目录导航
Immunity Canvas 7.26 + White Phosphorus Exploit Pack 1.28 + D2 Exploitation Pack 2.51
Immunity Canvas简介
Immunity CANVAS为全球的渗透测试人员和安全专业人员提供了数百种漏洞利用程序,一个自动化的漏洞利用系统以及一个全面,可靠的漏洞利用开发框架。对于刚接触CANVAS的用户或有经验的用户,他们希望从CANVAS中获得更多收益,我们有基于PDF的教程 可供下载。

单一安装许可证
- 包括一年的标准每月更新和支持
- 不受限制(无目标IP地址限制)
- 完整的源代码
支持的平台和安装
- Windows(需要Python和PyGTK)
- 的Linux
- 所有其他Python环境,例如手机和商用Unix(仅支持命令行版本,也可能提供GUI)
建造
- CANVAS的完全开放式设计使团队可以使CANVAS适应其环境和需求。
文献资料
- 所有文档均以演示影片的形式提供
- 漏洞利用模块具有其他信息
- 目前有800多个漏洞
- Immunity会仔细选择要包含在CANVAS漏洞中的漏洞。当务之急是高价值漏洞,例如远程软件,预身份验证以及主流软件中的新漏洞。
- 漏洞涵盖所有常见平台和应用程序
有效载荷选项(payloads)
- 为了提供最大的可靠性,漏洞利用总是尝试重用套接字
- 如果套接字重用不合适,则使用connect-back
- 随后的MOSDEF会话允许执行任意代码,并为常用操作(文件管理,屏幕截图等)提供侦听器shell
- 可以通过MOSDEF自动进行弹跳和拆分弹跳
- 可调隐蔽度
利用交付
- 通过网络提供的每月定期更新
- 漏洞利用模块和CANVAS引擎同时更新
- 客户通过电子邮件提醒每月更新
利用创建时间
- 稳定发行后的下一版本中的漏洞利用
漏洞利用的有效性
- 所有漏洞在发布前均经过全面质量检查
- 通过Flash电影展示的漏洞利用
- 可通过直接电子邮件获得利用开发团队的支持
进行自定义漏洞利用的能力
- 独特的MOSDEF开发环境允许快速开发漏洞利用程序
产品支持与维护
- 订阅包括电子邮件和电话支持,美国东部时间上午9点至下午5点(直接与开发团队联系)
- 每月最少一次更新
发展
- CANVAS是一个旨在轻松开发其他安全产品的平台。例如,DSquare的D2开发包,Intevydis的VulnDisco,Gleg的Agora和SCADA。
Immunity Canvas截图





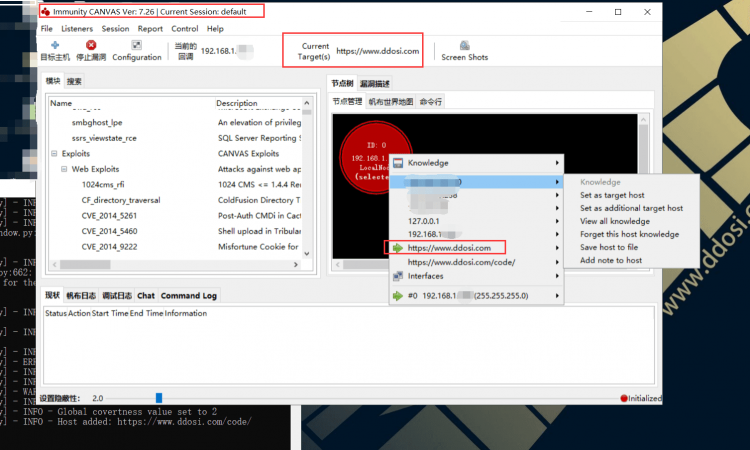
此处使用节点管理节点视图对此进行了演示,该视图显示了被利用的主机及其相互之间的关系。




也可以从命令行完全驱动CANVAS,从而将模块轻松集成到脚本中。
CANVAS严重依赖“侦听器”的概念。CANVAS侦听器是需要响应操作的所有内容,例如正在运行的漏洞利用模块,等待回调的开放端口或与已被利用的远程主机的连接。在此屏幕截图中,您可以看到一种高级CANVAS工具,该工具用于在被利用的过程中打印出所有可用的安全令牌。
然后,CANVAS用户可以将安全性令牌切换到找到的任何令牌,并尝试以新用户身份访问文件。
CANVAS严重依赖“侦听器”的概念。
CANVAS侦听器是需要响应操作的所有内容,例如正在运行的漏洞利用模块,等待回调的开放端口或与已被利用的远程主机的连接。在此屏幕截图中,您可以看到一种高级CANVAS工具,该工具用于在被利用的过程中打印出所有可用的安全令牌。
然后,CANVAS用户可以将安全性令牌切换到找到的任何令牌,并尝试以新用户身份访问文件。Covertness Bar是CANVAS的一项特殊功能,它允许某些漏洞利用程序根据用户需要的隐秘程度而有所不同。例如,应用程序防火墙有时会掩盖较高的隐蔽性,因为应用程序碎片会使防火墙无视流量。
可靠性和隐蔽性在Covertness Bar上是相反的,就像在现实生活中一样。CANVAS的多线程体系结构使高级用户可以一次运行多个漏洞利用,甚至可以将多台计算机的漏洞利用尝试合并到一个控制台中。
应用程序防火墙有时会掩盖高级别的隐蔽性,因为应用程序碎片会使防火墙无视流量。
可靠性和隐蔽性在Covertness Bar上是相反的,就像在现实生活中一样。
CANVAS的多线程体系结构使高级用户可以一次运行多个漏洞利用,甚至可以将多台计算机的漏洞利用尝试合并到一个控制台中。应用程序防火墙有时会掩盖高级别的隐蔽性,因为应用程序碎片会使防火墙无视流量。可靠性和隐蔽性在Covertness Bar上是相反的,就像在现实生活中一样。
CANVAS的多线程体系结构使高级用户可以一次运行多个漏洞利用,甚至可以将多台计算机的漏洞利用尝试合并到一个控制台中。
Immunity Canvas文献资料
各个CANVAS模块文档可在CANVAS GUI中查看,标准文档包含在每个版本的CANVAS变更日志中, 书面教程 也可以使用,但是记录CANVAS使用情况的最佳方法是使用示例:
基本概述
演示基本的CANVAS使用。涵盖GUI布局和交互,并解释CANVAS设计。
客户端开发
通过RealPlayer ActiveX导入堆栈溢出漏洞演示了CANVAS Professional ClientSide开发。
地理意识
演示CANVAS专业地理意识支持。
特权提升
演示如何在CANVAS Professional中集成本地特权升级。
HTTP隧道特权升级
演示了利用客户端错误以及如何通过便捷的方式通过HTTP传送漏洞的特权升级。
远程内核开发
Immunity ms08-001 IGMP远程内核利用程序的演示扫描易受攻击的Windows计算机的本地网络,并成功地对其进行利用。
先进的后门技术
演示抗扰性CANVAS的Windows内核Rootkit
先进的网络攻击技术
演示如何直接从PHP eval()攻击中反弹
CANVAS教程
以下链接是最初出现在论坛上的CANVAS使用教程的PDF版本。随着我们继续将旧资料转换为这种格式,可用教程的列表将会增加。
Immunity的CANVAS为全球的渗透测试人员和安全专业人员提供了数百种漏洞利用,一个自动化的漏洞利用系统以及一个全面,可靠的漏洞利用开发框架。要查看CANVAS的实际效果,请参见我们的视频文件 或查看 Vimeo上的CANVAS视频收藏。
CANVAS依赖关系
CANVAS依赖于以下(免费)软件包来运行:
- Python 2.6或2.7
- GTK
- PyCrypto(某些模块)
- Py-GTK及其相关库
- Pyasn1
- CANVAS 策略:ZeroMQ / PyZMQ
- Pynacl
- Bcrypt
- Asn1tools
Linux用户
Linux用户将需要获取以下软件包以获取其体系结构和python版本。如果某个软件包不可用,则某些发行版可能必须从源代码编译依赖项。
注意:可以从您选择的软件包管理工具中下载软件包:yum,rpm,apt-get,emerge等。
- Python25,Python26或Python27
- GTK2
- pycairo
- pygobject
- pycrypto
- pygtk
- pyasn1
- pynacl
- bcrypt
- asn1tools
发行特定说明
Ubuntu 18.04、17.10、16.10、16.04
Windows用户
Windows用户可以下载我们新的依赖项安装程序,该安装程序将下载并设置运行CANVAS所需的每个必需的依赖项(包括python 2.7(如果已选择))。
sha256sum:7024f8140b7d0ca56411bda12a2eecb1690693d1dc5910550682c57d7deb5439Mac OS X用户
OSX用户可以从Immunity下载对该平台具有最高依赖性的安装程序。然后,您可以将CANVAS下载为zip / tar文件,然后对其进行解压缩并运行CANVAS_ROOT/runcanvas.sh。请注意,您仍然需要自行安装pyasn1,pycrypto,pynacl,bcrypt和asn1tools。
sha256sum:3afc4f67b7272735d2490110aa79b5b46384f48cd1586b9683b82e7d7502d125CANVAS系统要求
硬件
CANVAS在任何现代硬件上都能很好地运行。一个简单的问题是问自己,硬件运行所选操作系统的性能如何。如果您的硬件运行良好,那么CANVAS将运行良好。以下是一些最低规格。
- 1.2GHz处理器
- 芯片架构/操作系统必须具有Python 2.5或更高版本的支持
- 1GB内存
- 250mb可用高清空间
- 适用于有线/无线卡的良好Linux驱动程序
操作系统
