目录导航
Pwn2Own简介
Pwn2Own是每年在 CanSecWest安全会议上举行的计算机黑客竞赛。2007 年 4 月在温哥华首次举办,现在每年举办两次,最近一次是在 2022 年5月。参赛者面临的挑战是利用广泛使用的软件和移动设备以前未知的漏洞。比赛的获胜者将获得他们开发的设备和现金奖励。Pwn2Own 竞赛旨在展示广泛使用的设备和软件的漏洞,同时还提供了自去年以来在安全方面取得的进展的检查点。
Pwn2Own Vancouver for 2022 比赛结果排名及详情
2022 年的 Pwn2Own Vancouver 正在进行中,比赛 15 周年纪念日已经见证了一些惊人的研究。请继续关注此博客以获取活动的更新结果、图片和视频。我们将在此处发布所有内容 – 包括最新的 Master of Pwn 排行榜。
以下是 Pwn 大师的当前排名:
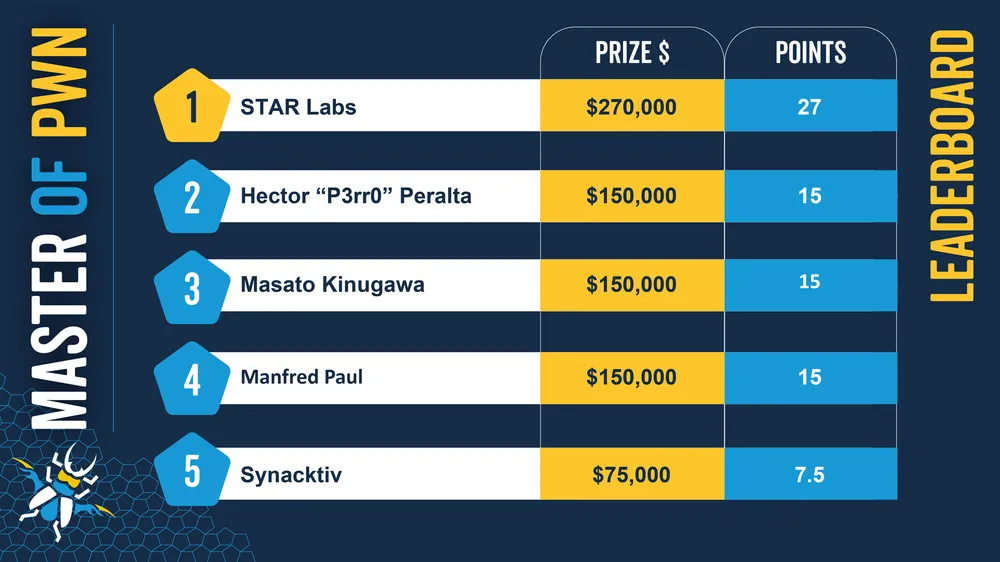
第一天 – 2022 年 5 月 18 日
成功– Hector “p3rr0” Peralta 能够针对 Microsoft Teams 展示不正确的配置。他获得了 150,000 美元和 15 个 Pwn 大师积分。
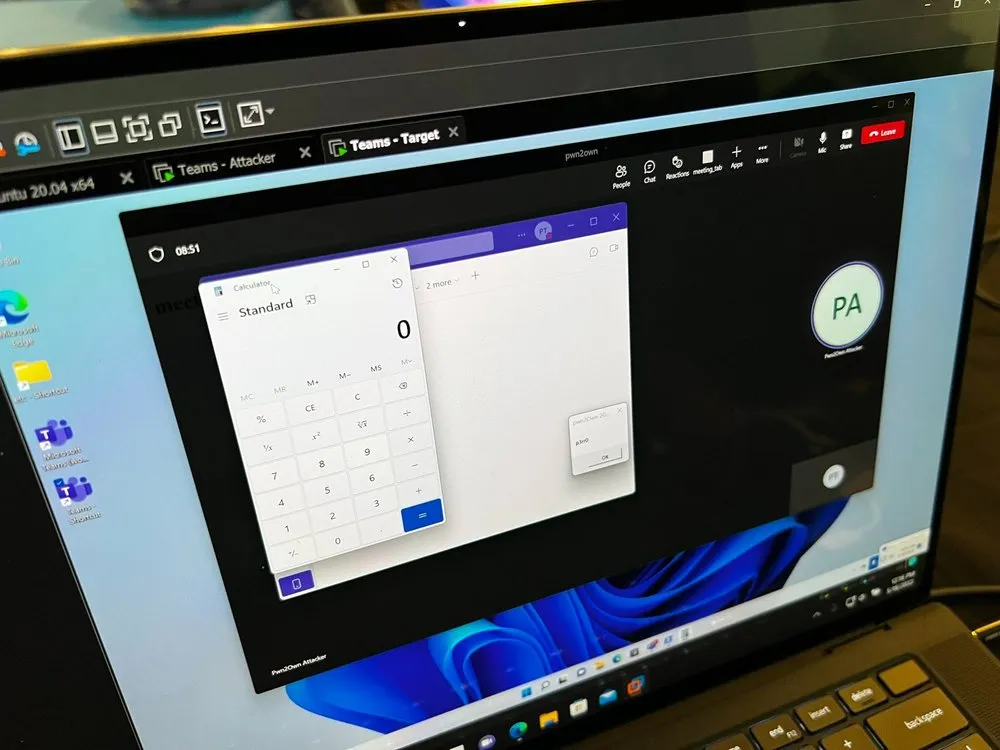
成功– STAR Labs 的 Billy Jheng Bing-Jhong ( @st424204 )、Muhammad Alifa Ramdhan ( @n0psledbyte ) 和 Nguyễn Hoàng Thạch ( @hi_im_d4rkn3ss ) 成功使用 OOB 读取和 OOB 写入在 Oracle Virtualbox 上实现升级。他们赚取 40,000 美元和 4 个 Pwn 大师积分。
成功– Masato Kinugawa 能够针对 Microsoft Teams 执行 3-bug 链的注入、错误配置和沙盒逃逸,获得 150,000 美元和 15 个 Pwn 大师积分。
成功– Manfred Paul ( @_manfp ) 在 Mozilla Firefox 上成功演示了 2 个错误 – 原型污染和不正确的输入验证,为他赢得了 100,000 美元和 10 个 Pwn 大师积分。

成功– Marcin Wiązowski 能够在 Microsoft Windows 11 上执行越界写入权限升级,获得 40,000 美元和 4 个 Pwn 大师积分,并获得 Microsoft 团队随附的白皮书的高度评价。
成功– Sea Security ( security.sea.com ) 的 Orca 团队能够在 Ubuntu 桌面上执行 2 个错误 – 一个越界写入 (OOBW) 和 Use-After-Free (UAF) – 获得 40,000 美元和 4 个 Master of Pwn 点。
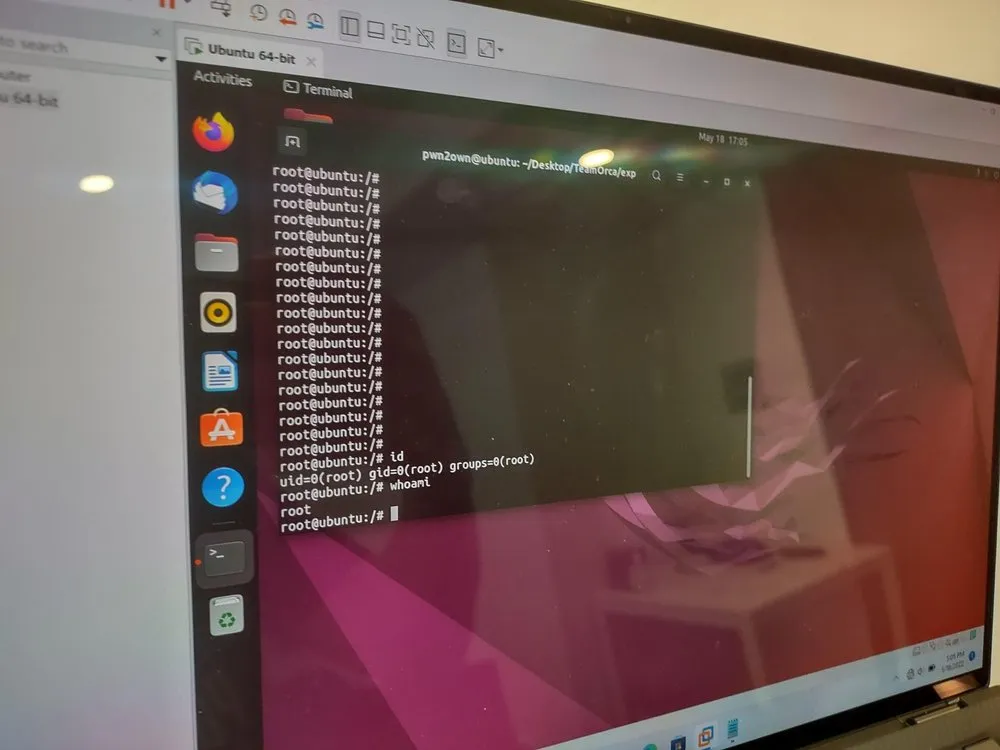
成功– STAR Labs 的 Daniel Lim Wee Soong ( @daniellimws )、Poh Jia Hao ( @Chocologicall )、Li Jiantao ( @CurseRed ) 和 Ngo Wei Lin ( @Creastery ) 成功展示了他们对 2 个漏洞(注入和任意漏洞)的零点击利用文件写入)在 Microsoft Teams 上。他们赚取 150,000 美元和 15 个 Pwn 大师积分。
成功– Manfred Paul ( @_manfp ) 在 Apple Safari 上通过带外写入成功赢得了他当天的第二场胜利,为他赢得了另外 50,000 美元和 5 个额外的 Master of Pwn 积分。
成功– Phan Thanh Duy( @PTDuy和 Lê Hữu Quang Linh( STAR Labs 的@linhlhq获得了 4 万美元和 4 个 Pwn 大师积分,以在 Microsoft Windows 11 上获得免费使用特权提升。
成功– Keith Yeo ( @kyeojy ) 在 Ubuntu 桌面上通过 Use-After-Free 漏洞获得了 4 万美元和 4 个 Pwn 大师积分。
第二天 – 2022 年 5 月 19 日
成功和 错误碰撞– 在当天的第一次尝试中,@Synacktiv 的 David BERARD 和 Vincent DEHORS能够在特斯拉 Model 3 信息娱乐系统上的已知沙盒逃生中展示 2 个独特的错误(双重免费和 OOBW)。他们赚了 75,000 美元和 7.5 Pwn 积分,虽然他们没有直接赢得这辆车,但他们已经赚到了足够的钱去自己买一辆!

