目录导航
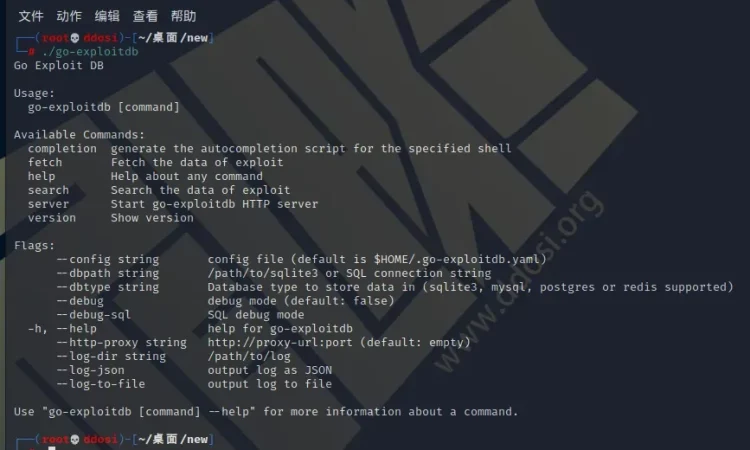
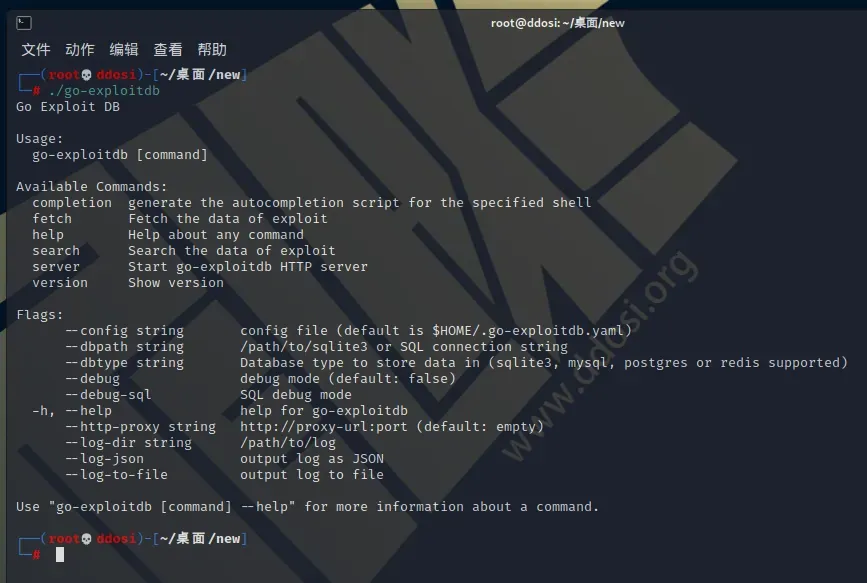
go-exploitdb简介
这是一个从一些漏洞利用数据库中搜索漏洞利用的工具。可以通过命令行界面搜索sqlite数据库(go-exploitdb)中插入的漏洞。在服务器模式下,可以使用简单的 Web API。
从如以下漏洞数据库中检索数据
- ExploitDB(OffensiveSecurity)通过 CVE 编号或 Exploit Database ID。
- GitHub 存储库
- 很棒的 Cve Poc
安装方法
Docker 部署
有一个 Docker 镜像可用
docker pull princechrismc/go-exploitdb使用容器时,它采用与普通命令行相同的参数。
本地部署安装
要求
go-exploitdb 需要以下软件包。
- git
- SQLite3, MySQL, PostgreSQL, Redis
- 最新版本的go
安装go-exploitdb
mkdir -p $GOPATH/src/github.com/vulsio
cd $GOPATH/src/github.com/vulsio
git clone https://github.com/vulsio/go-exploitdb.git
cd go-exploitdb
make installkali linux下可以直接使用如下命令安装使用
apt install go-exploitdb -y用法:
获取和插入Exploit
go-exploitdb fetch --help
获取exploit数据
用法:
go-exploitdb fetch [command]
可用命令:
awesomepoc 获取Awesome Poc
exploitdb 获取攻击性安全漏洞
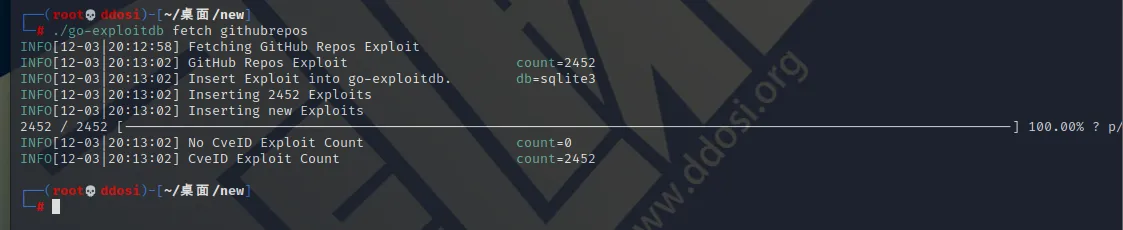
githubrepos 获取github repos的数据
Flags:
--batch-size int 要插入的大小数。(默认500)
-h,--help 帮助
全局标志:
--config string 配置文件 (默认是 $HOME/.go-exploitdb.yaml)
--dbpath string /path/to/sqlite3 或 SQL 连接字符串
--dbtype string 存储数据的数据库类型(sqlite3, mysql, postgres或redis支持)
--debug 调试模式(默认为关闭)
--debug-sql SQL调试模式
--http-proxy string http://代理url:端口 (默认: 空)
--log-dir string /path/to/log
--log-json 输出日志为 JSON
--log-to-file 输出日志到文件
使用“ go-exploitdb fetch [command] --help ” 获取更多信息关于命令。获取和插入攻击性安全漏洞利用数据库
go-exploitdb fetch exploitdb用法:搜索Exploits
$ go-exploitdb search -h
Search the data of exploit
用法:
go-exploitdb search [flags]
Flags:
-h, --help 搜索帮助信息
--param string 所有exploit: None | by CVE: [CVE-xxxx] | by ID: [xxxx](默认:无)
--type string All Exploits by CVE: CVE | by ID: ID (default: CVE)
全局标志:
--config string 配置文件 (默认是 $HOME/.go-exploitdb.yaml)
--dbpath string /path/to/sqlite3 或 SQL 连接字符串
--dbtype string 存储数据的数据库类型(sqlite3, mysql, postgres或redis支持)
--debug 调试模式(默认为关闭)
--debug-sql SQL调试模式
--http-proxy string http://代理url:端口 (默认: 空)
--log-dir string /path/to/log
--log-json 输出日志为 JSON
--log-to-file 输出日志到文件
按 CVE 搜索exploit(例如 CVE-2009-4091)
$ go-exploitdb search --type CVE --param CVE-2009-4091
Results:
---------------------------------------
[*]CVE-ExploitID Reference:
CVE: CVE-2009-4091
Exploit Type: OffensiveSecurity
Exploit Unique ID: 10180