CANVAS是为在Linux上运行而编写的。Windows和OSX是受支持的平台,而Linux是CANVAS真正的亮点。如果您将Windows作为企业IT策略的一部分,则CANVAS在VM中也可以很好地运行(请参阅上面的要求)。对于Linux,任何具有可靠软件包管理功能的现代桌面发行版都可以使用。我们推荐:
可以找到在Linux(包括RHEL)上安装CANVAS的视频演示。 这里
Windows用户
Windows用户可以从Immunity下载该平台的zip文件以及所有依赖关系(pycrypto除外)和安装说明。
由于出口管制的限制,我们无法运送pycrypto库。您可以通过下面显示的链接下载Windows的二进制安装程序。
Mac OSX用户
OSX用户可以从Immunity下载对该平台具有最高依赖性的安装程序。然后,您可以将CANVAS下载为zip / tar文件,然后对其进行解压缩并运行CANVAS_ROOT/runcanvas.sh。请注意,您仍然需要自行安装pyasn1。
exploits列表
exploits
+---clientside
| +---universal
| | +---clientdsample
| | +---CVE_2010_4452
| | | \---Resources
| | +---emacs_enriched
| | | \---Resources
| | +---java_AtomicReferenceArray
| | +---java_CVE_2012_5088
| | +---java_deserialize
| | +---java_deserialize2
| | +---java_DynamicBinding
| | | \---Resources
| | +---java_forName_getField
| | +---java_generic_mosdef
| | | \---Resources
| | +---java_jaxws
| | +---java_MBeanInstantiator_findClass
| | | \---Resources
| | +---java_method_chain
| | +---java_rhino
| | +---js_recon
| | +---ooo_230
| | +---safari_file_stealing
| | +---safari_file_stealing2
| | \---safari_navaction
| +---unix
| | +---android_parentstylesheet
| | +---apport_crash_handler
| | | \---Resources
| | +---CVE_2010_1807
| | +---firefox_pdfjs_filereader
| | | \---Resources
| | +---safari_parentstylesheet
| | \---sun_java_hsbparser_linux
| \---windows
| +---acrobat_exec
| +---acrobat_flash
| +---acrobat_jbig
| +---acrobat_js
| +---acrobat_js3
| +---acrobat_js4
| +---acrobat_libtiff
| +---acrobat_newplayer
| +---acrobat_toolbutton
| +---acrobat_ttf_sing
| | \---Resources
| +---acrobat_u3d_mesh
| +---acrobat_xfa
| | \---Resources
| +---adobe_flash_button
| | \---Resources
| +---adobe_flash_copypixelstobytearray
| | \---Resources
| +---adobe_flash_domainMemory_uaf
| | \---Resources
| +---adobe_flash_id3
| | \---Resources
| +---adobe_flash_intoverflow_apply
| | \---Resources
| +---adobe_flash_metadata_uaf
| | \---Resources
| +---adobe_flash_mp4_cprt
| | \---Resources
| +---adobe_flash_otf_parsing
| | \---resources
| +---adobe_flash_regexp
| | \---Resources
| +---adobe_flash_valueof
| | \---Resources
| +---adobe_shockwave_rcslchunk
| | \---Resources
| +---ani_cursor
| +---aurora_flash
| +---binder
| +---binderx
| | \---Resources
| +---cutezip_filename
| | \---Resources
| +---firefox_35
| +---firefox_appendchild
| +---firefox_array_reduceright
| +---firefox_channelredirect
| +---firefox_definesetter
| +---firefox_nsSVGValue
| +---firefox_utf8
| +---flash_APSB11_18
| +---flash_duke
| +---flash_newfunction
| +---flash_wild2
| | \---Resources
| +---FoxitLaunchit
| +---foxit_Action
| +---foxit_printf
| +---gapple_client
| +---gomplayer
| +---greendam_url
| +---hanword_exec
| | \---Resources
| +---ie7wmp
| +---iepdf
| +---ie_cardspaceclaimcollection
| +---ie_cdisplaypointer
| +---ie_cmarkup
| +---ie_comments
| +---ie_dumpfiles
| +---ie_execCommand
| +---ie_hcp
| +---ie_help
| +---ie_peers_setattribute
| +---ie_setuserclip
| +---installshield
| +---Itunes_10_6_1
| +---java_deserialize_win32
| +---java_docbase
| +---jetbrains_rce
| | \---Resources
| | \---projects
| | \---pycharm
| | \---.idea
| +---lnk_exec
| +---mosdef_activex
| +---ms06_014
| +---ms06_024
| +---ms06_055
| +---ms06_057
| +---ms06_071
| +---ms07_004
| +---ms07_051
| +---ms08_053
| +---ms08_078
| +---ms09_002
| +---ms09_032
| +---ms09_051
| +---ms09_061_cas
| +---ms10_026
| +---ms10_060
| | \---Resources
| | \---Application Files
| | \---reporterror_1_0_0_14
| +---ms11_003
| +---ms12_004
| | \---Resources
| +---ms12_005
| | \---Resources
| +---ms12_027
| +---ms12_037
| +---ms12_043
| +---ms13_056
| | \---Resources
| +---ms14_064_ie_oleaut32
| | \---Resources
| +---ms15_100
| +---ms16_006_silverlight
| | \---Resources
| +---office_dde
| | \---Resources
| +---office_wsdl
| | \---Resources
