalConfScan is a Volatility plugin extracts configuration data of known malware. Volatility is an open-source memory forensics framework for incident response and malware analysis. This tool searches for malware in memory images and dumps configuration data. In addition, this tool has a function to list strings to which malicious code refers.
- Memoryze – Free memory forensic software that helps incident responders find evil in live memory. Memoryze can acquire and/or analyze memory images, and on live systems, can include the paging file in its analysis.
- Memoryze for Mac – Memoryze for Mac is Memoryze but then for Macs. A lower number of features, however.
- Orochi – Orochi is an open source framework for collaborative forensic memory dump analysis.
- Rekall – Open source tool (and library) for the extraction of digital artifacts from volatile memory (RAM) samples.
- Responder PRO – Responder PRO is the industry standard physical memory and automated malware analysis solution.
- Volatility – Advanced memory forensics framework.
- Volatility 3 – The volatile memory extraction framework (successor of Volatility)
- VolatilityBot – Automation tool for researchers cuts all the guesswork and manual tasks out of the binary extraction phase, or to help the investigator in the first steps of performing a memory analysis investigation.
- VolDiff – Malware Memory Footprint Analysis based on Volatility.
- WindowsSCOPE – Memory forensics and reverse engineering tool used for analyzing volatile memory offering the capability of analyzing the Windows kernel, drivers, DLLs, and virtual and physical memory.
Memory Imaging Tools
- Belkasoft Live RAM Capturer – Tiny free forensic tool to reliably extract the entire content of the computer’s volatile memory – even if protected by an active anti-debugging or anti-dumping system.
- Linux Memory Grabber – Script for dumping Linux memory and creating Volatility profiles.
- Magnet RAM Capture – Free imaging tool designed to capture the physical memory of a suspect’s computer. Supports recent versions of Windows.
- OSForensics – Tool to acquire live memory on 32-bit and 64-bit systems. A dump of an individual process’s memory space or physical memory dump can be done.
OSX Evidence Collection
- Knockknock – Displays persistent items(scripts, commands, binaries, etc.) that are set to execute automatically on OSX.
- macOS Artifact Parsing Tool (mac_apt) – Plugin based forensics framework for quick mac triage that works on live machines, disk images or individual artifact files.
- OSX Auditor – Free Mac OS X computer forensics tool.
- OSX Collector – OSX Auditor offshoot for live response.
- The ESF Playground – A tool to view the events in Apple Endpoint Security Framework (ESF) in real time.
Other Lists
- Awesome Event IDs – Collection of Event ID resources useful for Digital Forensics and Incident Response.
- Awesome Forensics – A curated list of awesome forensic analysis tools and resources.
- Didier Stevens Suite – Tool collection
- Eric Zimmerman Tools – An updated list of forensic tools created by Eric Zimmerman, an instructor for SANS institute.
- List of various Security APIs – Collective list of public JSON APIs for use in security.
Other Tools
- Cortex – Cortex allows you to analyze observables such as IP and email addresses, URLs, domain names, files or hashes one by one or in bulk mode using a Web interface. Analysts can also automate these operations using its REST API.
- Crits – Web-based tool which combines an analytic engine with a cyber threat database.
- Diffy – DFIR tool developed by Netflix’s SIRT that allows an investigator to quickly scope a compromise across cloud instances (Linux instances on AWS, currently) during an incident and efficiently triaging those instances for followup actions by showing differences against a baseline.
- domfind – Python DNS crawler for finding identical domain names under different TLDs.
- Fileintel – Pull intelligence per file hash.
- HELK – Threat Hunting platform.
- Hindsight – Internet history forensics for Google Chrome/Chromium.
- Hostintel – Pull intelligence per host.
- imagemounter – Command line utility and Python package to ease the (un)mounting of forensic disk images.
- Kansa – Modular incident response framework in PowerShell.
- MFT Browser – MFT directory tree reconstruction & record info.
- Munin – Online hash checker for VirusTotal and other services.
- PowerSponse – PowerSponse is a PowerShell module focused on targeted containment and remediation during security incident response.
- PyaraScanner – Very simple multi-threaded many-rules to many-files YARA scanning Python script for malware zoos and IR.