从左到右:特斯拉的 2 位代表(站立和坐着)、ZDI 分析师 Michael DePlante、漏洞研究高级总监 (ZDI) Brian Gorenc、David BERARD 和 Synacktiv 的 Vincent DEHORS。
失败– 在第 2 天的第二次尝试中,namnp 无法在分配的时间内让他们的 Microsoft Windows 11 漏洞利用。
成功– Bien Pham ( @bienpnn ) 能够在 Unbuntu Desktop 上执行 Use After Free 错误,导致特权提升,获得 40,000 美元和 4 个 Master of Pwn 积分。
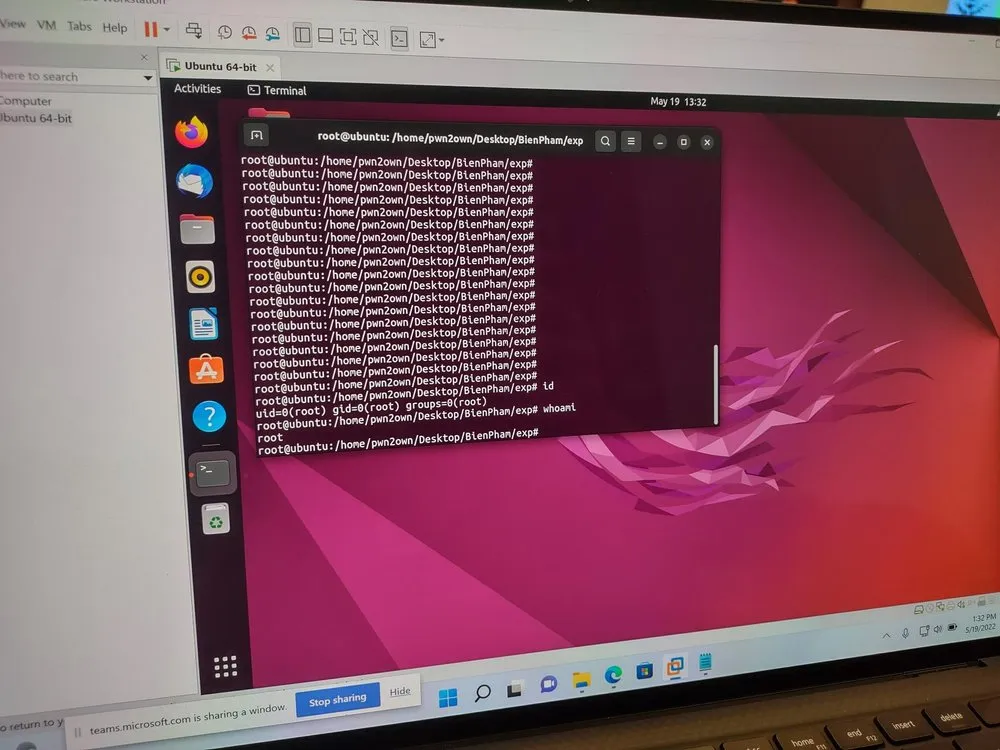
失败– @Jedar_LZ 无法在分配的时间内让特斯拉今天的第二次尝试工作。积极的一面是, @thedzi决定获取漏洞利用的详细信息并将其披露给特斯拉。
成功– T0 成功展示了导致 Microsoft Windows 11 权限提升的不正确访问控制错误 – 获得 40,000 美元和 4 个 Pwn 大师积分。
成功– 在第 2 天的最后一次尝试中,来自西北大学 TUTELARY 团队的 Jinpeng Lin (@Markak_)、Yueqi Chen (@Lewis_Chen_)和 Xinyu Xing (@xingxinyu)成功演示了Use After Free bug导致在Ubuntu 桌面提权。这为他赢得了 40,000 美元和 4 个 Master of Pwn 积分。

第三天 – 2022 年 5 月 20 日
失败– 在第 3 天的第一次尝试中,DoubleDragon 团队:Theori 的 Yonghwi Jin ( @jinmo123 ) 和 Enki 的 Yongjin Kim ( @adm1nkyj1 ) 无法在分配的时间内使用 Microsoft Teams。不过,一切并没有丢失,因为双龙团队能够对常规 ZDI 流程进行研究。
成功– 来自 Viettel Cyber Security 的 nghiadt12 能够通过 Microsoft Windows 11 上的 Integer Overflow 成功展示权限升级 – 赚取 40,000 美元和 4 个 Pwn 大师积分。
成功– Billy Jheng Bing-Jhong ( @st424204 ) STAR Labs 能够在 Ubuntu 桌面上成功演示 Use-After-Free 漏洞利用 – 又赚了 40,000 美元和 4 个 Pwn 大师积分。
成功– vinhthp1712 通过 Microsoft Windows 11 上的不当访问控制成功实现了特权提升。vinhthp1712 获得 40,000 美元和 4 个 Pwn 大师积分。
成功– 在比赛的最后一次尝试中,来自 REverse Tactics 的 Bruno PUJOS ( @brunopujos ) 在 Microsoft Windows 11 上通过 Use-After-Free 成功实现了特权提升。Bruno 获得了 40,000 美元和 4 个 Pwn 大师积分。
我们活动的常规节目安排到此结束!今年,我们共有来自 17 位参赛者的 21 次尝试,趋势科技和 ZDI 获得了 1,155,000 美元!我们迫不及待地想在不久的将来分享我们秋季活动的更多细节,敬请期待!