| +---opera_css
| +---pdf_u3d
| | \---Resources
| +---qt73_rtsp
| +---qt_rtsp
| +---quick_punk
| +---real_import
| +---safari_renderdestroy
| +---sandworm
| | \---Resources
| +---special_lnk
| +---speech
| +---ssreader
| +---sun_java_hsbparser
| +---trendmicro_maxsec_10
| +---trendmicro_setowned
| +---utorrent
| +---windows_shell_lnk
| +---wmf_setabort
| \---wpad_jscript
| \---Resources
+---command
| +---universal
| | +---adduser
| | +---chdir
| | +---checkvm
| | +---computername
| | +---converttomosdef
| | +---deluser
| | +---dir
| | +---diskspider
| | +---download
| | +---drinkcoaster
| | +---exitprocess
| | +---getarch
| | +---getcwd
| | +---gethostbyname
| | +---getpid
| | +---inject_from_mem
| | +---kerberos_ticket_export
| | +---kerberos_ticket_list
| | +---killprocess
| | +---memory_harvest
| | +---ps
| | +---rmdir
| | +---runcommand
| | +---spawn
| | +---startup
| | +---tcphostfind
| | +---unlink
| | +---upexec
| | +---upload
| | +---vbox_list_vms
| | +---vbox_vm_exec_cmd
| | +---vbox_vm_keystroke_injection
| | +---whoami
| | \---WiFi_Key_Dumper
| +---unix
| | +---GetRoot
| | +---NetworkManagerUnSecret
| | +---pcap_sniffer
| | +---pty_shell
| | +---setuid
| | \---switch_user
| \---windows
| +---addnullshare
| +---ad_check4PSadmin
| | \---Resources
| +---ad_dlexecute_psmosdef
| +---ad_getcomputers
| | \---Resources
| +---ad_getdomainusers
| | \---Resources
| +---ad_getlocalusers
| | \---Resources
| +---ad_getuserdetails
| | \---Resources
| +---arpscan
| +---cachedump
| +---callbackloop
| +---check_admin_user
| +---cleareventlog
| +---converttopowershell
| +---createservice
| +---curveball
| | \---Resources
| +---dcsync
| +---deleteservice
| +---disable_windows_defender
| +---disable_windows_firewall
| +---domainname
| +---dump_certstore
| | \---Resources
| +---DuplicateToken
| +---enumservices
| +---exitthread
| +---ExitWindows
| +---GetAddressBookInfo
| +---getallprocessdata
| +---GetBrowserInfo
| +---GetDrives
| +---getfileversion
| +---getintegritylevel
| +---getkey
| +---GetLocale
| +---getloggedinhashes
| +---getpasswordhashes
| +---getpriv
| +---getprocessname
| +---GetSystem
| | \---Resources
| +---getthreadsinfo
| +---GetUserActive
| +---getwindowscredentials
| +---get_dnscache
| +---get_installed_software
| +---get_installed_updates
| +---get_machinekeys
| | \---Resources
| +---get_putty_info
| +---get_token_info
| | \---Resources
| +---info_sessions
| +---injectdll
| +---keylog
| +---keylog2mem
| +---LogonUser
| +---lsadump
| +---modify_registry
| +---mosdefmigrate
| +---motiondetect
| +---passwordhints
| +---powershellcommand
| +---processinject
| +---psexec
| | \---Resources
| +---ps_invokemimikatz
| | \---Resources
| +---recordaudio
| +---recordvideo
| +---reg_add_value
| +---reg_create_key
| +---reg_delete_key
| +---reg_delete_value
| +---reg_dump
| +---reg_fingerprint
| +---reg_loggedon
| +---restartservice
| +---runpowershellscript
| +---samdump
| +---saycheese
| +---screengrab
| +---setthreadtoken
| +---startremoteservice
| +---startservice
| +---stopservice
| +---threadio
| +---touch
| +---touchfromfile
| +---windows_sniffer
| +---wlanlist
| +---wordpress_backdoor
| \---wordpress_backdoor_connect
+---config
| +---configuration
| \---remark_in_log
+---DoS
| +---Exchange_DoS
| +---iisftp_globbing
| +---ms07_019
| +---ms07_031
| +---ms08_063
| +---ms09_001
| +---ms09_013
| +---ms09_029
| +---ms09_041
| +---ms09_059
| +---ms10_068
| +---msrpccrash
| +---ms_msdtc
| +---pgpwdef
| +---realserver2
| +---smbloris
| | \---Resources
| +---umpnp_dos
| \---windows7netbioscrash
+---fuzzer
| +---msrpcfuzz
| \---tftp_fuzzer
+---importexport
| +---avdsimport
| +---importscan
| +---nessusxml
| +---nexposeimport
| +---nmapxml
| \---qualysguard
+---local
| +---unix
| | +---aixroot