- rastrea2r – Allows one to scan disks and memory for IOCs using YARA on Windows, Linux and OS X.
- RaQet – Unconventional remote acquisition and triaging tool that allows triage a disk of a remote computer (client) that is restarted with a purposely built forensic operating system.
- Raccine – A Simple Ransomware Protection
- Stalk – Collect forensic data about MySQL when problems occur.
- Scout2 – Security tool that lets Amazon Web Services administrators assess their environment’s security posture.
- Stenographer – Packet capture solution which aims to quickly spool all packets to disk, then provide simple, fast access to subsets of those packets. It stores as much history as it possible, managing disk usage, and deleting when disk limits are hit. It’s ideal for capturing the traffic just before and during an incident, without the need explicit need to store all of the network traffic.
- sqhunter – Threat hunter based on osquery and Salt Open (SaltStack) that can issue ad-hoc or distributed queries without the need for osquery’s tls plugin. sqhunter allows you to query open network sockets and check them against threat intelligence sources.
- sysmon-config – Sysmon configuration file template with default high-quality event tracing
- sysmon-modular – A repository of sysmon configuration modules
- traceroute-circl – Extended traceroute to support the activities of CSIRT (or CERT) operators. Usually CSIRT team have to handle incidents based on IP addresses received. Created by Computer Emergency Response Center Luxembourg.
- X-Ray 2.0 – Windows utility (poorly maintained or no longer maintained) to submit virus samples to AV vendors.
Playbooks
- AWS Incident Response Runbook Samples – AWS IR Runbook Samples meant to be customized per each entity using them. The three samples are: “DoS or DDoS attack”, “credential leakage”, and “unintended access to an Amazon S3 bucket”.
- Counteractive Playbooks – Counteractive PLaybooks collection.
- GuardSIght Playbook Battle Cards – A collection of Cyber Incident Response Playbook Battle Cards
- IRM – Incident Response Methodologies by CERT Societe Generale.
- IR Workflow Gallery – Different generic incident response workflows, e.g. for malware outbreak, data theft, unauthorized access,… Every workflow consists of seven steps: prepare, detect, analyze, contain, eradicate, recover, post-incident handling. The workflows are online available or for download.
- PagerDuty Incident Response Documentation – Documents that describe parts of the PagerDuty Incident Response process. It provides information not only on preparing for an incident, but also what to do during and after. Source is available on GitHub.
- Phantom Community Playbooks – Phantom Community Playbooks for Splunk but also customizable for other use.
- ThreatHunter-Playbook – Playbook to aid the development of techniques and hypothesis for hunting campaigns.
Process Dump Tools
- Microsoft ProcDump – Dumps any running Win32 processes memory image on the fly.
- PMDump – Tool that lets you dump the memory contents of a process to a file without stopping the process.
Sandboxing/Reversing Tools
- AMAaaS – Android Malware Analysis as a Service, executed in a native Android environment.
- Any Run – Interactive online malware analysis service for dynamic and static research of most types of threats using any environment.
- CAPEv2 – Malware Configuration And Payload Extraction.
- Cuckoo – Open Source Highly configurable sandboxing tool.
- Cuckoo-modified – Heavily modified Cuckoo fork developed by community.
- Cuckoo-modified-api – Python library to control a cuckoo-modified sandbox.
- Cutter – Reverse engineering platform powered by Radare2.
- Ghidra – Software Reverse Engineering Framework.
- Hybrid-Analysis – Free powerful online sandbox by CrowdStrike.
- Intezer – Intezer Analyze dives into Windows binaries to detect micro-code similarities to known threats, in order to provide accurate yet easy-to-understand results.
- Joe Sandbox (Community) – Joe Sandbox detects and analyzes potential malicious files and URLs on Windows, Android, Mac OS, Linux, and iOS for suspicious activities; providing comprehensive and detailed analysis reports.
- Mastiff – Static analysis framework that automates the process of extracting key characteristics from a number of different file formats.
- Metadefender Cloud – Free threat intelligence platform providing multiscanning, data sanitization and vulnerability assessment of files.
- Radare2 – Reverse engineering framework and command-line toolset.
- Reverse.IT – Alternative domain for the Hybrid-Analysis tool provided by CrowdStrike.