与往常一样,在Twitter 上关注我们以获取最新结果、更新和突发新闻。
再次感谢我们的合作伙伴 Tesla、Zoom 和 Microsoft 以及我们的赞助商 VMware。还要感谢参与的研究人员和供应商为比赛期间发现和报告的内容提供修复。提醒一下,供应商有 90 天的时间来修复所有披露的漏洞。
Pwn2Own Vancouver 2022 Rules(Pwn2Own温哥华2022比赛规则)[Google翻译版]
https://www.zerodayinitiative.com/Pwn2OwnVancouver2022Rules.html
PWN2OWN™ 竞赛(“竞赛”)完全按照适用法律进行,并应根据适用法律进行解释和评估。在法律禁止的情况下,本次比赛全部或部分无效。参加本次比赛即表示接受这些比赛规则(“比赛规则”)。趋势科技股份有限公司(“趋势科技”)是本次比赛的赞助商(“赞助商”)。
1. 资格。
Trend Micro Incorporated、Microsoft Corporation、Tesla Inc.、Zoom Video Communication, Inc. 和 VMware Inc. 及其各自的关联公司、子公司、相关公司、广告和促销机构的员工以及上述任何一方的家庭成员不属于有资格参加比赛。本次比赛在法律禁止的情况下无效。
参赛者必须在注册时达到其所在国家、省或居住州的成年年龄才能参加,并且不得是任何美国禁运或制裁国家/地区的居民,或以其他方式在任何美国被拒绝或禁止人员名单。参加者为比赛目的携带或导致转移到比赛举办国(“比赛地点”)的任何软件或技术可能受参加者居住国或旅行来源国的出口管制或受比赛地点的进出口要求。参加者有责任因参加比赛而遵守任何适用的进出口管制。
赞助商有权随时要求提供身份证明和/或参加比赛的资格。未能提供此类证明可能会导致取消资格。为竞赛目的而由主办方要求并提供给主办方的所有个人信息和其他信息必须真实、完整、准确且绝不具有误导性。如果参赛者在任何阶段提供不真实、不完整、不准确或误导性的个人详细信息和/或信息,主办方保留自行决定取消参赛者资格的权利。
如果您是公共部门的员工,那么您必须验证道德准则、法律和/或法规,这些道德准则、法律和/或法规管理您从与您开展业务的公司接受贵重物品的能力。在参加比赛和/或从赞助商处接受任何有价值的物品之前,请获得您所在组织的必要批准。此外,公共部门员工、K-12 公立和私立教育机构的员工以及所有图书馆,包括公立、私立学校、学院或大学、研究机构和私立图书馆,只有在您在您的官方身份,而不是您在这些实体工作的一部分。
2. 比赛期间。
比赛将于 2022 年 5 月 18日 至 20日在 CanSecWest 2022 会议期间举行。
3. 如何进入。
本次比赛对 CanSecWest 2022 会议的所有注册者和非注册者开放,但须符合此处的资格要求。参加比赛无需购买。
参赛者可以通过发送电子邮件至 [email protected] 联系赞助商并指明参赛者希望参加的类别来注册比赛。
所有参赛者必须注册零日倡议™(“ZDI”)研究人员帐户才能参与。
参赛者可以为给定类别注册多个条目,但每个条目必须针对该类别中的不同目标(有关类别、目标和奖品,请参见下文第 4 节)。参赛者每个目标只能注册一次。 每个条目都必须是一个单独且唯一的漏洞利用链。有关目标(软件、版本、配置、芯片组等)的具体细节将在注册过程中传达给参赛者。 如果参赛者代表一家公司,参赛者必须在注册过程中确定他们代表的是哪家公司。每家公司仅限于一次注册。每位参赛者只能以个人、团队或公司的身份注册一次。
主办方保留在注册过程中拒绝对不符合规则的参赛作品进行注册的权利。比赛报名截止时间为2022年 5 月 12日太平洋时间下午 5:00 。
4. 奖品。
趋势科技在针对以下类别中列出的目标的漏洞和利用技术竞赛期间提供现金和奖品。第一个成功攻破所选类别中的目标的参赛者将赢得为该特定目标指定的奖金金额。所有奖品均以美元计算。
比赛分为七个类别,包括:
- 虚拟化
- 网页浏览器
- 企业应用
- 服务器
- 本地权限提升
- 企业通信
- 汽车
每个类别都有一组目标,参赛者可以在注册过程中选择。
如果参赛者的尝试成功,它可能有资格获得附加奖金。此附加奖金可带来额外的金钱奖励和 Pwn 大师积分。参赛者必须在注册过程中确定他们正在尝试的附加奖金。只要尝试在没有附加组件的情况下满足原始类别的要求,就可以在尝试期间移除附加组件奖励。如果在尝试期间移除了附加奖励,这将影响潜在的 Pwn 积分奖励,如下面的 Pwn 大师部分所定义。各种附加奖金的资格要求记录在下面的每个类别中。
虚拟化类别
此类尝试必须从客户操作系统内启动,并在主机操作系统或管理程序中执行任意代码。
目标:
目标 | 奖 | Pwn 积分大师 | 有资格获得附加奖 |
甲骨文虚拟机 | $40,000 | 4 | 是的 |
VMware工作站 | $75,000 | 8 | 是的 |
VMware ESXi | $150,000 | 15 | 不 |
微软 Hyper-V 客户端 | $250,000 | 25 | 是的 |
对于 Oracle VirtualBox、VMware Workstation 和 Microsoft Hyper-V Client,来宾和主机操作系统都将运行 Microsoft Windows 11 21H2 x64。对于 VMware ESXi,来宾操作系统将运行 Microsoft Windows 11 21H2 x64。某些可选组件,例如 RemoteFX、旧版网络适配器(第 1 代)和光纤通道适配器,不被视为默认组件,将超出 Microsoft Hyper-V 客户端目标的范围。
可用的附加奖品:
附加奖 | 奖 | Pwn 积分大师 |
利用主机操作系统上的 Windows 内核漏洞提升权限。 | $50,000 | 5 |
要获得此附加奖,用于提升主机操作系统权限的内核漏洞必须不同于逃避虚拟化目标所需的任何内核漏洞。
网络浏览器类别
必须从被测目标发起此类尝试。例如,不允许从命令行启动被测目标。在此类别中,基于 Windows 的目标将在 VMware Workstation 虚拟机中运行。
目标:
目标 | 逃生选项 | 奖 | Pwn 积分大师 | 有资格获得 VMware Escape 附加奖 | 有资格获得双击附加奖 |
谷歌浏览器 | N/A – 仅渲染器 | $50,000 | 5 | 不 | 是的 |
Windows 内核权限提升 | $100,000 | 10 | 是的 | 是的 | |
沙盒逃生 | $150,000 | 15 | 是的 | 是的 | |
微软边缘(铬) | N/A – 仅渲染器 | $50,000 | 5 | 不 | 是的 |
Windows 内核权限提升 | $100,000 | 10 | 是的 | 是的 | |
沙盒逃生 | $150,000 | 15 | 是的 | 是的 | |
苹果浏览器 | N/A – 仅渲染器 | $50,000 | 5 | 不 | 不 |
Sandbox Escape 或 macOS 内核提权 | $100,000 | 10 | 不 | 不 | |
火狐浏览器 | N/A – 仅渲染器 | $50,000 | 5 | 不 | 不 |
沙盒逃逸或 Windows 内核权限提升 | $100,000 | 10 | 是的 | 不 |
可用的附加奖品:
附加奖品类型
| 附加奖 | 奖 | Pwn 积分大师 |
VMware Escape 附加组件 | 通过转义 VMware Workstation 虚拟机在主机操作系统上执行代码。 | $75,000 | 8 |
双击插件 | 单项必须在 Google Chrome 和 Microsoft Edge (Chromium) 上成功获得任意代码执行 | $25,000 | 3 |
参赛者只能在比赛中注册一次 Double-Tap Add-on 奖品。
企业应用类别
必须从被测目标发起此类尝试。例如,不允许从命令行启动被测目标。
目标:
目标 | 逃生选项 | 奖 | Pwn 积分大师 |
Adobe 阅读器 | 沙盒逃逸或 Windows 内核权限提升 | $50,000 | 5 |
Microsoft Office 365 专业增强版(Word/Excel/PowerPoint) | 不适用 | $100,000 | 10 |
Office 目标将在 Windows 11 x64 上运行 Microsoft Office 365 ProPlus x64(每月频道)。要为您的测试下载和配置它,请使用Microsoft 网站上提供的说明。要验证您是否在月度频道上,请检查文件->帐户,您将在内部版本号下看到频道配置。可从 https://products.office.com/en-us/try获得试用版。
基于 Microsoft Office 的目标将启用受保护的视图。Adobe Reader 将启用保护模式。
服务器类别
此类别的尝试必须从参赛者的笔记本电脑在比赛网络中启动。
目标:
目标 | 奖 | Pwn 积分大师 |
微软视窗 RDP/RDS | $200,000 | 20 |
微软交换 | $200,000 | 20 |
微软 SharePoint | $100,000 | 10 |
桑巴 | $75, 000 | 8 |
本地特权升级类别
必须从非管理员和非 root 帐户的被测目标内启动此类别的尝试。在此类别中,条目必须利用内核漏洞来提升权限。
目标:
目标 | 奖 | Pwn 积分大师 |
Ubuntu 桌面 | $40,000 | 4 |
微软视窗 11 | $40,000 | 4 |
企业通讯类
尝试必须通过与参赛者通信来破坏目标应用程序。示例通信请求可以是音频呼叫、视频会议、消息等。
目标:
目标 | 奖 | Pwn 积分大师 |
飞涨 | $150,000 | 15 |
微软团队 | $150,000 | 15 |
汽车类
此类尝试必须针对被测目标、Tesla Model 3 (基于 Intel 或 Ryzen)、Tesla Model S(基于 Ryzen)或等效的台式设备。根据所需条目的复杂性,此类别包含不同层级的目标。每个等级都有不同的要求,并有资格获得不同的奖品包。第 1 层目标代表最困难的参赛作品,要求参赛者在车辆中的三个不同子系统上执行任意代码。第 2 层目标要求参赛者在车辆中的两个不同子系统上执行任意代码,第 3 层目标专注于测试各个子系统。
一级目标:
目标 | 奖金金额 | Pwn 积分大师 | 额外的 奖 选项 | 合格 | ||
初始向量 | 中间 | 最后阶段 | ||||
调谐器, 无线上网, 蓝牙, 或调制解调器 | 信息娱乐 | 证监会, 网关, 或自动驾驶仪