| | +---android_hotplug
| | | \---Resources
| | +---chfnescape
| | +---CVE_2004_1329
| | +---CVE_2006_4842
| | +---CVE_2007_4003
| | +---CVE_2007_4513
| | +---CVE_2010_3847
| | | \---Resources
| | +---CVE_2010_3856
| | | \---Resources
| | +---CVE_2011_0182
| | | \---Resources
| | +---CVE_2011_1485
| | | \---Resources
| | +---CVE_2012_0056
| | | \---Resources
| | +---CVE_2016_1757
| | | \---Resources
| | +---dmesg_leak
| | | \---bin
| | +---DSU
| | +---fs_pipe_race_to_null
| | | \---Resources
| | +---linux_foll_write_cow
| | | \---Resources
| | +---linux_futex_requeue
| | | \---Resources
| | +---linux_pppol2tp
| | | \---Resources
| | +---linux_ptrace_setregs
| | | \---Resources
| | +---linux_rds
| | | \---Resources
| | +---linux_screen
| | | \---Resources
| | +---linux_tty_race
| | | \---Resources
| | +---linux_waitid_write
| | | \---Resources
| | +---maptrace
| | | \---Resources
| | +---ntfs3g_modprobe
| | | \---Resources
| | | +---3.16.0-4-amd64
| | | | \---compiled
| | | +---4.9.0-3-amd64
| | | | \---compiled
| | | \---sources
| | +---osx_dyld_print_to_file
| | +---osx_parsekeymapping
| | | \---Resources
| | +---osx_rootpipe2
| | | \---Resources
| | +---osx_rsh_libmalloc
| | +---osx_stickykeysfree
| | | \---Resources
| | +---overlayfs
| | | \---Resources
| | +---overlayfs_setattr
| | | \---Resources
| | +---perf_swevent_init
| | | \---Resources
| | +---PROCFS
| | +---proto_ops_null
| | +---recvmmsg
| | | \---Resources
| | +---rootpipe
| | | \---Resources
| | +---show_timer_leak
| | | \---bin
| | +---snapd_uid_overwrite
| | +---solaris_LD_PRELOAD
| | +---solroot
| | +---spectre_file_leak
| | | \---bin
| | +---sudo_elevate
| | | \---Resources
| | +---sudo_timestamp
| | | \---Resources
| | +---SYSRET
| | | \---Resources
| | +---udevd
| | +---usort_safemode
| | \---vmsplice
| \---windows
| +---alpc_appxedge_lpe
| | \---Resources
| +---alpc_takeover_lpe
| | \---Resources
| +---alpc_tasksched_lpe
| | \---Resources
| +---atmfd_pool_buffer_underflow
| | \---Resources
| +---CLOUDBURST
| +---CVE_2013_3881
| | \---Resources
| +---dde_closehandle_lpe
| | \---Resources
| +---destroyclass_uaf_lpe
| +---error_reporting_lpe
| | \---Resources
| +---ESET_EpFwNDIS
| | \---Resources
| +---ESET_LPC
| | \---Resources
| +---event_viewer_mscfile
| +---GDIWrite4
| +---i2omgmt
| +---localLPC
| +---menu_confusion_lpe
| | \---Resources
| +---mqac
| +---ms05_040
| +---ms07_066
| +---ms07_067
| +---ms08_025
| +---ms08_034
| +---ms08_049
| +---ms10_032
| +---ms10_048
| | \---Resources
| +---ms10_059
| +---ms11_032
| | \---Resources
| +---ms11_054
| | \---Resources
| +---ms11_080
| | \---Resources
| +---ms11_098
| | \---Resources
| +---ms12_042
| | \---Resources
| +---ms14_025
| +---ms14_040
| | \---Resources
| +---ms14_070
| +---ms15_051
| | \---Resources
| +---ms15_102
| | \---Resources
| +---ms16_032
| | \---Resources
| +---ms16_111
| | \---Resources
| +---ms16_135
| | \---Resources
| +---msimpersonate
| +---ms_enableeudc
| | \---Resources
| +---ms_kblayout
| | \---Resources
| +---ms_ntvdm
| +---ms_taskscheduler
| | \---Resources
| +---ms_tokenkidnapping
| +---ndproxy
| +---novell_nicm
| +---sdclt_uac_bypass
| +---seimpersonatepriv_lpe
| | \---Resources
| +---setimeinfoex_lpe
| | \---Resources
| +---setwindowfnid_lpe
| | \---Resources
| +---smb2_negotiate_local
| +---smbghost_lpe
| | \---Resources
| +---spectre_sam_leak
| | \---bin
| +---tpminit_wbemcomn
| | \---Resources
| +---unmarshal_to_system
| | \---Resources
| +---vbox_guest
| \---winpcap
+---recon
| +---dcedump
| +---dellchassis
| +---delldrac
| +---dnsfind
| +---dot_dot_slash
| +---getprintproviders
| +---getremotelanguage
| +---getservices
| +---getwwwhostnames
| +---httpfingerprint
| +---http_method_scanner
| +---icmpsweep
| +---ifids
| +---ipfingerprint
| +---ipheuristic