URL: https://www.exploit-db.com/exploits/10180
Description: Simplog 0.9.3.2 - Multiple Vulnerabilities
[*]Exploit Detail Info:
[*]OffensiveSecurity:
- Document:
Path: https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt
File Type: webapps
---------------------------------------按 ExploitDB-ID 搜索漏洞(例如 ExploitDB-ID:10180)
$ go-exploitdb search --type ID --param 10180
Results:
---------------------------------------
[*]CVE-ExploitID Reference:
CVE: CVE-2009-4091
Exploit Type: OffensiveSecurity
Exploit Unique ID: 10180
URL: https://www.exploit-db.com/exploits/10180
Description: Simplog 0.9.3.2 - Multiple Vulnerabilities
[*]Exploit Detail Info:
[*]OffensiveSecurity:
- Document:
Path: https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt
File Type: webapps
---------------------------------------
[*]CVE-ExploitID Reference:
CVE: CVE-2009-4092
Exploit Type: OffensiveSecurity
Exploit Unique ID: 10180
URL: https://www.exploit-db.com/exploits/10180
Description: Simplog 0.9.3.2 - Multiple Vulnerabilities
[*]Exploit Detail Info:
[*]OffensiveSecurity:
- Document:
Path: https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt
File Type: webapps
---------------------------------------
[*]CVE-ExploitID Reference:
CVE: CVE-2009-4093
Exploit Type: OffensiveSecurity
Exploit Unique ID: 10180
URL: https://www.exploit-db.com/exploits/10180
Description: Simplog 0.9.3.2 - Multiple Vulnerabilities
[*]Exploit Detail Info:
[*]OffensiveSecurity:
- Document:
Path: https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt
File Type: webapps
---------------------------------------用法:以服务器模式启动 go-exploitdb
$ go-exploitdb server -h
Start go-exploitdb HTTP server
用法:
go-exploitdb server [flags]
Flags:
--bind string HTTP服务器绑定到IP地址(默认为回循环接口)
-h, --help 服务器帮助信息
--port string HTTP服务器端口号(默认为1326)
全局标志:
--config string 配置文件 (默认是 $HOME/.go-exploitdb.yaml)
--dbpath string /path/to/sqlite3 或 SQL 连接字符串
--dbtype string 存储数据的数据库类型(sqlite3, mysql, postgres或redis支持)
--debug 调试模式(默认为关闭)
--debug-sql SQL调试模式
--http-proxy string http://代理url:端口 (默认: 空)
--log-dir string /path/to/log
--log-json 输出日志为 JSON
--log-to-file 输出日志到文件
启动服务器
$ go-exploitdb server
INFO[09-30|15:05:57] Starting HTTP Server...