|
500,000 美元
|
50
| 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 是的 | |||||
Autopilot Root Persistence 附加组件 | 是的 | |||||
CAN 总线插件 | 不 | |||||
第 2 层目标:
目标 | 奖金金额 | Pwn 积分大师 | 额外的 奖 选项 | 合格 | |
初始向量 | 最后阶段 | ||||
调谐器, 无线上网, 蓝牙, 或调制解调器 | 信息娱乐 | 250,000 美元 | 25 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
信息娱乐 | 证监会, 网关, 或自动驾驶仪 | 300,000 美元 | 30 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 是的 | ||||
CAN 总线插件 | 不 | ||||
调谐器, 无线上网, 蓝牙, 或调制解调器 | 证监会, 网关, 或自动驾驶仪 | 400,000 美元 | 40 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 是的 | ||||
CAN 总线插件 | 不 | ||||
第 3 层目标:
目标 | 奖金金额 | Pwn 积分大师 | 额外 选项 | 合格 | |
初始向量 | 选项 | ||||
调制解调器或调谐器 | 不适用 | 60,000 美元 | 6 | 车辆奖 | 不 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
无线上网 或蓝牙 | 不适用 | 60,000 美元 | 6 | 车辆奖 | 不 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
信息娱乐 | 不适用 | 35,000 美元 | 3.5 | 车辆奖 | 不 |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
诊断以太网 | 25,000 美元 | 2.5 | 车辆奖 | 不 | |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
基于 USB 的攻击 | 35,000 美元 | 3.5 | 车辆奖 | 不 | |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
沙盒逃生 | 100,000 美元 | 10 | 车辆奖 | 不 | |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
不受限制的根/内核 特权升级 | 150,000 美元 | 15 | 车辆奖 | 不 | |
信息娱乐根持久性附加组件 | 是的 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 是的 | ||||
证监会, 网关, 或自动驾驶仪 | 不适用 | 200,000 美元 | 20 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 是的 | ||||
CAN 总线插件 | 不 | ||||
自动驾驶仪和网关(仅限以太网攻击面) | 不适用 | 100,000 美元 | 10 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 是的 | ||||
CAN 总线插件 | 不 | ||||
自动驾驶仪 拒绝服务 | 不适用 | 50,000 美元 | 5 | 车辆奖 | 不 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 不 | ||||
钥匙扣 或电话即钥匙 | 不适用 | 100,000 美元 | 10 | 车辆奖 | 是的 |
信息娱乐根持久性附加组件 | 不 | ||||
Autopilot Root Persistence 附加组件 | 不 | ||||
CAN 总线插件 | 不 | ||||
· 针对“调制解调器或调谐器”、“Wi-Fi 或蓝牙”以及“网关、自动驾驶仪或 VCSEC”目标(或包含这些作为初始向量的目标)的条目必须通过与恶意基站或其他恶意实体。
· 针对“信息娱乐”目标(或包含信息娱乐作为初始向量的目标)的条目必须从被测目标启动,并且必须通过浏览恶意内容来实现代码执行。在第 1 层和第 2 层中,不允许对“信息娱乐”系统进行中间浏览器攻击。
· 任何利用内置浏览器漏洞的“信息娱乐”条目都必须与沙箱转义或根/内核权限升级链接。沙箱逃逸必须导致代码在浏览器遏制措施之外执行,而不仅仅是 Chromium 沙箱。
· “信息娱乐”类别中基于 USB 的攻击必须针对乘客经常插入的 USB 端口,该端口公开暴露在中控台或手套箱上。任何其他暴露的 USB 端口都不在此目标的范围内。
·如果参赛作品针对的是公开的 Odin 和更新服务以外的服务,则“信息娱乐”类别中针对诊断以太网攻击的参赛作品有资格获得额外的 10,000 美元奖金。
· 针对需要物理访问诊断以太网或 USB 的 Odin 和更新服务的条目没有资格获得 Unconfined Root/Kernel Escalation of Privilege 奖。
· 针对“Key Fobs 或 Phone-as-Key”目标的条目必须实现代码执行、任意车辆解锁或任意车辆启动使用与协议相关的弱点。不允许输入与 Key Fob 中继、Key Fob 克隆或 Rolljam 攻击相关的条目。输入必须在没有 Key Fob 的情况下成功。
· 除非另有说明,否则需要物理访问的条目超出范围。
可用的附加奖品:
附加奖品类型 | 附加奖 | 奖 | Pwn 积分大师 |
信息娱乐根持久性 | 条目的有效负载必须在重新启动后在信息娱乐目标上保持根持久性。 | $50,000 | 5 |
自动驾驶 Root Persistence | 条目的有效负载必须在重新启动后在 Autopilot 目标上保持根持久性。 | $50,000 | 5 |
CAN总线 | 条目的有效负载必须展示对任何物理 CAN 总线的任意控制。 | $100,000 | 10 |
除奖金外,该类别中符合条件的目标的第一轮获胜者将赢得特斯拉 Model 3 或类似车辆(建议零售价 44,990 美元(美元))(“特斯拉奖”)。如果参赛作品的目标是特斯拉 Model S(基于 Ryzen),特斯拉奖将是特斯拉 Model 3。车辆中不包含其他选项。如果因任何原因无法获得特斯拉奖,赞助商可以将特斯拉奖替换为 (1) 同等价值的替代特斯拉车辆,或 (2) 相当于特斯拉奖当前价值的金额,以美元支付,金额为赞助商的自由裁量权。
Pwn大师
比赛结束时总分最高的选手(“Master of Pwn”)将获得 65,000 ZDI 奖励积分(估计为 25,000 美元(美元))。总分是根据上表中分配的 Pwn 大师积分,通过成功参赛的总和计算得出的。
例如,如果参赛者有两个成功的条目(带有 Sandbox Escape 的 Microsoft Edge (Chromium) 和带有与 VMware Workstation 逃脱插件链接的 Sandbox Escape 的 Google Chrome)将是 38 Master of Pwn 积分。如果两名或更多参赛者在比赛结束时获得相同数量的积分,则每位参赛者将获得 65,000 ZDI 奖励积分(估计为 25,000 美元(美元))。
如果参赛者在尝试期间决定移除附加奖励,则该附加奖励的 Pwn 大师积分将从该尝试的最终总积分中扣除。如果参赛者在比赛开始后决定退出已注册的尝试,则该尝试的 Pwn 大师积分将除以 2 并从参赛者的比赛总积分中扣除。
除非第 4 节中的类别说明中另有说明,否则特定类别的第一轮获胜者将除了赢得奖金外,还将赢得一台笔记本电脑(估计价值 1,000 美元)。这些奖品的获胜者无权获得差价,如果有的话,介于实际奖品价值和估计奖品价值之间。预计奖品价值以本竞赛规则印刷之日为准。
一个类别可能没有赢家。如果某个类别没有获胜者,赞助商可以自行决定使用该类别的奖金在上述另一个类别中提供额外的奖品,该奖品可能等于或低于该类别的初始奖品。类别。获胜的几率取决于一个类别中符合条件的参与者的数量以及满足此基于技能的竞赛要求的能力。奖品将在每位获奖者满足此处规定的要求后八 (8) 周内分发。
奖品必须按已颁发的形式接受,不得转让、分配、替换或兑换现金,除非主办方自行决定。奖品的任何未使用部分将被没收且没有现金价值。如果由于任何原因无法颁发奖品(或其任何部分),主办方保留自行决定以同等或更高价值的奖品替换的权利。奖品税(如有)由获奖者自行承担。
如果在竞赛规则发布和竞赛之间发布、强化、更新或召回其中一个目标或设备的新版本,主办方保留自行决定添加或修改类别的权利。
主办方不对任何遗失或错配的奖品承担任何责任。
5. 获胜者选择。
如果超过一个参赛者注册一个给定的类别,参赛者的顺序将随机抽取。根据参赛者的顺序,第一个参赛者将有机会尝试破坏选定的目标。如果不成功,将给予下一位随机抽取的参赛者机会。这将一直持续到参赛者成功攻破目标为止。第一个成功攻破选定目标的参赛者将赢得该类别中该目标的奖金。目标被攻破后,该类别的比赛结束,没有其他参赛者将参加该类别的比赛(除非赞助商提供了额外的获胜者选项,如果适用,该选项将在比赛中公布)。
成功的入口必须利用漏洞来修改程序或进程的标准执行路径,以允许执行任意指令。该条目需要击败旨在确保安全执行代码的目标技术,例如但不限于数据执行保护 (DEP)、地址空间布局随机化 (ASLR) 和/或应用程序沙盒。2022 年竞赛的目标将不会为控制流强制技术 (CET) 缓解提供硬件支持。如果存在沙盒,则需要完整的沙盒转义,除非在第 4 节的类别描述中另有说明。生成的有效负载应在提升的上下文中执行(例如,在基于 Windows 的目标上,中等完整性级别或更高级别)。
参赛者最多可以尝试三 (3) 次成功。三 (3) 次尝试中的每一次都将单独限制在五 (5) 分钟的时间段内。一次尝试被视为成功,尝试的所有元素必须在 5 分钟窗口内完成。所有三 (3) 次尝试必须在三十 (30) 分钟内完成,不包括在尝试前设置设备所需的时间。尽管有上述规定,如果参赛者在尝试期间遇到因无法访问或不可用的网络、服务器、互联网服务提供商或参赛者或主办方无法控制的其他连接而导致的任何连接问题,主办方可酌情延长参赛者的时间。 .