| +---ip_to_vhosts
| +---mssqlresolve
| +---mysql_version_detection
| +---osdetect
| +---owa_ipleak
| +---parallel_portscan
| +---portscan
| +---portsweep
| +---revproxybypass
| +---rmi_scanner
| +---rpcdump
| +---shareenum
| +---shareenum_ng
| +---smbversion
| +---smtp_fingerprint
| +---spdetect
| +---telnetbanner
| +---testhost
| +---traceroute
| +---udpportscan
| +---udpsweep
| +---urlmangle
| +---userenum
| +---webcrawler
| +---whereami
| +---wp_finger
| +---wp_plugindetect
| +---wp_themedetect
| \---zeroconf_recon
+---remote
| +---cisco
| | \---cisco_snmp_oid
| | \---Resources
| +---universal
| | +---aspnet_download
| | +---confluence_macro_lfi
| | +---ftpd_check
| | +---hpe_ilo4_addNewAdmin
| | +---java_rmi_service
| | | \---Resources
| | +---jbossmq_httpil_deserialization
| | +---jenkins_jrmp_deserialization
| | | \---Resources
| | | \---cli_request
| | +---lshttpd_disc
| | +---mysql_auth_bypass
| | +---mysql_login_remote
| | +---nss
| | +---realvnc_noauth
| | +---sap_bi_p4
| | +---snortrpc
| | +---ssh_enum
| | +---struts2_dmi_rce
| | | \---Resources
| | +---struts_ognl
| | | \---Resources
| | \---wls_core_deserialization
| +---unix
| | +---airos_remote_write
| | +---aixcmsd
| | +---aixttdb
| | +---alienvault_alarm_deserialization
| | +---asus_samba
| | +---cachefsd_lpd
| | +---cmsd_xdrarray
| | +---CVE_2010_4344
| | +---CVE_2011_0997
| | +---CVE_2012_1182
| | +---CVE_2012_1182_NONX
| | +---CVE_2012_5613
| | +---dotnetnuke_formbypass
| | | \---Resources
| | +---dtspcd
| | +---evocam
| | +---exim_expansion_rce
| | +---exim_heap_overflow
| | +---goahead_env_rce
| | | \---Resources
| | +---gpsd
| | +---horde_eval
| | +---hplaserjet_connect
| | +---hp_imc_rce
| | +---in_lpd
| | +---iplanet_chunked
| | +---linksys_apply_cgi
| | +---mu
| | +---netopia_adsl
| | +---netscaler_traversal_rce
| | +---nginx
| | +---nginx_chunk
| | +---openssl_keylen
| | +---padding_oracle
| | | \---Resources
| | +---php_limit
| | +---proftpd_mod_copy
| | +---pserverd
| | +---rexd
| | +---rsync
| | +---sadmind
| | +---samba_is_known_pipename
| | | \---Resources
| | +---samba_nttrans
| | +---samba_trans2
| | +---sapdb
| | +---shoutcast_fs
| | +---snmpXdmid
| | +---solaris_rpc_cmsd
| | +---solaris_rpc_libnsl
| | +---solaris_samba
| | +---solaris_telnet
| | +---sol_printer_conf
| | +---stinky
| | +---stinky_debug
| | +---sunlogin
| | +---sunlogin_pamh
| | +---svndate
| | +---ttdb_xdrarray
| | +---unixshellfromport
| | +---webmin
| | +---wuftpd_sexec
| | +---wuglob
| | +---xampp_webdav
| | +---xfs_swapchar2b
| | +---ypbind
| | \---yppasswdd
| \---windows
| +---3comtftp
| +---abyss
| +---altn_sg
| +---apachechunk_win32
| +---awservices
| +---bigant22
| +---blackice
| +---BLUEKEEP
| | \---payloads
| +---borland_ib
| +---brightstor_cmdexec
| +---brightstor_discovery
| +---brightstor_media
| +---brightstor_message
| +---cam
| +---ca_lic
| +---cesarftp
| +---citect_scada
| +---citrix_metaframe
| +---citrix_pp
| +---CVE_2010_3964
| +---CVE_2011_3175
| +---CVE_2011_3176
| +---db2_jdbc
| +---domino_cram
| +---easyfilesharing
| +---edirectory_http
| +---emc_networkerFS
| +---ETERNALBLUE
| | \---custom_libs
| | +---kerberos
| | | \---asn1
| | \---newsmb
| +---eznet
| +---ezserver
| +---filecopa
| +---fp30reg
| +---goodtech_ssh
| +---groupwise_messenger
| +---groupwise_webaccess
| +---harborlisten
| +---IAWebMail
| +---icecast
| +---iis5asp
| +---iis6_propfind
| +---iisftp_nlst
| +---iis_doubledecode
| +---iis_webdav
| +---imail_imap
| +---imail_rcptoverflow
| +---Insight
| +---ipswitch_cal
| +---lotus_domino_http
| +---mailenable
| +---mailenable_imap
| +---mdaemon
| +---mdaemon_control
| +---MercurImapSubscribe
| +---ms01_023
| +---ms01_033
| +---ms03_001
| +---ms03_007
| +---ms03_022
| +---ms03_026
| +---ms03_049