- Rizin – UNIX-like reverse engineering framework and command-line toolset
- StringSifter – A machine learning tool that ranks strings based on their relevance for malware analysis.
- Threat.Zone – Cloud based threat analysis platform which include sandbox, CDR and interactive analysis for researchers.
- Valkyrie Comodo – Valkyrie uses run-time behavior and hundreds of features from a file to perform analysis.
- Viper – Python based binary analysis and management framework, that works well with Cuckoo and YARA.
- Virustotal – Free online service that analyzes files and URLs enabling the identification of viruses, worms, trojans and other kinds of malicious content detected by antivirus engines and website scanners.
- Visualize_Logs – Open source visualization library and command line tools for logs (Cuckoo, Procmon, more to come).
- Yomi – Free MultiSandbox managed and hosted by Yoroi.
Scanner Tools
- Fenrir – Simple IOC scanner. It allows scanning any Linux/Unix/OSX system for IOCs in plain bash. Created by the creators of THOR and LOKI.
- LOKI – Free IR scanner for scanning endpoint with yara rules and other indicators(IOCs).
- Spyre – Simple YARA-based IOC scanner written in Go
Timeline Tools
- Aurora Incident Response – Platform developed to build easily a detailed timeline of an incident.
- Highlighter – Free Tool available from Fire/Mandiant that will depict log/text file that can highlight areas on the graphic, that corresponded to a key word or phrase. Good for time lining an infection and what was done post compromise.
- Morgue – PHP Web app by Etsy for managing postmortems.
- Plaso – a Python-based backend engine for the tool log2timeline.
- Timesketch – Open source tool for collaborative forensic timeline analysis.
Videos
- The Future of Incident Response – Presented by Bruce Schneier at OWASP AppSecUSA 2015.
Windows Evidence Collection
- AChoir – Framework/scripting tool to standardize and simplify the process of scripting live acquisition utilities for Windows.
- Crowd Response – Lightweight Windows console application designed to aid in the gathering of system information for incident response and security engagements. It features numerous modules and output formats.
- DFIR ORC – DFIR ORC is a collection of specialized tools dedicated to reliably parse and collect critical artifacts such as the MFT, registry hives or event logs. DFIR ORC collects data, but does not analyze it: it is not meant to triage machines. It provides a forensically relevant snapshot of machines running Microsoft Windows. The code can be found on GitHub.
- FastIR Collector – Tool that collects different artifacts on live Windows systems and records the results in csv files. With the analyses of these artifacts, an early compromise can be detected.
- Fibratus – Tool for exploration and tracing of the Windows kernel.
- Hoarder – Collecting the most valuable artifacts for forensics or incident response investigations.
- IREC – All-in-one IR Evidence Collector which captures RAM Image, $MFT, EventLogs, WMI Scripts, Registry Hives, System Restore Points and much more. It is FREE, lightning fast and easy to use.
- Invoke-LiveResponse – Invoke-LiveResponse is a live response tool for targeted collection.
- IOC Finder – Free tool from Mandiant for collecting host system data and reporting the presence of Indicators of Compromise (IOCs). Support for Windows only. No longer maintained. Only fully supported up to Windows 7 / Windows Server 2008 R2.
- IRTriage – Incident Response Triage – Windows Evidence Collection for Forensic Analysis.
- KAPE – Kroll Artifact Parser and Extractor (KAPE) by Eric Zimmerman. A triage tool that finds the most prevalent digital artifacts and then parses them quickly. Great and thorough when time is of the essence.
- LOKI – Free IR scanner for scanning endpoint with yara rules and other indicators(IOCs).
- MEERKAT – PowerShell-based triage and threat hunting for Windows.
- Panorama – Fast incident overview on live Windows systems.
- PowerForensics – Live disk forensics platform, using PowerShell.
- PSRecon – PSRecon gathers data from a remote Windows host using PowerShell (v2 or later), organizes the data into folders, hashes all extracted data, hashes PowerShell and various system properties, and sends the data off to the security team. The data can be pushed to a share, sent over email, or retained locally.
- RegRipper – Open source tool, written in Perl, for extracting/parsing information (keys, values, data) from the Registry and presenting it for analysis.
转载请注明出处及链接