除了启动尝试所需的操作之外,针对这些目标的成功进入必须不需要用户交互,并且必须在用户会话中发生,无需重新启动或注销/登录。例如,必须与对话框交互才能成功完成漏洞利用或将恶意文件写入 Startup 文件夹是不允许的。
条目中使用的初始漏洞必须在已注册的目标中。条目中使用的沙箱转义必须在注册的目标中(除非条目利用内核权限提升)。给定的漏洞只能在所有类别中使用一次。攻击中使用的漏洞必须是未知的、未发布的或之前未向供应商或赞助商报告的。如果参赛作品利用了先前已知的漏洞,如供应商或赞助商所证明,赞助商可以自行决定选择接受参赛作品并以低于初始奖品提供的价值提供奖品给定的类别。
如果存在身份验证,则漏洞利用必须在对服务进行身份验证之前发生,或者包括绕过身份验证。如果参赛作品需要中间人攻击,赞助商可以自行决定接受参赛作品并以低于给定类别初始奖品的价值提供奖品. 参赛者可以在比赛之前联系赞助商,以确定需要此类技术的提议参赛作品的奖品资格。
除非在第 4 节的类别描述中另有说明,否则目标将在所选目标(Microsoft Windows 11 21H2 x64、Apple macOS Monterey 和 Ubuntu 22.04 for Desktop)上可用的最新、完全修补的操作系统版本上运行。所有目标将是 64 位(如果可用),并以默认配置安装。
赞助商保留自行决定什么是成功参赛的权利。如果赞助商认为该部分漏洞利用链未能满足要求,赞助商可以自行决定接受参赛作品并以低于给定类别的初始奖品的价值提供奖品上述规则。例如,如果该条目包含先前已知的漏洞,并且供应商尚未发布补丁,则赞助商可能会接受该条目并以低于给定类别的初始奖品的价值提供奖品.
在成功演示漏洞利用后,参赛者将向赞助商提供功能齐全的漏洞利用以及解释参赛作品中使用的漏洞和利用技术的白皮书。在利用多个漏洞来获得代码执行的情况下,必须提供有关所有漏洞(内存损坏、信息泄漏、升级等)的详细信息以及使用它们的顺序才能获得奖品。竞赛获胜者披露的漏洞和利用技术将向受影响的供应商披露,并且根据ZDI 研究人员协议,利用和白皮书将成为赞助商的财产 。
6. 参赛者的赔偿。
通过参加比赛,参赛者免除并让赞助商免于对参赛者或任何其他人造成的任何伤害、损失或损害(包括人身伤害、死亡或财产损失)承担任何和所有责任,从而导致全部或直接或间接地因接受、拥有、使用或滥用任何奖品、参与比赛、违反比赛规则或参与任何与奖品相关的活动而直接或间接承担责任。参赛者同意全额赔偿赞助商免受第三方与比赛有关的任何和所有索赔,但不限于此。
7. 责任限制。
参赛者承认并同意,主办方对可能发生的任何计算机、在线、软件、电话、硬件或技术故障不承担任何责任或义务。主办方不对任何不正确或不准确的信息负责,无论是由网站用户或与比赛相关或在比赛中使用的任何设备或程序或比赛管理中可能发生的任何技术或人为错误造成的。主办方不对任何电话网络或线路、计算机在线系统、服务器、提供商、计算机设备、软件、电子邮件、播放器或浏览器因技术问题或流量而导致的任何问题、故障或技术故障负责互联网上、任何网站上的拥塞,或由于上述原因的任何组合。主办方不对参赛者或任何与参与或下载本次比赛材料相关或导致的计算机造成的任何伤害或损害负责。参赛者对因参加比赛或因接受、拥有、使用或未能获得任何奖品而造成或声称造成的伤害承担责任。如果由于任何原因(包括主办方无法控制的原因,例如计算机病毒感染、漏洞、篡改、未经授权的干预、欺诈、技术故障)导致比赛无法按计划进行,主办方不承担任何责任或义务,或对本次比赛的管理、安全、公平、诚信、自然灾害或适当进行的腐败。
8. 行为。
作为参加比赛的条件,每位参赛者同意受这些比赛规则的约束,并在注册过程中表示同意。参赛者进一步同意受主办方决定的约束,该决定在所有方面都是最终决定并具有约束力。主办方保留自行决定取消任何被发现有以下情况的参赛者参赛资格的权利: (a) 违反比赛规则;(b) 篡改或试图篡改比赛或任何设备、比赛网站或比赛节目;(c) 以不符合体育道德或破坏性的方式行事,干扰比赛的任何部分;或 (d) 从事任何形式的骚扰、冒犯、歧视或威胁性言论或行为,包括(但不限于)与种族、性别、性别认同和表达、国籍有关的言论或行为,宗教、残疾、婚姻状况、年龄、性取向、军人或退伍军人身份或其他受保护类别。注意:任何故意破坏比赛合法运作的企图都可能违反刑法和民法。如果做出这样的尝试,赞助商保留在法律允许的最大范围内寻求补救和损害赔偿的权利,包括但不限于刑事起诉。
9. 隐私/个人信息的使用。
通过参加比赛,参赛者:(i) 授予赞助商使用他/她的姓名、肖像、邮寄地址、电话号码和电子邮件地址(“个人信息”)来管理比赛的权利,包括但不限于联系和公布获奖者;(ii) 承认赞助商可能会就上述 (i) 中列出的任何活动向赞助商的第三方代理和服务提供商披露其个人信息。
赞助商将仅将参赛者的个人信息用于确定的目的,并以符合赞助商隐私政策的方式保护参赛者的个人信息: trendmicro.com/privacy
10. 知识产权。
所有知识产权,包括但不限于商标、商号、徽标、版权、设计、宣传材料、网页、源代码、图纸、插图、标语和陈述,均归赞助商和/或其关联公司所有。保留所有权利。未经所有者明确书面同意,严禁未经授权复制或使用任何受版权保护的材料或知识产权。
11. 终止。
主办方保留自行决定以任何方式、在任何时间、以任何理由终止全部或部分竞赛和/或修改、修改或暂停竞赛和/或竞赛规则的权利恕不另行通知。
12. 法律。
这些是官方的比赛规则。比赛受适用的法律和法规的约束。为了遵守任何适用法律或对赞助商和/或比赛有管辖权的任何其他实体的政策,比赛规则如有更改,恕不另行通知。所有有关竞赛规则的解释、有效性、解释和可执行性或参赛者与赞助商之间与竞赛有关的权利和义务的问题和问题均应受所在国法律管辖并按其解释。德克萨斯州包括程序规定,但不影响任何法律选择或可能导致适用任何其他司法管辖区法律的法律冲突规则或规定。
13. 优先级。
如果竞赛规则的条款和条件与任何竞赛相关材料中包含的披露或其他声明之间存在任何差异或不一致,则以竞赛规则的条款和条件为准,管辖和控制。
© 2022 趋势科技公司。版权所有。PWN2OWN、ZERO DAY INITIATIVE、ZDI 和 Trend Micro 是 Trend Micro Incorporated 的商标或注册商标。所有其他商标和商品名称均为其各自所有者的财产。
Pwn2Own Vancouver 2022 Rules(Pwn2Own温哥华2022比赛规则)[英文原版]
THE PWN2OWN™ CONTEST ("CONTEST") IS CONDUCTED SOLELY IN ACCORDANCE WITH AND SHALL BE CONSTRUED AND EVALUATED ACCORDING TO APPLICABLE LAW. THE CONTEST IS VOID IN WHOLE OR PART WHERE PROHIBITED BY LAW. ENTRY IN THIS CONTEST CONSTITUTES ACCEPTANCE OF THESE CONTEST RULES (THE "CONTEST RULES"). TREND MICRO INCORPORATED ("TREND MICRO") IS THE SPONSOR OF THIS CONTEST ("SPONSOR").