| +---ms04_007
| +---ms04_011_lsass
| +---ms04_011_sslpct
| +---ms04_031
| +---ms04_045
| +---ms05_010
| +---ms05_017
| +---ms05_021
| +---ms05_039
| +---ms05_043
| +---ms05_046
| +---ms06_025
| +---ms06_025b
| +---ms06_040
| +---ms06_066
| +---ms06_070
| +---ms06_074
| +---ms07_029
| +---ms07_065
| +---ms08_001
| +---ms08_059
| +---ms08_062
| +---ms08_067
| +---ms09_022
| +---ms09_022_loaddll
| +---ms10_025
| +---ms10_061
| +---ms14_068
| +---ms17_010
| +---mssqlhello
| +---mssqlresolvestack
| +---mssql_auth
| +---mssql_replwritetovarbin
| +---mswinstcp
| +---msxexch50
| +---naimas32
| +---netbackup_javaui
| +---netmail
| +---netmail_webadmin
| +---niprint
| +---norton_upx
| +---nwspool_a
| +---nwspool_b
| +---nwspool_c
| +---openview_trace
| +---oracle8listener_win32
| +---OSVDB_65361
| +---OSVDB_65361_0x6
| +---owa_rce
| | \---Resources
| +---radexecd
| +---realserver
| +---samiftp
| +---savant
| +---slwebsupervisor
| +---smartag_word
| +---smb2_negotiate_remote
| +---SMBGHOST
| | \---Resources
| +---ssrs_viewstate_rce
| | \---Resources
| +---symantec_iao
| +---symantec_rm
| +---tivoli_storage
| +---tm_sprotect
| +---tm_sprotectagent
| +---tomcat_file_upload
| | \---Resources
| +---ut2004secure
| +---VAASeline_Control
| +---veritas_decrypt
| +---vmware_dhcpd
| +---vsploit_exchangepop3
| +---vsploit_mercurimap
| +---vsploit_winamp512
| +---vsploit_winprox
| +---w3who
| +---warftp_165
| +---wftpd
| +---wingate_httpproxy
| +---wireshark_dect
| +---worldmail
| +---WS_FTPD
| +---ws_ftpd_xcrc
| +---xitami
| \---zen
+---reporting
| \---canvas_report
+---server
| +---badtunnel
| | \---Resources
| +---clientd
| +---dns_proxy
| +---httpserver
| +---httpuploader
| +---http_proxy
| +---icmp_proxy
| +---ms08_068
| +---spikeproxy
| \---xserver
+---tool
| +---addhost
| +---addhostsfromfile
| +---atsvc
| +---autoassess
| +---autohack
| +---compile
| +---debian_ssh_key_brute
| +---del_idrac_user
| +---emailsender
| +---find_null_vnc
| +---frontpage_rpc_fileupload
| | \---Resources
| +---get_idrac_users
| +---iis_machinekey
| | \---Resources
| +---jboss7_management_deployer
| | \---resources
| +---massattack2
| +---oraclegetinfo
| +---oraclegetpwd
| +---oraclegetuser
| +---smbbrute
| +---smbclient
| +---smtp_mass_scan
| +---snmp_brute
| +---ssh_brute
| +---ssh_reverse_tunnel
| +---telnet_brute
| \---VulnAssess2
+---trojan
| +---BuildCallbackTrojan
| +---BuildDNSCallback
| +---BuildHTTPCallback
| +---BuildMOSDEFDLL
| +---BuildPowershellCallback
| +---BuildWARCallbackTrojan
| | \---Resources
| +---connecttoservice
| +---inject_mosdef
| +---installmosdefservice
| +---installremotemosdefservice
| +---linrootkitinject
| +---loadlinrootkit
| +---ram_dumper
| +---thunderbird_backdoor_deployer
| | \---extension
| | \---content
| +---thunderbird_backdoor_manager
| \---wmi_persistence
| \---Resources
\---web
+---1024cms_rfi
+---acutecp_rfi
+---adaptcms_rfi
+---adminbot_include
+---aimstats_exec
+---ajaxfb_include
+---anyinventory_include
+---awzmb_include
+---b1gbb_include
+---barryvan_include
+---blindisapi
+---blog_pixelmotion
+---booby_include
+---brightmail_restore
+---browsercrm_include
+---cep_include
+---CF_directory_traversal
+---citrix_netscaler_soap
+---cmsmadesimple_eval
+---coldfusion_rce
| \---Resources
+---coppermine
+---couchdb_roles
| \---Resources
+---cpcommerce_rfi
+---cutenews_exec
+---CVE_2014_5261
+---CVE_2014_5460
+---CVE_2014_9222
+---dagger_include
+---dfblog4_exec
+---dfdcart_include
+---dokeos_rce
+---dokuwiki_exec
+---dokuwiki_exec2
+---dragoon_include
+---drupal_name_sqli
+---drupal_name_sqli_callback
+---drupal_services_rce
+---drupal_services_sqli
+---e107_exec
+---easypx41_lfi
+---elasticsearch_CVE_2015_1427
| \---Resources
+---enetman_include
+---FCKEditor
+---flatchat2_exec
+---flip_include