INFO[09-30|15:05:57] Listening... URL=127.0.0.1:1326通过 cURL 获取针对 CVE 的搜索漏洞利用(例如 CVE-2006-2896)
$ curl http://127.0.0.1:1326/cves/CVE-2006-2896 | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:100 666 100 666 0 0 39340 0 --:--:-- --:--:-- --:--:-- 41625
[
{
"ID": 325173,
"exploit_type": "OffensiveSecurity",
"exploit_unique_id": "1875",
"url": "https://www.exploit-db.com/exploits/1875",
"description": "FunkBoard CF0.71 - 'profile.php' Remote User Pass Change",
"cve_id": "CVE-2006-2896",
"offensive_security": {
"ID": 325173,
"ExploitID": 325173,
"exploit_unique_id": "1875",
"document": {
"OffensiveSecurityID": 325173,
"exploit_unique_id": "1875",
"document_url": "https://github.com/offensive-security/exploitdb/exploits/php/webapps/1875.html",
"description": "FunkBoard CF0.71 - 'profile.php' Remote User Pass Change",
"date": "0001-01-01T00:00:00Z",
"author": "ajann",
"type": "webapps",
"platform": "php",
"port": ""
},
"shell_code": null,
}
}
]
按唯一 ID 搜索exploit(例如利用唯一 ID:10180)
$ curl http://127.0.0.1:1326/id/10180 | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:100 1936 100 1936 0 0 52643 0 --:--:-- --:--:-- --:--:-- 53777
[
{
"ID": 334917,
"exploit_type": "OffensiveSecurity",
"exploit_unique_id": "10180",
"url": "https://www.exploit-db.com/exploits/10180",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"cve_id": "CVE-2009-4091",
"offensive_security": {
"ID": 334917,
"ExploitID": 334917,
"exploit_unique_id": "10180",
"document": {
"OffensiveSecurityID": 334917,
"exploit_unique_id": "10180",
"document_url": "https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"date": "0001-01-01T00:00:00Z",
"author": "Amol Naik",
"type": "webapps",
"platform": "php",
"port": ""
},
"shell_code": null,
}
},
{
"ID": 334918,
"exploit_type": "OffensiveSecurity",
"exploit_unique_id": "10180",
"url": "https://www.exploit-db.com/exploits/10180",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"cve_id": "CVE-2009-4092",
"offensive_security": {
"ID": 334917,
"ExploitID": 334917,
"exploit_unique_id": "10180",
"document": {
"OffensiveSecurityID": 334917,
"exploit_unique_id": "10180",
"document_url": "https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"date": "0001-01-01T00:00:00Z",
"author": "Amol Naik",
"type": "webapps",
"platform": "php",
"port": ""
},
"shell_code": null,
}
},
{
"ID": 334919,
"exploit_type": "OffensiveSecurity",
"exploit_unique_id": "10180",
"url": "https://www.exploit-db.com/exploits/10180",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"cve_id": "CVE-2009-4093",
"offensive_security": {
"ID": 334917,
"ExploitID": 334917,
"exploit_unique_id": "10180",
"document": {
"OffensiveSecurityID": 334917,
"exploit_unique_id": "10180",
"document_url": "https://github.com/offensive-security/exploitdb/exploits/php/webapps/10180.txt",
"description": "Simplog 0.9.3.2 - Multiple Vulnerabilities",
"date": "0001-01-01T00:00:00Z",
"author": "Amol Naik",
"type": "webapps",
"platform": "php",
"port": ""
},
"shell_code": null,
}
}
]
go-exploitdb下载地址
GitHub:
go-exploitdb_0.4.1_linux_amd64.tar.gz
云中转网盘:
https://yzzpan.com/#sharefile=h6GQ2vaY_20733
解压密码:www.ddosi.org
注意事项:
新版本部分命令可能有所改动,
比如-type 改为 -stype
-param改为 -sparam
项目地址
转载请注明出处及链接