1. ELIGIBILITY.
Employees of Trend Micro Incorporated, Microsoft Corporation, Tesla Inc., Zoom Video Communication, Inc., and VMware Inc. and their respective affiliates, subsidiaries, related companies, advertising and promotional agencies, and the household members of any of the above are not eligible to participate in the Contest. This Contest is void where prohibited by law.
Contestants must be at the age of majority in their country, province or state of residence at the time of registration in order to participate and may not be a resident of any United States embargoed or sanctioned country or otherwise be listed on any United States denied or barred persons list. Any software or technology that attendees bring or cause to be transferred for purposes of the Contest to the country in which the Contest is held (“Contest Location”) may be subject to the export controls of attendee’s country of residence or travel origin or subject to the import and export requirements of the Contest Location. Attendees are responsible for compliance with any applicable import and export controls as a result of their attendance at the Contest.
Sponsor shall have the right at any time to require proof of identity and/or eligibility to participate in the Contest. Failure to provide such proof may result in disqualification. All personal and other information requested by and supplied to the Sponsor for the purpose of the Contest must be truthful, complete, accurate, and in no way misleading. The Sponsor reserves the right, in its sole discretion, to disqualify any contestant should such contestant at any stage supply untruthful, incomplete, inaccurate, or misleading personal details and/or information.
If you are a public sector employee, it is critical that you verify the ethics code, laws, and/or regulations that govern your ability to accept items of value from companies with whom you conduct business. Please obtain the necessary approval from your organization before participating in the Contest and/or accepting any item of value from Sponsor. In addition, public-sector employees, employees of K-12 public and private education institutions and all libraries, including public, private school, college or university, research, and private libraries can participate in the Contest only if you are doing so outside of your official status and not as part of your employment with those entities.
2. CONTEST PERIOD.
The Contest will be held May 18th – 20th, 2022, during the CanSecWest 2022 Conference.
3. HOW TO ENTER.
This Contest is open to all registrants and non-registrants of the CanSecWest 2022 Conference, subject to the eligibility requirements herein. No purchase is required to participate in the Contest.
The contestant can register for the contest by contacting Sponsor via e-mail at [email protected] and indicating in which categories the contestant wishes to participate.
All contestants must sign up for a Zero Day Initiative™ ("ZDI") Researcher account in order to participate.
The contestant can register multiple entries for a given category but each entry must be for a different target in that category (See Section 4 below for categories, targets, and prizes). The contestant can only register once per target. Every entry must be a separate and unique exploit chain. Specific details about the targets (software, versions, configurations, chipsets, etc.) will be communicated to contestants during the registration process. If the contestant is representing a company, the contestant must identify which company they are representing during the registration process. Each company is limited to one registration. Each contestant may only register once as either an individual, a team or company.
The Sponsor reserves the right to deny registration to entries that do not comply with the rules during the registration process. Contest registration closes at 5:00 p.m. Pacific Time on May 12th, 2022.
4. PRIZES.
Trend Micro is offering cash and prizes during the competition for vulnerabilities and exploitation techniques against the listed targets in the below categories. The first contestant to successfully compromise a target within the selected category will win the prize amount indicated for that specific target. All prizes are in US currency.
The contest has seven categories consisting of:
- Virtualization
- Web Browser
- Enterprise Applications
- Server
- Local Escalation of Privilege
- Enterprise Communications
- Automotive
Each category has a set of targets that can be selected by the contestant during the registration process.
If the contestant’s attempt is successful, it might be eligible for an Add-on Bonus. This Add-on Bonus results in additional monetary prizes and Master of Pwn points. The contestant must identify which Add-on Bonus they are attempting during the registration process. It is possible to remove the Add-on bonuses during the attempt as long as the attempt meets the requirements of the original category without the Add-ons. If the Add-on bonus is removed during the attempt, this will impact the potential Master of Pwn points award as defined the Master of Pwn section below. The eligibility requirements for the various Add-on Bonuses are documented in each category below.
Virtualization Category
An attempt in this category must be launched from within the guest operating system and execute arbitrary code on the host operating system or in the hypervisor.
Targets:
Target | Prize | Master of Pwn Points | Eligible for Add-on Prize |
Oracle VirtualBox | $40,000 | 4 | Yes |
VMware Workstation | $75,000 | 8 | Yes |
VMware ESXi | $150,000 | 15 | No |
Microsoft Hyper-V Client | $250,000 | 25 | Yes |
For Oracle VirtualBox, VMware Workstation, and Microsoft Hyper-V Client, both the guest and the host operating system will be running Microsoft Windows 11 21H2 x64. For VMware ESXi, the guest operating system will be running Microsoft Windows 11 21H2 x64. Certain optional components, such as RemoteFX, Legacy Network Adapter (Generation 1), and Fibre Channel Adapter, are not considered default and will be out of scope for the Microsoft Hyper-V Client target.
Available Add-on Prizes:
Add-on Prize | Prize | Master of Pwn Points |
Escalation of privilege leveraging a Windows kernel vulnerability on the host operating system. | $50,000 | 5 |
To be eligible for this add-on prize, the kernel vulnerability used to escalate privilege on the host operating system must be different from any kernel vulnerability required to escape the virtualization target.
Web Browser Category
An attempt in this category must be launched from the target under test. For example, launching the target under test from the command line is not allowed. In this category, the Windows-based targets will be running in a VMware Workstation virtual machine.
Targets:
Target | Escape Options | Prize | Master of Pwn Points | Eligible for VMware Escape Add-on Prize | Eligible for Double Tap Add-on Prize |
Google Chrome | N/A – Renderer Only | $50,000 | 5 | No | Yes |
Windows Kernel Escalation of Privilege | $100,000 | 10 | Yes | Yes | |
Sandbox Escape | $150,000 | 15 | Yes | Yes | |
Microsoft Edge (Chromium) | N/A – Renderer Only | $50,000 | 5 | No | Yes |
Windows Kernel Escalation of Privilege | $100,000 | 10 | Yes | Yes | |
Sandbox Escape | $150,000 | 15 | Yes | Yes | |
Apple Safari | N/A – Renderer Only | $50,000 | 5 | No | No |
Sandbox Escape or macOS Kernel Escalation of Privilege | $100,000 | 10 | No | No | |
Mozilla Firefox | N/A – Renderer Only | $50,000 | 5 | No | No |
Sandbox Escape or Windows Kernel Escalation of Privilege | $100,000 | 10 | Yes | No |
Available Add-on Prizes:
Add-on Prize Type
| Add-on Prize | Prize | Master of Pwn Points |
VMware Escape Add-on | Execute code on the host operating system by escaping the VMware Workstation virtual machine. | $75,000 | 8 |
Double Tap Add-on | Single entry must successfully gain arbitrary code execution on Google Chrome and Microsoft Edge (Chromium) | $25,000 | 3 |
Contestants are only eligible to register once for the Double-Tap Add-on prize in the contest.
Enterprise Applications Category
An attempt in this category must be launched from the target under test. For example, launching the target under test from the command line is not allowed.
Targets:
Target | Escape Option | Prize | Master of Pwn Points |
Adobe Reader | Sandbox Escape or Windows Kernel Escalation of Privilege | $50,000 | 5 |
Microsoft Office 365 ProPlus (Word/Excel/PowerPoint) | N/A | $100,000 | 10 |
The Office targets will be running Microsoft Office 365 ProPlus x64 (Monthly Channel) on Windows 11 x64. To download and configure this for your testing, please use the directions available on Microsoft’s web site. To verify you are on Monthly Channel, check under File->Account and you will see the channel configuration under the build number. A trial is available from https://products.office.com/en-us/try.
Microsoft Office-based targets will have Protected View enabled. Adobe Reader will have Protected Mode enabled.
Server Category
An attempt in this category must be launched from the contestant’s laptop within the contest network.
Targets:
Target | Prize | Master of Pwn Points |
Microsoft Windows RDP/RDS | $200,000 | 20 |
Microsoft Exchange | $200,000 | 20 |
Microsoft SharePoint | $100,000 | 10 |
Samba | $75, 000 | 8 |
Local Escalation of Privilege Category
An attempt in this category must be launched from within the target under test from a non-admin and non-root account. In this category, the entry must leverage a kernel vulnerability to escalate privileges.
Targets:
Target | Prize | Master of Pwn Points |
Ubuntu Desktop | $40,000 | 4 |
Microsoft Windows 11 | $40,000 | 4 |
Enterprise Communication Category
An attempt must compromise the target application by communicating with the contestant. Example communication requests could be audio call, video conference, message, etc.