+---frontaccount_include
+---fuzzylime_include
+---gallery1_include
+---geeklog2_remote
+---gneric_include
+---grape_include
+---groupe_include
+---helplink_include
+---idrac_appweb_rce
| \---Resources
+---izicontents_include
+---jafcms_include
+---jboss6_jmxinvokerservlet_deserialize
+---jboss_jmxconsole_deployer
| \---resources
+---jenkins_checkscript_rce
+---jenkins_cli_deserialization
+---jenkins_xstream_rce
| \---Resources
+---joomla12pic_include
+---joomlaartform_rfi
+---joomlachronoforms_include
+---joomlaclickheat_rfi
+---joomlacolorlab_include
+---joomlacompetitions_rfi
+---joomlacp_include
+---joomladadamail_rfi
+---joomlafeedrator_rfi
+---joomlaflashfun_include
+---joomlaflashup_include
+---joomlagooglebase_rfi
+---joomlajcs_include
+---joomlajuser_include
+---joomlamosdirectory_include
+---joomlamosmedia_include
+---joomlamp3_include
+---joomlaoflq_include
+---joomlaradiov5_include
+---joomlarss_rfi
+---joomlaslideshow_include
+---joomlatimesheet_rfi
+---joomlatreeg_rfi
+---joomla_eval
+---joomla_mm_rce
+---joomla_session_unserialize
+---joompana_include
+---journalness_exec
+---jquery_file_upload
+---lamasoft_include
+---lavague_include
+---limesurvey_include
+---linksnet_include
+---livealbum_include
+---lms_include
+---lookstrike_include
+---loudblog_exec
+---lsgb_exec
+---magento_set_pay_info
+---mantis113
+---mazensphpchat_remote
+---MEWebMail
+---mindmeld_include
+---minibill_include
+---mknoboard_include
+---moinmoin_rce
+---mssqlinject
+---musoo_include
+---mygallery_remote
+---nagios_ping
+---ncaster_include
+---netrisk_include
+---news2_include
+---newsoffice_include
+---nuboard_include
+---nuclearbb_include
+---offl_include
+---openads_exec
+---openrealty_exec
+---oracle_forms_rce
+---ossigeno_include
+---ote_include
+---pacercms_exec
+---pbd_include
+---pbx_rce
+---peopleaggregator_include
+---persism_remote
+---philex_include
+---phpauction_include
+---phpbbplus_include
+---phpbb_highlight
+---phpbg_include
+---phpblock_include
+---phpdj_include
+---phpffl_include
+---phphtml_remote
+---phplinkadmin_rfi
+---phplinks_include
+---phplist_lfi
+---phpmyadmin_injection
+---phpmybb1210_include
+---phpmytourney_include
+---phpnews_include
+---phporacle_include
+---phppm_include
+---phpprofiles_include
+---phpqladmin_include
+---phprealty_include
+---phpsitebackup_include
+---phpskelsite_rfi
+---phpslash_rce
+---phpuserbase_include
+---phpwcms_include
+---phpyabs_rfi
+---php_cgi_remote
+---php_includetest
+---pindorama_include
+---piwik
+---plone
+---pluck_lfi
+---pnphpbb2_lfi
+---podcastgen_include
+---portallwebphp_include
+---powl_include
+---punbb_langexec
+---qgs_include
+---quickteam_rfi
+---quinsonnas_include
+---rails_accept_readfile
+---rails_actionpack_render
+---rails_activestorage_rce
+---rails_webconsole_rce
+---rconfig_ajaxserver_rce
+---ripecms_include
+---roundcube
+---scwiki_include
+---segue_include
+---serweb_include
+---shoutpro_exec
+---sige_include
+---sitellite_remote
+---sitex_lfi
+---slogin_rfi
+---smallaxe_include
+---smartpub_exec
+---smf_csrf
+---smf_exec
+---smf_exec_gif
+---someryc_include
+---sourdough_include
+---sphpell_include
+---strawberry_lfi
+---streamline_include
+---struts2_default_action_mapper
+---strutsCodeInjection
+---sugarcrm_fileupload
+---sunboard_include
+---test_cle
+---test_safemode_bypass
+---tikiwiki_exec
+---tinymce_joomla
+---towel_include
+---trionic_include
+---trixbox_exec
+---troforum_include
+---txxcms_include
+---vbulletin_preauth_decodeArguments
+---vbulletin_widget_rce
+---vehicleworkshop_upload
+---visualpic_include
+---vportal_include
+---vrealize_vcofactory_deserialize
+---WAnewsletter_remote
+---webdesktop_include
+---webed_include
+---weblogic_t3_deserialization
+---wordsmith_include
+---wordtube_remote