Targets:
Target | Prize | Master of Pwn Points |
Zoom | $150,000 | 15 |
Microsoft Teams | $150,000 | 15 |
Automotive Category
An attempt in this category must be launched against the target under test, a Tesla Model 3 (Intel or Ryzen-based), Tesla Model S (Ryzen-based) or equivalent bench top unit. This category contains targets at different tiers based on the complexity of the entry required. Each tier has different requirements and are eligible for different prize packages. Tier 1 targets represent the most difficult entries and require the contestant to get arbitrary code execution on three different sub-systems in the vehicle. Tier 2 targets require the contestant to get arbitrary code execution on two different sub-systems in the vehicle and Tier 3 targets focus on testing the individual sub-systems.
Tier 1 Targets:
Target | Prize Amount | Master of Pwn Points | Additional Prize Options | Eligibility | ||
Initial Vector | Intermediate | Final Stage | ||||
Tuner, WiFi, Bluetooth, or Modem | Infotainment | VCSEC, Gateway, or Autopilot
|
$500,000 USD
|
50
| Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | Yes | |||||
Autopilot Root Persistence Add-on | Yes | |||||
CAN Bus Add-on | No | |||||
Tier 2 Targets:
Target | Prize Amount | Master of Pwn Points | Additional Prize Options | Eligibility | |
Initial Vector | Final Stage | ||||
Tuner, WiFi, Bluetooth, or Modem | Infotainment | $250,000 USD | 25 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Infotainment | VCSEC, Gateway, or Autopilot | $300,000 USD | 30 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | Yes | ||||
CAN Bus Add-on | No | ||||
Tuner, WiFi, Bluetooth, or Modem | VCSEC, Gateway, or Autopilot | $400,000 USD | 40 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | Yes | ||||
CAN Bus Add-on | No | ||||
Tier 3 Targets:
Target | Prize Amount | Master of Pwn Points | Additional Option | Eligibility | |
Initial Vector | Option | ||||
Modem or Tuner | N/A | $60,000 USD | 6 | Vehicle Prize | No |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Wi-Fi or Bluetooth | N/A | $60,000 USD | 6 | Vehicle Prize | No |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Infotainment | N/A | $35,000 USD | 3.5 | Vehicle Prize | No |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Diagnostic Ethernet | $25,000 USD | 2.5 | Vehicle Prize | No | |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
USB-based Attack | $35,000 USD | 3.5 | Vehicle Prize | No | |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Sandbox Escape | $100,000 USD | 10 | Vehicle Prize | No | |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
Unconfined Root/Kernel Escalation of Privilege | $150,000 USD | 15 | Vehicle Prize | No | |
Infotainment Root Persistence Add-on | Yes | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | Yes | ||||
VCSEC, Gateway, or Autopilot | N/A | $200,000 USD | 20 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | Yes | ||||
CAN Bus Add-on | No | ||||
Autopilot and Gateway (Ethernet Attack Surface only) | N/A | $100,000 USD | 10 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | Yes | ||||
CAN Bus Add-on | No | ||||
Autopilot Denial-of-Service | N/A | $50,000 USD | 5 | Vehicle Prize | No |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | No | ||||
Key Fobs or Phone-as-Key | N/A | $100,000 USD | 10 | Vehicle Prize | Yes |
Infotainment Root Persistence Add-on | No | ||||
Autopilot Root Persistence Add-on | No | ||||
CAN Bus Add-on | No | ||||
· Entries against “Modem or Tuner”, “Wi-Fi or Bluetooth”, and “Gateway, Autopilot, or VCSEC” targets (or targets that include these as initial vectors) must achieve code execution by communicating with a rogue base station or other malicious entity.
· Entries against the “Infotainment” target (or targets that include Infotainment as an initial vector) must be launched from the target under test and must achieve code execution by browsing to malicious content. In Tier 1 and Tier 2, man-in-the-middle browser attacks against the “Infotainment” system are not allowed.
· Any “Infotainment” entry that is leveraging vulnerabilities in the built-in browser must be chained with a sandbox escape or a root/kernel privilege escalation. The sandbox escape must result in code execution outside the browser containment measures, not just the Chromium sandbox.
· USB-based attacks in the “Infotainment” category must target the USB port that passengers would routinely plug into that is openly exposed on the center console or glovebox. Any other exposed USB ports are not in scope for this target.
· Entries against Diagnostic Ethernet attacks in the “Infotainment” category are eligible for an additional $10,000 USD bonus if the entry targets a service other than the exposed Odin and Update services.
· Entries targeting Odin and Update services that require physical access to the Diagnostic Ethernet or USB are not eligible for the Unconfined Root/Kernel Escalation of Privilege prize.
· Entries against the “Key Fobs or Phone-as-Key” target must achieve code execution, arbitrary vehicle unlock, or arbitrary vehicle start using protocol-related weaknesses. Entries related to Key Fob relay, Key Fob cloning, or Rolljam attacks are not allowed. The entry must succeed without the Key Fob being present.
· Entries that require physical access are out of scope, unless otherwise stated.
Available Add-on Prizes:
Add-on Prize Type | Add-on Prize | Prize | Master of Pwn Points |
Infotainment Root Persistence | Entry’s payload must maintain root persistence on the Infotainment target over a reboot. | $50,000 | 5 |
Autopilot Root Persistence | Entry’s payload must maintain root persistence on the Autopilot target over a reboot. | $50,000 | 5 |
CAN Bus | Entry’s payload must demonstrate arbitrary control of any physical CAN bus. | $100,000 | 10 |
Along with the prize money, the first-round winner against an eligible target in this category will win a Tesla Model 3 or comparable vehicle (MSRP $44,990 (USD)) (“Tesla Prize”). If the entry targets a Tesla Model S (Ryzen-based), the Tesla Prize will be a Tesla Model 3. No additional options are included in the vehicle. If the Tesla Prize is not available for whatever reason, Sponsor may substitute the Tesla Prize for (1) an alternate Tesla vehicle of equivalent value, or (2) an amount equal to the current value of the Tesla Prize payable in USD, in Sponsor’s discretion.
Master of Pwn
The contestant with the highest total points at the end of the contest ("Master of Pwn") will receive 65,000 ZDI reward points (estimated at $25,000 (USD)). Total points are calculated by the sum of the successful entries based on the allocated Master of Pwn points in the tables above.
For example, if a contestant has two successful entries (Microsoft Edge (Chromium) with a Sandbox Escape and Google Chrome with a Sandbox Escape chained with a VMware Workstation escape add-on) would be 38 Master of Pwn points. If two or more contestants have the same number of points at the end of the contest, each of these contestants will receive 65,000 ZDI reward points (estimated at $25,000 (USD)).
If the contestant decides to remove an Add-on Bonus during their attempt, the Master of Pwn points for that Add-on Bonus will be deducted from the final point total for that attempt. If the contestant decides to withdraw from the registered attempt after the start of the contest, the Master of Pwn points for that attempt will be divided by 2 and deducted from the contestant’s point total for the contest.
Along with the prize money, the first-round winner for a given category will win a laptop (estimated value of $1,000 (USD)) unless otherwise stated in the Category description in Section 4. Winners of these prizes are not entitled to the difference, if any, between the actual prize value and the estimated prize value. The estimated prize value is as of the date of printing of these Contest Rules.
It is possible that a category may have no winner. If a category has no winner, Sponsor may, in its sole discretion, choose to use the prize money from that category to offer additional prize(s) in another above listed category that may be equal to or less than the initial prize offering for such category. The odds of winning depend on the number of eligible participants in a category and the ability to meet the requirements of this skills-based Contest. Prizes will be distributed within eight (8) weeks after each winner has fulfilled the requirements set out herein.
Prizes must be accepted as awarded and cannot be transferred, assigned, substituted, or redeemed for cash except at the sole discretion of Sponsor. Any unused portion of a prize will be forfeited and have no cash value. Sponsor reserves the right, in its sole discretion, to substitute a prize of equal or greater value if a prize (or any portion thereof) cannot be awarded for any reason. Taxes on prizes, if any, are the sole responsibility of the winner.
Sponsor reserves the right, in its sole discretion, to add or modify the categories if a new version of one of the targets or devices are released, hardened, updated, or recalled between the release of the Contest Rules and the Contest.
The Sponsor shall not assume any liability for any lost or misdirected prizes.
5. WINNER SELECTION.
If more than one contestant registers for a given category, the order of the contestants will be drawn at random. Based on the contestant order, the first contestant will be given an opportunity to attempt to compromise the selected target. If unsuccessful, the next randomly drawn contestant will be given an opportunity. This will continue until a contestant successfully compromises the target. The first contestant to successfully compromise a selected target will win the prize money for that target in the category. After a target has been compromised, the contest for that category is over and no other contestants will participate in the contest for that category (unless Sponsor has offered an additional winner option, which would be announced at the Contest, if applicable).