+---worksimple_rfi
+---wpbackup_include
+---wpdm_fileupload
+---wpeasycart_rce
+---wpflash_include
+---wpsniplets_exec
+---wpsniplets_rfi
+---wpsymposium_rce
+---wptable_remote
+---wptouch_nonce
+---wpuserpro_rce
+---xoops_cjcontent
+---xoops_horoscope
+---xoops_icontent
+---xoops_tinycontent
+---xoops_xtconteudo
+---zabbix
\---zencart_remote
CANVAS_Dependency_Installer校验码
CANVAS_Dependency_Installer.exe
SHA256:
7024f8140b7d0ca56411bda12a2eecb1690693d1dc5910550682c57d7deb5439
MD5:
51c28d40e9582f6760ce24cad042c4ba
Immunity Canvas下载地址
①迅雷网盘:https://pan.xunlei.com/ 提取码: xk77
②雨苁网盘: https://w.ddosi.workers.dev
解压密码: www.ddosi.org
ubuntu安装方法
sudo apt-get update
sudo apt-get -y install python-pip
sudo apt-get -y install gtk2.0
sudo apt-get -y install python-glade2
sudo apt-get -y install python-nacl python-bcrypt
sudo pip install pycrypto
sudo pip install pyasn1
sudo pip install diskcache==4.1.0
sudo pip install asn1tools
sudo apt-get install -y python-pycurl
sudo apt-get install -y libcanberra-gtk-module
sudo pip install pycurl
sudo pip install requests
sudo pip install pygame
sudo bash CANVAS/installer/linux_installer.sh
sudo python CANVAS/runcanvas.py正确打开方式(使用方法)
①把Immunity Canvas 7.26文件夹内的所有文件复制到C:\ProgramData\0Day\CANVAS
(没有目录就建目录)

②安装Windows Dependency文件夹下的这两个文件
CANVAS_Dependency_Installer.exe
pycurl-7.43.0.win32-py2.7.msi

③安装pygame requests
pip install -U pygame --user
pip install requests④运行 canvas.bat,如果闪退直接运行 runcanvas.py

加载的时候耐心等一会就好了

注意事项
工具来源于国外论坛,安全性自测.
仅可用于授权的渗透测试,切勿用于违法犯罪.
为了你的安全,请将此类软件放虚拟机中运行.
转载请注明出处及链接.

解压码是错误的
试一下www.ddosi.com
how do i configure path??? to python?? please help 🙁
C:\Users\Administrator\AppData\Local\Programs\Python\Python310
rem Find what version of python is available, we use the highest available.
IF exist c:\Python27x\python.exe (
echo “Using Python 2.7 .bat setup….”
PATH=c:\Python27x\DLLs;C:\python27x\;!PATH!\\
python.exe -W ignore C:\ProgramData\0Day\Tools\CANVAS\runcanvas.py
this is from canvas.bat, the original and the immunity canvas depencies installed python 2.7 and it still wont work going into C:\Users\Administrator\AppData\Local\Programs\Python\Python310 in administrator theres no programs folder and in my user account there a programs folder but all thats inside is a commons folder and that it, this is becoming difficult lol hope you can help some more mister awesome 🙂
使用python27版本,然后canvas.bat里面设置路径
i know i am bothering you but what do i put to set the path? it seems set already because i installed python27, do i set it here? PATH=c:\Python27x\DLLs;C:\python27x\;!PATH!\\ if so what do i change and how lol im sorry
我给你发邮件吧
send the email to this email address i put down when making this comment 🙂 thank you for all your help 🙂
like dr.shivers asked i have a problem with immunity canvas on windows, how do i configure the python path? like step by step because google does not have anything about this, i have to use it on windows since immunity canvas this version does not work on kali linux which i cannot also install on kali linux please help me i will be really appreciative.
Set the Python path on the software
I know you can install the new version of canvas in new kali but is there any work around to install this version to kali? ive tried and things become broken big time no matter installing manually or not, is there any way?
I have a question master yu li, in widnows when starting canvas theres always an error about python not being in the path, i installed python but canvas wont open because its like its acting like python is not installed because of no path but i installed python, hope you can help, yet again you are the best.
Configure Paths
Ok 🙂 can you reupload? Secure Connection Failed when clicking download link, thank you yu li