A successful entry must leverage a vulnerability to modify the standard execution path of a program or process in order to allow the execution of arbitrary instructions. The entry is required to defeat the target’s techniques designed to ensure the safe execution of code, such as, but not limited to, Data Execution Prevention (DEP), Address Space Layout Randomization (ASLR) and/or application sandboxing. The targets for the 2022 Contest will not have hardware support for the Control-flow Enforcement Technology (CET) mitigation. If a sandbox is present, a full sandbox escape is required unless otherwise stated in the Category description in Section 4. The resulting payload should be executing in an elevated context (for example, on Windows-based targets, Medium integrity level or higher).
A contestant has up to three (3) attempts to succeed. Each of the three (3) attempts will be individually limited to a time period of five (5) minutes. For an attempt to be deemed successful, all elements of the attempt must complete within the 5-minute window. All three (3) attempts must be completed within thirty (30) minutes, excluding time needed to setup device prior the attempt. Notwithstanding the foregoing, Sponsor may extend a contestant’s time, in Sponsor’s discretion, if during an attempt, the contestant experiences any connection issues caused by inaccessible or unavailable networks, servers, Internet Service Providers, or other connections that are outside of contestant’s or Sponsor’s control.
A successful entry against these targets must require no user interaction beyond the action required to launch the attempt and must occur within the user’s session with no reboots, or logoff/logons. For example, having to interact with a dialog in order to successfully complete the exploit or writing a malicious file to the Startup folder is not allowed.
The initial vulnerability utilized in the entry must be in the registered target. The sandbox escape utilized in the entry must be in the registered target (unless the entry leverages a kernel privilege escalation). A given vulnerability may only be used once across all categories. The vulnerabilities utilized in the attack must be unknown, unpublished, or not previously reported to the vendor or the Sponsor. If the entry leverages a previously known vulnerability, as evidenced by the vendor or Sponsor, Sponsor may, in its sole discretion, choose to accept the entry(ies) and offer the prize(s) at a value less than the initial prize offering for a given category.
If authentication is present, the exploit must occur prior to authentication to the service or include an authentication bypass. If the entry requires a man-in-the-middle attack, Sponsor may, in its sole discretion, choose to accept the entry(ies) and offer the prize(s) at a value less than the initial prize offering for a given category. Contestants may contact the Sponsor prior to the Contest to obtain a determination regarding prize eligibility for proposed entries that require such techniques.
The targets will be running on the latest, fully patched version of the operating system available on the selected target (Microsoft Windows 11 21H2 x64, Apple macOS Monterey, and Ubuntu 22.04 for Desktop) unless otherwise stated in the Category description in Section 4. All targets will be 64-bit, if available, and installed in their default configurations.
Sponsor reserves the right to solely determine what constitutes a successful entry. The Sponsor may, in its sole discretion, choose to accept the entry(ies) and offer the prize(s) at a value less than the initial prize offering for a given category if the Sponsor deems that part of the exploit chain fails to meet the above rules. For example, if the entry contains a previously known vulnerability, and the vendor has not yet released a patch, Sponsor may accept the entry(ies) and offer the prize(s) at a value less than the initial prize offering for a given category.
Upon successful demonstration of the exploit, the contestant will provide Sponsor with a fully functioning exploit plus a whitepaper explaining the vulnerabilities and exploitation techniques used in the entry. In the case that multiple vulnerabilities were exploited to gain code execution, details about all of the vulnerabilities (memory corruption, infoleaks, escalations, etc.) leveraged and the sequence in which they are used must be provided to receive the prizes. Vulnerabilities and exploit techniques revealed by contest winners will be disclosed to the affected vendors and the exploits and whitepapers will become the property of the Sponsor in accordance with the ZDI researcher agreement.
6. INDEMNIFICATION BY CONTESTANT.
By entering the Contest, contestant releases and holds Sponsor harmless from any and all liability for any injuries, loss, or damage of any kind to the contestant or any other person, including personal injury, death, or property damage, resulting in whole or in part, directly or indirectly, from acceptance, possession, use, or misuse of any prize, participation in the Contest, any breach of the Contest Rules, or in any prize-related activity. The contestant agrees to fully indemnify Sponsor from any and all claims by third parties relating to the Contest, without limitation.
7. LIMITATION OF LIABILITY.
Contestant acknowledges and agrees that Sponsor assumes no responsibility or liability for any computer, online, software, telephone, hardware, or technical malfunctions that may occur. The Sponsor is not responsible for any incorrect or inaccurate information, whether caused by website users or by any of the equipment or programming associated with or utilized in the Contest or by any technical or human error which may occur in the administration of the Contest. The Sponsor is not responsible for any problems, failures, or technical malfunctions of any telephone network or lines, computer online systems, servers, providers, computer equipment, software, e-mail, players, or browsers, on account of technical problems or traffic congestion on the Internet, at any website, or on account of any combination of the foregoing. The Sponsor is not responsible for any injury or damage to contestant or to any computer related to or resulting from participating or downloading materials in this Contest. Contestant assumes liability for injuries caused or claimed to be caused by participating in the Contest, or by the acceptance, possession, use of, or failure to receive any prize. The Sponsor assumes no responsibility or liability in the event that the Contest cannot be conducted as planned for any reason, including those reasons beyond the control of the Sponsor, such as infection by computer virus, bugs, tampering, unauthorized intervention, fraud, technical failures, or corruption of the administration, security, fairness, integrity, natural disaster, or proper conduct of this Contest.
8. CONDUCT.
As a condition of participating in the Contest, each contestant agrees to be bound by these Contest Rules and indicates consent as part of the registration process. Contestant further agrees to be bound by the decisions of the Sponsor, which shall be final and binding in all respects. The Sponsor reserves the right, in its sole discretion, to disqualify any contestant found to be: (a) violating the Contest Rules; (b) tampering or attempting to tamper with the Contest or any of the equipment, the Contest website or Contest programming; or (c) acting in an unsportsmanlike or disruptive manner that interferes with any portion of the Contest; or (d) engaging in any form of harassing, offensive, discriminatory, or threatening speech or behavior, including (but not limited to) relating to race, gender, gender identity and expression, national origin, religion, disability, marital status, age, sexual orientation, military or veteran status, or other protected category. CAUTION: ANY ATTEMPT TO DELIBERATELY UNDERMINE THE LEGITIMATE OPERATION OF THE CONTEST MAY BE A VIOLATION OF CRIMINAL AND CIVIL LAWS. SHOULD SUCH AN ATTEMPT BE MADE, THE SPONSOR RESERVES THE RIGHT TO SEEK REMEDIES AND DAMAGES TO THE FULLEST EXTENT PERMITTED BY LAW, INCLUDING BUT NOT LIMITED TO CRIMINAL PROSECUTION.
9. PRIVACY / USE OF PERSONAL INFORMATION.
By participating in the Contest, contestant: (i) grants to the Sponsor the right to use his/her name, likeness, mailing address, telephone number, and e-mail address ("Personal Information") for the purpose of administering the Contest, including but not limited to contacting and announcing the winners; and (ii) acknowledges that the Sponsor may disclose his/her Personal Information to third-party agents and service providers of the Sponsor in connection with any of the activities listed in (i) above.
Sponsor will use the contestant’s Personal Information only for identified purposes, and protect the contestant’s Personal Information in a manner that is consistent with Sponsor’s Privacy Policy at: trendmicro.com/privacy
10. INTELLECTUAL PROPERTY.
All intellectual property, including but not limited to trademarks, trade names, logos, copyrights, designs, promotional materials, web pages, source code, drawings, illustrations, slogans, and representations are owned by Sponsor and/or its affiliates. All rights are reserved. Unauthorized copying or use of any copyrighted material or intellectual property without the express written consent of its owner is strictly prohibited.
11. TERMINATION.
Sponsor reserves the right, in its sole discretion, to terminate the Contest, in whole or in part, and/or modify, amend, or suspend the Contest, and/or the Contest Rules in any way, at any time, for any reason without prior notice.
12. LAW.
These are the official Contest Rules. The Contest is subject to applicable laws and regulations. The Contest Rules are subject to change without notice in order to comply with any applicable laws or the policy of any other entity having jurisdiction over the Sponsor and/or the Contest. All issues and questions concerning the construction, validity, interpretation, and enforceability of the Contest Rules or the rights and obligations as between the contestant and the Sponsor in connection with the Contest shall be governed by and construed in accordance with the laws of the State of Texas including procedural provisions without giving effect to any choice of law or conflict of law rules or provisions that would cause the application of any other jurisdiction’s laws.
13. PRECEDENCE.
In the event of any discrepancy or inconsistency between the terms and conditions of the Contest Rules and disclosures or other statements contained in any Contest-related materials, the terms and conditions of the Contest Rules shall prevail, govern, and control.
© 2022 Trend Micro Incorporated. All rights reserved. PWN2OWN, ZERO DAY INITIATIVE, ZDI and Trend Micro are trademarks or registered trademarks of Trend Micro Incorporated. All other trademarks and trade names are the property of their respective owners.
转载请注明出处及链接

